Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

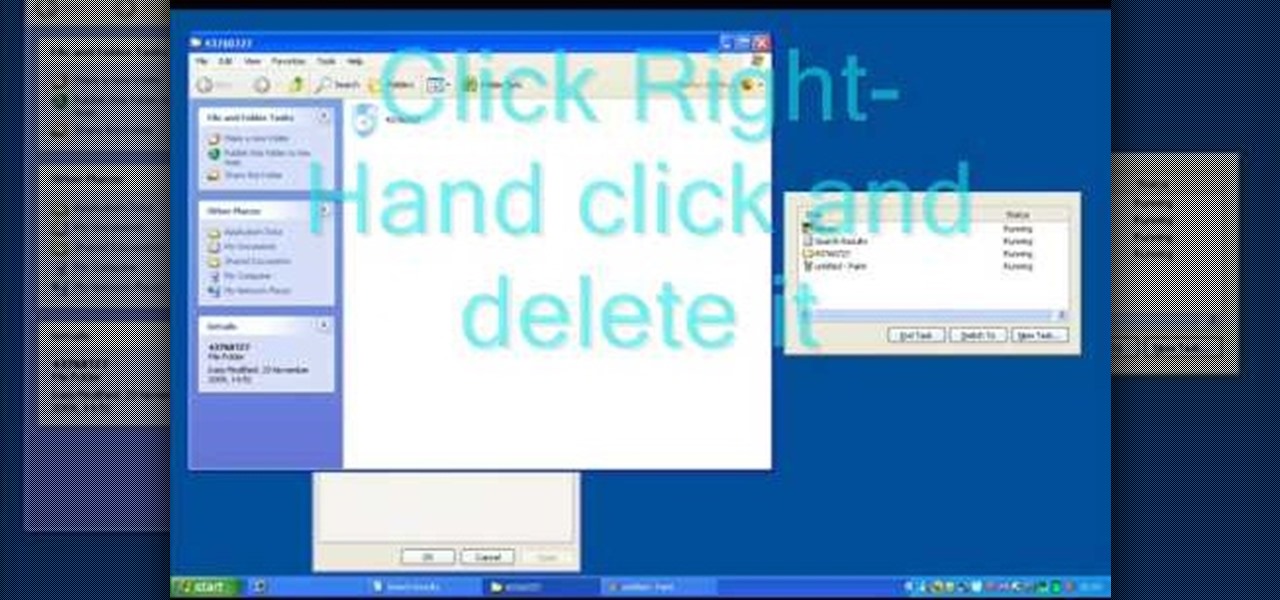
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

No matter what kind of business you have, small or big, online-based or not, when you're dealing with email marketing, the number one things your targets will see is the subject line, and if your subject line looks spammy or uninteresting, it's not going to help you one bit.

In this tutorial, we learn how to throw a crazy gyroball in wiffle ball. You will first stand still with the ball in your hand grasping it lightly, when you go to throw the ball, throw with force and spin your body around. This should make the ball go straight into the target almost every time you throw it. Keep practicing this until you have the hand placement correct. Try moving your hand in different positions around the ball so that the grasp makes the ball move in the right direction. Af...

In this Golf video tutorial you will learn how to avoid slicing with your driver off the tee in golf. First and foremost make sure that your grip is correct. The next point is allowing the club to sit on the ground the way the manufacturer wanted it. The next important lesson is to ensure that your feet and your shoulders are aligned straight down the target. And the last and the most important point to remember is to swing back to the ball with your hips first. Don’t use your arms first. If ...

Jim McLean shows us how to do an eight step swing in this video. You start the swing in the "address" or universal position. The first step is to move the club three feet back from the ball in a uniform motion. Position two is moving the club half way back where the club is pointing down the target line. Position three is a three quarter golf swing is when your elbows are level and the shaft of the club is pointing into the plane line. Position four is preparing to swing forward. Position fiv...

This video is on Golf and will show you how to use the variable tee drill to cure a pull shot in golf. This video is from Golf Link. A typical problem for somebody who tends to pull the ball is they position the ball too far forward. So, when they are setting up, the shoulders are actually looking left. By the time the club head reaches the ball during the swing, they are swinging around to the left producing the pull. The variable ball position drill will cure this problem. Place a club on t...

In this video tutorial, viewers learn how to use the hand rollover to cure a hook shot in golf. A reason why people hit hook shots is because when they come to impact, they roll their hands too early and too much. Therefore closing the club face and causing the ball to go left. To correct this, when you're coming to impact, rotate into a position where the back of the left hand is facing the target. This will square the club face. This video will benefit those viewers who enjoy playing golf a...

In this video tutorial, viewers learn how to cure slices by rolling the wrist. Some people hit slice shots because they strike with a underhand or reverse position. The correct way is when your hand comes back for impact, it should rotate into position with the back of the left hand facing the target. If the back of your left and is facing anywhere else, the ball will slice. A drill that users can do is to use their wrist watch as a guide. Start with it at a 45 degree angle. When you swing, i...

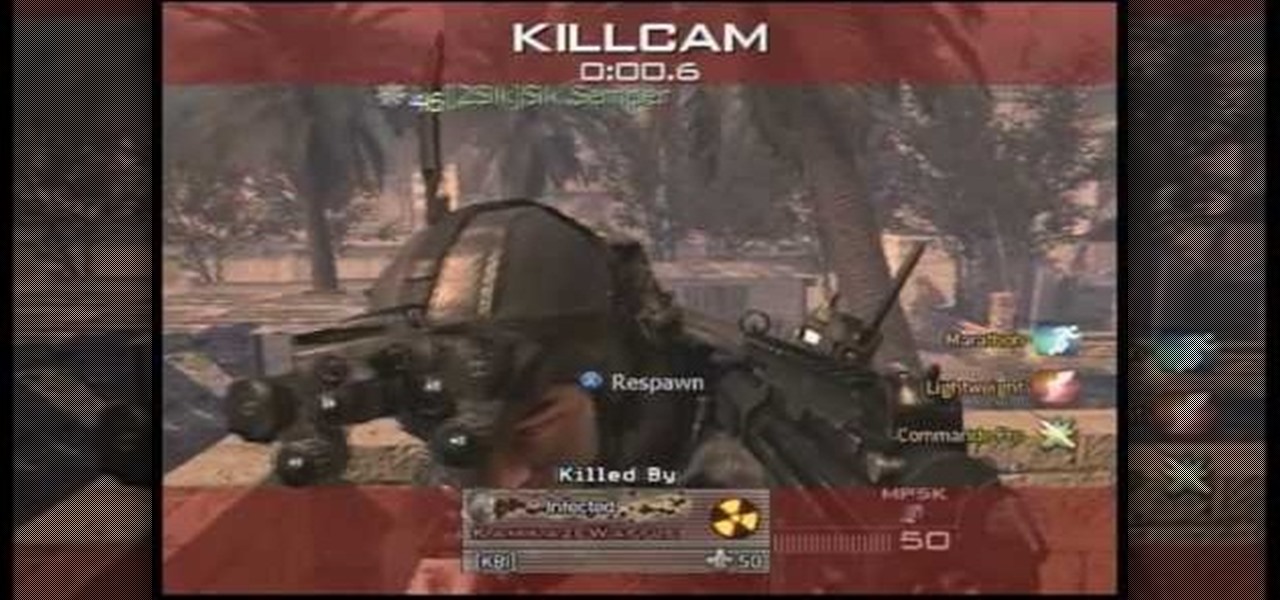
This video shows you how knives can be much more than a short range weapon in the online mood of the game, Call Of Duty: Modern Warfare 2. KamikazeWaffle and other players show you 50 ways of killing you enemy using the knife. Some of those tricks involve throwing the knife across a map and still hits its target. They also demonstrate how any objects around you can be used to change the direction of the thrown knife to the desired destination. Kill cam is recorded for each of the 50 tricks so...

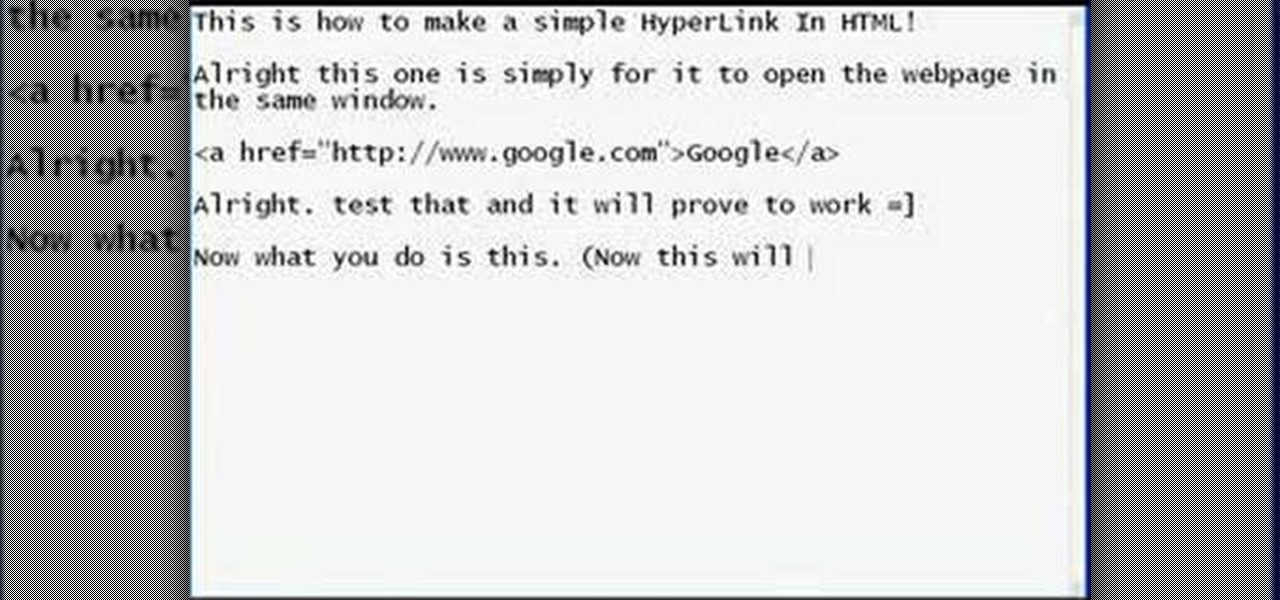
This how to video shows how to put an HTML hyperlink on a web page. It starts with the basic code to simply insert the link and have that link open in the same window. The code appears as follows: <a href="http://www.website.com">Text that will show up on the page </a>. The example used is Google, so it would be, <a href="http://www.google.com">Google</a>. The video then explains how to create a hyperlink that shows up in a new window. Sticking with the Google reference it would read <a href=...

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt explains how he teaches the BEEF method of shooting. The work BEEF is an acronym for a ball shooting concept in basketball. The B stand for balance, the E for eyes, the second E for elbows, and the F for follow-through. To have good balance it is important to have you feet about shoulder width apart. Your eyes should always be focused on a target, and your elbows should be in line. Finally follow through means it sh...

This how to video shows you a six pack abs workout that will help you tone and tighten your stomach. Learn three of the best abdominal sculpting exercises to target your midsection.

This pilates how-to video illustrates the Swimming exercise. This pilates exercise is good for core stabilization, upper back extension and hip extension. This is good to improve back strength and those deep abdominal stabilizers.

This video pranking tutorial shows how to make a ketchup bomb out of ketchup and aluminum foil. The ketchup bomb will explode on contact with the target and make a sticky, staining, red mess. It's easy to make the ketchup bomb during lunch, saving the practical joke for whenever you're ready to strike. Learn how to make a ketchup bomb by watching this instructional video. Use this as inspiration for one of your April Fools Day pranks!

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

After hosting an augmented reality experience using its Snapchat Landmarker technology at the Statue of Liberty, Snap is now giving creators the opportunity to create their own Lenses with Lady Liberty.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

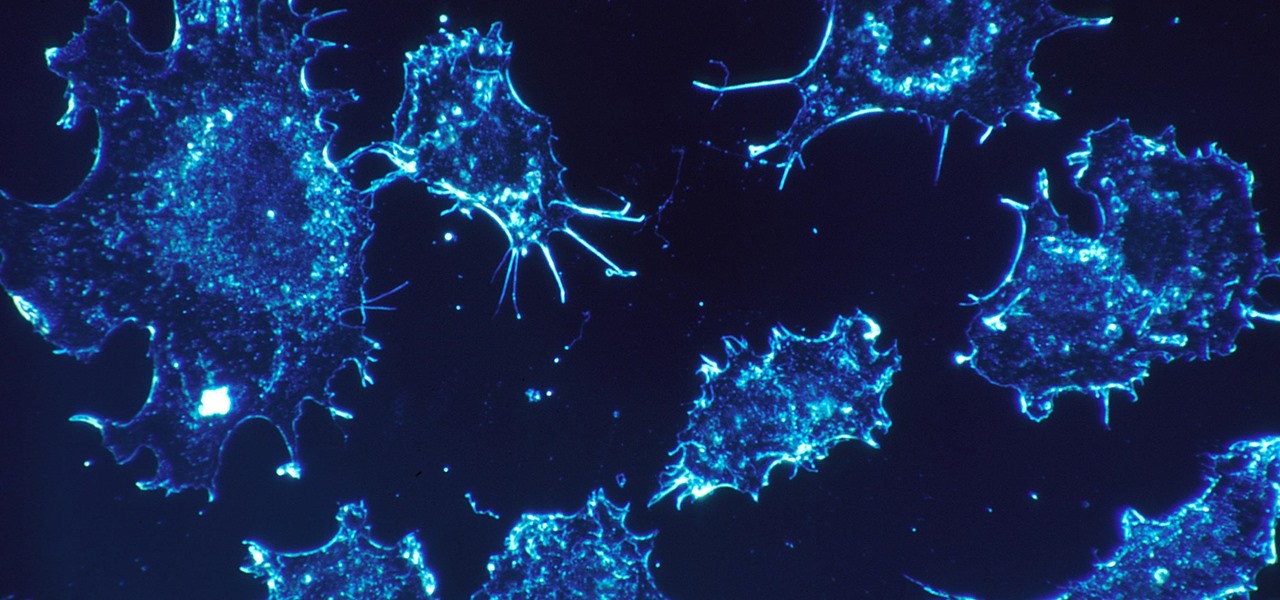
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.