In this video Tanky shows you how to make a LEGO bookcase. He details each step of how to create a small LEGO bookcase, starting from the base and building one level at a time. He Suggests connecting all parts in the final step in order to ensure the bookcase does not fall apart. He then inserts books into each shelf to create a filled bookcase that displays twenty books on two levels of shelf. The LEGO books fit in well. If you follow the steps in this video you will have a realistic LEGO bo...

This video lesson will show you how to breastfeed when you are just starting out. Breastfeeding offers babies and mothers remarkable health benefits that are lifelong. A new born baby is ready to breastfeed. But, it may not come naturally to all babies. A baby is born well fed, but, it is a good idea to bring the baby to the mother’s breast as soon as she is born. This will help the baby to connect with the taste and smell easily. A mother’s breast should be the first thing to reach a baby’s ...

This video is going to show you how to create purple felt flowers for your children or a nice little gift. The items you will need are an 18in piece of tread doubled knotted at the end, hot glue gun, a needle, a pom pom, and felt cut into the shapes you want to make your flowers out of. You want to begin by take the thread attached to the needle and doing a running stitch through the felt. Pull the thread as much as possible and then take the two ends and do a whip stitch to connect the two e...

Learn the right way to draw a wolf with its full body, by watching this video. The artist begins by drawing three circles faintly and connecting them with a line, representing the head and body of the wolf. Next, the skeletal structures of the legs are outlined. The tail and ears are faintly outlined next. The artist then begins outlining the face in detail, adding the eyes, nose, mouth, ears etc to the wolf’s head. The body is now outlined adding rough edges to indicate fur. The legs of the ...

In this video tutorial, viewers learn how to remove and replace vinyl siding. Users will need a siding removal tool (zip tool). Insert this tool beneath the bottom edge of the overlap and pull down while sliding the tool horizontally. Remove the nails underneath and simply pull down the siding. Now measure the length of the siding. With the new siding, connect it on the exterior wall and reinforce it with some nails. This video will help those viewers who need to learn how to replace a vinyl ...

iPodTouchHelping teaches you how to Jailbreak version 3.1.2 iPhone and iPod using Blackra1n. Connect your iPod or iPhone to your computer and make sure it appears in iTunes. You need to go to Blackra1n and click on the Windows icon. Download the program and run it. Click Make it rain in the Blackra1n application. You might get some error messages, just ignore them. The process will finish and the device will reboot. You will see the Blackra1n icon on your device, tap that and select Cydia and...

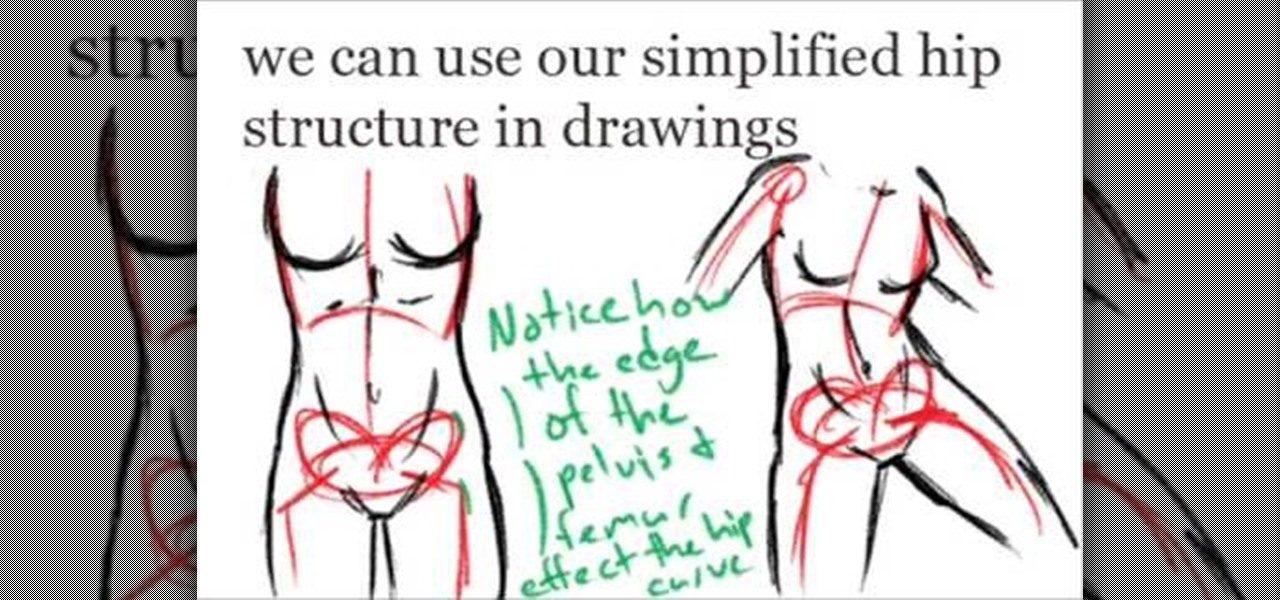
This video, which gives tips on drawing realistic hips, is helpful to people learning to draw the human form. The video starts by showing examples of bad drawings of hips and explains that these are how you should not be drawing them. It then shows a realistic black line picture of the pelvis bone on which the presenter has drawn a simplified version of it in a contrasting red color. He gives a simple description of his drawing, saying it is like an oval with butterfly wings coming from it. H...

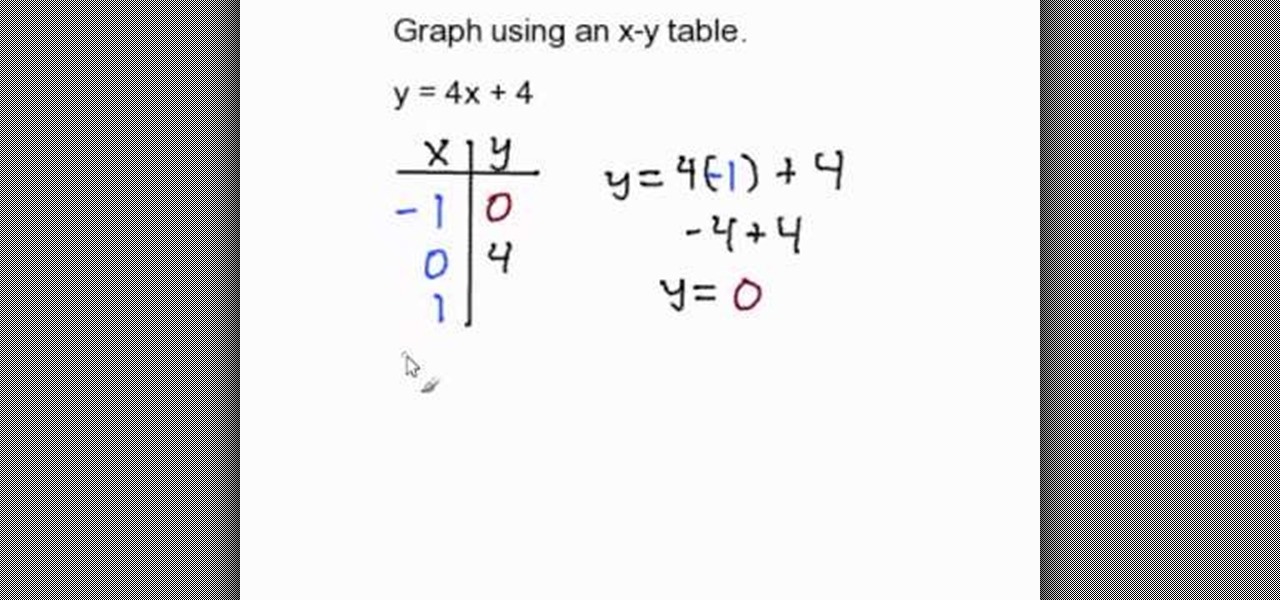
In this video the author shows how to graph using an X-Y table. He shows how to do this with a sample equation. He builds a table of x, y values where he takes sample values for x like -1, 0, 1 and now he substitutes these values in the equation of the line and obtains the corresponding y values. Now finally he has an x, y value table which now he shows how to plot it on a coordinate plane. He plots all the three pairs on the graph and connects them with a line finally obtaining the resultant...

Ever hear of MoneyWell? There's a whole slew of personal budgeting softwares available today, but figuring out which one is right for you is extremely difficult. This video tutorial will help you understand the concepts behind MoneyWell and how easy it is to manage your cash flow.

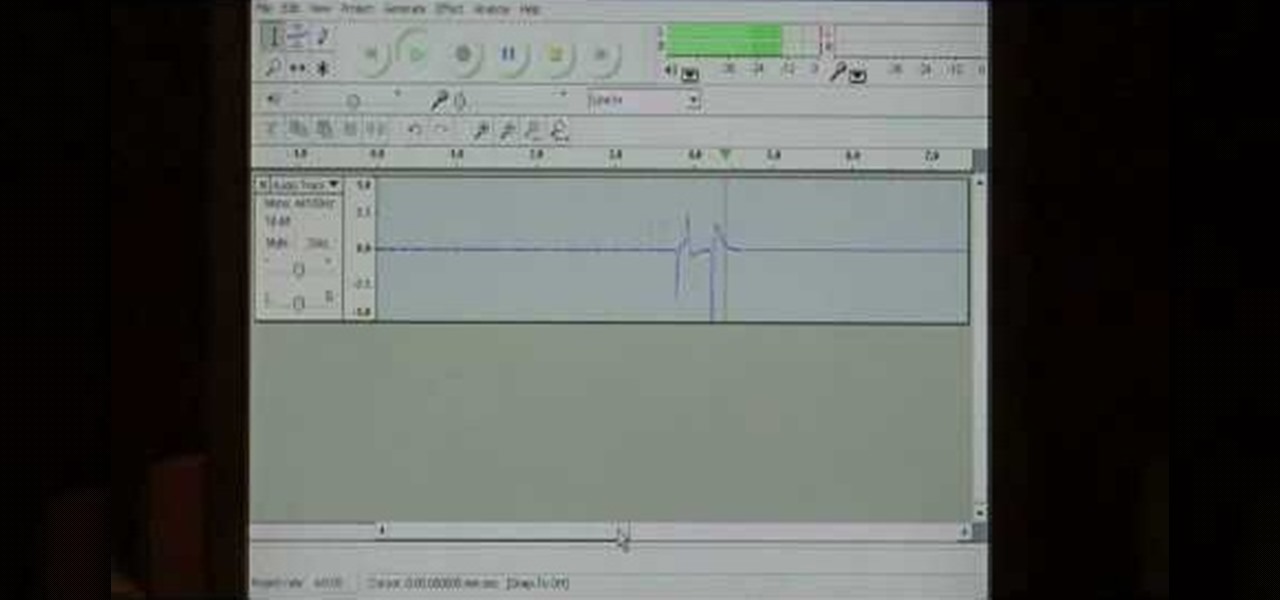
Dave Andrews gives a simple overview of how to take a cassette tape and convert it to a CD using Audacity. First you will need a cassette tape player, like a boom box, with a microphone jack. Then you'll want to download the free program called Audacity. To begin recording music from the cassette tape simply press the record button on the audacity application while you press the play button on the boom box. You'll want to make sure the audio cable is connected from the boom box to the PC. Fin...

Most people own a Wii system, or at least have seen the infamous Wiimote that serves as the controller for the console. What most people have overlooked is that this handy piece of technology can be set to work on PC. Surf the web or scroll through photo albums without the need for a mouse as the narrator takes you through an easy to follow, visual guide how to install these programs on your computer. You can even use the remote just like a classic NES controller for emulators on your compute...

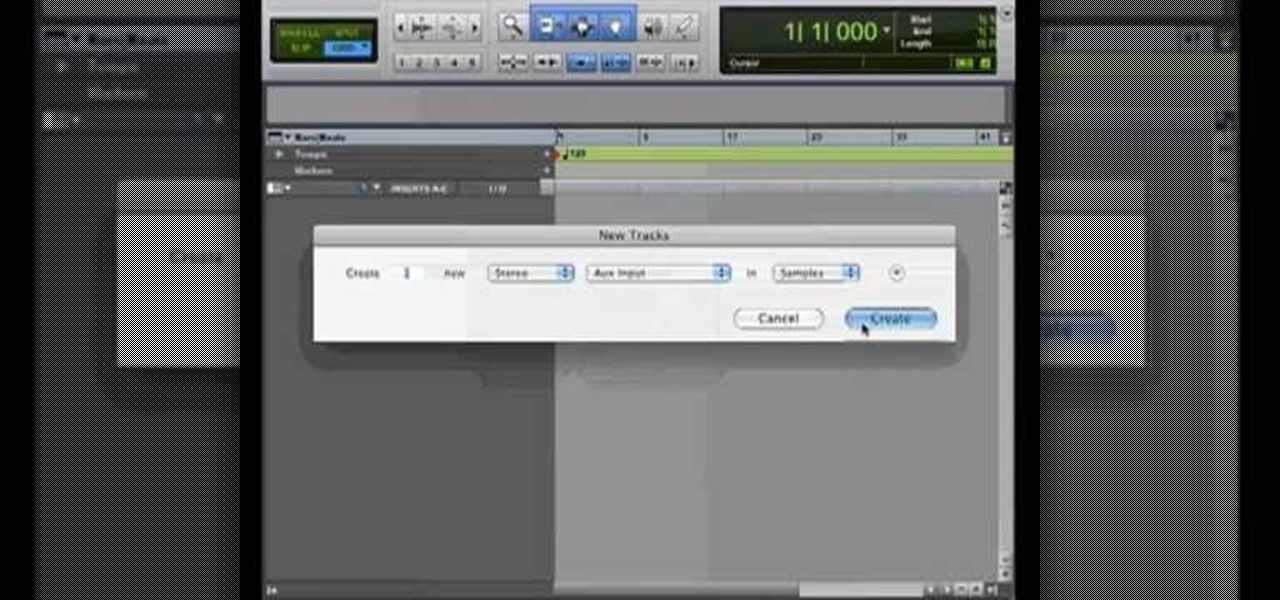
After finally completing a rhythm section using Reason software, you may want to rewire using Protools. First decide how to feed Reason into Protools. The best, would be to re-patch individually into Protools, however the demo here shows a simpler approach that will be easier for anyone to use. First and foremost, Shut down Reason and boot a new session in Protools. Then add an AUX input and instantiate the rewire plug-in to connect to Reason. Make sure the main Reason stereo is feeding track...

Does your calculator just crunch numbers? Boring no longer. Mod your calculator into a fun video game console by installing Super Mario.

This video covers the steps needed to convert a VHS video tape to DVD. You will need to purchase a video capture card in order to do this project. Connect your VCR to your computer using a coaxial cable. This is a great way to preserve and restore old VHS tapes by digitizing them.

This video explains how to make an Origami Icosahedron (designed by Heinz Strobl) using 50 strips of paper. You need 20 strips of a single color for the triangles and 30 of a contrasting color to connect the triangles.

Watch this instructional quilting video to quilt a pantograph pattern with a longarm sewing machine. A pantograph is a mechanical linkage connected in a special manner so that the movement of one specified point is an amplified version of the movement of another point. If a a line drawing is traced by the first point, an enlarged copy will be drawn by a pen fixed to the other. Take note of the proper way to stand and move one's body when stitching out pantographs. It's best not to move one's ...

Taking a cue from Apple and its Health app for iOS, Google has created a central hub to collect health and fitness data on your Android device. With it, you can share and sync health and fitness data, such as steps, heart rate, water intake, sleep quality, and calories burned, between different apps and devices and use your favorite app to view all the information.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

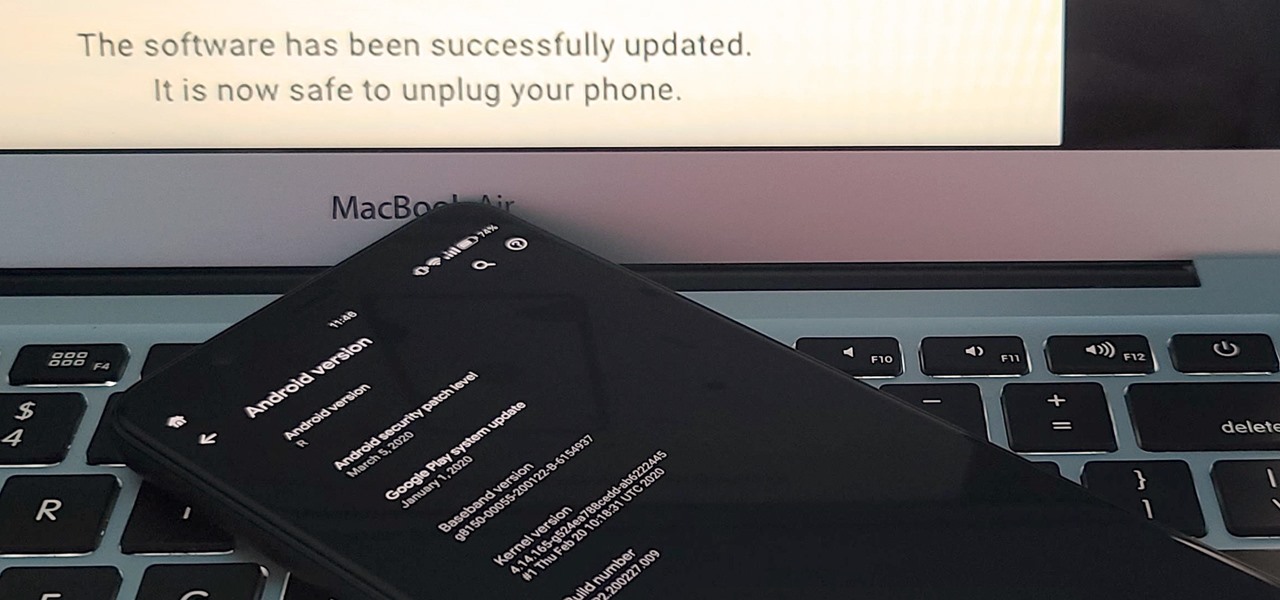
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.

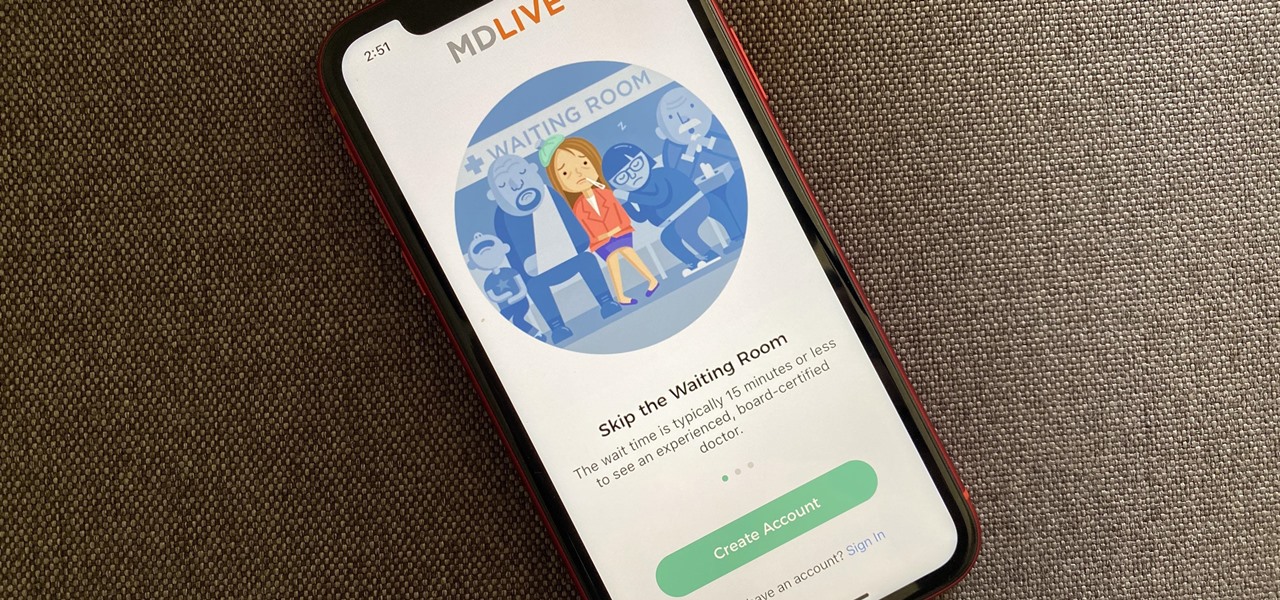
The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

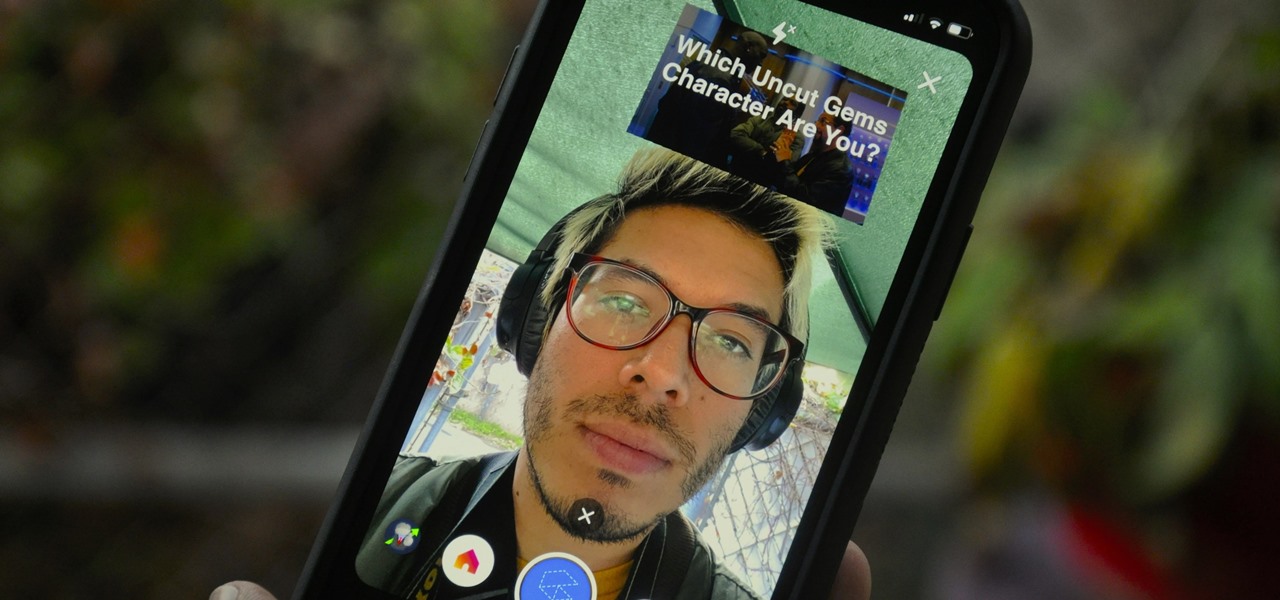
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

It's no secret that Snapchat has upped its AR game as of late. They're competing neck-and-neck with the likes of Instagram to see who can out-cool the other. Snap Inc's latest endeavor, 3D Paint, aims to steal the AR spotlight once again by giving you the ability to draw over the real world.

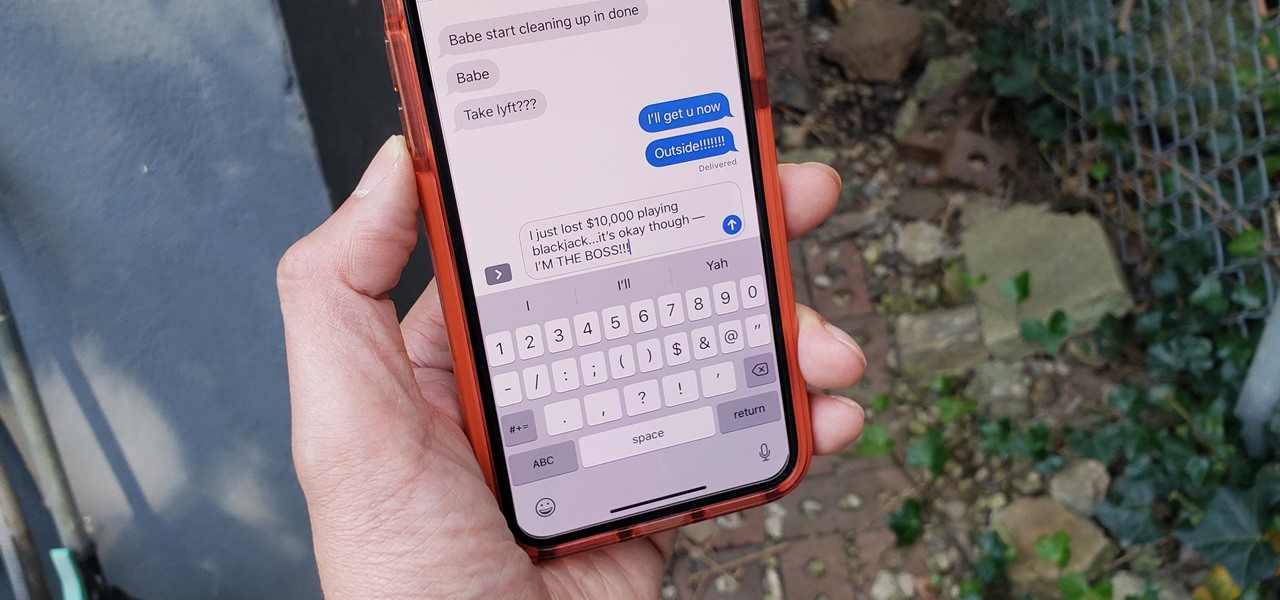
There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

When shooting video on your phone, you have two cameras at your disposal, the rear camera and the selfie camera, and you can switch freely between the two. As for microphones, you may have more than one but, unlike with the cameras, it's not easy to switch between them. Filmic Pro solves this problem by isolating the mics so you can choose the best option for the audio track.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

There has never been a better time to be a movie enthusiast, with more options now than ever to buy high-quality digital titles to watch on almost any device you own. That said, all those choices can lead to your movie collection scattered across different apps and services. What you need is a way to combine those movies into one, convenient location — and there's an answer to that.

On Friday, at IFA 2018 in Berlin, Samsung invited attendees into the residence of Family Guy's Griffin family to learn all about its "smart home" products via augmented reality.

Google's ARCore team is staying busy, as evidenced by yet another update of its augmented reality toolkit.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

One of the leading chipmakers for smartphones is getting ready to announce a new processor made specifically for augmented and virtual reality headsets.

Snap Inc. added stickers back in 2016 to its Snapchat app, and it has been building on that functionality ever since. Now, you can add Bitmojis and even GIFs from Giphy to your photos and videos. Even better, you can pin any of these stickers to background items or moving subjects when sharing videos. That means stickers aren't pinned to the screen itself but to a real-world location.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

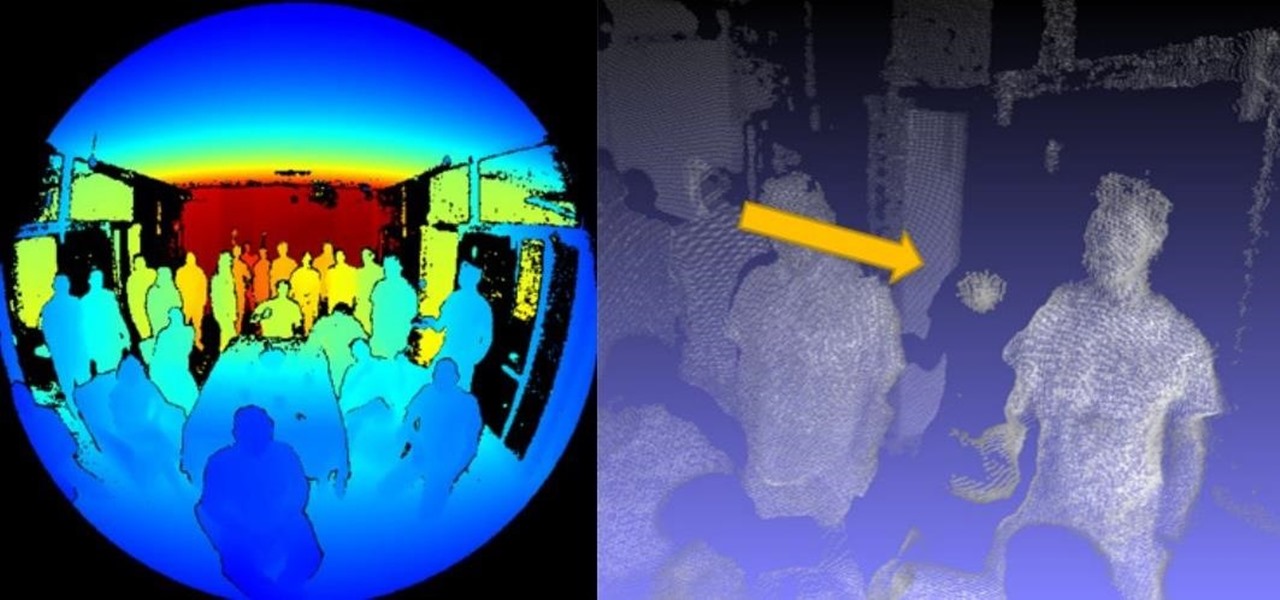
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.