Just days after the launch of Google Poly, the marketplace for 3D virtual objects that developers can use for augmented and virtual reality apps, SketchFab, the current leader in the space, is firing back with a major enhancement to its platform.

While Snap's third quarter financial reports disappointed Wall Street, China's Tencent took the opportunity to expand its investment in the social media company.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

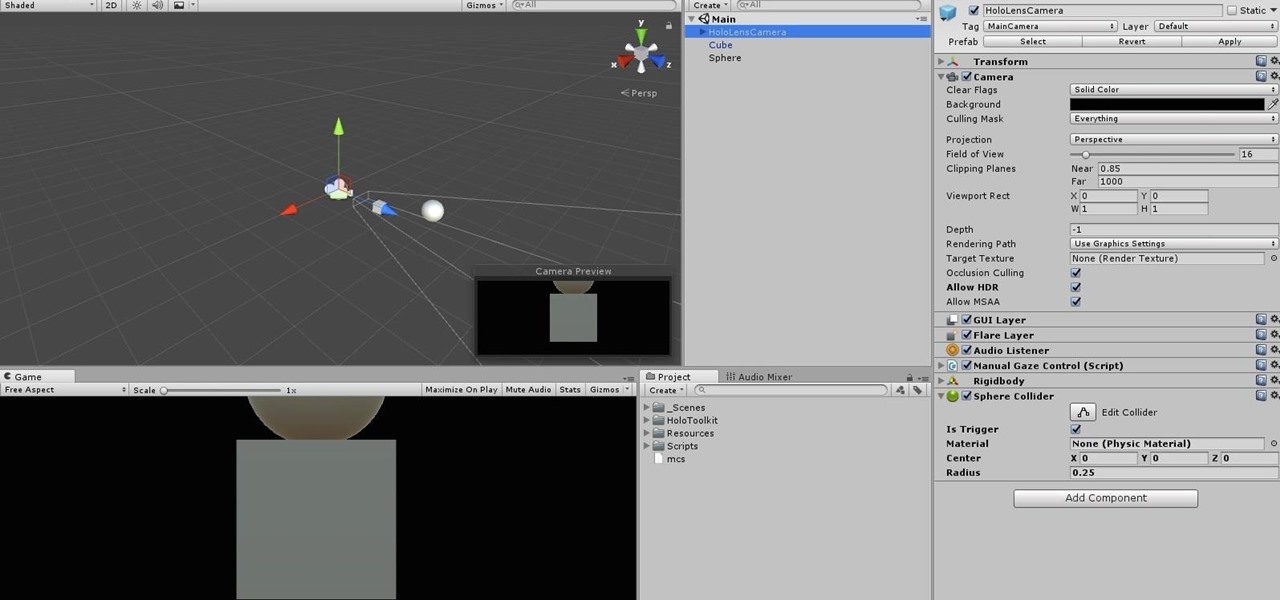
In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.

Mobile game companies Hit Point Studios and Legacy Games have adapted their Color BlastAR augmented reality game for iOS with the ARKit platform.

With the official release of iOS 11, the availability of an app that uses the much-hyped ARKit platform to place virtual furniture in one's home was expected.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

IKEA can help customers determine if a couch fits in their living room, but who is going to help them figure out if their new SUV will fit in the garage?

If giving truly is better than receiving, then The Box AR should be the best ARKit app available when iOS 11 releases next week.

When it comes to finding lost things, the joke goes that it's always in the last place you look. With an assist from ARKit, Pixie can make your iPhone the first and last place you look for that missing item.

Ahead of the highly-anticipated iPhone unveiling and iOS 11 launch, augmented reality developer Scope AR has confirmed that the iOS version of Remote AR, their live support video calling app, will support iOS 11 and ARKit immediately.

It seems like it was just last week that AMC and Next Games unveiled their location-based zombie game based on hit TV series The Walking Dead. (Wait, actually it was just last week.)

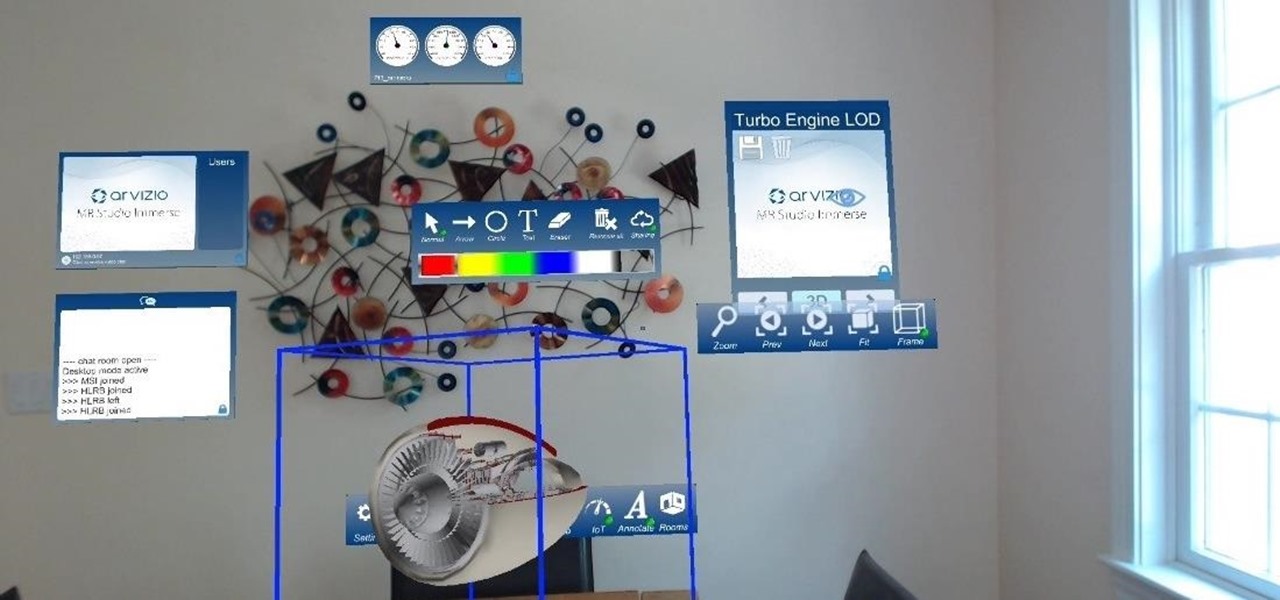
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

Thanks to augmented reality, fashion companies can let customers try on cosmetics, clothes, more cosmetics, and sunglasses from the comfort of their homes and through the non-judgmental eyes of their smartphone camera.

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

Furniture arranging apps have been rolling out on different platforms for a while now thanks, in no small part, to augmented reality.

Luden.io just revealed more details about their mobile game "AR Tribe," made using Apple's ARKit. The company has previously focused on VR games such as InMind 2 and VRobot. This is the company's first attempt at AR, and it looks like it's going to be pretty cool.

Yes, you read that headline correctly. Spotify now has 140 million monthly active users, which is up from the 126 million users on the streaming service last year. (If you're wondering, Mexico's population is currently 127 million.)

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

A new feature of Google's Gboard for Android lets users doodle an emoji in order to find it. The change was part of a few updates introduced earlier today.

Driverless partnerships continue to appear as Continental AG, leading German automotive manufacturing company, has signed a strategic cooperation agreement with global electric startup, NIO. The goal of this partnership is to research, share, and develop autonomous technology, among other developments.

UPDATE: It was previously reported that the OnePlus 3T 128 GB in Gunmetal would be discontinued. GSM Arena received an official rebuttal from the company which noted that the phone is not discontinued, but rather, out of stock. Though, it seems like the company has more of a problem keeping track with what its reps report, rather than its phone supply.

It looks like Samsung's Bixby finally got one up on Apple's Siri — when it comes to which virtual assistant can spit better rhymes, that is. Mhm, that's right. It's a rap battle between one AI and another, and Siri just can't spit.

When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

OnePlus just unveiled a new version of their popular OnePlus 3T—a limited edition all-black "colette" version for the boutique's 20th anniversary today. The slick device will feature the iconic colette logo on the back.

A 5-year-old girl was injured after the battery in another Samsung phone exploded in China. The Samsung Note 4 was reportedly charging next to the sleeping girl when it blew up in her Guizhou-based home.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

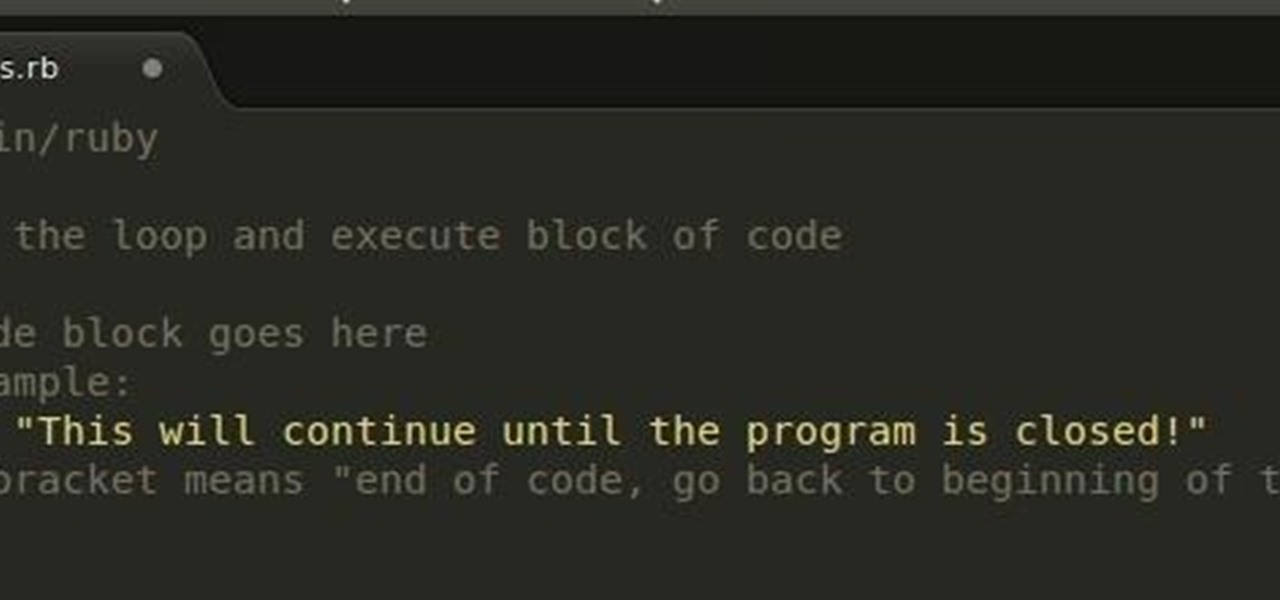
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

In a long-awaited move, the popular messaging platform WhatsApp has finally made its official web debut. Desktop and laptop owners will be happy to know that they can now message their favorite contacts directly from their computers, without the need to install additional apps.

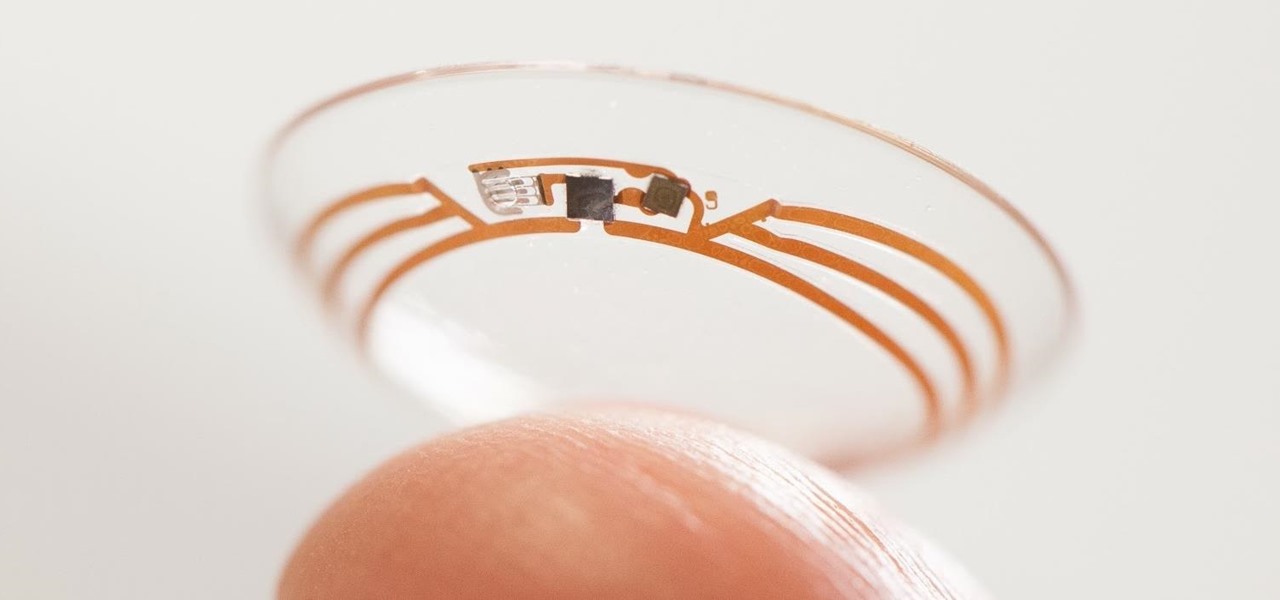
Warning: Google wants to take control of your sight. While this statement isn't (or is) true, it doesn't change the fact that Google is partnering up with Novartis to create contact lenses.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.