Having already solved for functionality and form factor, Nreal appears poised to pull ahead of its consumer smartglasses competition as the third piece of the puzzle now falls into place.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Unless you're one of the world's top golfers, there's a good chance you are not stepping onto the fairways of Pebble Beach Golf Links this weekend.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

This card is totally gorgeous, it has a bit of everything and I can't say it is going to be a quick card but I can say it is a 'Humdinger!' and anyone who receives it will keep it forever.. The card has a paper folded quilt style background made from the Anna Griffin Paper Tricks2 kit and this creates something stunning for the 3D flowers and sentiment to sit on, as well as the glitzy bow & embellishment.. perfect for something large and if you ever wanted a card to make a statement, then thi...

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Like many smartphones nowadays, your Samsung Galaxy S4 comes bundled with a headset for you to listen to music, watch videos without disturbing others, and even make phone calls. I personally only use it for music, whether it's Play Music, Pandora, or streaming from YouTube.

Today is Friday, and I cannot wait to sit back and crack open a nice cool Smirnoff Ice when I get home. If you lost respect for me after that statement, you have only gained mine.

Your bike is your prized possession - it is your mode of transportation, your exercise and definitely your fashion statement. But, just because you love your bike, doesn't mean you want to destroy your outfit by riding it. Follow this tutorial and add a pretty mesh barrier to your back wheel and stop ripping and soiling your skirts.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

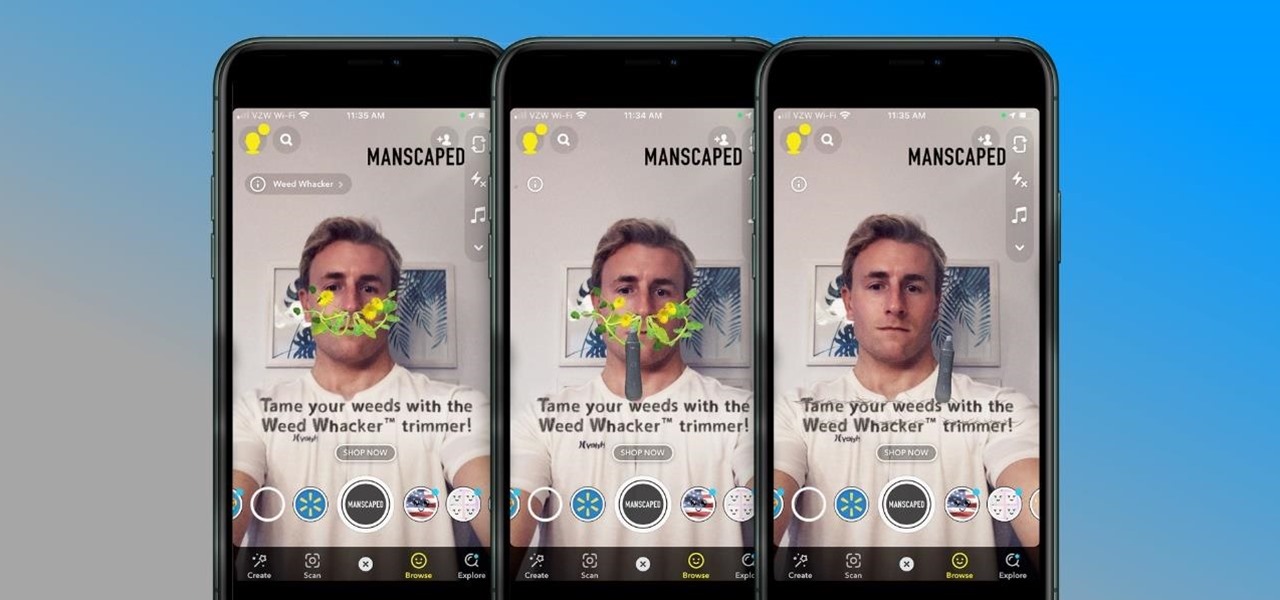
If you're a man and subscribe to podcasts or YouTube channels that cater to masculine interests, then you've almost certainly encountered sponsorships from Manscaped. And that means I don't have to explain what the company is selling you (for the uninitiated, it's a company dedicated to helping you trim your body hair—most notably, your nether regions, in addition to other areas).

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

After awarding $410 million to the company that supplies it with VCSELs and LiDAR sensors, Apple has made another strategic investment into a company that may contribute to future augmented reality hardware innovations.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

While the rest of the world is scrambling to figure out how to adopt augmented reality and VR tools for remote meetings, one company is building its war chest to serve the growing space of corporate clients who need this kind of immersive computing training.

Twitter replies have traditionally acted like public spaces. Once a tweet is out there, pretty much anyone can reply to it. In some cases, that makes for good discussion. In others, it can lead to disaster, abuse, and harassment. Twitter's looking to change that by giving you more control over who can reply to tweets.

With big-name tech companies like Apple and Facebook gearing up to push out their own smartglasses in the coming years, engineering conglomerate Bosch has been working on the optical components that could help the competition catch up.

Less than a month after the worldwide launch of HoloLens 2, call center consultant BellSystem24 has already prepared an augmented reality solution for one of its clients.

The end of year surprises keep on flowing from the Plantation, Florida offices of Magic Leap. This time, it's yet another game from the company's old partner Insomniac Games, and it's called Strangelets.