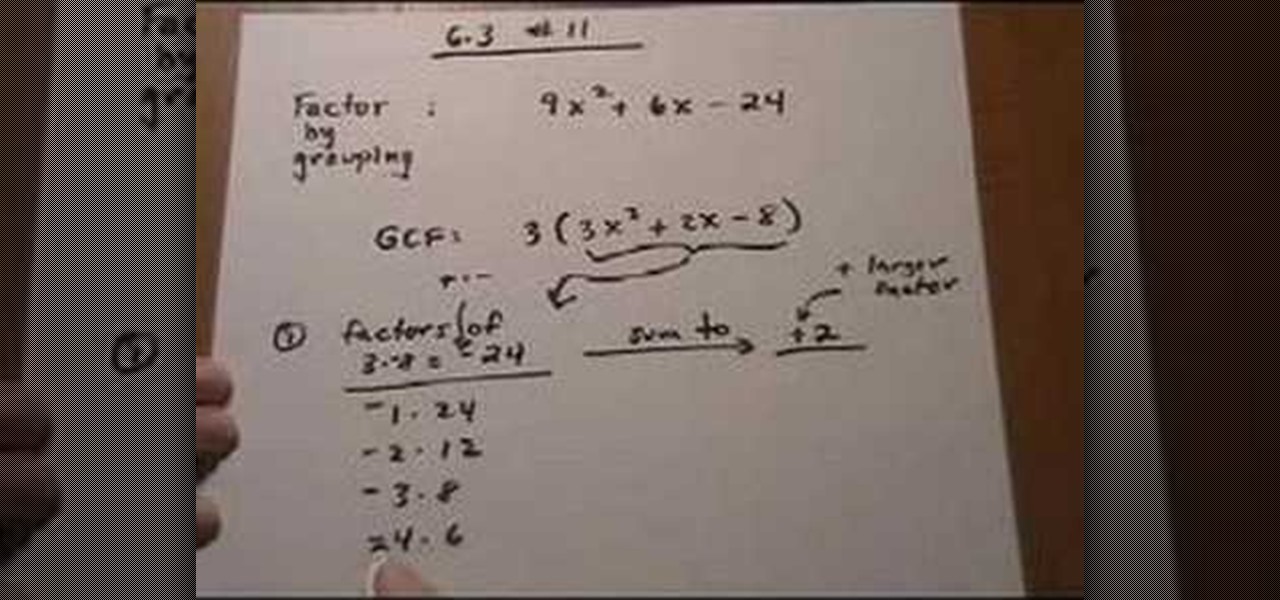One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Augmented reality is becoming a slam dunk for sports entertainment, as leagues, their teams, and their broadcast partners have been quick to adopt AR.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

This guide will cover the SQL Insert statement and how to use it when programming in Delphi.

Learn simple statements in speaking Hindi male/female. Like for male, if you say I walk it would be "main chaltaa hun" in Hindi and "main chaltee hun" for female so main for I chaltaa or chaltee for walk and hun for present tense.

Bettie Page was the ultimate pin up girl. Naturally curvaceous and blessed with batty eyes and full lips, Page was adored by men all over and had women copying her every hairstyle and makeup look. It's no wonder, then, that we still see so many interpretations of her signature pompadour hair look today.

This lesson describes the method to find the factors of a trinomial, which consists of three terms, by grouping. First of all, factor out the greatest common factor (GCF), and write the reduced trinomial in parentheses. Let the terms of the trinomial be written in order of exponent of the variable. For example, 3(3X2+2X-8) trinomial is written in the order of variable, with 3(GCF) factored out. Now identify the coefficient of the first and last terms, for example in this case, it is 3 and 8. ...

They say you have to be in the right place at the right time... how about an elevator? If you happen to run into your ideal employer or business partner, in an elevator – or anywhere else for that matter – you'll have about 30 seconds or less to wow them. Here's how to do it.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Learn how to decorate your graduation cap. Customizing your graduation cap is a way to stand out among the sea of identical, ill-fitting graduation robes.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

After several iterations of the product, Snap is focused on making sure the world knows that its smartglasses can be fashionable.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

Just months after we previewed the augmented reality, volumetric video conferencing powers of Mimesys, the company has undergone a major change — it's now a part of Magic Leap.

After launching its first augmented reality title for Angry Birds on the Magic Leap One, Rovio has doubled back to the platform that made its franchise famous.

The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

Google and Apple are working to enable augmented reality content for the web, but startup 8th Wall has managed to launch a web AR platform that works on mobile browsers now.

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Cosmetics maker Coty is hanging an augmented reality Magic Mirror on the wall of its Bourjois boutique in Paris that will tell customers which shade of makeup will make them the fairest of them all.

In the weeks following Google's AR toolkit launch last month, the availability of quality ARCore apps has been somewhat limited. That changed on Tuesday, as a flurry of new and updated apps arrived on the Play Store, including some AR experiences available exclusively on Android.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

Nowadays, with the convenience of online shopping, brick-and-mortar retailers and malls have to work harder to draw shoppers to stores. This year, many of them are turning to augmented reality for assistance.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Augmented reality sells, but who's buying? Over the past week, two companies made executive hires to capitalize on the growth of augmented reality as a service to sell to other businesses. Meanwhile, two companies joined forces to offer augmented reality tools to headset makers and content providers.