Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Get tons of free money, unlimited items and instant levels with this hack for Fish World using Cheat Engine. CE will get you whatever you want in Fishworld.

Want massive, Arnold Schwartzenegger-worthy shoulders? Well, you'll have to work for it, but they're achievable with a few strategic exercises. Building muscle, especially big muscles like your biceps, requires heavy resistance.

Kristen Stewart is a well known tomboy who really doesn't care whether she's wearing Chanel or Target when she's out and about. But the sister knows how to glam it up big time on the red carpet and for photo shoots, where she brings out her hidden sultry, feminine side.

Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

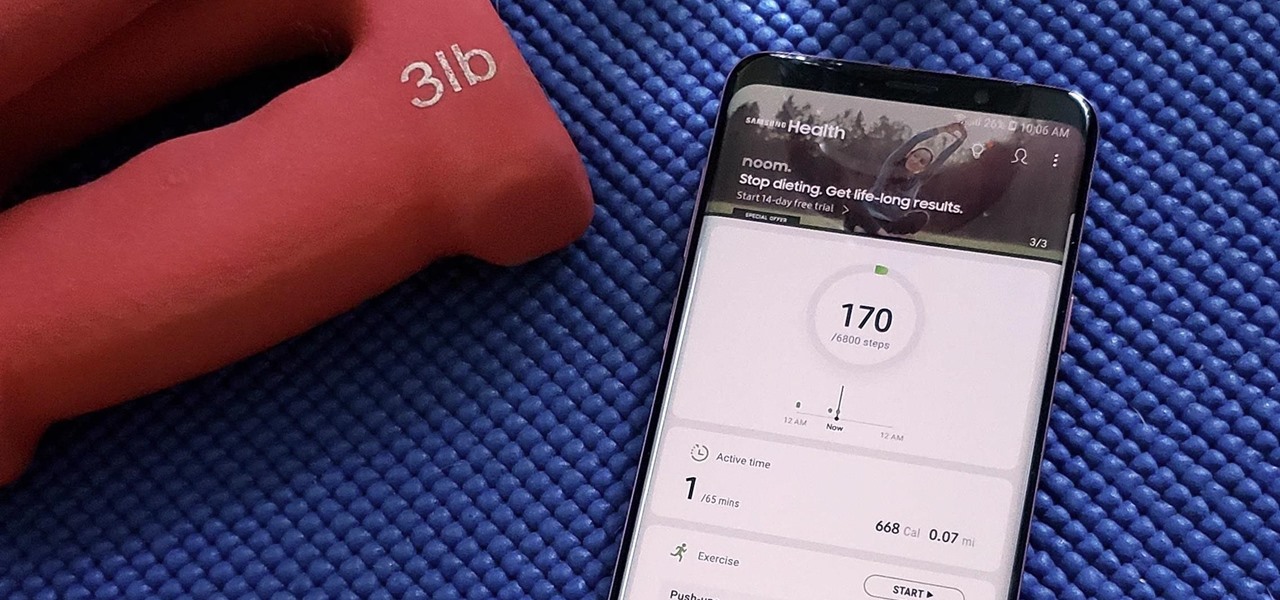
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

In this how-to video, you will learn how to make Cobra-style paper airplane. All you need is a regular piece of paper. This style is useful for hitting targets or flying straight. Fold the paper in half vertically and unfold. Take the top corner of the paper and fold it to the edge of the middle crease. Repeat with the other corner. Take the tip of the center and fold it to the horizontal line created by the folded corners. Make sure you make tight folds. Open it up and make a fold horizontal...

See the angled edge of the blade? This is the bevel angle. Match this to the face of the whetstone. For a clever-like tool like a machete, this should be at a high angle--15 to 25 degrees.

Ladies, it seems to be the trend to wear boyfriend cuts in clothes so here’s a video that will show you how to create a creative super cute and girly top using a guys shirt and tighty-whities. You can wear guy clothing and still look very feminine.

Get ready for one heck of a battle in the Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

You may have to eventually abandon your stealthy approach in this mission on The Saboteur for the Xbox 360. The second mission in Act 2: Better Dying Through Chemistry is when you reach the entrance, there's a gunner behind sandbags by himself. If you take him out quickly and disguise yourself you can actually play this level pretty quietly. There are two basic kinds of targets, the smaller, thinner tanks, and the bigger, darker tanks. The big tanks you can blow with dynamite and as long as y...

Get all of the info on the 15th puzzle, entitled "Guardians", in Assassin's Creed 2. Puzzle wheel: Seemingly every other ring is linked here, so we’ll cut straight to the chase: Turn the third (and fourth) rings right twice, the fifth (and first) right four times, the fourth (and first) right five times, the fifth (and first) left five times and the second left five times. Finally, move the fifth (and second) rings right five times. Image: Another gimme – just move the Assassin logo over the ...

All Things Come to He Who Waits: After parting ways with Leonardo, break into the walled-off area to the northeast and trigger this mission via a waypoint on the parapet walk. After the cut scene, you need to trail a courier that zigs a zagging path through the city. Stay far enough behind him that he doesn't get curious, but also be sure to keep him in your sights. If he gets separated from you by a wall, a countdown timer hurries you to catch back up.

Wolves in Sheep's Clothing: So, yes, that means there are more than one wolf in sheep's clothing. Hit the map marker and this mission will immediately kick off. You need to check the nearby street in front of a large, regal building to find a certain somebody. The area is marked green on your map, so don't waste time anywhere else. Just turn on eagle vision and, once you've spotted the target, a cut scene will take over.

Arivederci: Or is that Arrivederci? This mission won't take long. As long as your notoriety is at zero (and it has to be), this mission is a piece of cake. You have to escort Ezio's mother and sister across town to the city's exit. The city is temporarily packed with guards, but they'll pay you no mind, even if you run. Just avoid bumping into guards and you'll be a-okay.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

Work out the butt and thighs with press exercises. Learn about butt and thigh presses in this dumbbell fitness video. Take action: place feet higher or lower depending on target area, bring thighs to chest without rolling hips, but do not lock knees. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting an...

Learn how to do incline barbell presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

How to unlock everything - all of the hidden characters and stages - Super Smash Bros Brawl (SSBB) for the Nintendo wii.

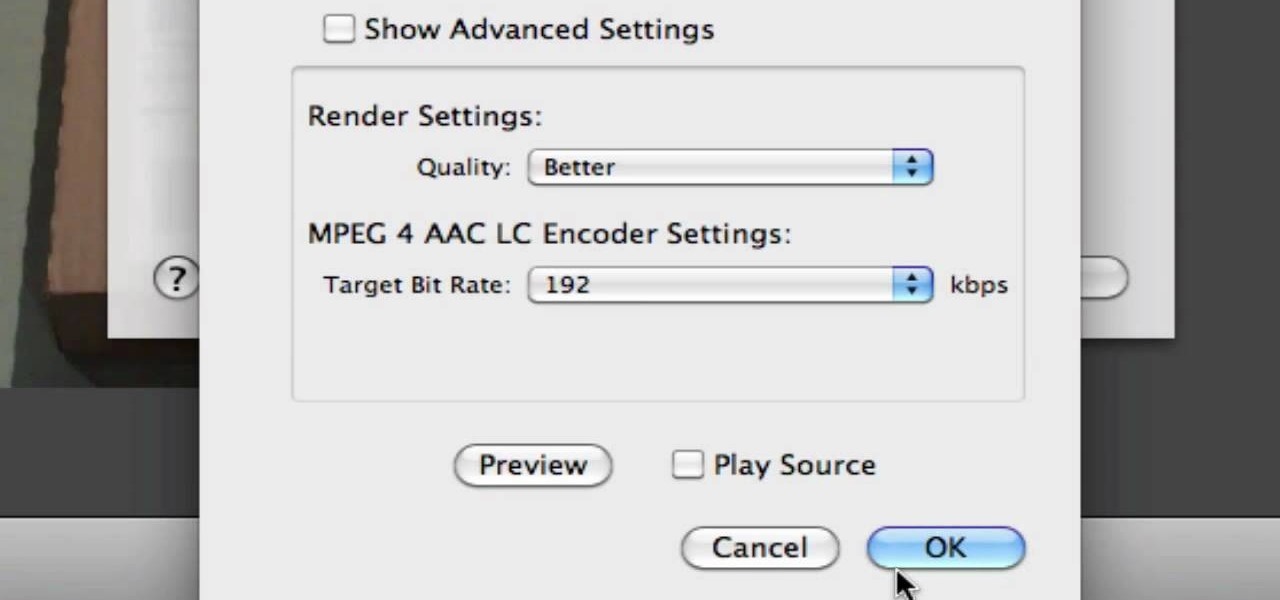
In this video from AppleGenius0921 we learn how to export videos using Screenflow in HD. Launch Screenflow, make sure you're editing is complete and go to File, then Export. A window will come up asking the name you want to save it as and where you want to save it. Make a good title that is relevant to your video. Now click customize. Then click settings. Now go to compression type and double click H.264. Set the quality on Best. Click OK and use no filter. Now go to size and click 1280x720 H...

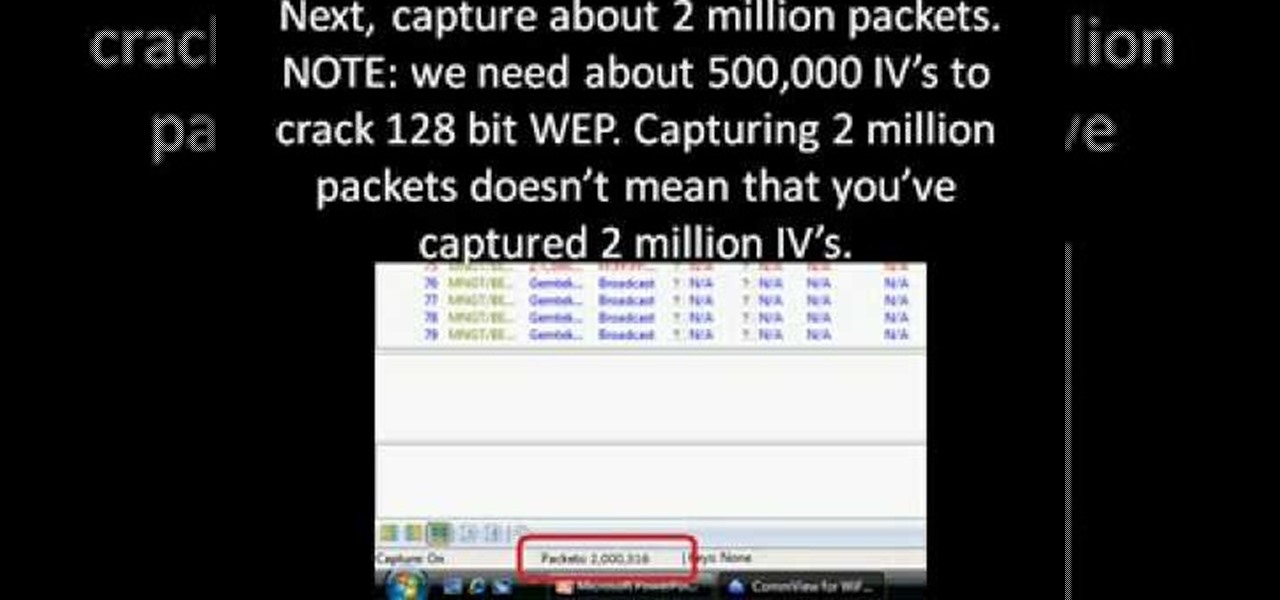
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.