
News: Snap Releases Lens Studio 4.0 with 3D Body Mesh & More, Upgrades Scan as Fashion Assistant
Throughout Thursday's virtual Snap Partner Summit, Snapchat's parent company made a profound statement: If you use Snapchat, you're a creator.


Throughout Thursday's virtual Snap Partner Summit, Snapchat's parent company made a profound statement: If you use Snapchat, you're a creator.

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.
Hand tracking is a key component in making natural interactions with augmented reality content, and one of the leading technology makers in this discipline has just improved on its tracking engine.

In response to Sony unveiling its own holographic display back in October, Looking Glass Factory CEO Shawn Frayne quickly penned a letter welcoming the electronics mainstay to the field, with a post-script teasing the reveal of their own for December of 2020.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.
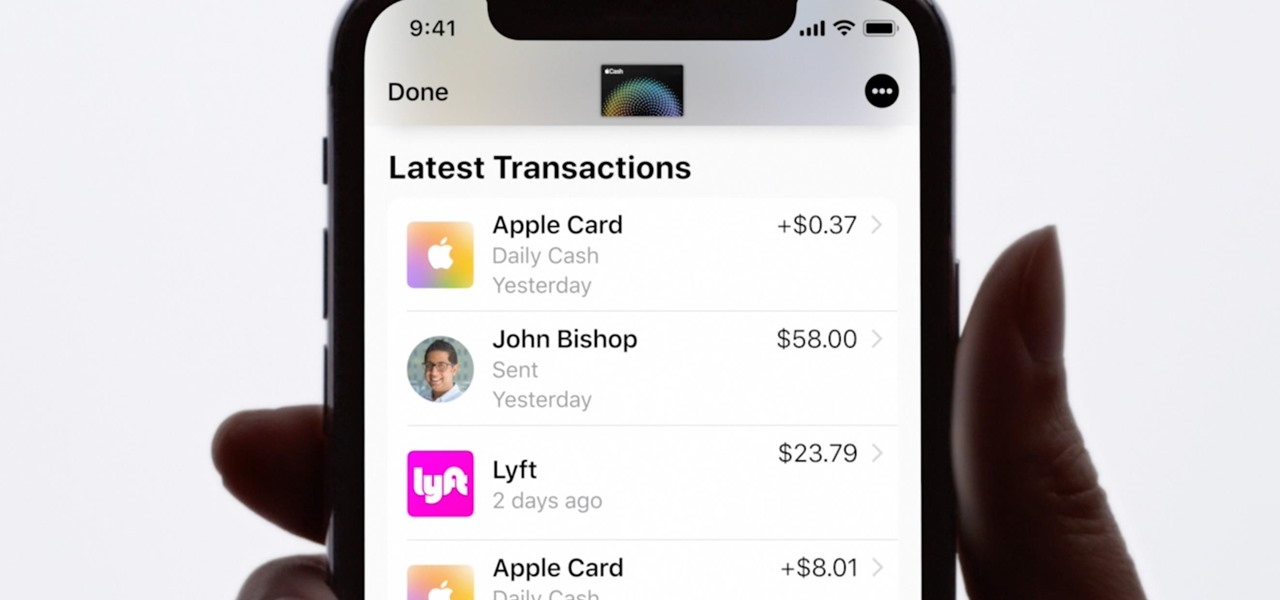
Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

I've been playing around with iOS 7 for a while now, and for the most part, I dig it. It's a nice update for a stale OS, and there are a lot of great new features. But like any good piece of tech, there are a few things to be disliked. Some of these are big issues, and some could be considered nitpicking, but given that I'm fairly used to the older iOS 6 version, they feel big to me. Paper cuts always hurt worse than gashes.

When you don't feel like talking, let your iPhone do all the work. Yes, your iPhone can speak for you, and it works over phone calls and FaceTime calls. It will even work its magic over your iPhone's speaker for in-person conversations. While Apple created this feature to support people who are unable to speak and people who have lost or are losing their speech abilities, anyone can use it.
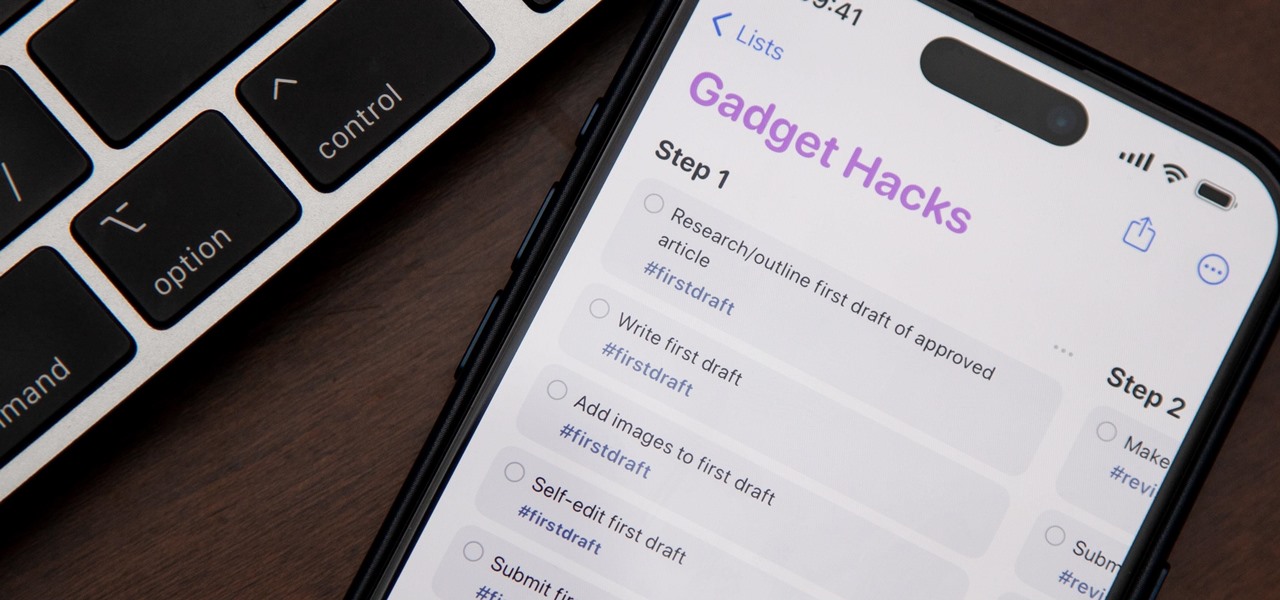
If you're still using a third-party task manager on your iPhone, you might want to check out Apple's updated Reminders app. With each new update, Reminders gets more powerful yet remains one of the simplest task managers to use, and iOS 17's new to-do list features reinforce that statement.

Your iPhone's clipboard can only save one item at a time, so it may seem impossible to retrieve your entire history of copied text, images, and other content. Luckily, there is a workaround you can use to find and copy your past clipboard contents, but you have to implement it first.
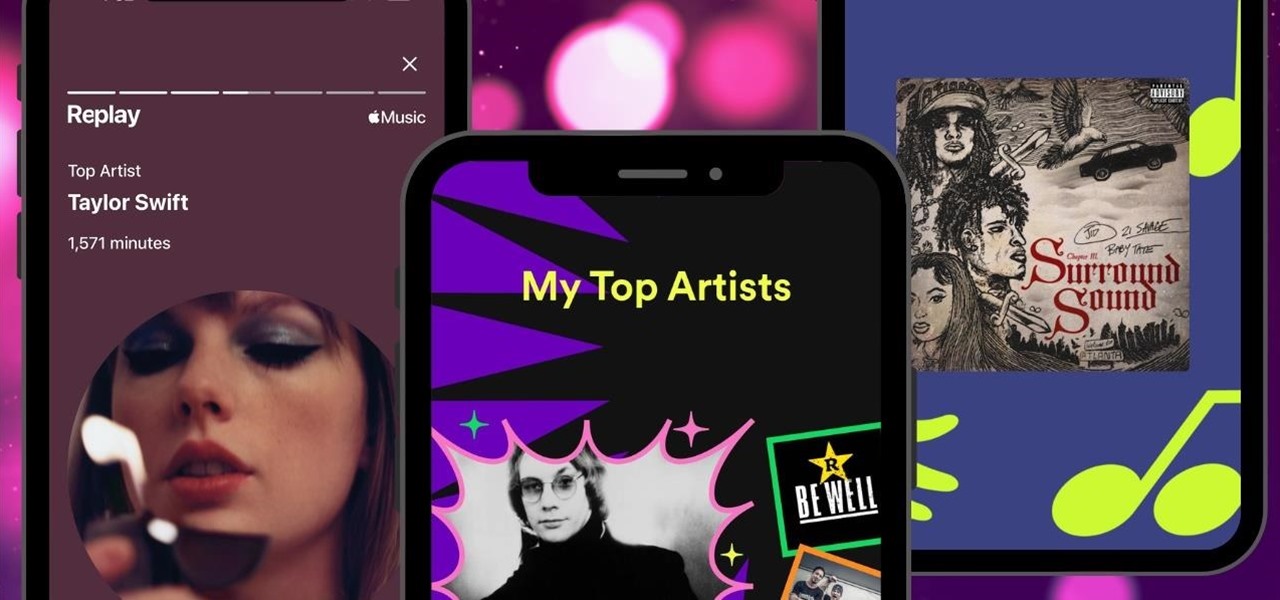
It's that time of year again. No, not the holiday season … the "share your year in music listening" season. And no matter which music streaming service you use, there's a way to find and share (or not share) your activity from 2022.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.

If your iPhone's home screen is littered with apps in no discernible order, and you rely on muscle memory to locate one when you need it, it gets harder with each new app icon added. Folders can help organize the mess, but you can also create your very own app picker or group of app pickers. They act similar to folders but show apps in a list and let you add the same app to multiple app pickers.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Apple just released the second iOS 14.2 public beta (build number 18B5061e) for iPhone today, Wednesday, Sept. 30. The update adds emoji from Emoji 13.0 to iOS for the first time, including smiling face with tear, seal, ninja, anatomical heart, among many others from the collection.

In a similar vein to Facebook's colorful backgrounds for text posts, Instagram has a way to add vivid text-only status updates for your stories. That way, you can conjure up colorful stories that make a statement without even needing to take a photo or video in the first place. And now there are even more fonts to choose from.
It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

While autonomous vehicles are almost assuredly the future of personal transportation, we are likely many years from seeing self-driving cars become as ubiquitous as manually-driven ones, as the auto industry has a myriad of government regulations and other constraints to contend with. Until then, augmented reality is looking like the next big thing in automotive technology.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Welcome back Hackers\Newbies!

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Apple's built-in search on iPhone is an incredibly valuable tool you shouldn't ignore or underutilize, and we're here to show you why. So, buckle in because this list covers hidden and lesser-known Spotlight features that will leave you wondering how you ever lived without Spotlight Search on iOS.

You can play background sounds on your iPhone to help you focus, stay calm, or fall asleep, giving you a personal sound machine wherever you go. Even better, there's a way to set each of your apps to play one of Apple's six ambient soundscapes automatically. When you open the app, its assigned sound plays, then it stops when you exit or switch to another app.

Some apps look great with Dark Mode, and some do not. So when you have system-wide Dark Mode enabled on your iPhone and are using an app that only looks good in Light Mode, you'd normally have to turn the dark appearance off manually, then switch it back on when you leave. But there's a workaround that can automate the process for you.