Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

There's perhaps no statement more classic (and more annoying) than the "but" sentence. We've all heard it before: "I love you, but..."
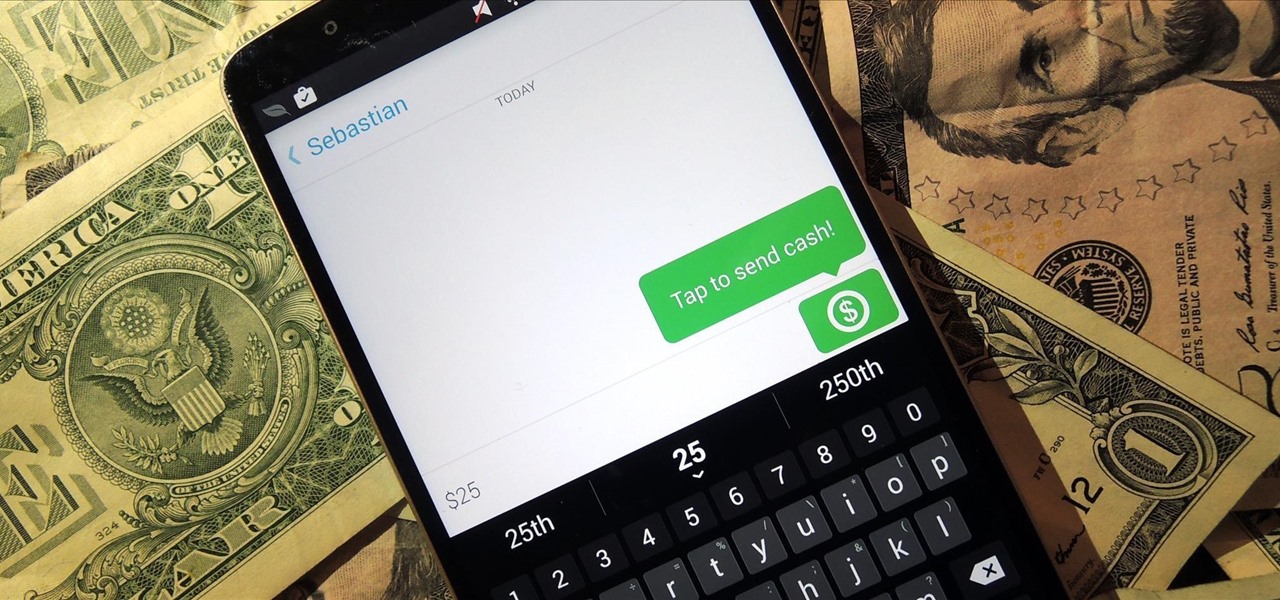
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

What happens when you accidentally delete a photo or video from your iPad or iPhone? How do you get it back?

Sprint and T-Mobile have agreed to a $31.6 billion deal that, if it gets through federal regulators—which is far from a sure bet—would create a formidable carrier to really compete against AT&T and Verizon. The deal comes packaged with a $1 billion "breakup" fee that Sprint would have to pay T-Mobile in the event the deal does not go through. After the deal, Deutsche Telekom, which owns about 67% of T-Mobile, would maintain a 20% ownership stake.

"Millions of us have smartphones with the power to speed up research that will benefit billions of people around the world." - Professor Francois Grey

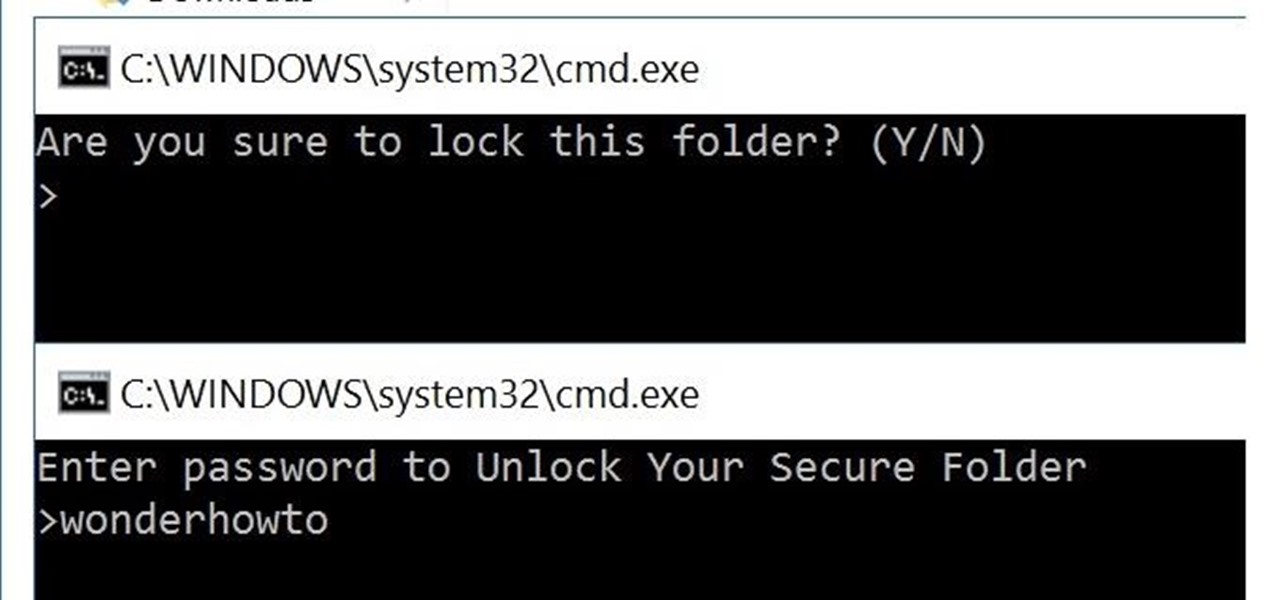
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

There have been hundreds of reports of users hearing a grinding noise when they place a disc into their brand new Xbox One video game consoles. To prove it, here is an awesomely sad compilation of Xbox One owners having the issue.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to release its own real-time picture and video messaging application, aptly titled Poke. One of the biggest criticisms (besides the wave of recent security issues) of Snapchat is that even though the messages self destruct and ...

Later today, the Olympics are kicking off in London on NBC and its partner stations. However, if you don't have cable or a television with some good reception—or if you'd rather just follow the events on-the-go or at your desk—you're not out of luck. Photo by Locog

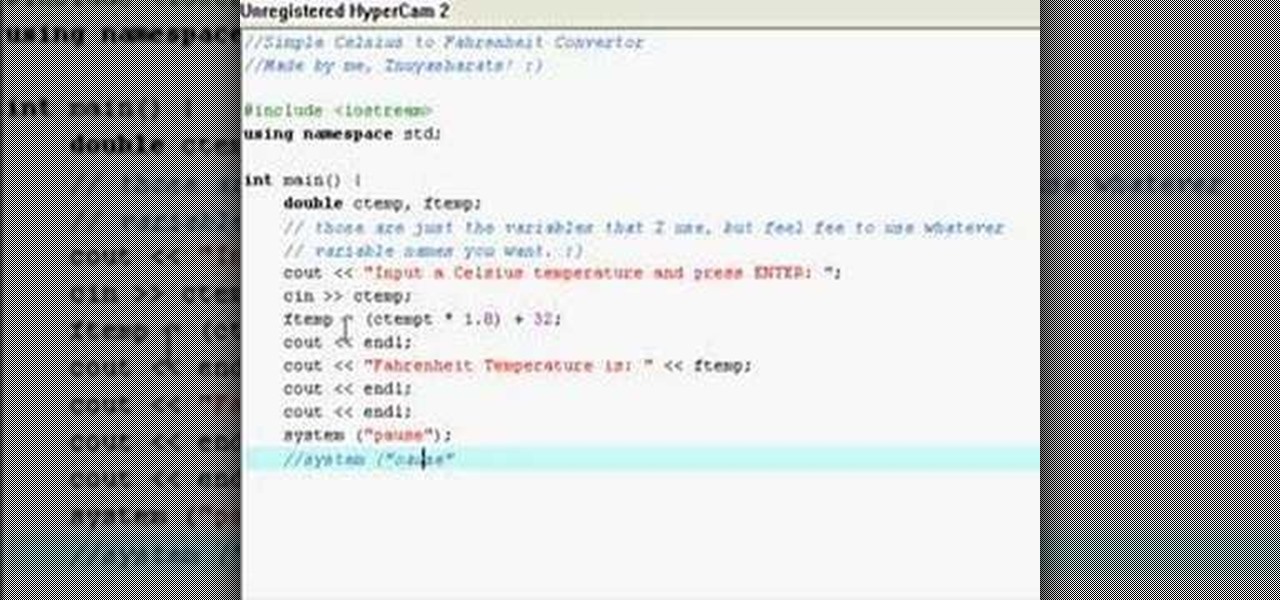
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

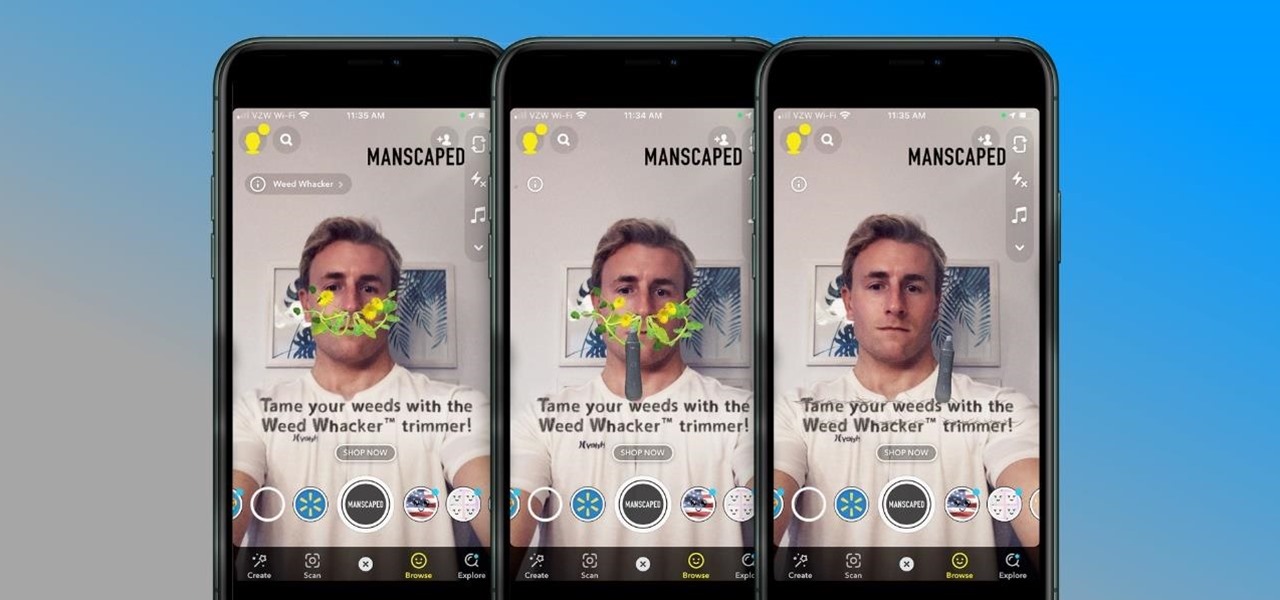
If you're a man and subscribe to podcasts or YouTube channels that cater to masculine interests, then you've almost certainly encountered sponsorships from Manscaped. And that means I don't have to explain what the company is selling you (for the uninitiated, it's a company dedicated to helping you trim your body hair—most notably, your nether regions, in addition to other areas).

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Welcome back, my greenhorn hackers!

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

Alongside Sesame Street, the Dr. Seuss universe has been a constant presence in the formative years of several generations of children in the US.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

As augmented reality continues its collision course with mainstream adoption, the technology will now have a role in one of the most anticipated boxing matches of the year.