While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Video: . This Video will Show you how to Season and Clean

Here is a video that shows 90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.)

90 seconds that could save your life. How to actually MAKE A FIRE with a lens, rather than just burning a hole in a leaf. (Or frying ants, which seems to be the other thing that kids like to do with magnifying glasses.) By forming your target material into an efficient ball, you will be able to start a fire even with very small lenses. Like less than an inch across small. The finer the individual fibres, and the more densely they are packed, the more effective is your ball of smigtin (smoulde...

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

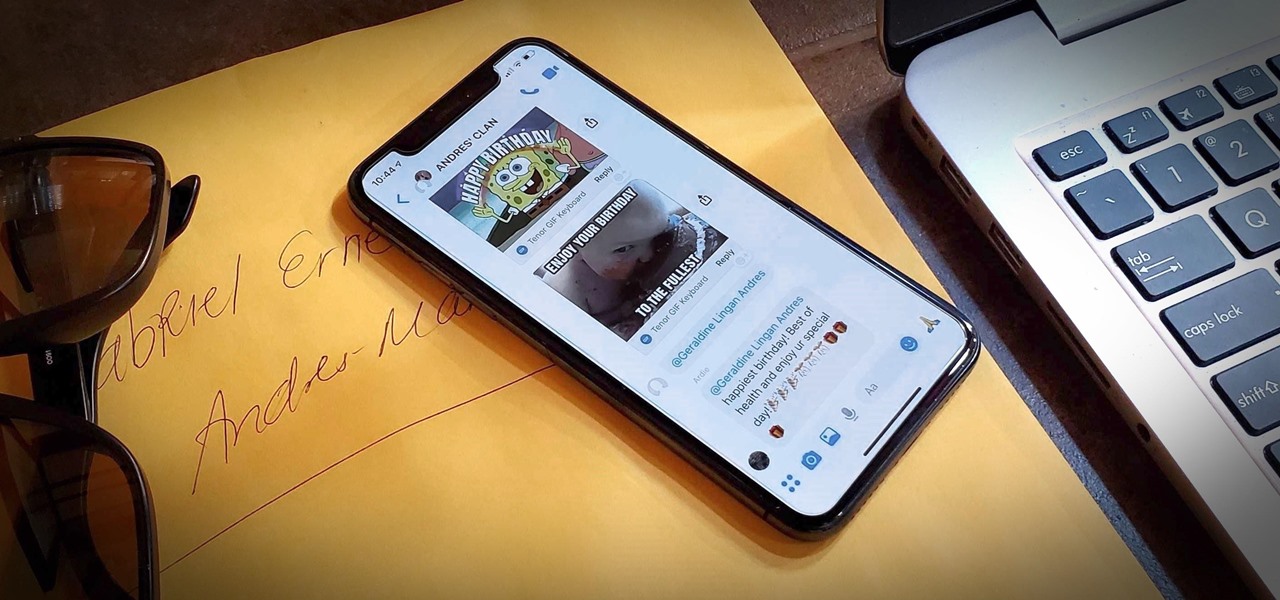
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

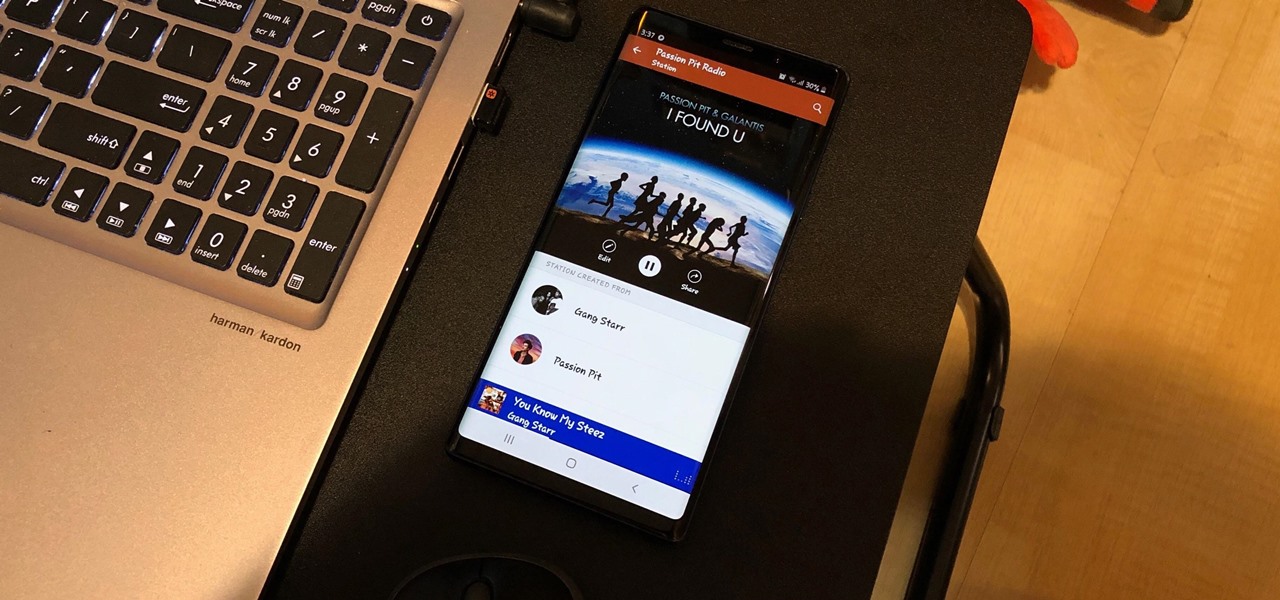
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

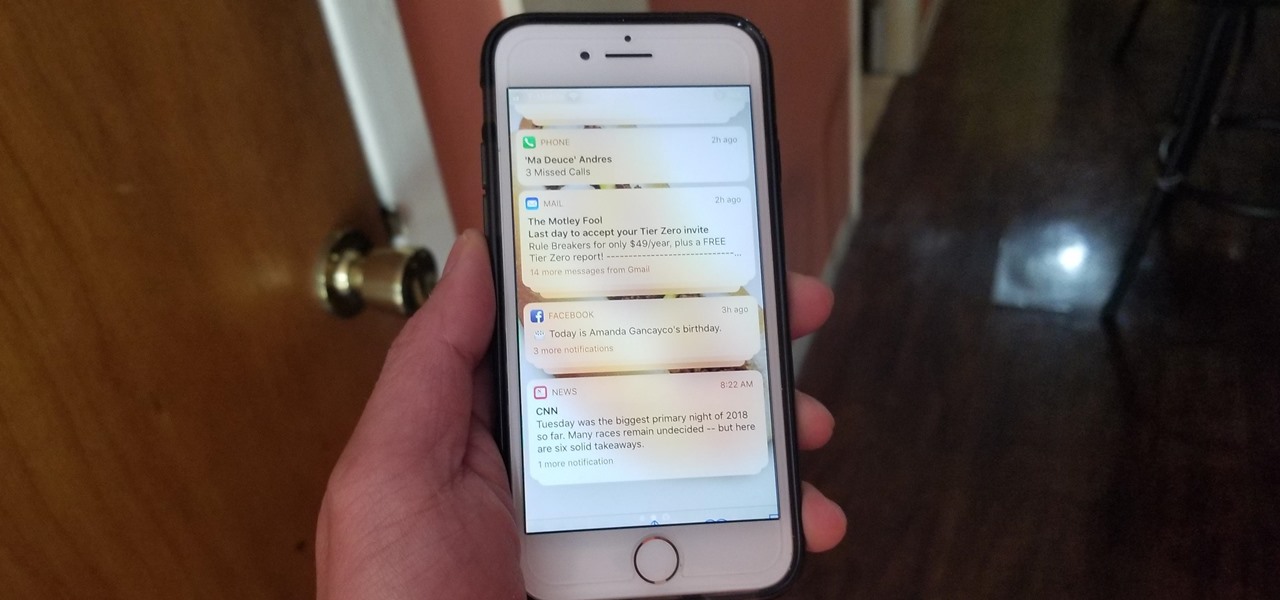
When you first update to iOS 12 on your iPhone, notifications on the lock screen and in the history will be grouped automatically into stacks based on a variety of factors for each app. For example, articles from Apple News will be stacked together based on sites. But you can also change this so that all alerts from a particular app will be grouped in one bundle, not separate ones.

At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

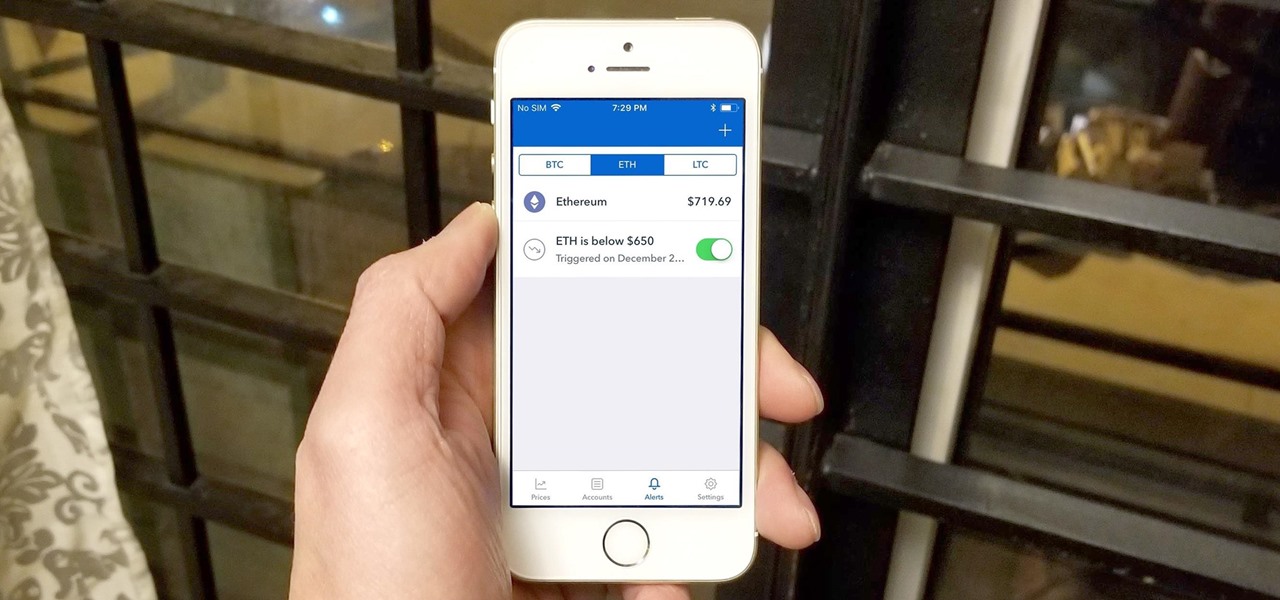
Bitcoin's wild price fluctuations — and by extension, Bitcoin Cash, Litecoin, and Ethereum — can be terrifying if you're new to trading cryptocurrency. Seasoned traders, however, see these price movements as opportunities to maximize their holdings and profits. With Coinbase, you can trade cryptocurrencies more efficiently.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The promise of augmented reality when it comes to gaming is the conversion of the player's real-world environment into a virtual playground.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.