This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

When you're trying to cut some calories or just eat more veggies, it's important to enjoy what you're eating. If all you're doing is telling yourself "no" and focusing on what you can't eat, you are pretty much destined to fail at your diet.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.
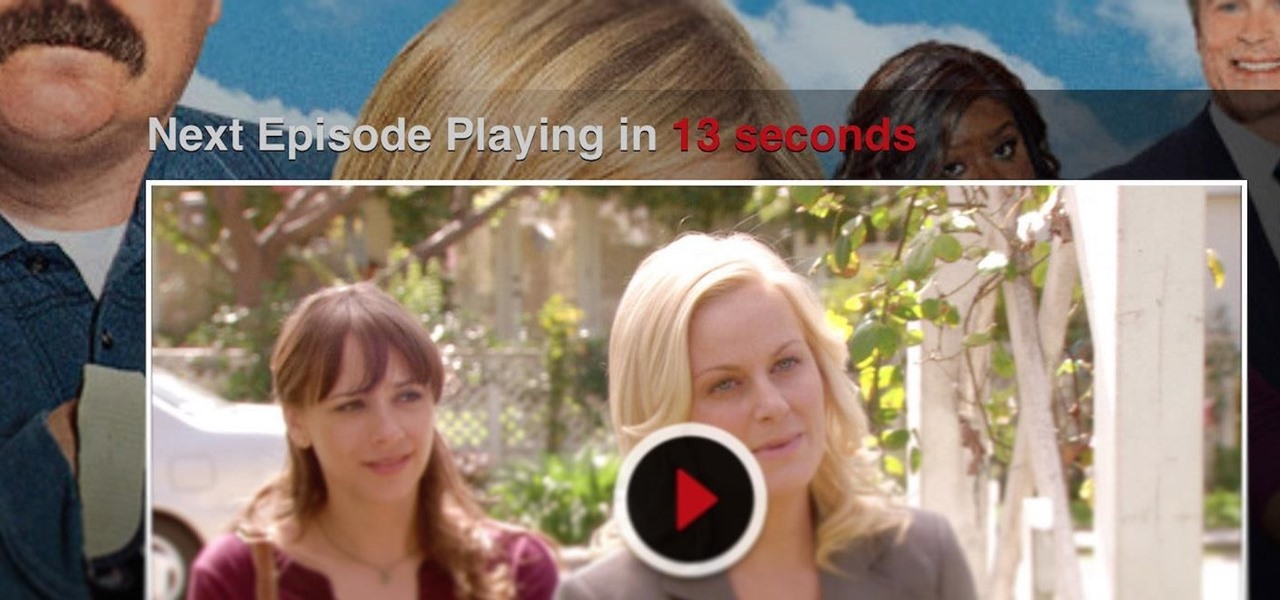
Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Step 1: Introduction: Hello! Hackers

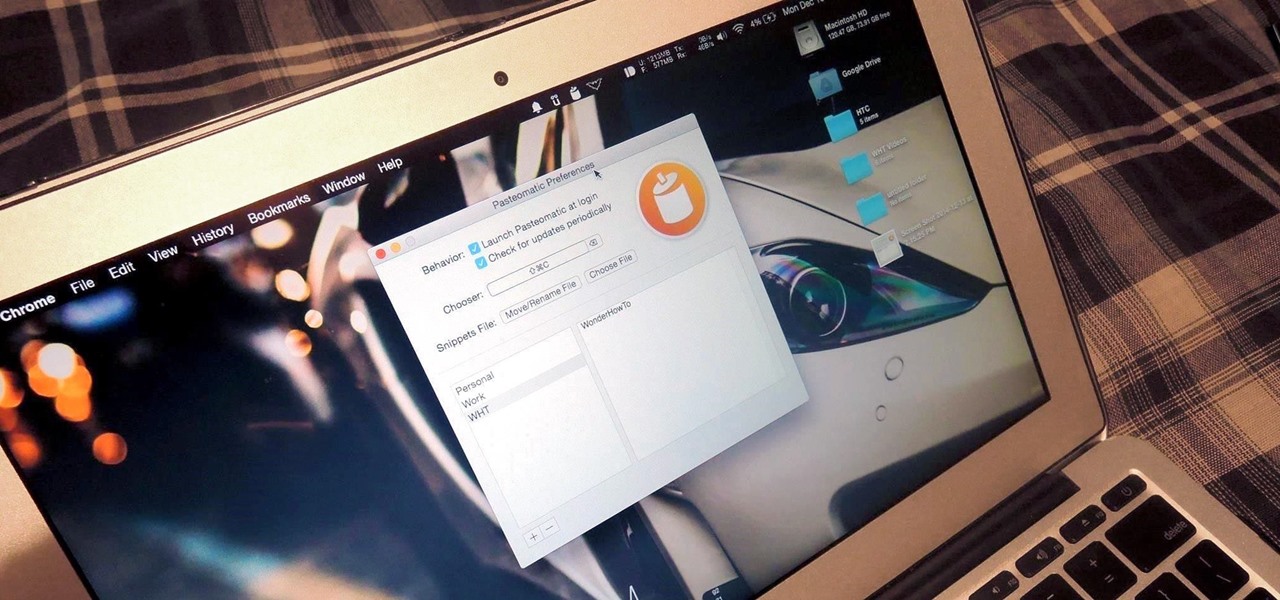
Your Mac's clipboard is great when you are just copying and pasting a phone number or address, but sometimes you end up having to re-copy the same thing over and over every day. To make those phrases a lot more easily accessible, the people over at Tiny Robot Software have released Pasteomatic. With this app, you will be able to use a hotkey to bring up a collection of your most commonly used text snippets and paste them into any text field or document.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

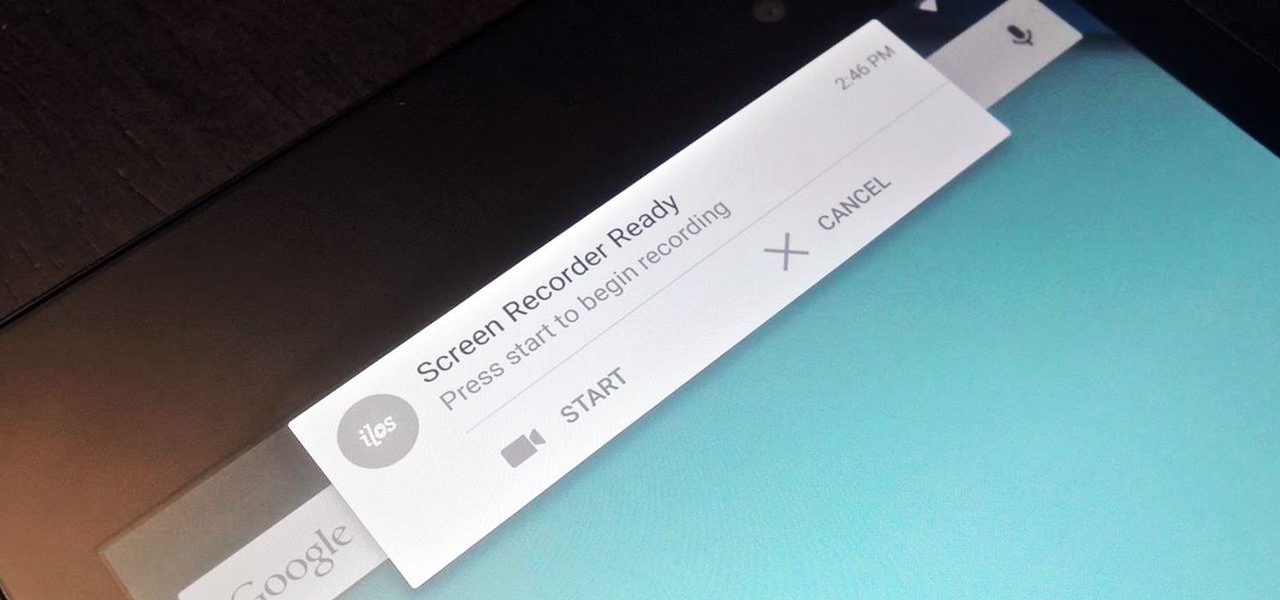
Native screen recording was initially introduced on Android 4.4 KitKat and, although useful, was primarily utilized by developers to showcase their apps. It required either a rooted device and an app or a non-rooted device with some ADB commands, which, while totally doable, wasn't necessarily ideal.

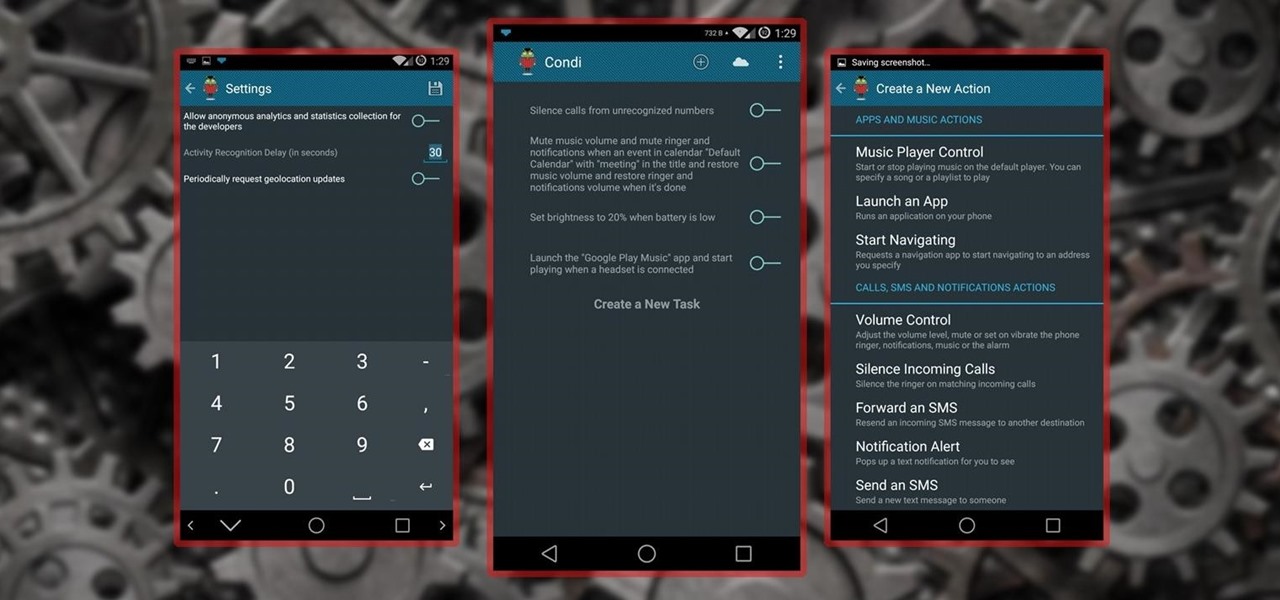
No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.

Finding a unique wallpaper can be extremely difficult, and even the most dynamic wallpapers become exhausted and boring to look at after a while. Searching for new, interesting wallpapers can become a tedious task, so instead, let's just make our own instead.

Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.

Clash of Clans is one of the most successful games ever to come out for Android and iOS. It has been downloaded over 50 million times from Google Play alone, and shows no signs of decline.

Greetings, my friend. Welcome to Null Byte. I am Dr. Crashdump. Linux will be talked about a lot in Null Byte. It's used in most tutorials on this site, actually. You should learn how to use Linux as soon as possible, but where do you start? No worries. Let's figure that out.

Playing any multiplayer game without chatting is like watching Avatar on your iPhone—just downright sad. So, in order to get the shit-talking going between your friends and party members, you will need get your headset working properly and use Party Chat, which can get a little confusing.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

My grandfather's brother won this car in a lottery during 1957. He had no driver's license, but his brothers used to give him a lift in it. From 1975 to 1996, the car was parked in my grandfather's brother's garage. My grandfather moved the car on a trailer in 1996 to his garage a few miles away, but it's been standing still there until this year when I rolled it out and started it up. This was the first time someone turned it on in 38 years!

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Did YOU know...that African Americans have the highest rate of colorectal cancer, and that it is more likely to be advanced at diagnosis? The age for colonoscopy in ACG guidelines dropped to 45 for African Americans in 2009. This digestive ditty about colon cancer screening in Black Americans pays homage to Beyonce's iconic Single Ladies video. Help us to get the word out--Email this link to your African American colleagues and friends and post it to your Facebook or Twitter pals! We can prev...

I know what you're thinking—taking a screenshot is super simple. While that is partly true, taking of a screenshot of the Start Screen in Windows 8 is little bit tricky, unless you're on your Surface.

Video: . The Walls is a PvP survival map that takes back Minecraft to it's roots: crafting, surviving and creativity.

If you've completed chapter 3 of Disgaea 4: A Promise Unforgotten, you can access the map maker and start to create your own maps for multiplayer. This guide teaches you how to use the map maker in Disgaea 4 to create unique maps for use against your online opponents!

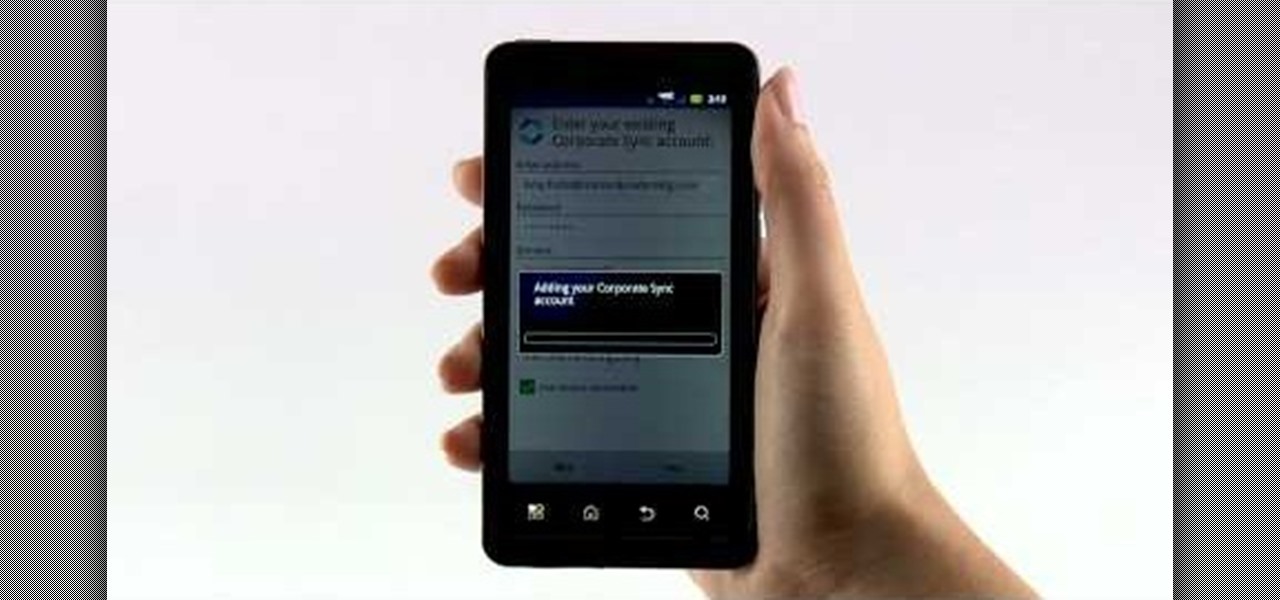
The Motorola Droid Bionic has support for both corporate email and personal email accounts. If you want to setup either, take a look at this guide from Motorola on how to sign into your email on the Android smartphone so that you can start reading and sending new messages using Verizon Wireless's 4G network connection.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

A variation on the Rice Krispie treat, make some cookies using Cap'n Crunch cereal! Start with a box of powdered Cap'n Crunch and bread flour, and then add baking powder, baking soda, butter, white sugar, brown sugar and some eggs.

We know that December 31st may seem like old news now, but for the Chinese the New Year is just getting started. Chinese New Year begins on February 3rd and ushers in the Year of the Rabbit.

If you're a small business operator and AT&T is your carrier, you'll want to take advantage of the AT&T Online Account Management portal for small business customers. This video shows how to request an online registration code (required to register your account), how to use it to register your account, and how to set up your username and password.

You've probably seen a lot of impressive how-to videos - or simple "show off" videos - on how to fold crazy 100-sided modular origami sphere-like thingymabobs, but most of the time we're betting you're sitting there going, "huh?".

Most snowmen sadly melt even before Christmas even starts (and some turn yellow towards the bottom, but let's get into that later), but this cupcake snowman will stay firm and cute...until you stick it into your mouth, that is.

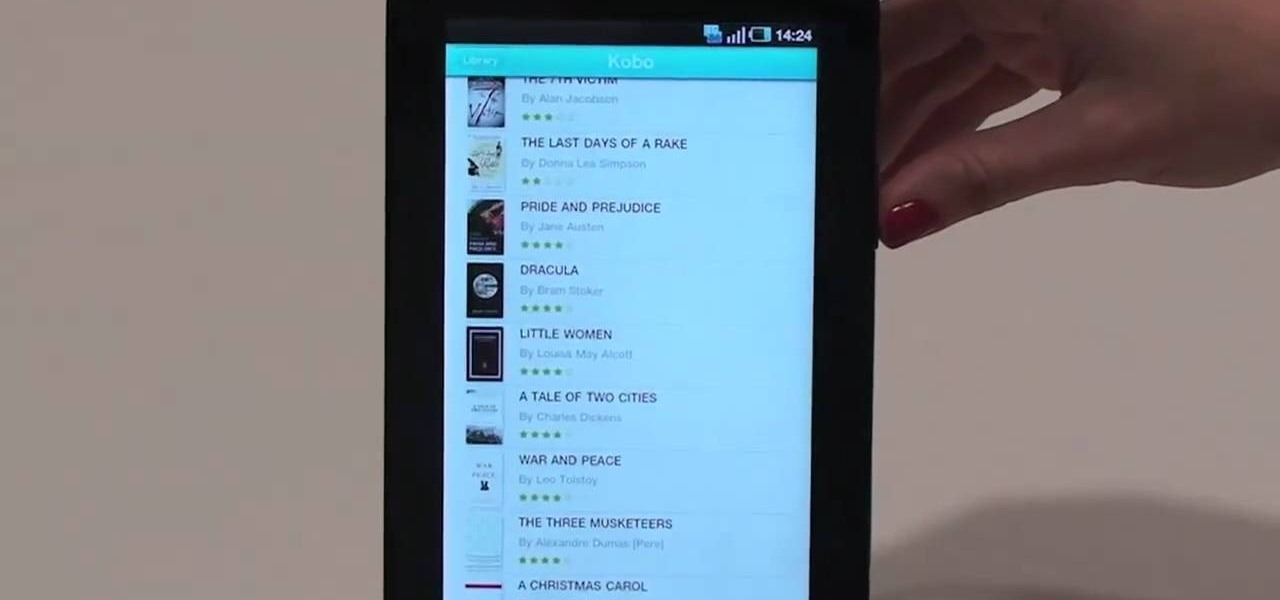
One of the coolest features on the Samsung Galaxy Tab is the in-built Readers Hub. It's ideal for reading all of the newspaper, books and magazines within the Android tablet. All you need to do is go to the Reader Hub and start reading! Watch and see how easy it is!

November is national Novel Writing Month, which means if you've been dreaming about penning a bestselling science fiction or fantasy thriller since you turned 10, now is the time to put pen to paper.

In this tutorial, we learn how to perform a Ghost Ride Heelflip on a long board. First, get on your board and start to petal. Then, bring your left foot off and bring it near the board, as close as you can. Then, bring your right foot behind you and then flip your board over. After this, jump up with both of your feet and jump onto the board to the other side of you. Practice doing this to get it right, it may take you a little while. When done, you can start to learn different variations on ...