
How To: Insult someone with the perfect insult
Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.


Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

Don't let the fear of those red, itchy mosquito bites keep you from enjoying the outdoors this summer. Even if your mosquito repellant doesn't work and you end up getting bitten there are some easy household items that will alleviate any discomfort.

A clogged drain is not only an unpleasant but seems to happen at the most inconvenient time. Good thing there is a simple way to unclog most minor stoppages with a few household products. Be your own plumber and keep those drains free and flowing.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another group competition game. This game is known as stack the chair. You can easily get this at one of your local Mal-Mart's, K-Mart's, or Target. These chairs came in a package. Don't forget to divide the group of party guest in half. So let's say you have 20 guests, 10 in one group, 10 in the other and their goal is t...

When Treasury Wine Estates released 19 Crimes Snoop Cali Red this summer, named for its new partner in wine, rapper Snoop Dogg, it already came with the brand's signature AR-enhanced label.

With Samsung's One UI version of Android, it's easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in an overlay ribbon that can also get in the way.

Samsung simplified the interface in its Camera app for the Galaxy S20. It's easier to use for the most part, but now you have to go digging to access certain camera modes. To make up for this, One UI now lets you rearrange the tabs in the Camera app.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

The Halloween season is the perfect time for telling scary stories, but augmented reality is here to bring the tradition of frightening children to the modern age.
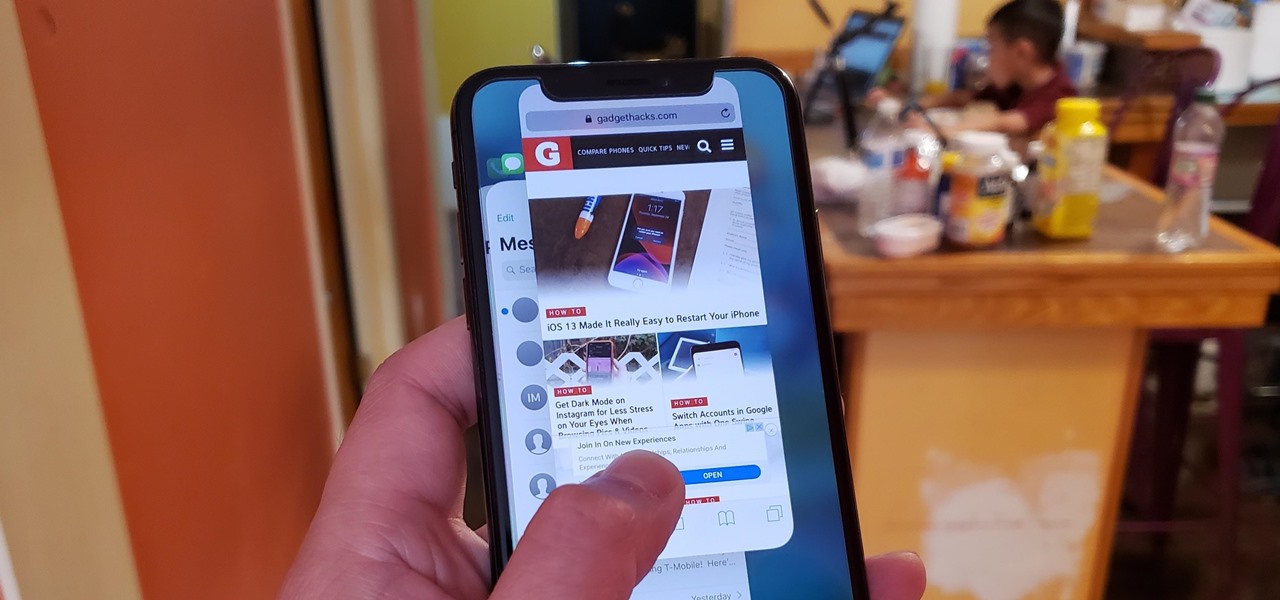
As efficient as your iPhone is, it doesn't hurt to fully close running apps from time to time to free up memory and keep background processes to a minimum. Force-closing is also a great way to troubleshoot buggy apps, and can often resolve minor issues without having to restart your device.

In recent days we've covered the marriage of augmented reality and top-tier music artists. This time, though, the music stars are showing off the tech rather than integrating it into their act.

While Modiface, YouCam, and others have been playing in the virtual make-up marketing pool for a while, here comes Google ready to splash down with a cannonball.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat.
One of the most prestigious annual events for the advertising industry, the Cannes Lions is the ideal backdrop for Snapchat to show the brands and agencies in attendance what it's got.
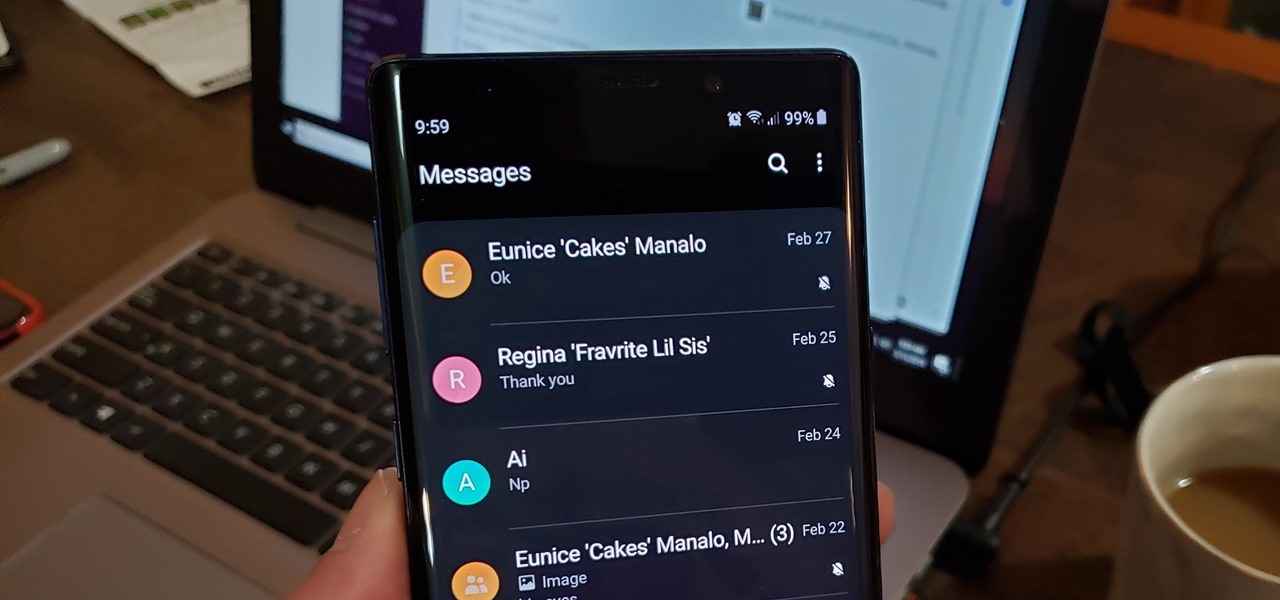
Text conversations and group chats can sometimes devolve to random and nonsensical chatter that bombard you with annoying notifications. Naturally, this can get distracting and prevent you from focusing on more pressing matters. Fortunately, Samsung Messages has a feature built in to minimize distractions whenever conversations go out of hand.

A major software tool first promised during the reveal of the HoloLens 2 earlier this year is finally available.

Apps that can display virtual furniture in the home are one of the most popular applications of mobile AR today, but Houzz has decided to raise the stakes with its latest update.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

Apple has finally released iOS 12 for everyone to enjoy, and there are plenty of cool features to go around. Perhaps the coolest feature, at least, for those of us with an iPhone X, is the return of an oft-used gesture we loved on other model iPhones.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

Burning Man 2018 is underway, but Intel and the Smithsonian American Art Museum are giving those not in attendance the ability to view the art from the event through Snapchat.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.
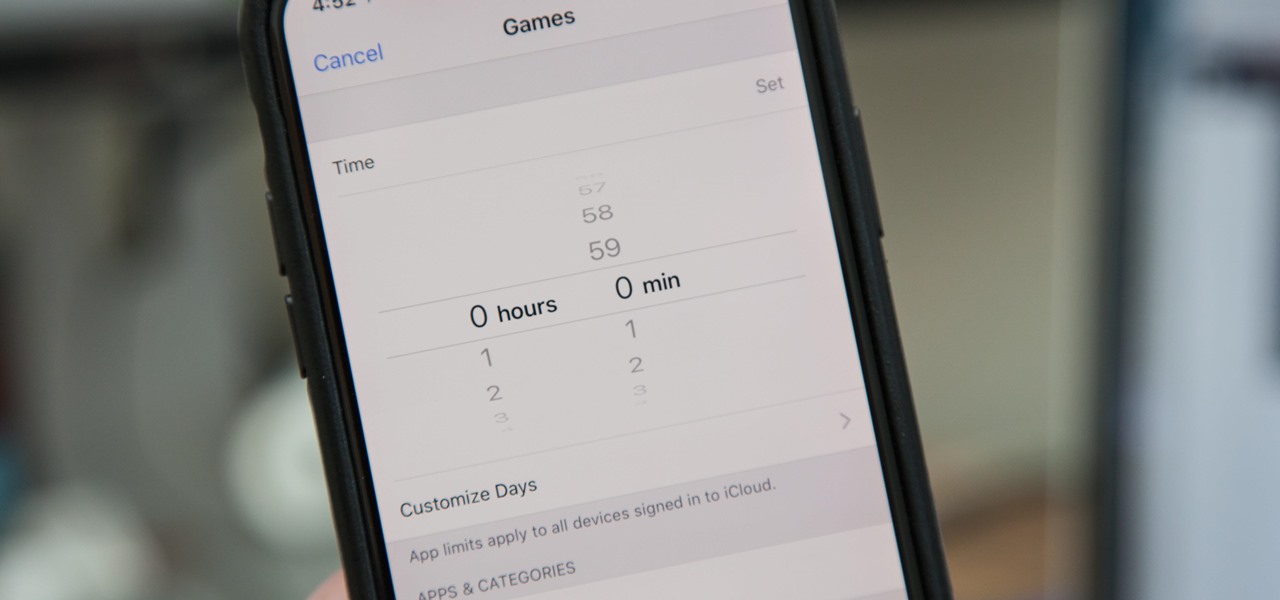
Most of us have, at one point or another, found ourselves glued to our smartphone in a trance-like state, totally unaware of what's around us. Well, Apple has a way to curb overuse with an awesome tool for iPhone starting in iOS 12. It can help nudge us away from our phones to spend more time attending to real-life matters.

Apple's lead marketing tool for the iPhone X, 3D Animoji that you control with your facial and head movements, are once again in the spotlight in a new commercial the company posted on its Korean YouTube account this week.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.
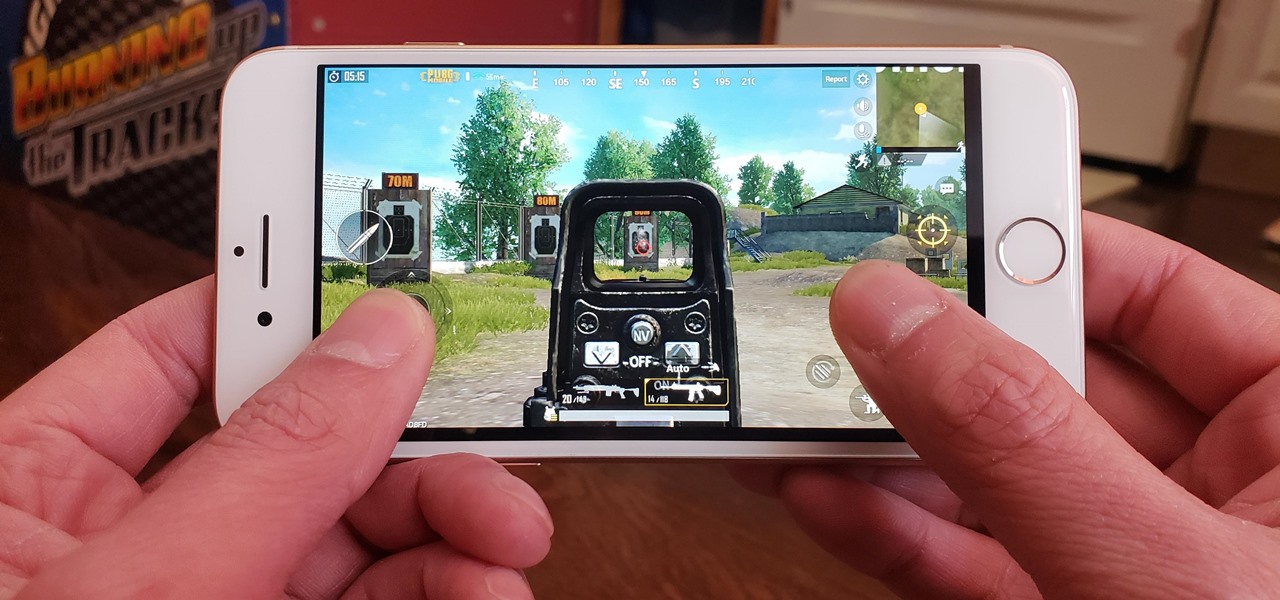
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

The Tesla-riding Starman that was launched into space via Elon Musk's SpaceX last week will miss its Mars target and is instead headed toward a lonely asteroid belt in the void of space. But if you missed the initial launch and would like to get a taste of what Starman is seeing, you can now take a short ride along thanks to a new Snapchat Lens.
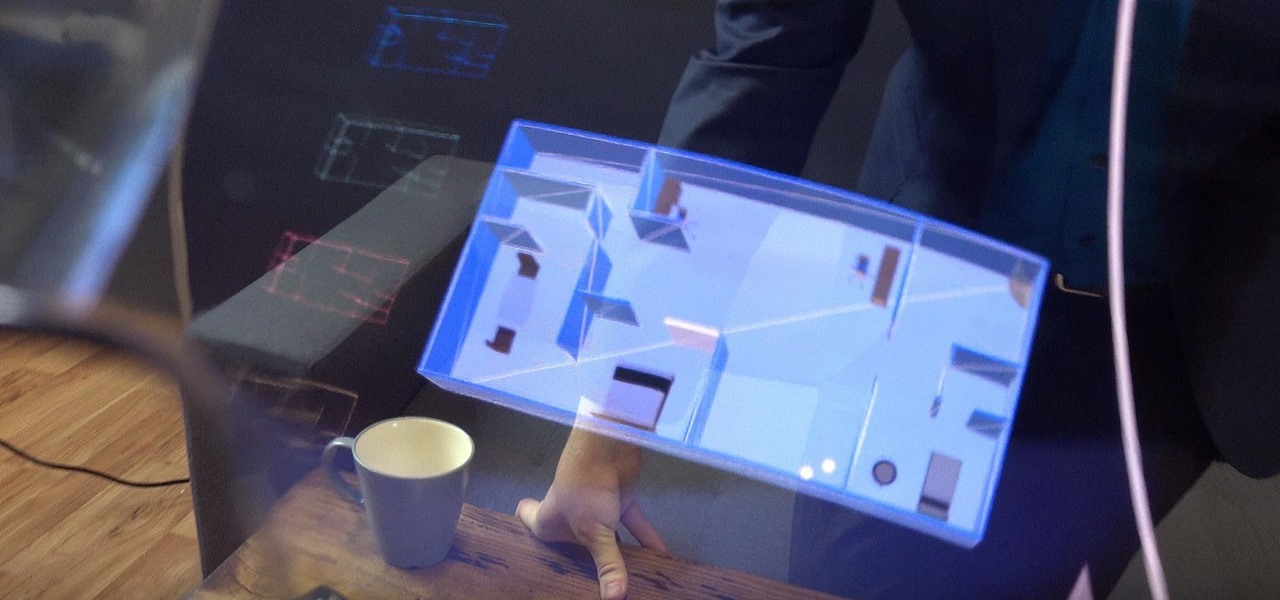
In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

Although expected to be only a modest upgrade over the S8, we can't help but be excited about the Galaxy S9's unveiling late next month. Among the many rumors and questions we're looking to see addressed, one of the biggest queries we have is, of course, with the price tag. We might not have to wait a month for the goods, however, thanks to a new pricing announcement out of South Korea.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.