Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

Huawei has been on a roll recently. They just became the second largest smartphone manufacturer in September, passing Apple and trailing only Samsung. Shortly after, they announced their new Kirin 970 flagship SoC to rival the Snapdragon 835, then followed that up by announcing the Mate 10 and 10 Pro. Well apparently, Huawei isn't done with announcements just yet.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.

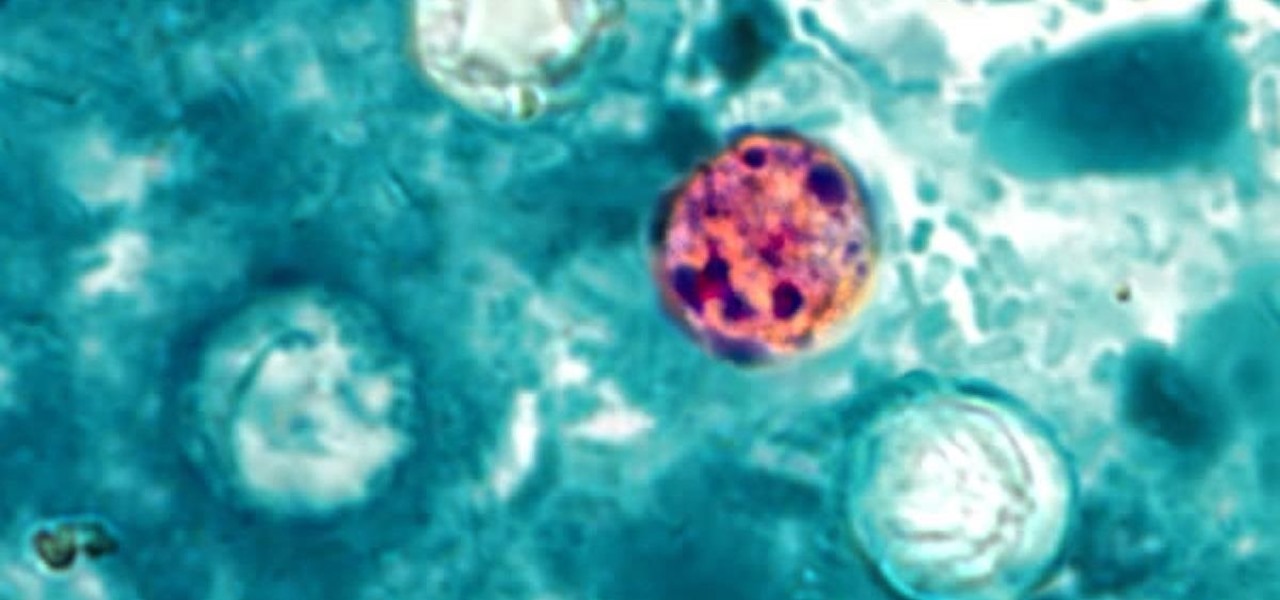
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

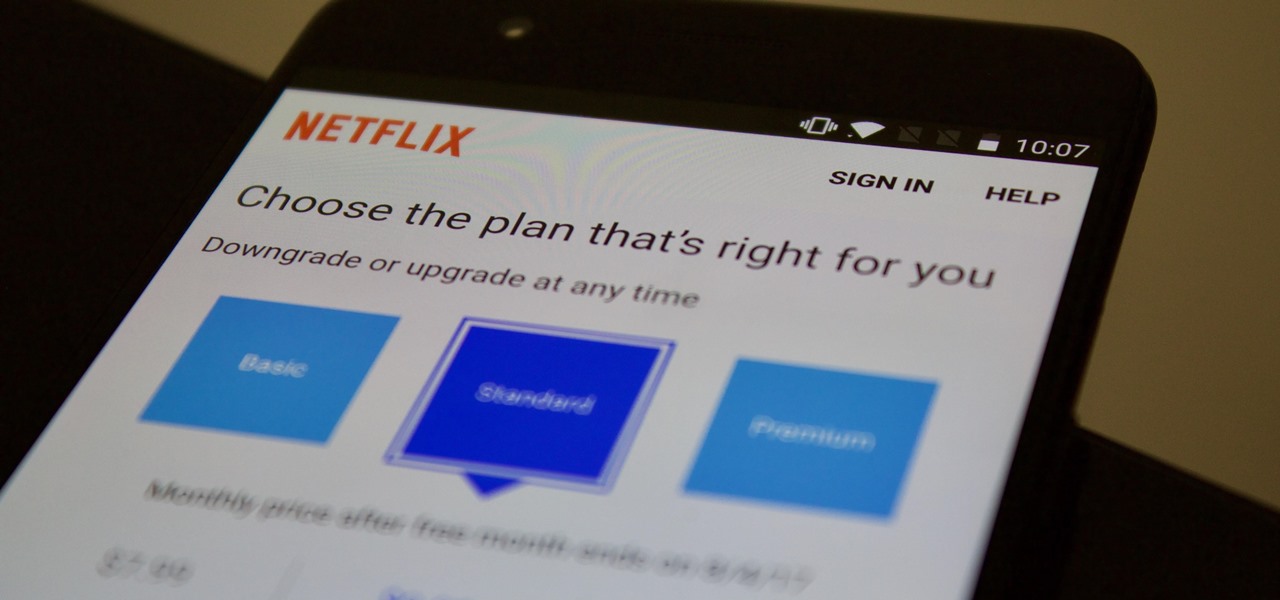
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.

Crazy Taxi continues to be a favorite among gamers of all ages, from those who played the game in late-'90s arcades to those who discovered the game later on consoles. This weekend, Sega announced their mobile version of Crazy Taxi would now be available for free. What a time to be alive. So does the arcade classic still hold up in 2017? Let's find out.

A Seattle development team is putting the "ARRRR" in AR with the maiden voyage of Captain Blimey, an augmented reality game for iOS and Android devices that puts a pirate premise on Pokémon GO.

It's no secret that Samsung had a lot of bad press this year. Despite this, we've reported how, even with the massive negativity in the media, Samsung has been expected to have an excellent Q1. Not only have those expectations been confirmed today, but Samsung has announced they are also working on a new flagship smartphone. One that some say could be the Note 8.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Uber wants you to forget about cars and start thinking about fully autonomous flying as an alternative—a more "economically favorable" way of getting to your grinding nine-to-five.

Udacity, the online education startup that set out to train a school of self-driving car engineers, is now spinning off into its own autonomous tech company called Voyage.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Lenovo, the company that now owns Motorola, just announced two new entries in their wildly successful midrange Moto G series. The Moto G5, and its bigger brother, the Moto G5 Plus, were both shown off in detail at Mobile World Congress 2017 in Barcelona, Spain.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

In the Western world, the only time you'd associate food with cockroaches is health code violations. And while other cultures and countries are more open to cooking with and eating these and other little buggers, insects are probably not a food trend that will be adopted by the West anytime soon.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

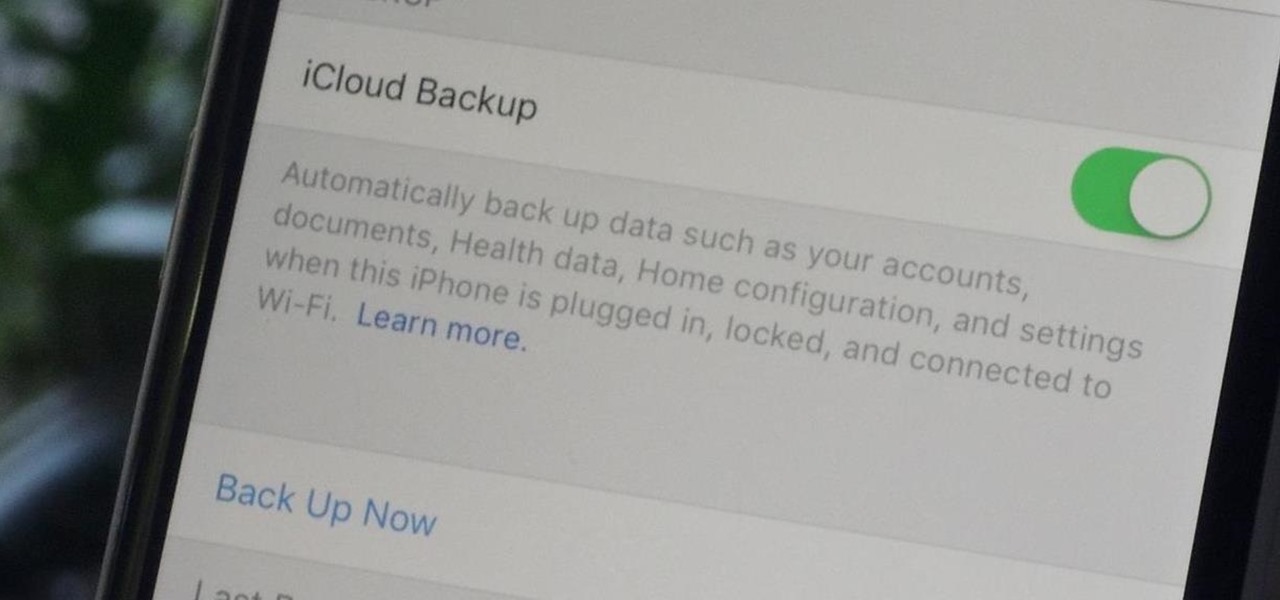
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

Welcome back, my rookie hackers!

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.