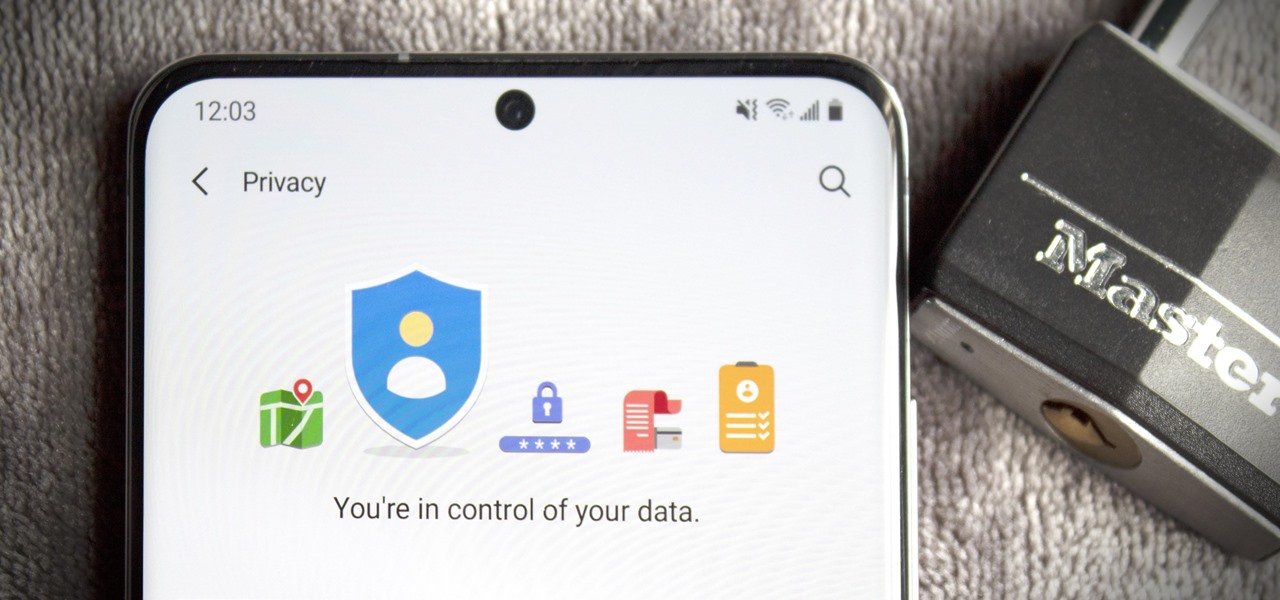
Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.
Welcome back Hackers\Newbies!

A vending machine is an invaluable yet totally frustrating piece of equipment. It's a godsend whenever your tummy's growling or you need an ice-cold drink on a hot summer day. But when something gets stuck inside or the machine flat-out malfunctions, it quickly becomes your archenemy. And when you're broke, it's basically just one big tease.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

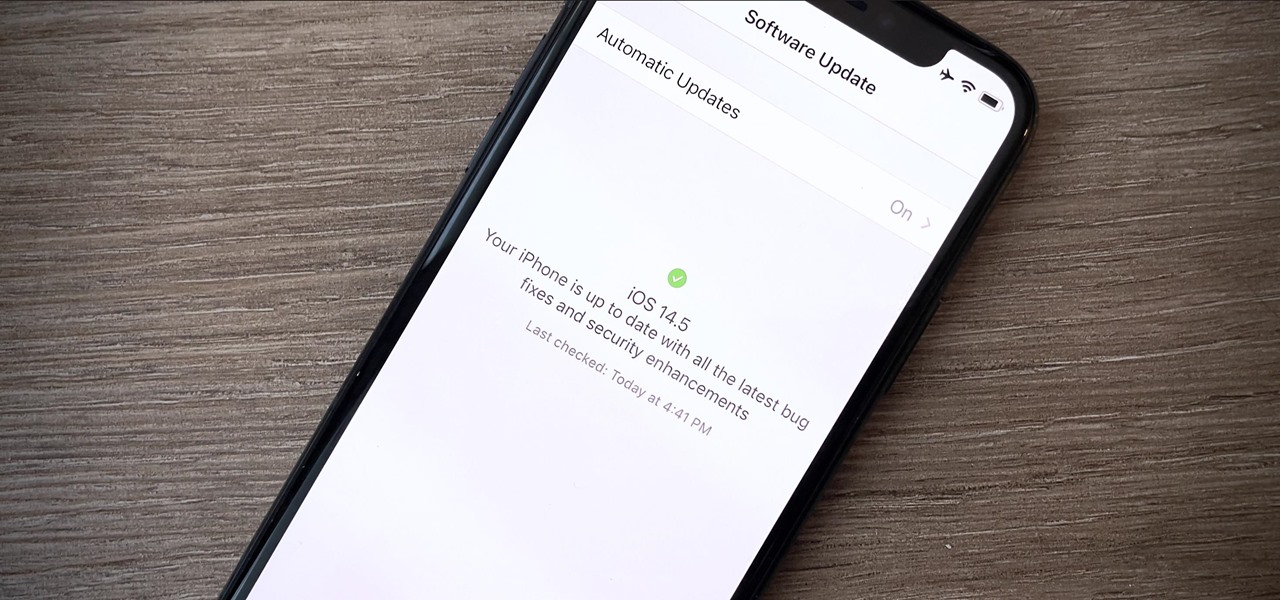
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Do you live in a dangerous neighborhood? Even if your area isn't known to be dangerous, it could still be a target of home burglaries. Don't let the thieves have the upper hand. Make sure the only thing they're stealing is grass. To properly secure your home from external threats, you must find weaknesses potential and potential entry points and fix them.

This is a video tutorial that shows you how to start your scooter when you lost your keys. If you're stealing a scooter, then that's your own fault, this is just to show you how to start your little motorcycle without keys, for emergencies. Now, this video is in a different language, but there's text for you to luck at, so follow along.

Learn how to use a site: http://www.copyscape.com to check if people are stealing content from your website.

Does one of you keep stealing the covers or hogging the entire bed? Kiss goodbye to bedroom battles with this how-to video guide to harmonious bed-sharing. These bed sharing tips are sure to help you with your relationship. Share a bed with your partner harmoniously.

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

Set up a large maze in a field. However, there are no walls to the maze, just outlines on the ground.

When you think of archery bows, you think of a curved piece of wood. You can feel the taut string between your fingers. Images of Robin Hood appear, stealing from the rich and giving to the poor. You think of simplicity. But when it comes to hunting, a bow is an entirely different beast.

With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighbors up. These "farmers" are the ones seeking quick hacks and cheats.

You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password for your BlackBerry Bold.

Have you been sharing your Netflix password with your friends? How about Rhapsody or Hulu Plus? If you get caught sharing your online subscription accounts, you could be slapped with a fine and even imprisoned.

I am the crime watch co-chairman for our neighborhood crime watch committee of our home owner's association. Instead of making a boring "do this, do that" video, I decided to make a funny video from the eyes of a criminal that specializes in stealing from homes, just like mine. This is meant to teach homeowners what to look out for when keeping their homes safe from criminals.

Not sure about the entire STEALING other children's LEGOs is cool in this short, but the sense of style and mood is quite beautiful. It features LEGOs and thats all that matters to me.

There's a certain achievement in Assassin's Creed: Revelations that springs up whenever the games chooses to. The Tax Evasion achievement is only worth 10G on Xbox 360, or a bronze trophy on PlayStation 3, but boy is it fun.

I've decided to write this post so some of the fledgling street artists who may or may not follow this world in the future are informed about two things in the urban art world that are either not discussed at all, or distorted (intentionally or otherwise) to the point of misinformation. Those two things are, as the title says, the dangers of street art, and the morals of street art.

I know hollywood has no original ideas, but its amazing how quick things get stolen. Rubber Johnny a really creepy video by Chris Cunningham was totally stolen by the Hills Have Eyes, which I only recently saw.

Colleges Aren't Just for Learning Our favorite bloggers have compiled a fantastic list of the Top Ten Most Legendary College Pranks. Lots of the legendary hoaxes and wacky pranks come from the notorious Pail & Shovel Party.... And the one's that seem more like impossible feats? Well MIT is certainly great at using their genius for laughs.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

This week's challenge will be the final Phone Snap Challenge, so let's make this count, everyone! To close off Phone Snap, we'd like to get a little silly. So start practicing all of your funny faces in the mirror and get those photo editing apps ready! Photograph somebody's funny face with your cell phone—whether it be your own, a family member's, a friend's, or your pet's, and post your very best shot to the Phone Snap community corkboard.

Reflections can make lifeless photos come to life or add a point of interest to an otherwise uninteresting photograph. They can also be used to distort one's perspective. With a mixture of a little imagination and science, some beautiful reflection shots can be created. This week, photograph some reflections with your cell phone and share them to the community corkboard.

What do you do when you've been wanting to take some awesome photos with your cell phone but can't seem to find a captivating subject? Well, whether or not you realize it, no matter where you go, you will always have a reliable subject to photograph—you! For this week's Phone Snap Challenge, we want you to show us your taste and personality by sending in your most creative and expressive self-portrait!

In this week's Phone Snap Challenge, we would like you to experiment with lighting and mood setting to create a silhouette. A silhouetted photograph contains a subject that is defined with an outline, appearing dark against a bright background. The subject generally appears dark, without any detail, while the background is bright and more exposed. Silhouettes in photographs appear to be simple, yet they can convey a sense of drama and emotion. Before you get started, check out this guide on h...

Now that the holiday weekend is over, there's only one more celebration this year, and that's saying goodbye to 2011 and welcoming 2012 with open arms! For this week's Phone Snap challenge, we'd like to ring in the new year with you and see your best cell phone photo from your celebration. Take a picture right as the clock strikes twelve or show us something that represents what the end of the year and the beginning of another means to you.

The holidays are here and all of us here at Phone Snap hope you're spending them under a nice warm roof with some yummy food and great company! For this week's Phone Snap challenge, we want you to utilize your cell phone to capture some holiday spirit. Whether it be the gifts under the tree, stockings hanging over the fireplace, Christmas lights outside, or everybody gathered together wearing their favorite holiday sweaters—we'd love for you to share with us!

It is always a bittersweet moment to find yourself looking back on the fond memories that seem to have taken place in the distant past. When your favorite song from 10 years ago comes onto the radio, or when a sudden scent reminds you of the summers you spent as a child—these types of moments tend to trigger the fondest of memories. For this week's challenge, we'd like to see a photo that captures a nostalgic feeling, whether it be your favorite childhood food, meaningful memorabilia you've s...

Using an analog camera to create multiple exposures is a technique that has long been in practice throughout the history of photography. Pressing the shutter button twice will superimpose the exposure of two different images onto the same piece of film. Sometimes done in an artistic manner, sometimes by accident—you never know what you'll get until you develop your roll of film.