
How To: Origami a shirt with a dollar bill
These step by step instructions help you to fold your own money origami shirt. Perfect for beginners. Money origami is great for presents and tips!


These step by step instructions help you to fold your own money origami shirt. Perfect for beginners. Money origami is great for presents and tips!

These step by step instructions help you to fold your own money origami bow tie. Perfect for beginners. Money origami is great for presents and tips!

These step by step instructions help you to fold your own money origami duck. Perfect for beginners. Money origami is great for presents and tips!

These step by step instructions help you to fold your own money butterfly out of two dollar bills. Perfect for beginners. Money origami is great for presents and tips!

Learn to play "Money" by Pink Floyd on guitar with Eric Olson.

This video explains how to get more money for items you're selling on eBay. If you're trying to create a business, you need to think differently than if you're cleaning out your closet.

She thinks just because you're related that your closet is her closet; and if she ever gives your things back, they're never washed. If it's time to stop your sister from being a closet bandit, check out this video. This tutorial is full of tips for gettinf rid of that pesky sibling and keeping your clothes all to yourself.

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Not everyone in Hollywood owes their nice complexion to a dermatologist. Here are some homespun beauty secrets you can steal.

When watching stories in your Instagram feed, there's a high probability that you'll come across an AR filter that you'll want to try out for yourself. A quick browse and search in the Effect Gallery will bring up nothing in most cases. But all of that unproductive work isn't necessary because there's a faster and simpler way to get the AR effect in Instagram Stories, and it works all of the time.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

There is not a single museum that houses all of the 36 paintings of Johannes Vermeer, so Google decided to come up with a solution to give art aficionados a venue to see the artist's work all in one place — your home.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The Essential Phone didn't have a hot start when it was released back in August. A delayed release, poor camera performance, and high price tag led many to avoid the otherwise well-received device. But after a few software updates and price drops, it's now a steal of a deal.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Baidu signed a cooperation agreement on June 7, the first day of the CES Asia conference, with multiple companies in the autonomous vehicles industry. The companies listed in the press release include Desay SV, United Automotive Electronics, and Hangsheng Electronics, as well as possibly additional auto manufacturers. Baidu plans to "jointly develop" upcoming intelligent driving production plans.

Instagram Direct is fast becoming the end-all-be-all messaging app, and it just added some incredibly convenient features that should make it a bit more practical. These new additions have a clear purpose: To help Instagram Direct grow its base and take on more feature-rich messengers like Snapchat or WhatsApp.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.
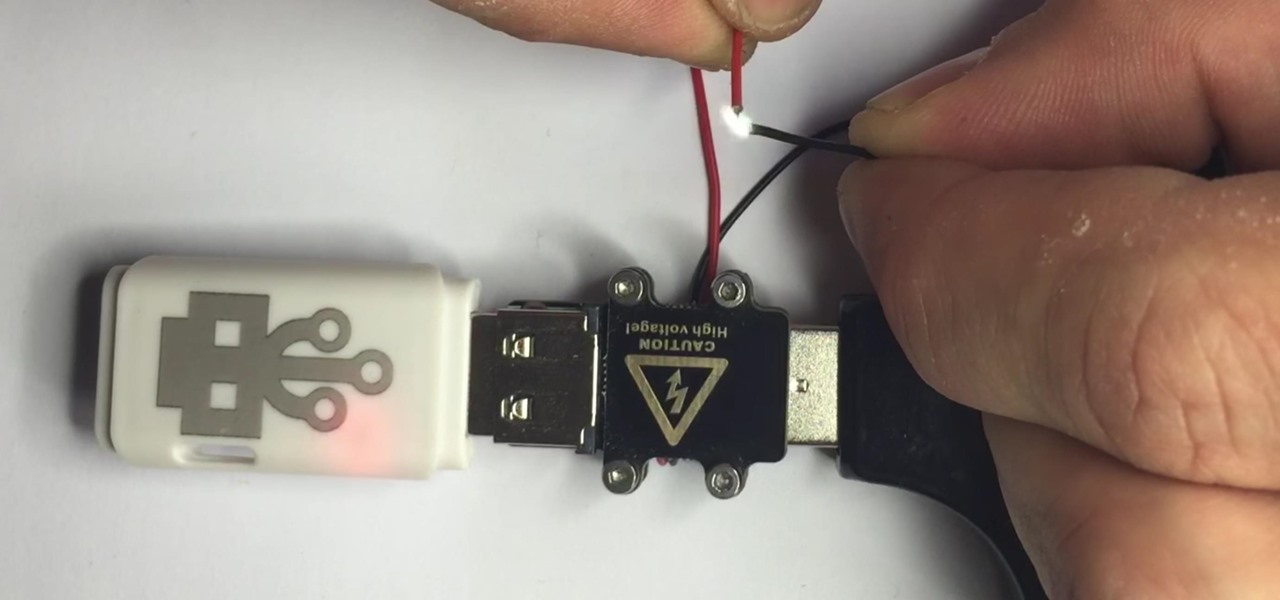
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Samsung's next Galaxy Note smartphone is expected to contain some nifty new additions that the company hopes will give it the long desired edge it has been seeking over Apple. One of those features that might make the difference? An iris scanner, which could make it the first major smartphone on the market to have that technology included.
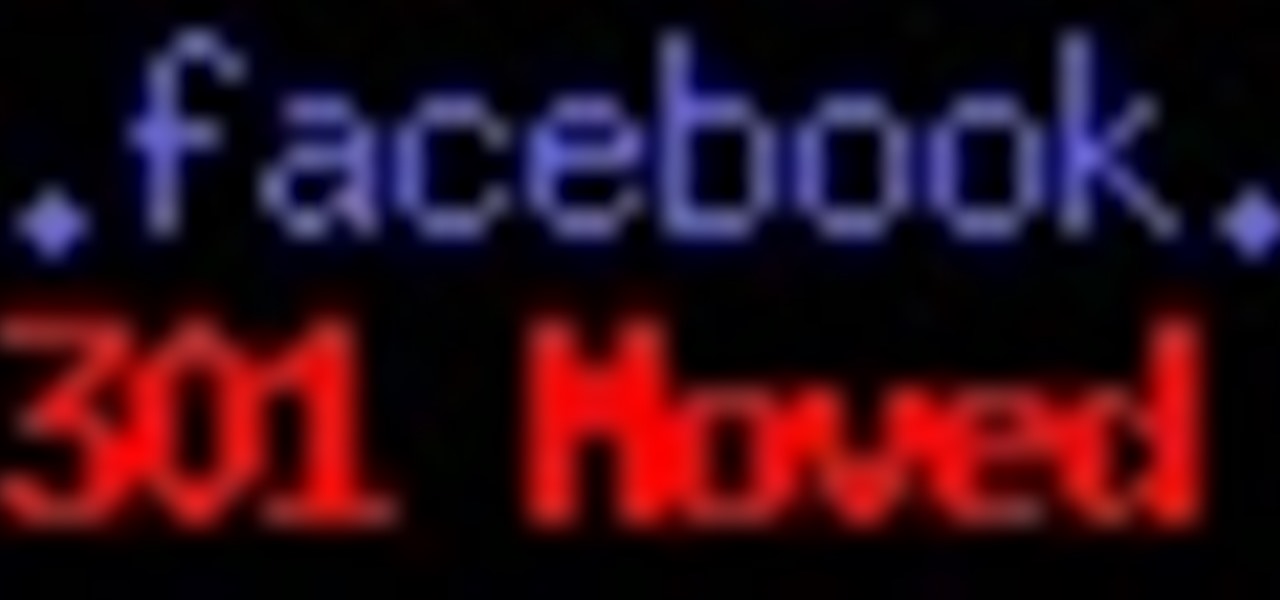
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

February 21st is going to be a busy day for Android smartphones. Samsung has already scheduled its "Unpacked" event to show off their new Galaxy S7 and S7 Edge handsets, and now LG is joining in on the action, as it will unveil the G5 on the same day, at the Mobile World Congress in Barcelona.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

There is a question that has haunted man since the dawn of time: What if you could combine your tablet and your smartphone? Historians around the world have documented wars on the subject, and philosophers and kings who dared ask the question went down in the annals of history.
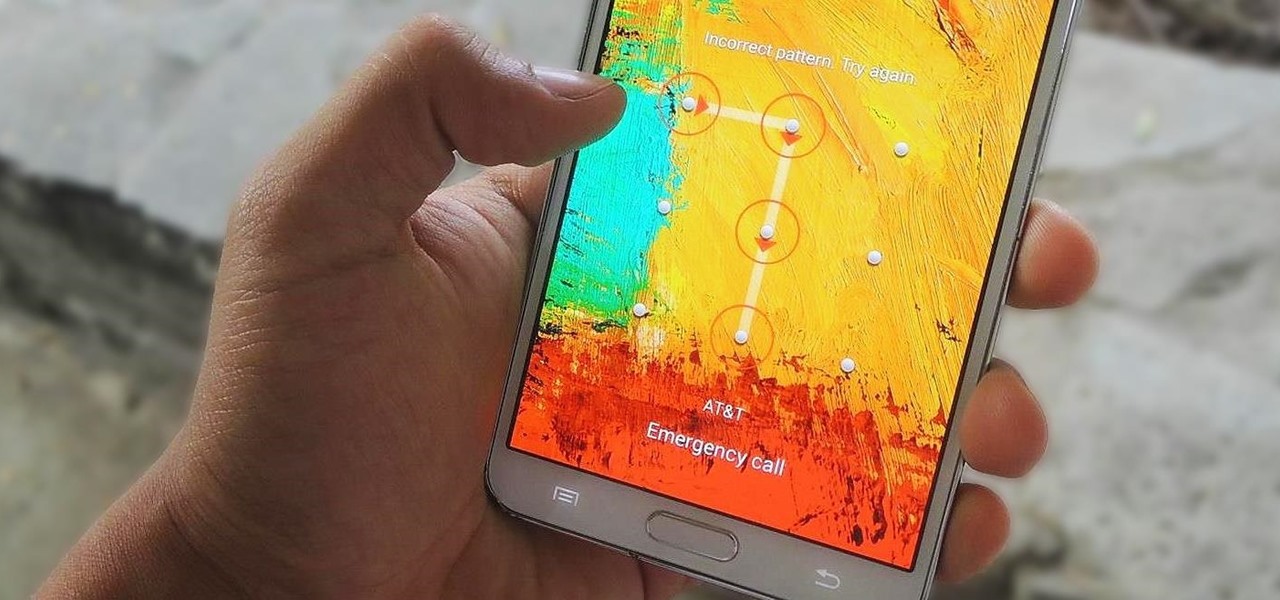
Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

Want the best view of Los Santos in Grand Theft Auto 5 without having to purchase a plane or steal a chopper? You can enjoy the sights of the Los Angeles replica by hopping on one of the trains rolling around the city—and forget about riding in one of the cars, we're going straight into the cockpit.

If an athlete gets athlete's foot, what does an astronaut get? Mistletoe. Yup, that's about the only time I've ever really needed mistletoe for anything, but cheesy one-liners aside, mistletoe can be the greatest wingman (or wingwoman) ever, but only during the holiday season.

I know I can't be the only person whose socks go missing in a shroud of mystery, but I'm determined to catch the sock-thieving gnomes in the act. While I have my suspicions, I can't quite prove it. Sure, I could drink a load of Red Bulls and never sleep, guarding my socks—but that's just crazy right? Luckily, I've found a way to set up my phone to catch the culprits.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.