Being infected with HIV means a lifetime of antiviral therapy. We can control the infection with those drugs, but we haven't been able to cure people by ridding the body completely of the virus. But thanks to a new study published in Molecular Therapy by scientists at the Lewis Katz School of Medicine (LKSOM) at Temple University and the University of Pittsburgh, all that may change.

The squiggly guys in this article's cover image are Propionibacterium acnes. These bacteria live in low-oxygen conditions at the base of hair follicles all over your body. They mind their own business, eating cellular debris and sebum, the oily stuff secreted by sebaceous glands that help keep things moisturized. Everybody has P. acnes bacteria—which are commonly blamed for causing acne—but researchers took a bigger view and discovered P. acnes may also play a part in keeping your skin clear.

Android lovers out there might be sad to hear that a high-end version of the Samsung Galaxy S8+ with 6 GB of RAM and 128 GB of internal storage won't be released in the US, but rather, in China.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

While augmented reality is mostly in the minds of consumers in the form of Pokémon GO, AR has been popular behind the scenes, with AR companies marketing it as a tool to help business operations become more efficient. This business-to-business market is the target of the new app DOTTYAR, which "provides 3D visualization tools for augmented reality viewers."
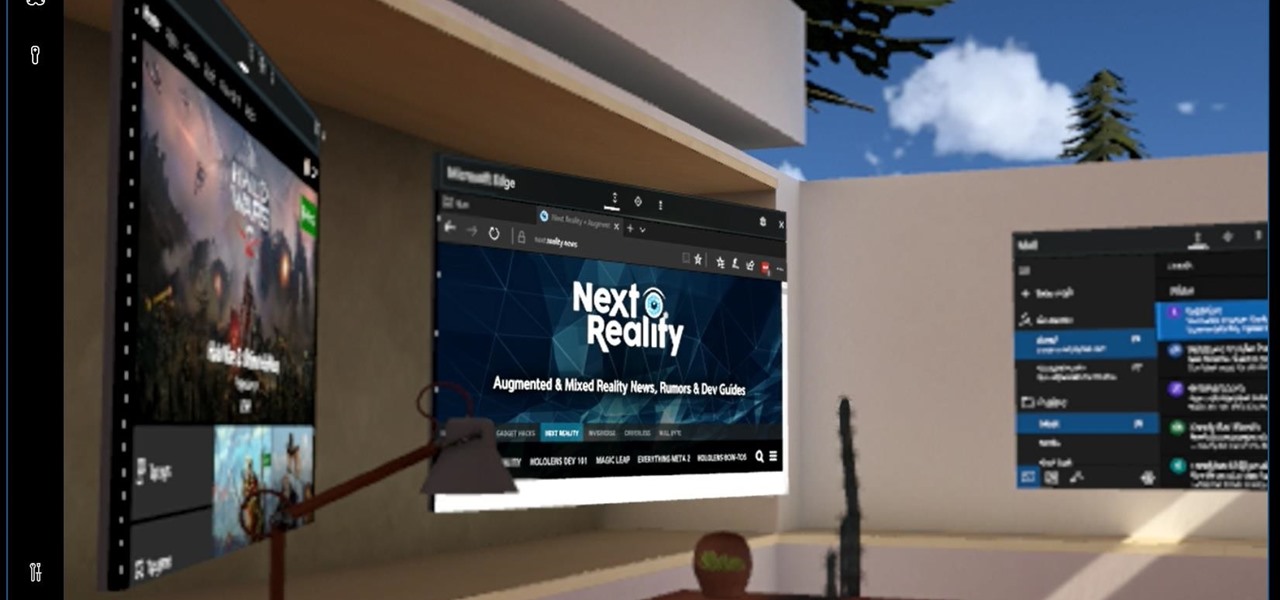
If you're part of the Windows 10 Insider Program, build 15048 launched this morning, and included a nice big unannounced surprise. You can now launch the Mixed Reality Portal and enable the simulation to try out mixed reality right from your PC, even if you don't have one of the new Acer dev kits.

By looking for the mechanism that allows influenza A to invade lung cells, scientists also discovered a treatment that might block the virus from taking hold there.

If you have stuck volume buttons, it can be a real pain to adjust sound levels since your only other option is to use the volume menu in Settings. But even if your volume rocker is working fine, it's still a little weird to have to click a mechanical button to control one of the most central aspects of an operating system that is otherwise entirely touch-based.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

A tiny louse is responsible for decimating the citrus industry. Diaphorina citri, the louse in question, better known as the Asian citrus psyllid, harbors and spreads the "Candidatus Liberibacter asiaticus" bacteria that causes citrus greening disease.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

DAQRI, a company mostly known for its odd but fun-looking industrial Smart Helmet, unveiled their new Smart Glasses product at CES 2017. Their smartglasses look like a strange attempt to answer the Microsoft HoloLens, and the price tag of $4,995 for the developer's edition reinforces that notion.

All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Thanksgiving.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

Looking past the obvious visual similarities between the iPhone 7 and Google's new Pixel phones, there are several indications that the search giant had Apple in its sights as they released their latest flagships. For once, this isn't an Android phone we're talking about, it's a Google phone—and it showcases Google's latest strategy.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Hello again, ***UPDATE: Adding links to the other Two articles****

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!
Welcome back Hackers\Newbies!

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

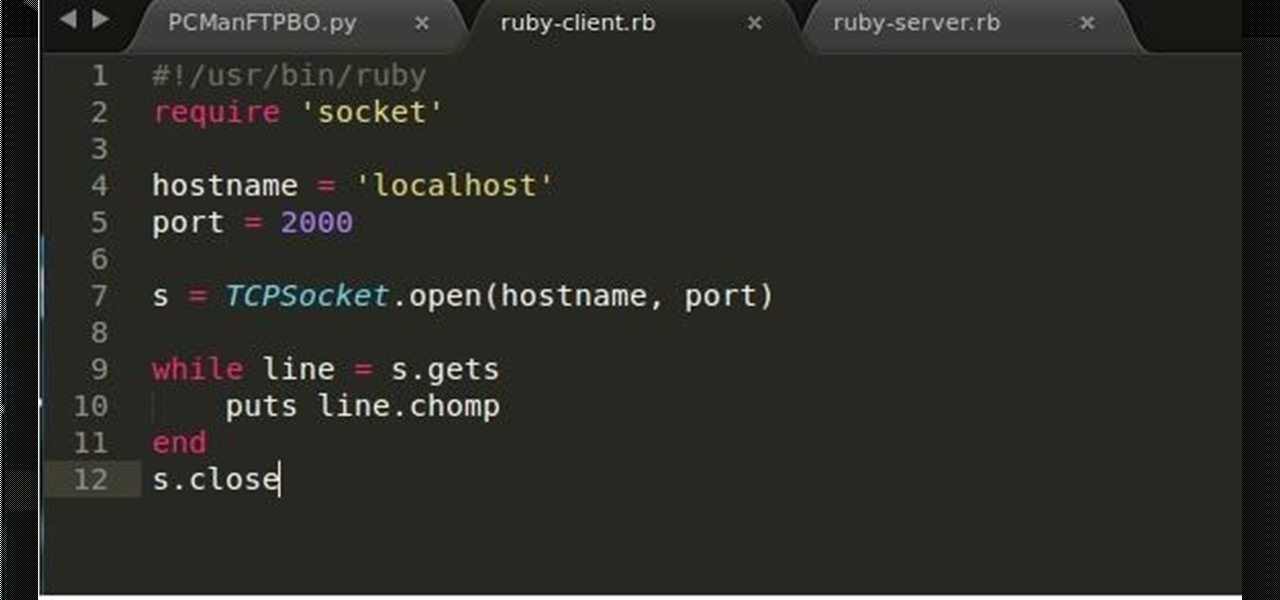
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.