In this video tutorial, viewers learn how to spot a fake Rolex watch. Rolex watches are made perfectly and will not have any problems. Rolex watches are well maintained and are durable in water. There will be no water in the watch. Fake watched will always leak. Rolex watches will never have a date and day on the dial with stainless steal. A real Rolex has 2 1/2 times magnification, while a fake Rolex will only have 1 1/2 times magnification. This video will benefit those viewers who are plan...

Take it up a notch next Halloween by re-creating a classic princess with a naughty twist! In this two-part tutorial, learn how to steal the look of sweet & innocent Disney princess, Snow White and transform her into one hot retro pin-up model! Makeup & hairstyling is gone over by makeup & hair specialist Iris with a step by step process. Take seven short friends with you as dwarves and your look is complete!

Cranberry sauce is one of the most important side dishes to any Thanksgiving dinner—even Christmas dinner! And if you're like me, you usually buy a can of cranberry sauce for the holidays because you don't have the extra time to go homemade with the turkey stealing the show.

Need a new foam boffer sword? Can't get into a LARPing event without it? Well, you better steal one, or make one, but this video will show you how to do the latter.

In a legal brief entered on Monday, Florida-based startup Magic Leap has filed suit against the founder of Nreal, a former employee of Magic Leap, claiming that the company's Nreal Light smartglasses were built using Magic Leap's intellectual property.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

In the not so distant past, you had to actually go meet someone in person to repay money you owed them. Say they covered your half of dinner or picked up movie tickets — they wouldn't get their money back at least until the next time you saw them. Thankfully, Venmo has effectively eliminated this inconvenience.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Ex-Uber CEO and founder Travis Kalanick's bad and likely illegal behavior aside, his vision of not wanting to pay "the other dude in the car" has lead to a ground-breaking driverless test fleet.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

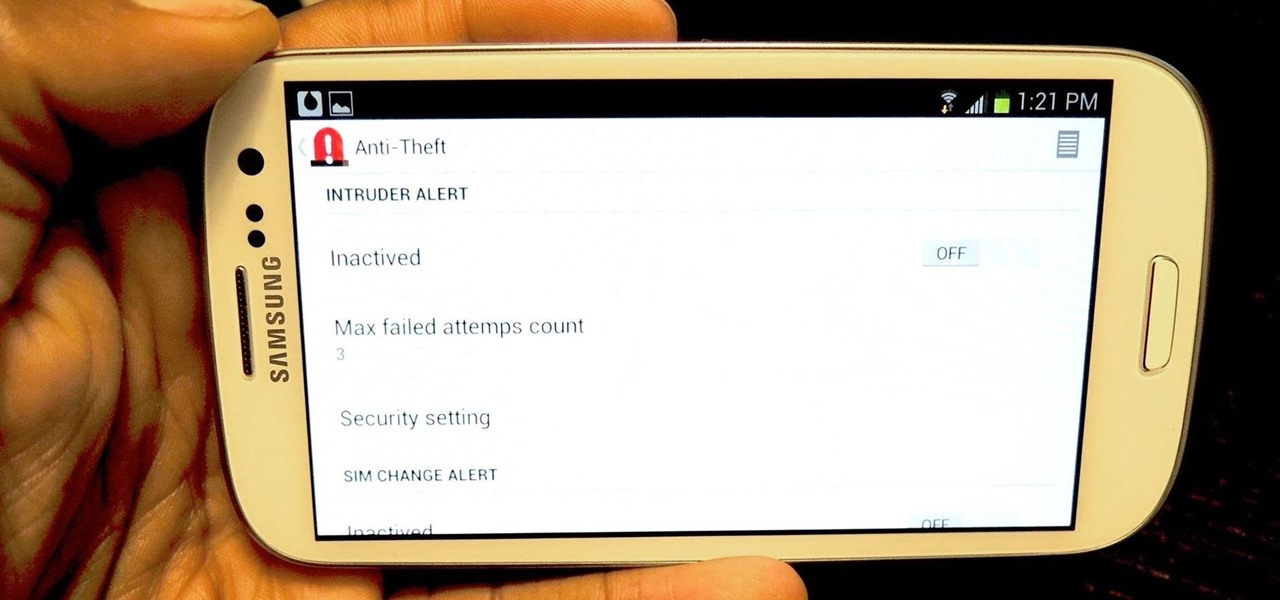
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

In most collectible trading card games players fail to realize the value of low-level creatures. They aren't sexy, but they can win you games when used correctly. This video will teach you how to build a Yu-Gi-Oh! based on three stars or less creatures that is still pretty damn effective.

It doesn't take much to make "House" hottie Oliva Wilde look gorgeous. But she really does turn things up a notch in her new movie "Tron," in which she plays fierce warrior Quorra. While Wilde may be genetically blessed, we can steal her beautiful night out smoky eyes from the movie.

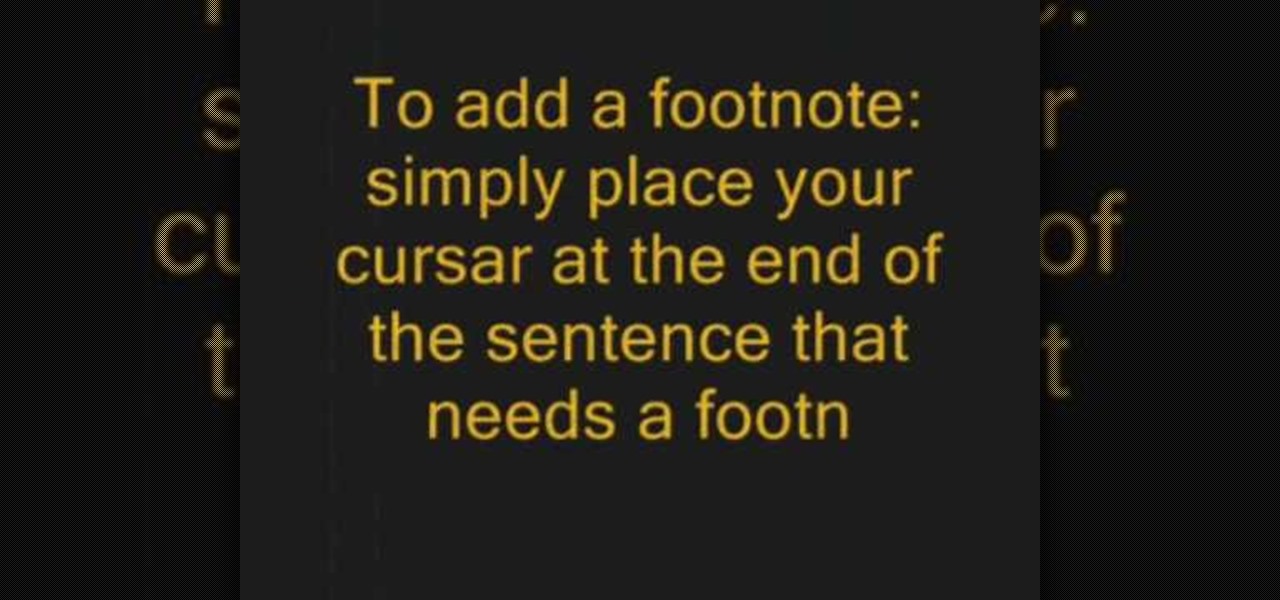
In this tutorial, we learn how to add a footnote to a research paper. To do this, you will need to have all the sources written down where you got the information for the topics that you're writing about. Make sure you give credit to all the places that you go the information, or else you stole it and it's plagiarized. You will need to write down the author's name, title of the source, publication company, city of publication, copy date, and page number. To add the footnote, you will simply w...

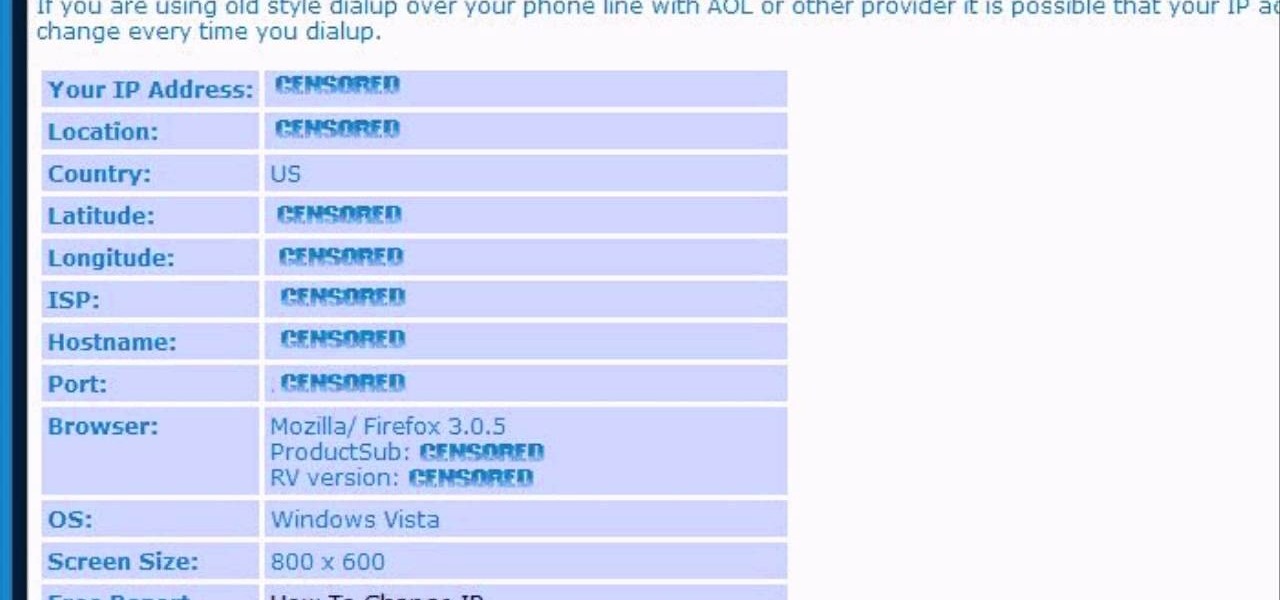
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. Once you have this information, make sure you don't share it with anyone else. If someone gets this information, they will be able to hack into your computer and ruin it. They could also access sensitive information and s...

We may not have Brigitte Bardot's perfect plush lips or her French sex appeal so natural she seems to have been born with it, but we can steal her makeup tricks! Bardot was most famous for her bedroom eyes - you know, the half closed, half open wink she would lay upon cinema viewers and men that sent the good kind of chills down their spines.

In this tutorial, we learn how to use Adobe Acrobat to read PDF files. First, click on combined files on your desktop, then add files to the program. You will see different documents on your computer when you browse, then take these files and move them up and down in the order you want to read them. This can help you organize the file so if you send it in an e-mail it will look more put together. You will also be able to print out the document after you view it, in case you want to take it wi...

Do you worry that if your PC is stolen someone can copy all of your data? Then you should encrypt your hard drive and removable USB drives too. In this video tutorial, you'll see how Windows 7 has beefed up Bitlocker, its built-in encryption program, and learn how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just under two minutes of your time. For more information, including complete, step-by-step ...

Disney star, Selena Gomez, always has stunning makeup and hair. Steal her look with help from this makeup tutorial hosted by Beechbum06. This look uses browns & silvers and is applied with all affordable makeup products! Wear this exact look with the following:

Are you sick of your dogs bad behavior? Such as chewing your furniture, bothering you while eating dinner, barking incessantly, and even stealing your slippers! Dee Hoult shows us how to properly use the 'Kong' toy to prevent all this undesirable behavior. It's simple, you just fill the toy with your dogs regular dog food, soak it with water, and put it in the freezer for 1 hour! Then you give your "Kong Pupsicle" to your dog, who will play with it for 30-45 minutes, getting the food out of t...

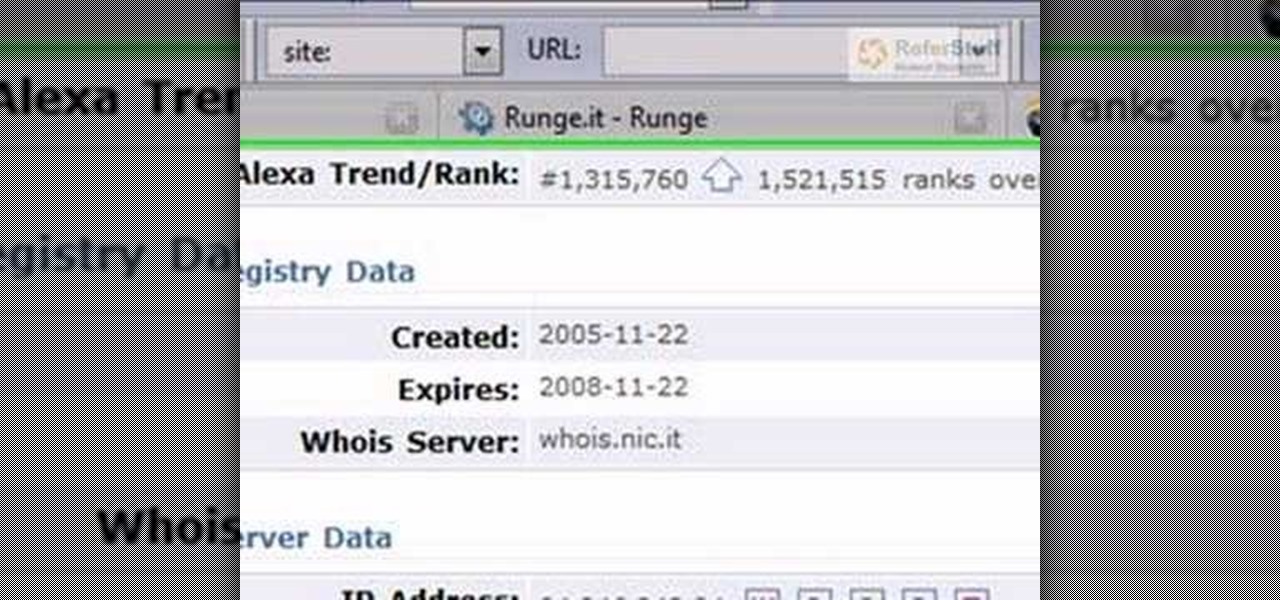
In this video from richardfallah we learn how to track a scam email. You can tell a scam from an email that looks a bit funny. So if it's an email that looks like it's from Bank of America, you might see a link to click that actually would take you to another site which is an exact clone of the Bank of America website, but it has a different web address. This is NOT Bank of America! They will try to steal all of your information if you type in your personal information. Whois is a great tool ...

Looking to change your look into something more... uh, scene? This video might inspire a new do with step by step instructions on how to get "scene" or "emo" volumized hair with a bit if teased height. Steal this look with help from this three-part hair styling tutorial.

Patent is the best way to keep what is rightfully yours. 1. You need an experienced patent attorney who knows the ins and outs to get you through the gatekeepers. 2. Gatekeepers are the patent examiners who make sure that already existing patents are not copied. 3. Register the idea to the USPTO to get the credit. 4. Once pending, the idea is ready for manufacturing. It can be sold to companies. "It is better to patent your ideas before someone steals it from you. "

Ashley Fierce unlocks the secrets of getting hair like Beyoncé Knowles in her video "Single Ladies." You can start out by straightening your hair and putting on a plastic headband in order to tame any short baby hairs you might have. Use hairspray to tame the front and sides of your hair and then take a comb and hairspray and lightly tease small sections of your hair in order to give them volume. Take your bangs and bobby pin them to the side so that they are out of your way. You will work wi...

Want to look like Courtney Cox Arquette from her hit series Cougar Town? Courtney Cox is absolutely beautiful in her show, so why not steal some of her looks for personal use? Princess Pinkcat shows you how she creates her Courtney Cox makeup look from Cougar Town.

In this three part video series, learn how to steal the distinguished English Rose makeup look seen all over the red carpet. Part one goes over how to apply the base and foundation. In part two, eye application is gone over, and in the last video, learn how to apply makeup to your lips that will last. Learn how to achieve the flawless, luminous skin, captivating eyes, & soft sexy lips to achieve the English Rose look.

Hacking a bike lock is something that you may need to do sometime if you forget your combination or maybe just didn't bring the key for the lock with you. You should never hack a bike lock to steal anything and should know that this tutorial is for informational purposes only. The first thing you will need to do to accomplish this task is to get a marker. Once you have the correct size marker to fit into the key hole, just stick it in there. Once it is in the lock, just press down while turni...

Steal Rihanna's look with this tutorial hosted by makeup artist, TiffanyD, teaching how to use "reversed eyeliner". Reverse Eyeliner is a different technique, but simply means applying the eyeliner to the lower eyelashes and winging it upward, while leaving the top lids blank. Watch how this easy application is done and then go try it yourself!

Watch this video tutorial to learn how to book the best hotel room for your money. You've spent all year saving up for your dream vacation. The last thing you want is to end up in a hotel room that ruins the whole trip.

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need

This is basically how to make a lock pick for a combination lock. Don't go using this to steal things from peoples lockers. These are the steps below...