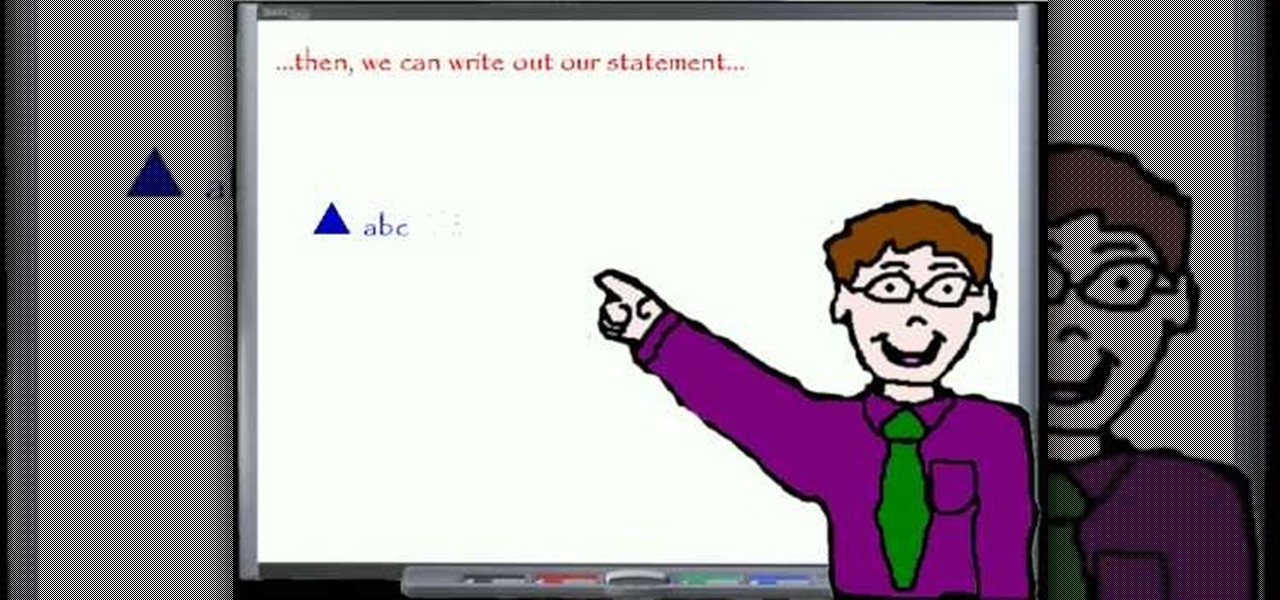
In this "Math Made Easy" geometry episode, you learn how to prove that two triangles are congruent (equal) by using the "side-side-side" evidence. By using "side-side-side" to prove that two triangles are congruent, you are stating that all the respective corresponding sides of two triangles are equal in length thus proving the triangles are congruent. The narrator in this tutorial provides you with definitions about statements, proofs, and congruency. This becomes useful when setting up a ta...

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.
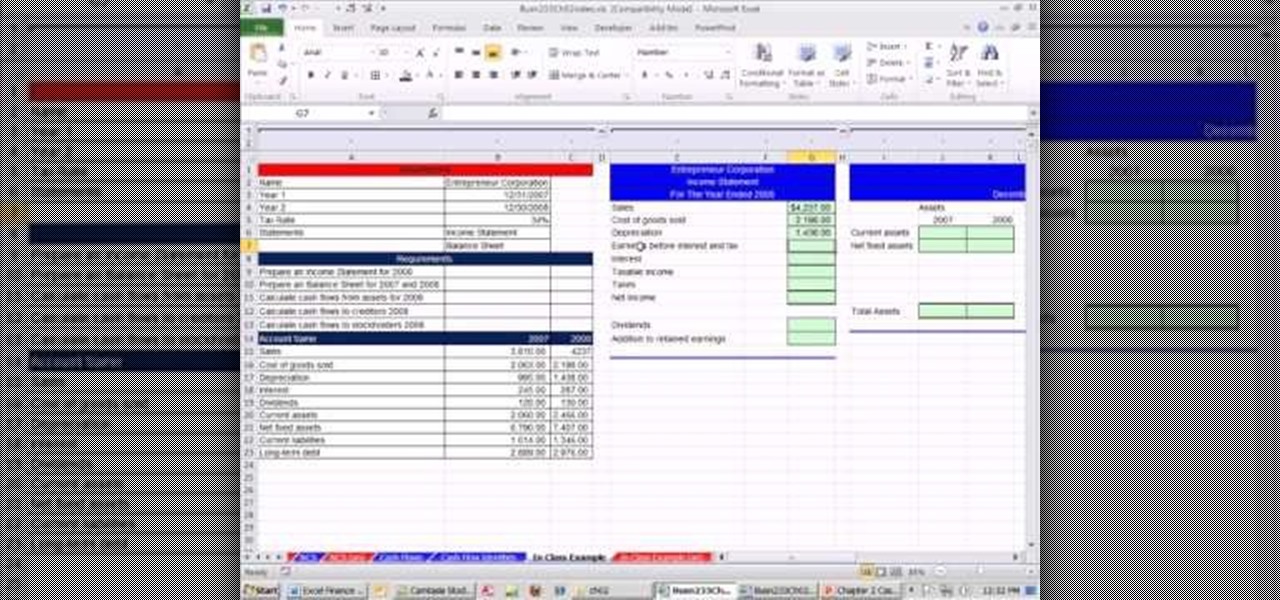
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 11th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to calculate cash flow from assets, cash flow to creditors and cash flow to shareholders using accounting financial statements.
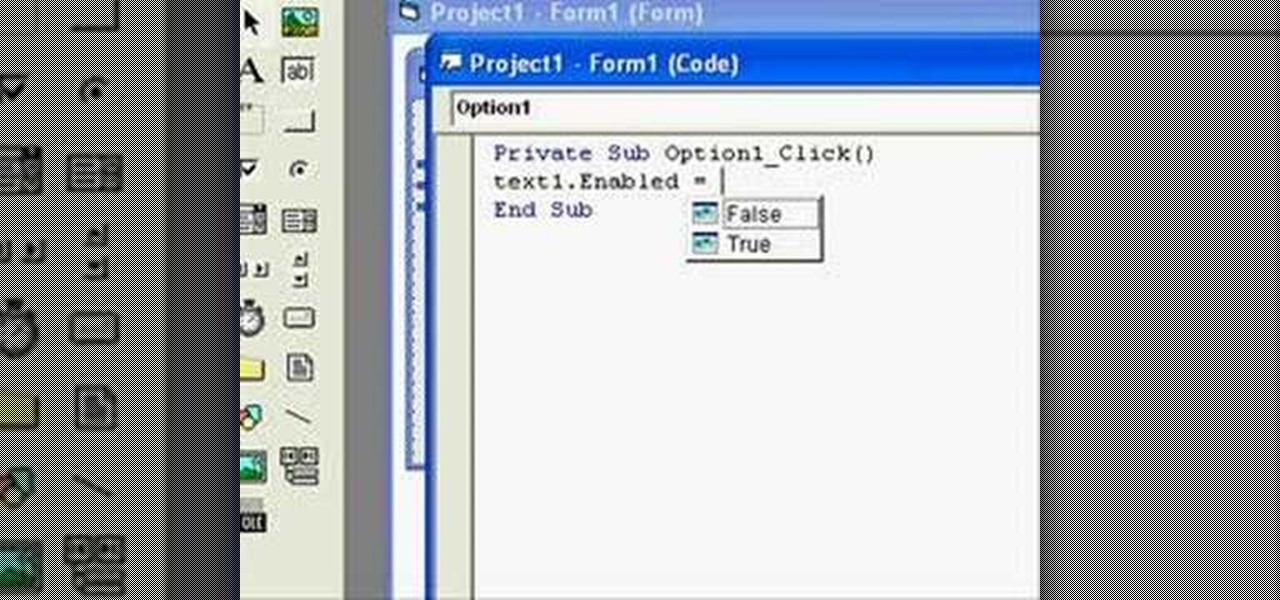
In this clip, you'll learn how to use "True" and "False" statements in your VB code. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

If you've ever heard of a little artist named Banksy, you know that street art has the unique power of combining whimsy with sociopolitical commentary, all done with mind-blowing efficiency.

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program conditionals - if, if/then, and if/else statements - in GlovePie.

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

In this tutorial, we learn how to speak English with conditionals. Conditional statements need special attention and usually start with the word "if". An example of a conditional statement is "if you want, we'll go out to dinner". This has two parts, a condition, and a result. The condition is expressed by "if". To report them, don't change the verbs unless you're dealing with a real condition. Look and see if verb tenses can change depending on how the sentence is structured. Try to remember...

The instructor in this video uses humor to teach people math, which is not a favorite subject for many. The video goes on to teach the students in the video different ways to cut the conic sections into different shapes. The teacher then focuses on parabolas and defines the formulas. The formula is y = x^2. The rest of the video dissects the equation breaking it down into much more meaningful statements so that the average human being who is not very good at math can understand the equation. ...

In this video, Robert Ahdoot becomes "surfer dude" and shows us the ways of deductive reasoning, as relating to geometry. He begins with a simple example of a syllogism, taking two premises and using them to form a conclusion. This is called the Law of Syllogism. This concept is then used for geometric statements. If two angles are complementary, they sum to 90 degrees. If two angles sum to 90 degrees, then they are acute. By the law taught, it can be said that if two angles are complementary...

In this tutorial the instructor shows how to solve percent equations. The general form of a percent equations is that a is b% of c. As there can be three kinds of variables a, b, c, the questions involving percent equations can be of three types having one of the three variables unknown. These kind of percent statements can be solved easily by setting up an equation. So, to convert percent statement into a equation replace the unknown term with n, the 'is' term with equals sign and the '%' si...

This explains how to use two-note chords when playing rhythm guitar. A step by step video tutorial that will show you how to mix two note melodic ideas with double stops and throwing in a single note melody. Andrew Wasson from Creative Guitar Studio put together a melodic phrase and a minus one track that will be available to download from his site. Andrew goes over all the techniques you need to help you learn this phrase and teaches them to you with simple instructions. These double stop an...

We can’t really tell you to become a mind reader. But we can teach you how to make some impressively accurate guesses, based on psychics’ tricks of the trade. You will need a pleasant demeanor, a keen eye, leading statements, listening skills, knowledge of the human nature, and the ability to read body language. This instructional tutorial covers tricks like the Barnum Reading and interpreting body language. Watch this video tutorial and learn how to read people's minds just like a psychic, o...

Being organized and using good formatting in your CSS files can save you lots of time and frustration during your development process and especially during troubleshooting. The multi-line format makes it easy to browse attributes but makes your file vertically very long. The single-line format keeps your file vertically short which is nice for browsing selectors, but it's harder to browse attributes. You can also choose how you want to group your CSS website statements. Do you do it by sectio...

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

Learn simple statements in speaking Hindi male/female. Like for male, if you say I walk it would be "main chaltaa hun" in Hindi and "main chaltee hun" for female so main for I chaltaa or chaltee for walk and hun for present tense.

They say you have to be in the right place at the right time... how about an elevator? If you happen to run into your ideal employer or business partner, in an elevator – or anywhere else for that matter – you'll have about 30 seconds or less to wow them. Here's how to do it.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

An English teacher shows how to use "either" and "neither" to make negative statements. These words are the opposite of "so" and "too."

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

I'm back! We're learning Java WhileLoops today.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)