Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Prying into people's lives without them putting up their guard can be difficult, unless you can convince them that you already know them very well. Most people don't have many friends they can be honest with, and this can be exploited. Once they're convinced you already know their secrets, they'll start to fill you in on the little details.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...
A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

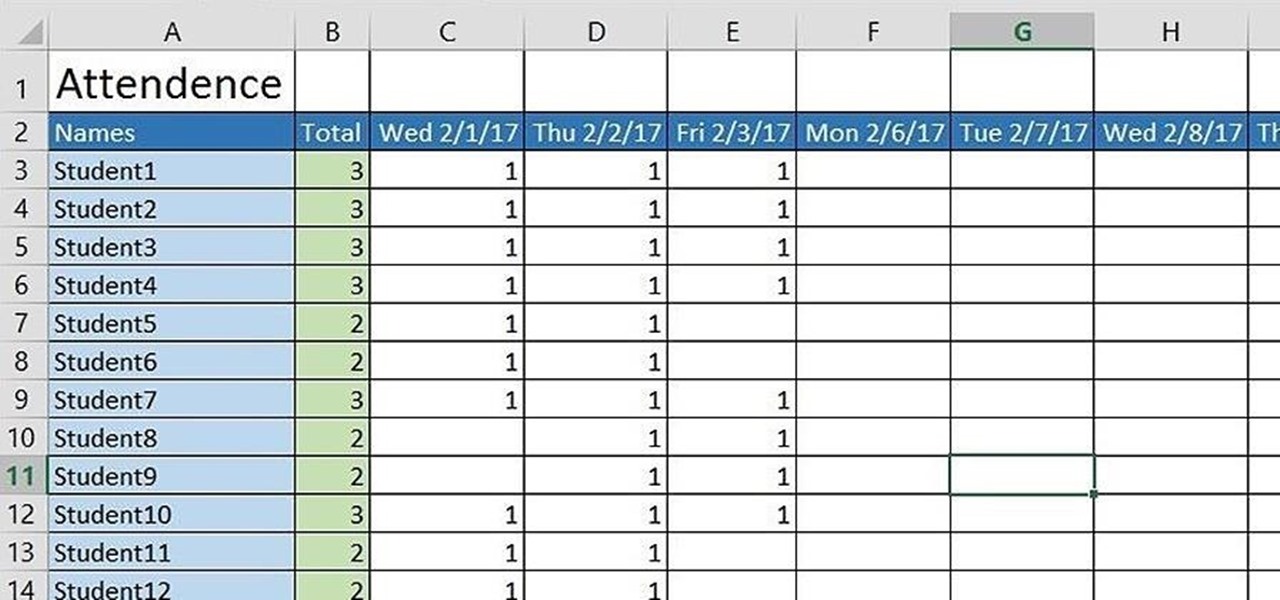
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

Beauty pageants require contestants to take platforms by writing essays introducing their connection to social issues. Write a solid pageant platform statement with a pageant veteran in this free beauty pageant preparation video series.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

After awarding $410 million to the company that supplies it with VCSELs and LiDAR sensors, Apple has made another strategic investment into a company that may contribute to future augmented reality hardware innovations.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

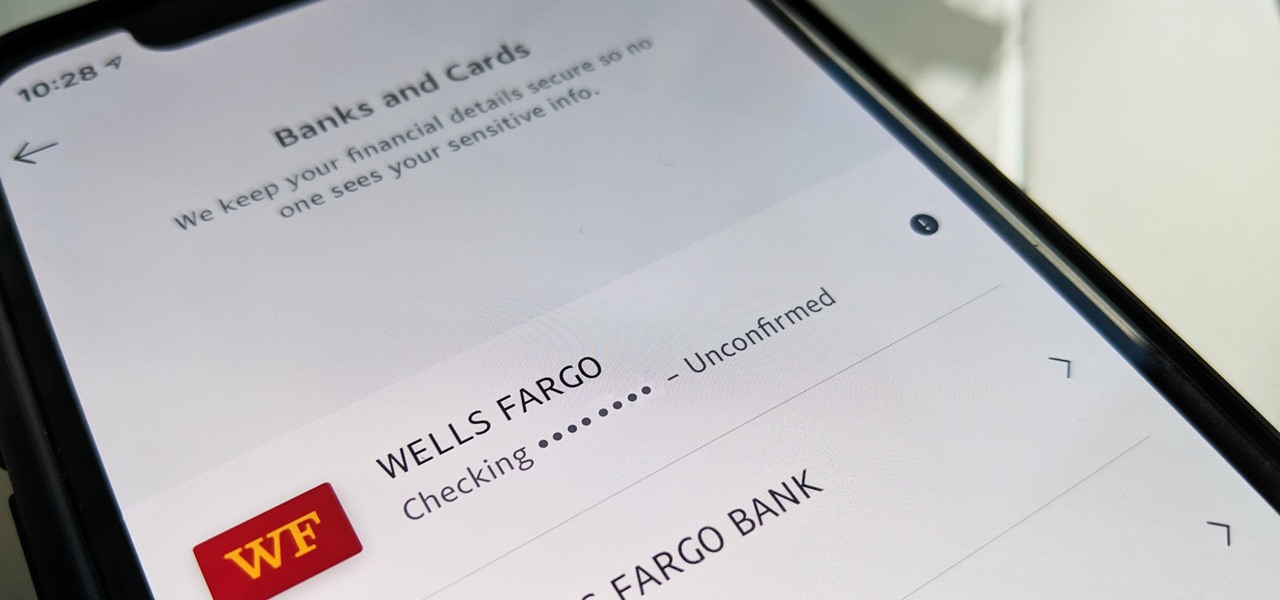
PayPal is one of the most popular payment systems across the globe. It makes payments fast, easy, and secure, and with 250+ million users, it's not going anywhere. If you're new to the online service, one of the first things you should learn is how to add your bank account, credit card, or debit card to PayPal, and make your life easier when it comes to online payments and withdrawals.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

Twitter replies have traditionally acted like public spaces. Once a tweet is out there, pretty much anyone can reply to it. In some cases, that makes for good discussion. In others, it can lead to disaster, abuse, and harassment. Twitter's looking to change that by giving you more control over who can reply to tweets.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

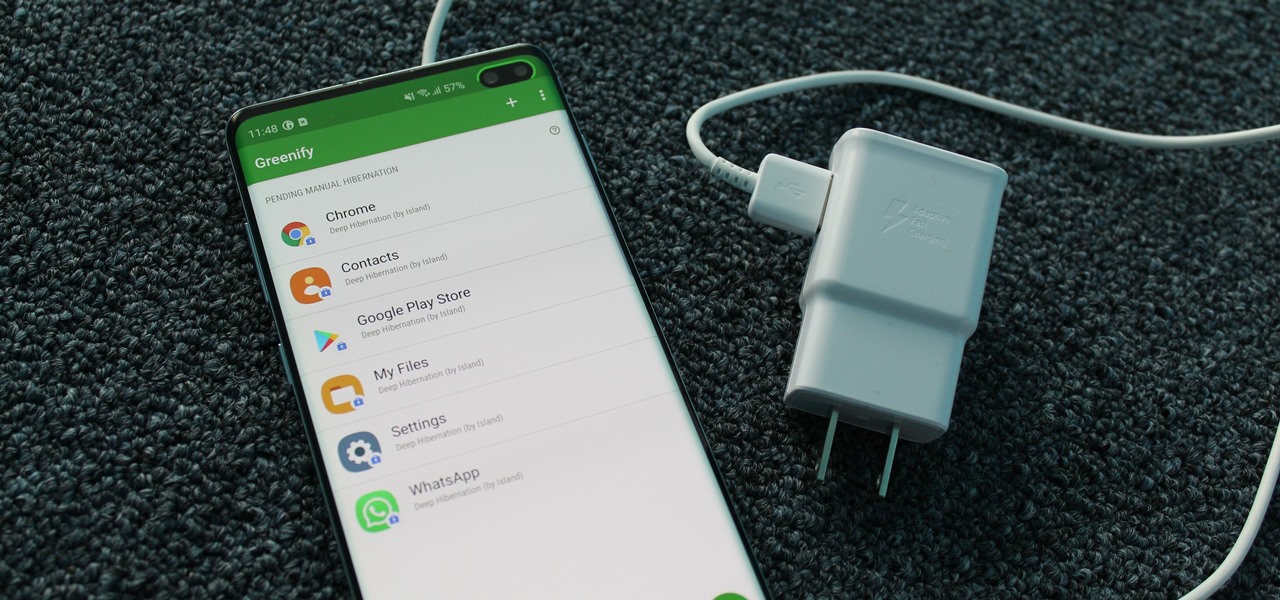
Despite newer phones having larger batteries, after a few months, my battery life drops significantly. I started researching solutions after my third phone. No matter who I asked, the most recommended solution was always Greenify. And unlike other solutions, you don't need root to use it.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.

The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

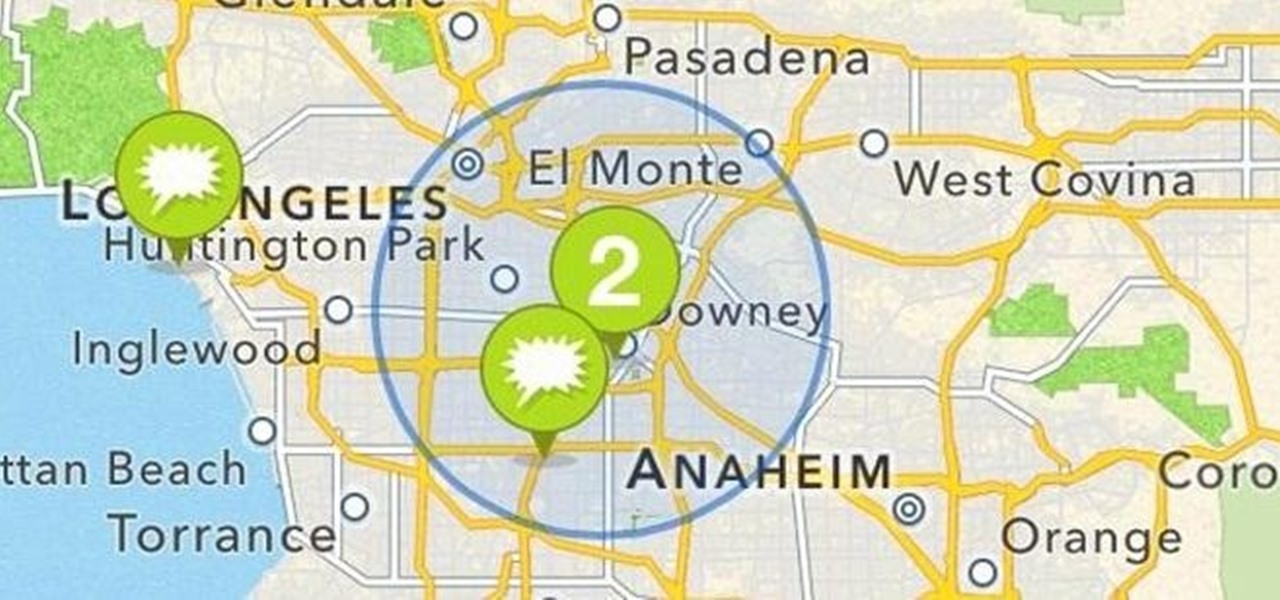
In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

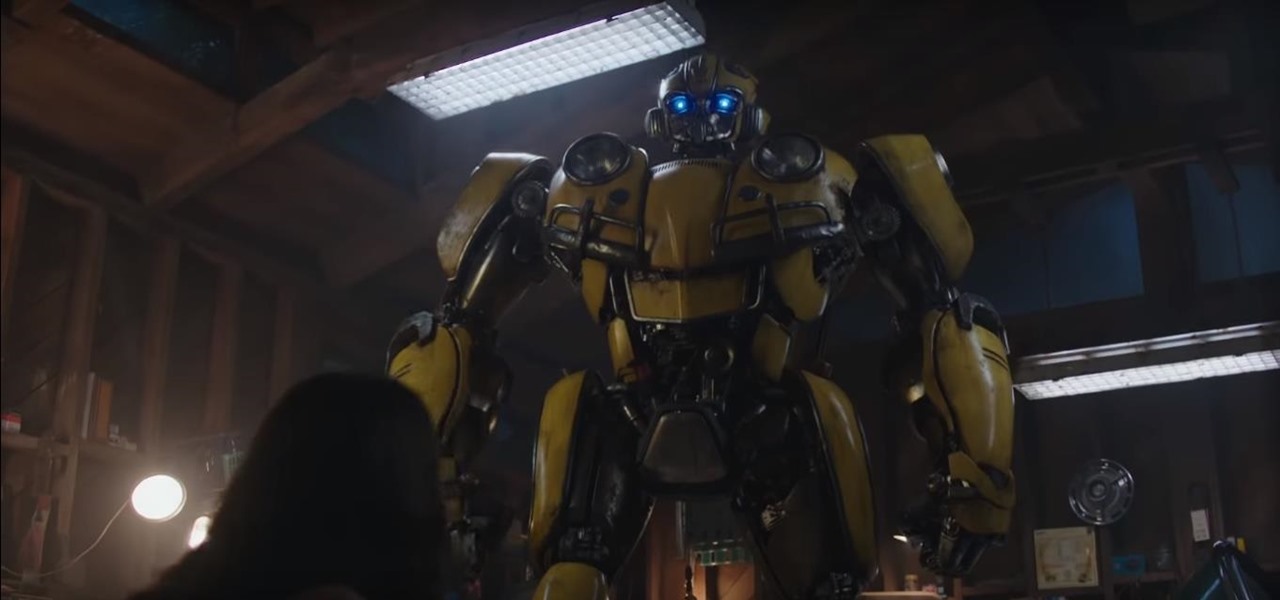
Fan favorite Transformer Bumblebee returns to theaters on Friday in a spin-off of the film franchise, so Paramount Pictures is bringing the car-robot back into the homes of fans via augmented reality.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

Last week, Twilio showed off how avatar-based chat communications will work on the Magic Leap One, and now a new startup has unveiled yet another way that augmented reality telepresence and remote collaboration can take place on the device.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

The dream of Google Glass lives on via North's stylish and normal-looking smartglasses that bring text messages and navigation prompts into the user's field of view and Amazon Alexa integration for voice-activated assistance.