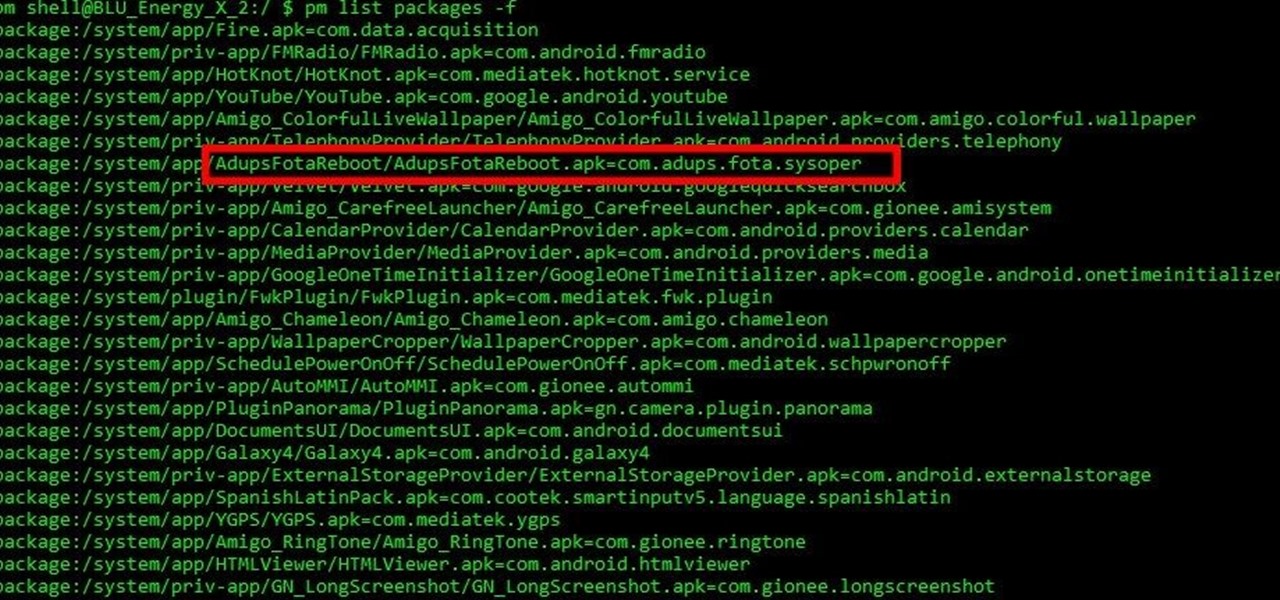
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

If you haven't come up with a funny, innovative costume yet for Halloween, you're running out of time. While all your friends are busy perfecting their month-long DIY costume project, you're still being lazy about it and have just now started to search online for ideas.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Why did I write this when they're tons of scanning tools available.

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Sweaty palms, stuttered speech, and terror blackouts: if you're someone who absolutely despises speaking before audiences, you've probably experienced side effects like these. No matter how well prepared we are, or how familiar our audience is, giving a presentation can be an experience more terrifying than death, according to psychologists. Unfortunately, it's impossible to avoid public speeches, but you can make these events less frightening with a few simple hacks.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Halloween is a night to dress up as any character you'd like—but for women, that typically means wearing something skimpy or downright absurd. From "sexy" policewomen to nearly undressed fairy tale princesses, we're surrounded by costumes that leave little to the imagination. And, let's be honest: who wants to spend a chilly October night in barely-there clothing?

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

I love my cast-iron skillet, but I never seasoned it properly. Instead, I took that sucker out of its packaging, wiped it down with a damp cloth to remove any factory dust, and started cooking with it ASAP. And you know what? It works just fine.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

If you drop your smartphone in water, take it apart as much as you can and place it in rice. It's been the most recommended method of cell phone rescue since the days of clamshells. In fact, it's usually the only thing recommended when searching for "how to save your wet phone." Turns out, we've been wrong all along.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

With its latest version of Apple Maps, Apple has made perhaps its strongest push since the launch of the app to dethrone Google Maps from its perch atop the App Store rankings.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

If the importance of augmented reality and VR hardware to Facebook's future wasn't already clear enough, a shake-up in the executive ranks at the company has made it as clear as smartglasses lenses.

The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

The remake of the Warner Bros. classic animation meets live-action movie Space Jam, this time starring LeBron James instead of Michael Jordan, hits theaters today.

Some tried to call it a brief cryptocurrency-fueled fad, but it looks like NFTs are here to stay. Now, one of the biggest sneaker companies on the planet, Japan's Asics, is getting into the game with its own set of NFTs, and there's a virtual object component included.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

It's all fun and games until the technology is actually put into use and you realize augmented reality is now part of Death Star.

The startup JigSpace, which was among the first apps to support ARKit and LiDAR for iPhone augmented reality apps, has capitalized on its early mover status by innovating within the space.

While Apple was one of the first to integrate LiDAR into mobile devices for depth sensing, headset maker Varjo has developed a truly remarkable feat with its implementation of the sensor.

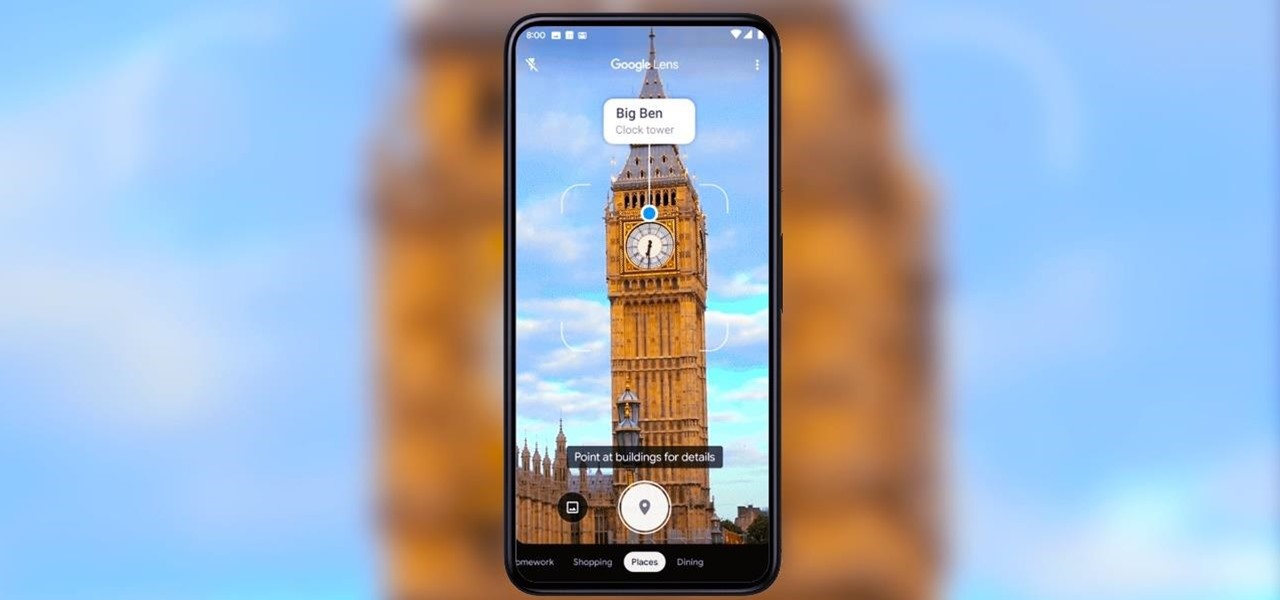
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Ever since Snapchat rebuffed its acquisition attempts, Facebook has morphed Instagram with features from Snapchat, such as stories, chat, and, of course, augmented reality.

During the Tuesday launch of Google I/O, the company's CEO, Sundar Pichai, pulled off a Steve Jobsian "one more thing" move near the end of his keynote address that was simply stunning.