Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.
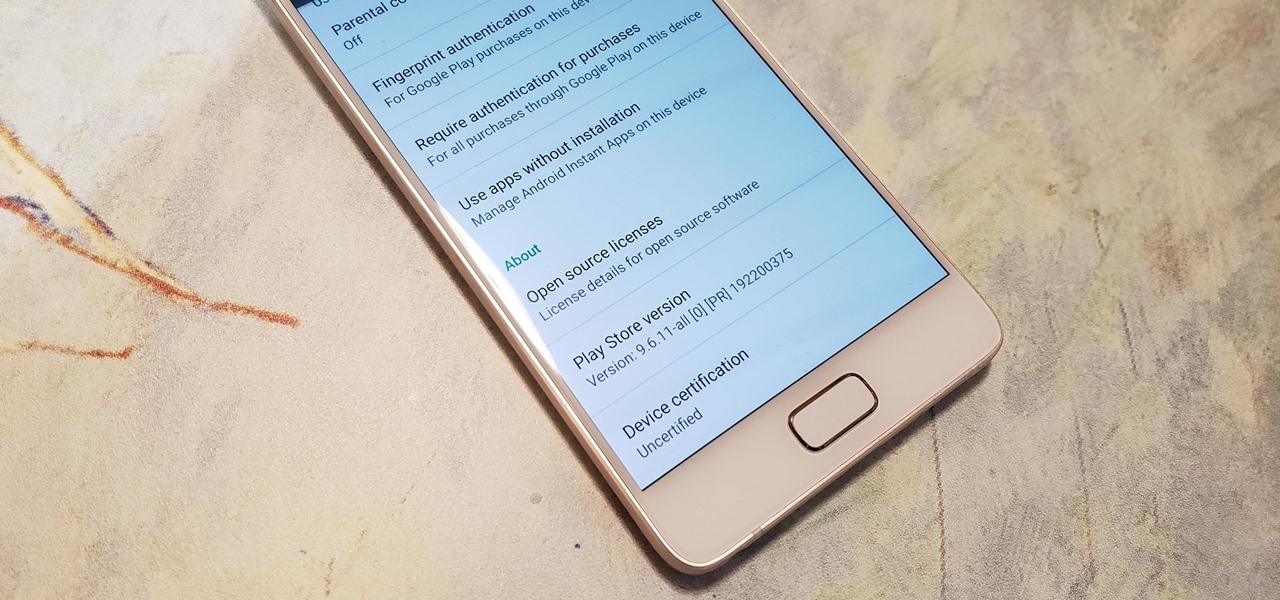
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

During Mobile World Congress 2018, OEMs started to introduce the world to Android Oreo (Go edition). Android Go offers smooth performance on entry-level specs, allowing for genuinely good cheap phones. At first, the US only had one Android Go device, but it looks like a second will join in the near future, the Nokia 1.

With Mobile World Congress fast approaching, all eyes in the industry are set on Samsung's Galaxy S9 announcement on February 25. While leaks and rumors about the S9 and S9+ have been flooding in for quite some time, we're getting a much clearer picture of these handsets as the announcement draws near.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

Preserving battery life has become one of the biggest problems for the average user. Whether you're on Android or iPhone, your battery is probably a massive concern. While there are a ton of battery-saving tips out there, they mainly rely on you manually performing actions yourself. This isn't the case if you use IFTTT to take care of your battery automatically.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Google's launchers are some of the most polished home screen apps out there, but they lack the ability to customize. With the old Google Now Launcher, we had Xposed GEL Settings to add options for tweaking the layout, but that project was abandoned when the Pixel Launcher came out. Now, a new root mod will give us some key customization settings for Google's latest launcher.

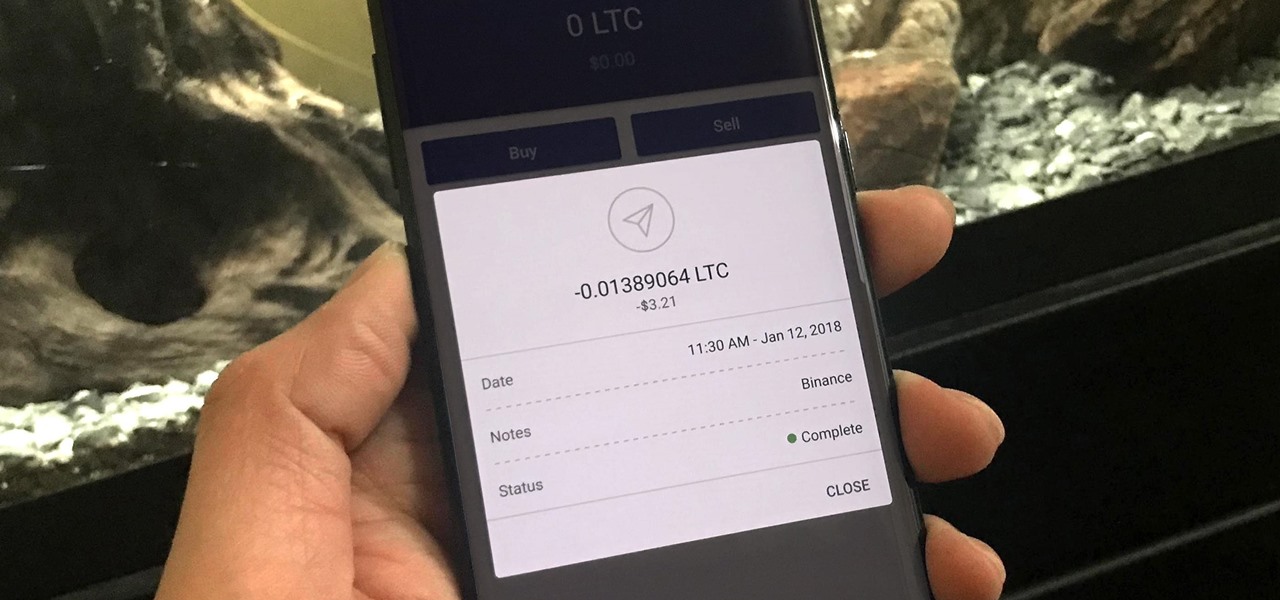
The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinbase, the most popular cryptocurrency app.

Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

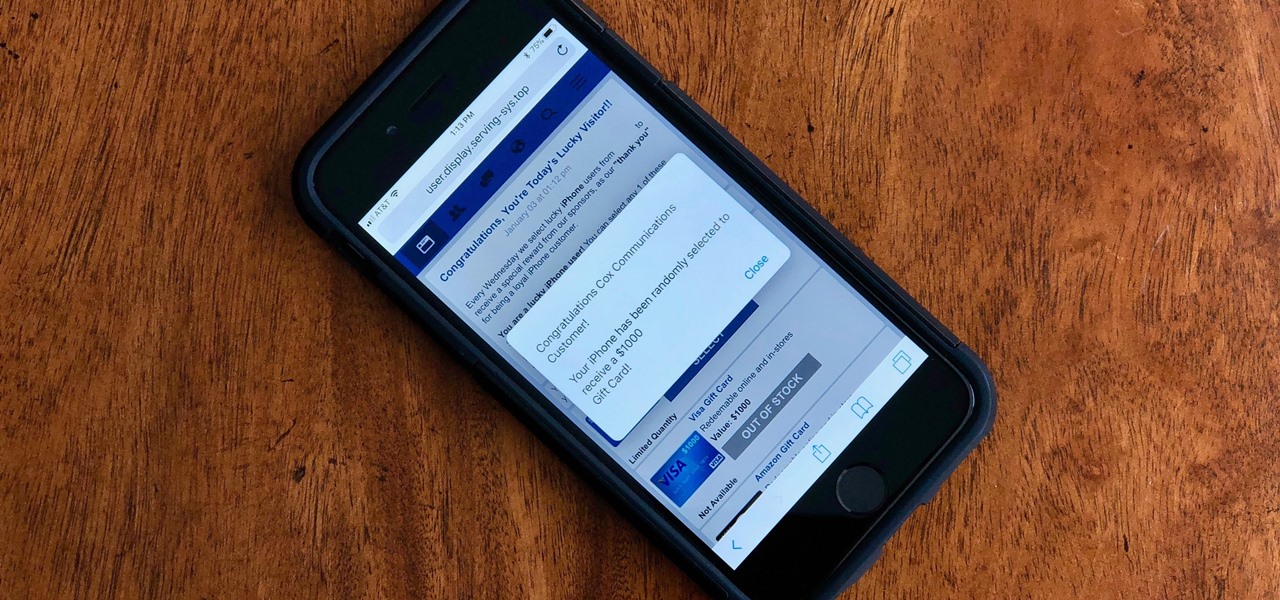
Safari for iPhone is generally a good mobile browsing experience — except when it isn't. Popup ads are a real issue, and they cause both great annoyance as well as concern over iOS security. How do you stop these nuisances and return to a web without fear of popups?

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

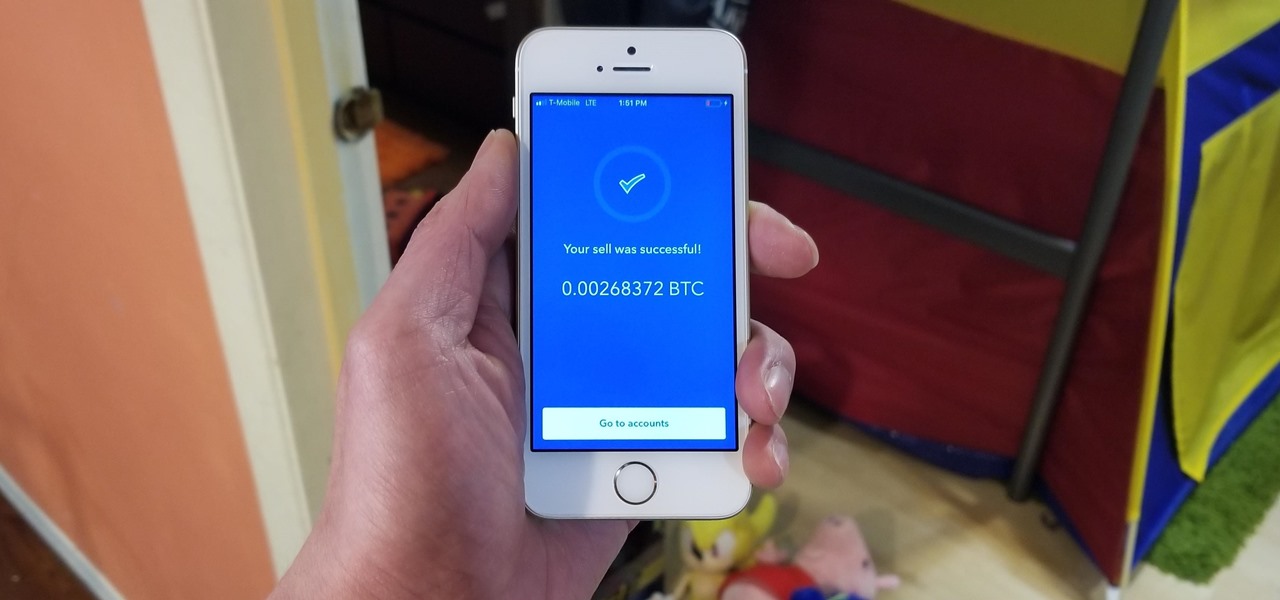
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

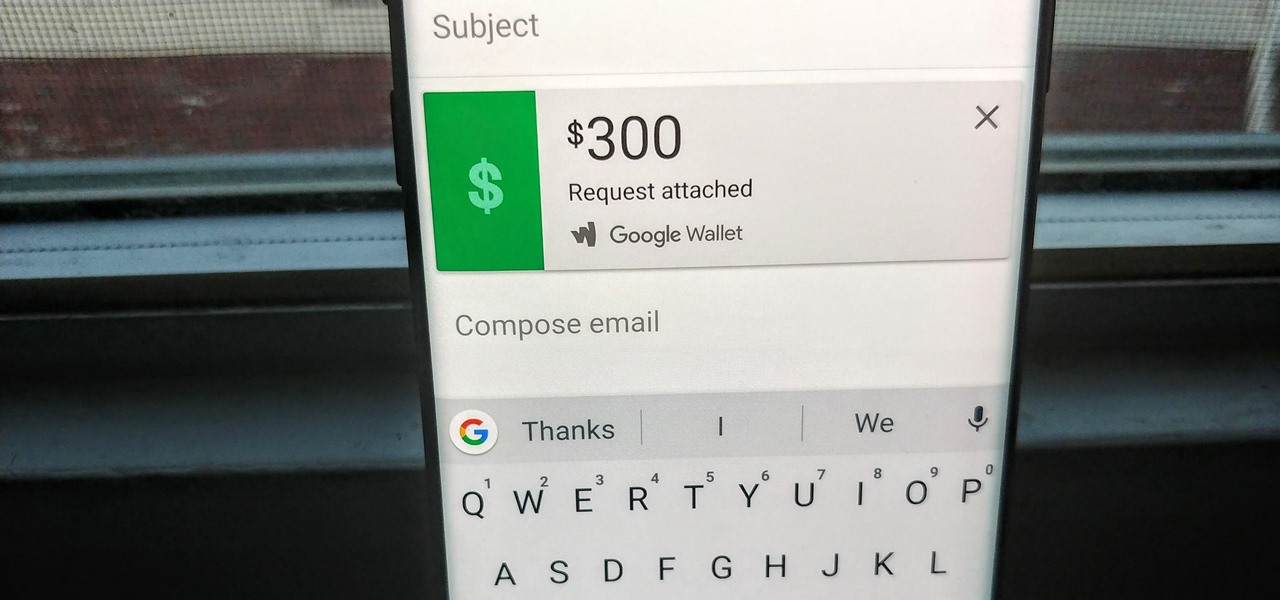
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

HTC is heading in a strange direction lately. Instead of releasing just one flagship in the spring season, they released two top-tier phones, with one having last year's specs and both having last year's design. They were also supposed to manufacture both the Pixel 2 and 2 XL, but Google was unimpressed by the HTC-made Pixel 2 XL and looked to LG for the bigger device. Now it seems, HTC isn't finished yet.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

With the new iPhone X, Apple introduced a buttonless design for the first time. But without a home button, navigation within iOS 11 had to change to accommodate the new model. To solve this issue, Apple created gestures to perform the actions that the home button once executed. But while Apple users have to wait until November 3 to use these gestures, you can get these features right now on Android.

One of the best new features in Android Oreo is the new Adaptive Icons system. Starting now, developers can create a single icon for their apps, then your launcher can stylize those icons in a broad range of shapes to match your system theme. Most home screen apps haven't added support for this feature yet, but Nova Launcher just threw its hat into the ring.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

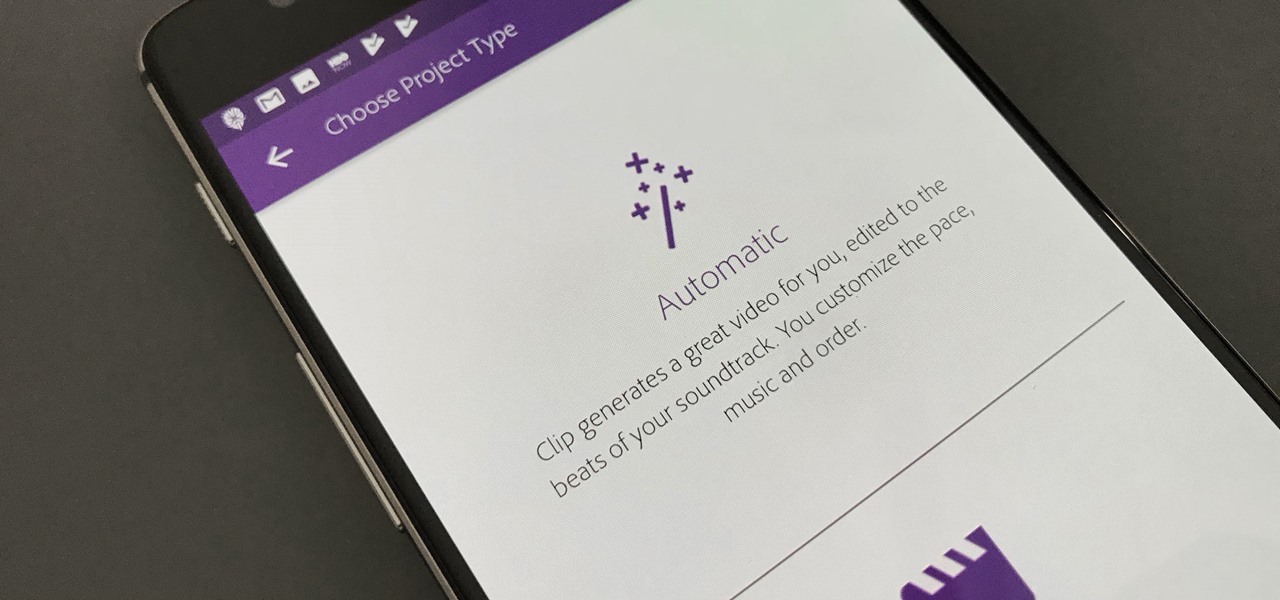
Are you interested in video editing, but have no background in it? Are you looking to put together a short from some clips you've shot, but don't know where to start? You could use iMovie, an application that comes free with every iPhone, but then what would you do on Android? There must be a universal solution that works across both iOS and Android to let you work however and wherever you like.

Staphylococcus aureus is a widespread bacteria — about a third of us have it on our body right now — usually in our nose or on our skin. And it probably isn't causing an infection. But, about 1% of people who have Staphylococcus aureus present have a type that is resistant to the antibiotic methicillin.

With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.

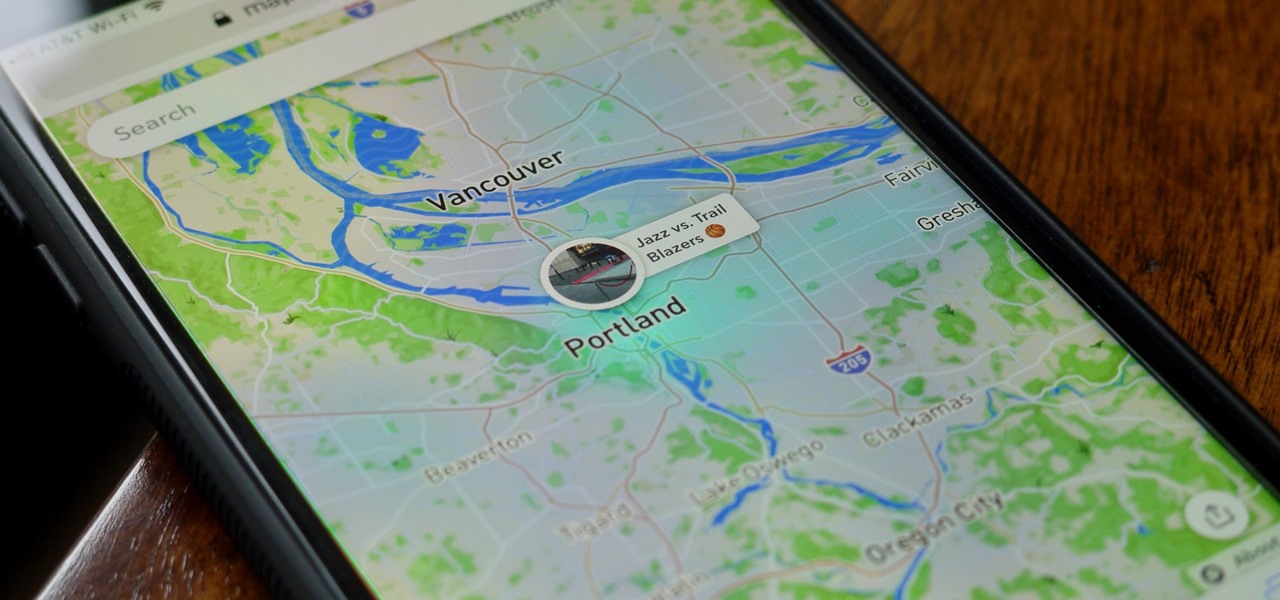
Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.