Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

With a new installment of the Saw horror series opening in theaters nationwide this weekend, Lionsgate is betting its ad dollars on immersive advertising to sell tickets.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

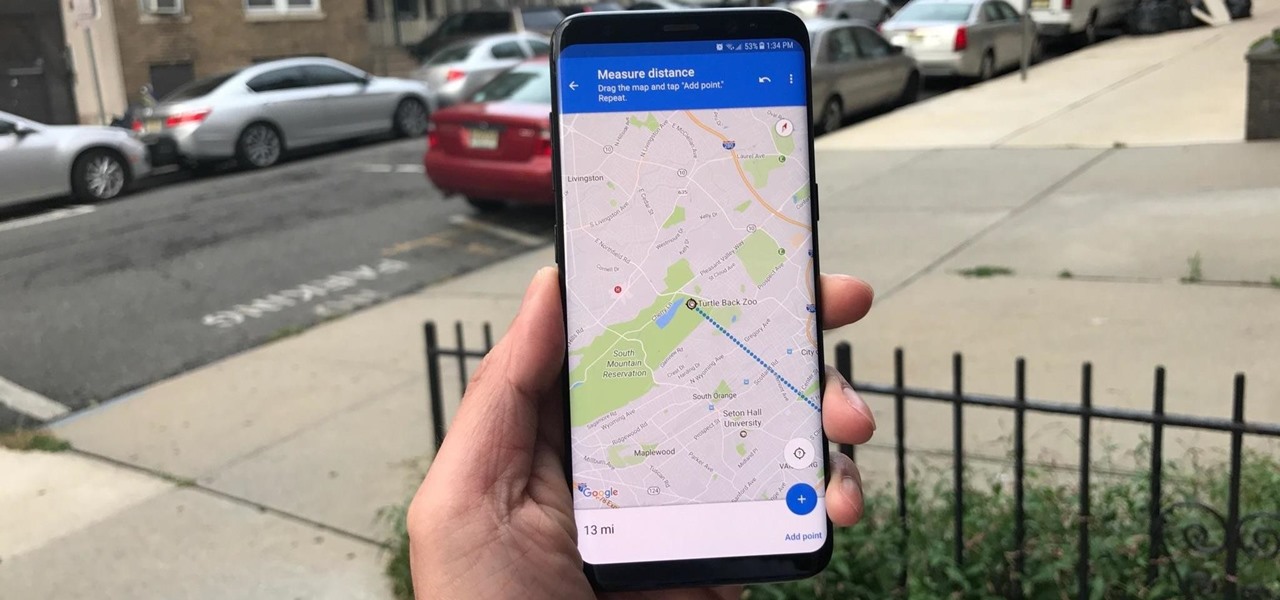
If you want to find out the linear distance between your hotel and a landmark or restaurant you want to visit, Google Maps has a great feature that lets you quickly measure the distance between two or more points. It's perfect for getting an idea of how far places are in relation to each other, which can help you plan trips more efficiently.

San Francisco-based startup AstroReality is putting the AR in lunar with a high-detailed model of the moon that comes to life through an accompanying augmented reality mobile app.

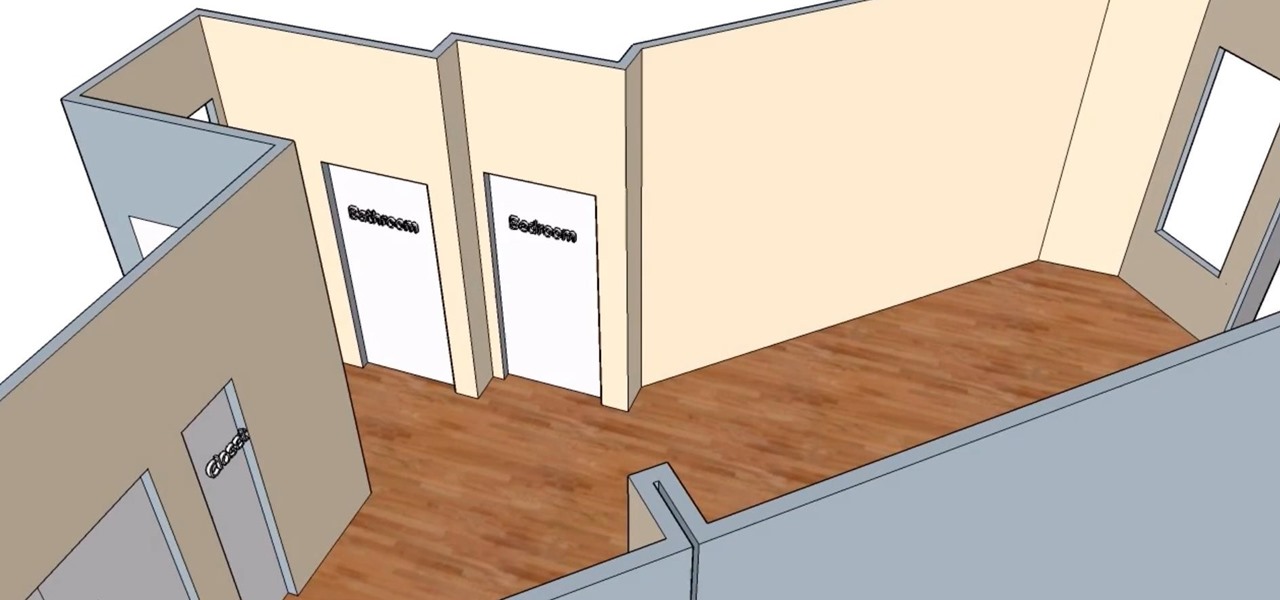
Measuring a room has never been so easy thanks to Apple's ARKit. SmartPicture 3D is known for its quick measurements based on pictures from your smartphone. Recently, they released a video of the company measuring a room using the ARKit.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

Screen mirroring app iDisplay has arrived for Vuzix M300 Smart Glasses. With the app installed on the M300 and the companion software running on a Mac or Windows computer, users can mirror or extend the computer's desktop to the headset's display, which is connected to the computer via Wi-Fi or USB cable. The app does not yet appear on Vuzix's app store.

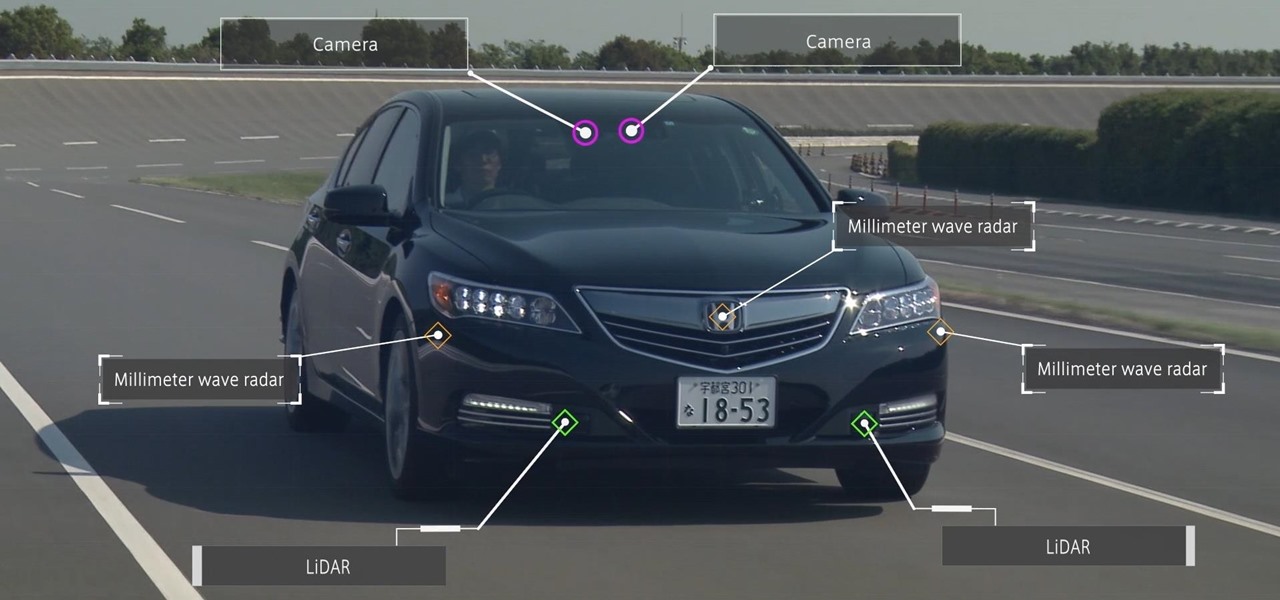
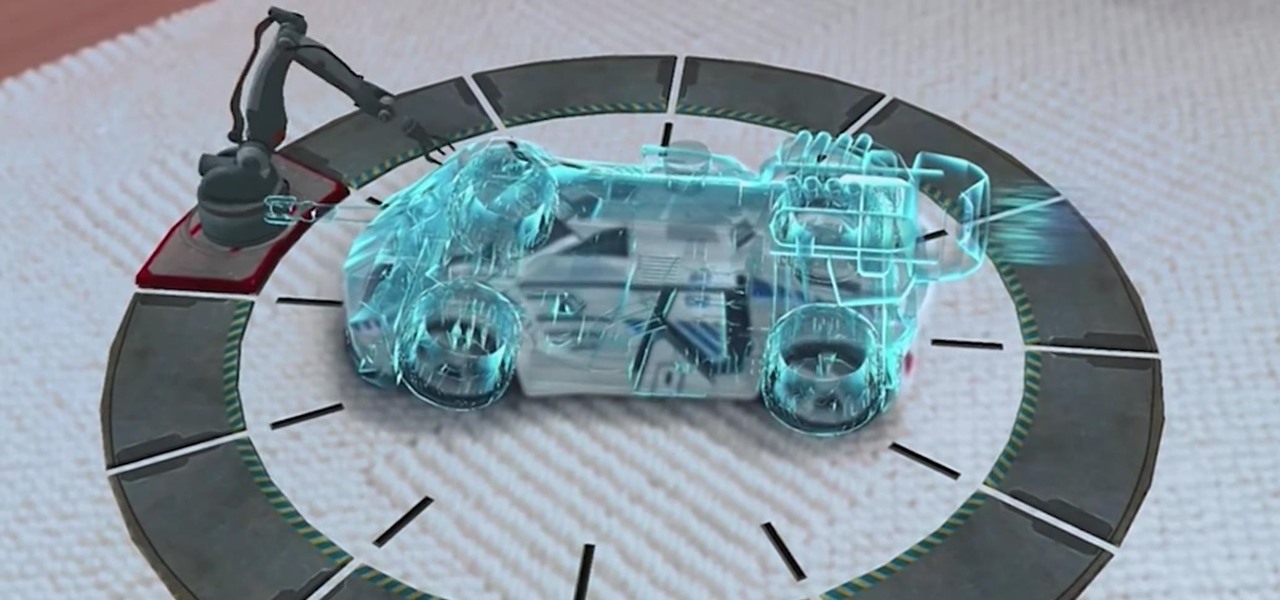
Honda president Takahiro Hachigo has just announced that Honda will complete development of fully self-driving cars by 2025. While the company aims to have level 3 — or conditionally autonomous cars requiring human intervention only in emergencies — on the road in time for the 2020 Tokyo Olympics, these level 4 cars would require no intervention in most environments and thus bring Honda one step closer to producing fully driverless cars.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

In mid-November, Vuforia officially released Vuforia 6.1, which has full support for the Microsoft HoloLens. They also released their AR Starter Kit to the Unity Asset Store, which contains scenes that show you how to use Vuforia features. While I have yet to find any confirmation, I believe it is safe to assume that the AR Starter Kit will work with the HoloLens. I already had a Vuforia tutorial planned for this week, so as soon as I know for sure, I will begin working on it.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

In the past, some of Google's Nexus devices have had root methods even before the phones hit shelves. The Google Pixel and Pixel XL are basically Nexus devices from a software standpoint, so why have we gone more than a week since release without a working root method or custom recovery?

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that today's devices are capable of doing far more than beeping at 7 in the morning.

When casting a flyrod, in most cases, tight loops will allow the fly to travel farther, more accurately, and with less effort. To cast these tight loops, the tip of the rod must travel in a straight line path, slack must be eliminated, and there must be a constant acceleration to a sudden stop. The most common mistake is using the wrist to move the rod which causes the tip to travel in a half circle or windshield wiper type motion.

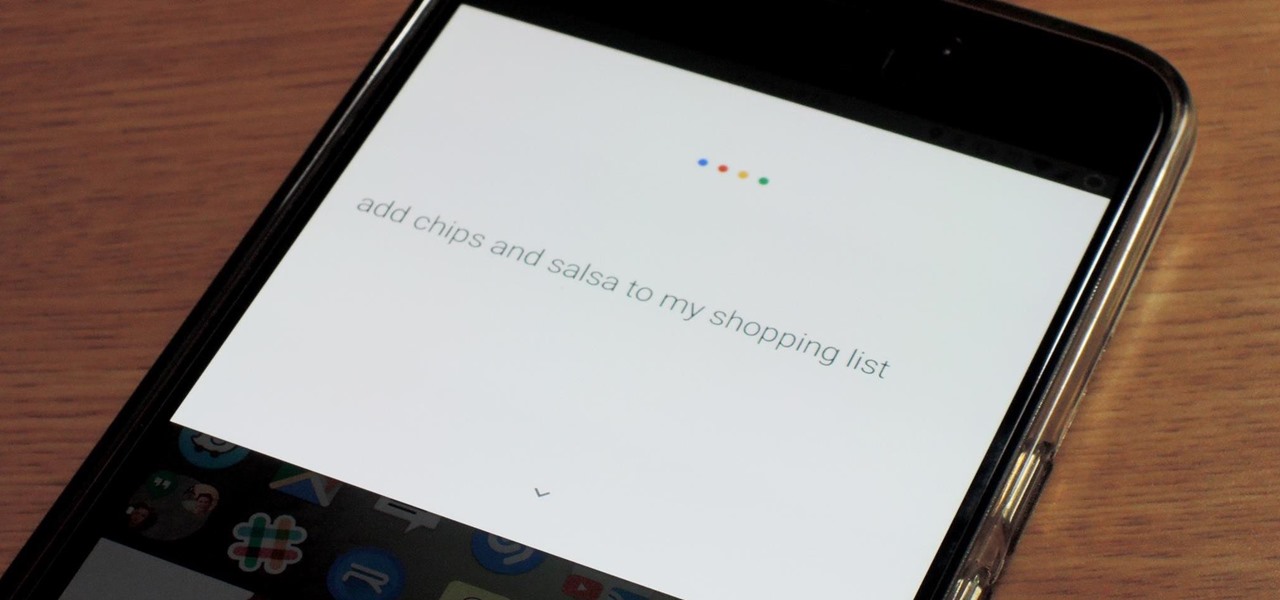
If you use Google Keep, you'll be happy to know that you can add items to lists and even start new ones with "OK Google" voice commands on Android, and it works fairly well. (Hat tip to Reddit user rambantu for finding this trick.)

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

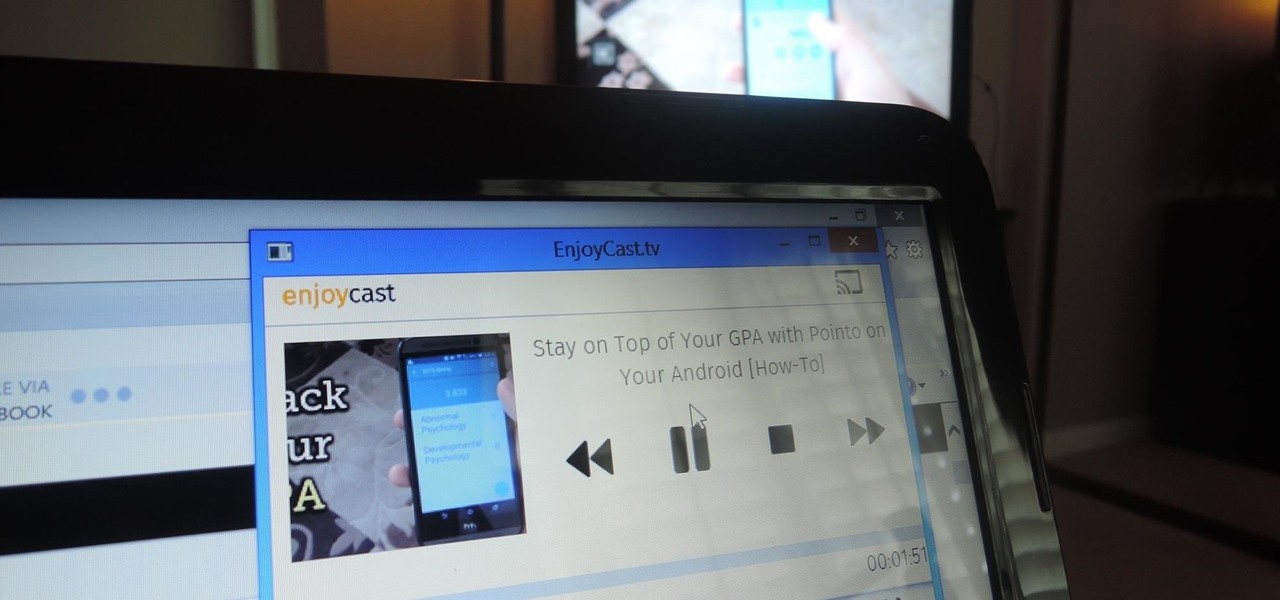
Google's Chromecast has been out for almost two years, and I can safely say it has changed the way I use my TV. At first it was a hassle to even get local media to play on it, but now casting has branched out to torrent streaming, which was a real game changer. Unfortunately, most apps only let you stream one video or song at a time, or you can't add magnet links or torrents to a playlist of local content.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.