Navigating through row after row of plants, my tiny fingers would reach into the leaves to pluck all the vile little creatures from their homes and deposit them into a can of gasoline. Potato bug duty, my least favorite gardening chore. Growing up, my family had a small garden every year. And every year, I was recruited to help plant, maintain, and eventually harvest the vegetables from it. There were some tasks I didn't mind, but the ones I hated most usually involved bugs (have you ever see...

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

As the holidays approach, so does that wonderful Autumn day where loads of people happily camp out in freezing weather in front of their favorite stores to save a few bucks on their favorite electronics. And yes, that day is near... Black Friday brings the biggest markdowns of the year, and that includes slashed prices on many of our favorite touchscreen devices, including the Kindle Fire HD, Samsung Galaxy Tab 2, and Nexus 7. Want to get your hands on an Android tablet for cheap? Below are a...

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

Today we're going to draw Spongebob! He's going to be facing forward, so even beginners should find drawing this guy to be a piece of cake! 1) Begin by sketching out a rectangle with a broader top and a narrow bottom, make sure it's not too skinny though. This will be the base of Spongebob's body.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

AdSense. It's a beautiful thing, isn't it? Google AdSense is something every website owner or blogger should use… it's what every blog needs… if you plan on making any money and surviving. So, how much traffic do you need to actually start making money via AdSense? This video will try and answer that question for you. You must have targeted traffic to drive your blog.

This Sports video tutorial shows how to hit the golf ball as a draw. Frank demonstrates in this video how to hit a draw. It is very easy to hit one. What you should aim to achieve is an inside outside swing. He has laid out three clubs on the ground. One club is on target line. The other two clubs are parallel to each other and are on swing path line with the ball placed in their middle. When you swing your club back, go through the two clubs winding up. In the unwind portion, your club shoul...

You either love politics, or you don't, but office politics are entirely different than your local elections. It could mean respect, raises, or could even mean your job. Just staying out of it could stunt your career. Here’s how to jump in and get ahead – without getting burned.

Do you live in a dangerous neighborhood? Even if your area isn't known to be dangerous, it could still be a target of home burglaries. Don't let the thieves have the upper hand. Make sure the only thing they're stealing is grass. To properly secure your home from external threats, you must find weaknesses potential and potential entry points and fix them.

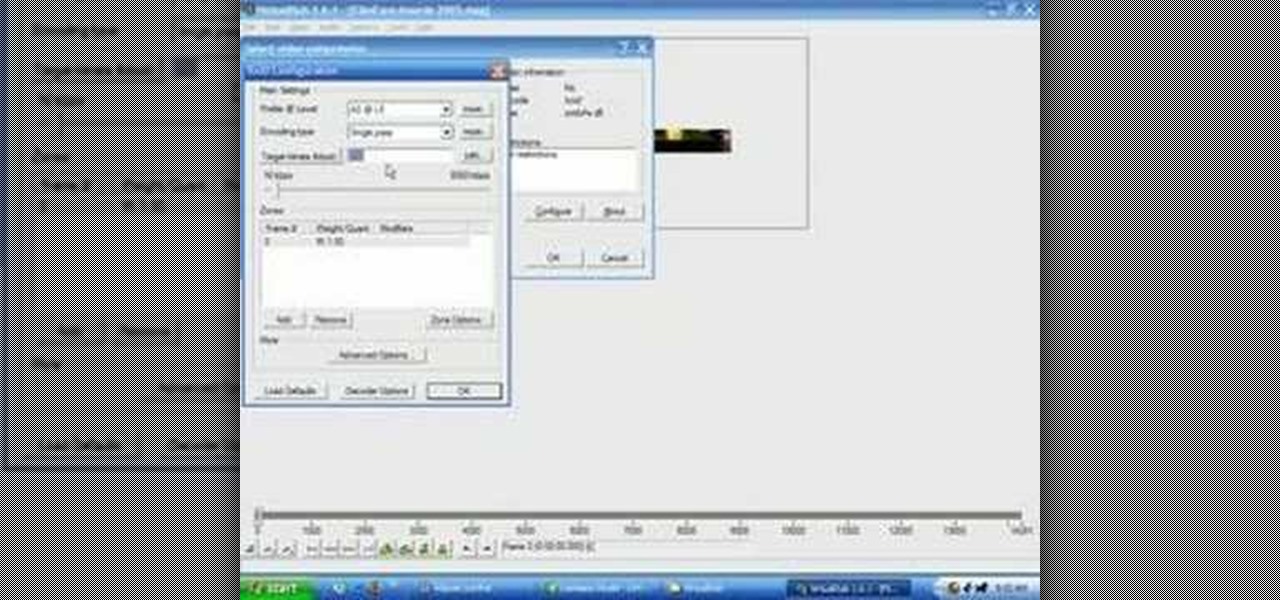
This quick video will show you how to compress a video file. To compress a video file you will need software called Virtual Dub. Open Virtual Dub and open a video file you want to compress. Click on Video Compression Choose the video codec named Xvid, and click on Configure. Select AS@L5 and Single Pass. Click on the target button, select 300kb. Go to Audio Compression. Select MPEG layer 320kb stereo sound. Save as an AVI. When it's finished the file will be on your desktop.

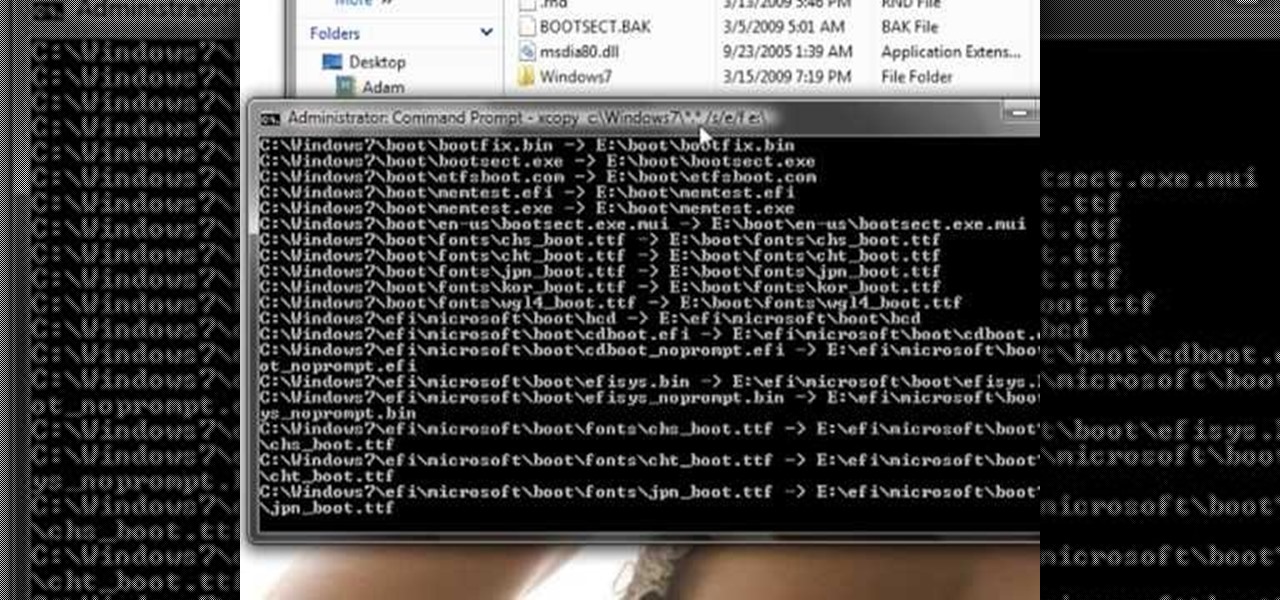
This guide works 100% for Vista & Windows 7, unlike most of the guides out there. The method is very simple and hassle free. Needless to say, your motherboard should support USB Boot feature to make use of the bootable USB drive.

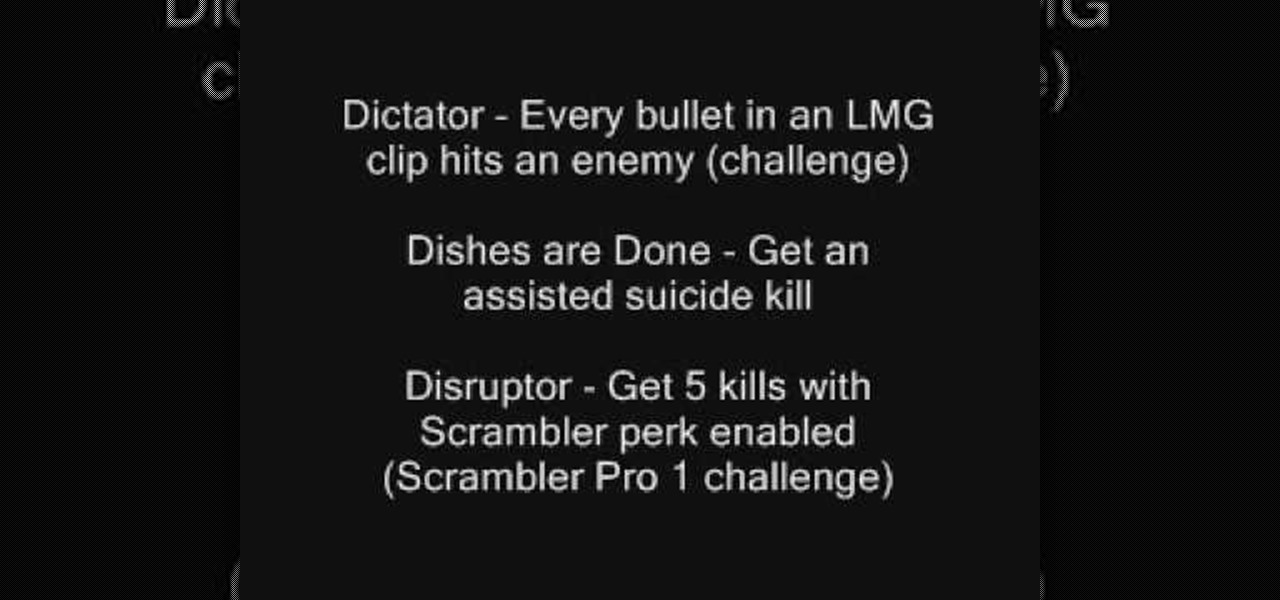
In Call of Duty: Modern Warfare 2 (COD4), there are titles that you can unlock for use on your Callsigns. If you want to know how to unlock all of the titles, this three-part video list them all and how to achieve them.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

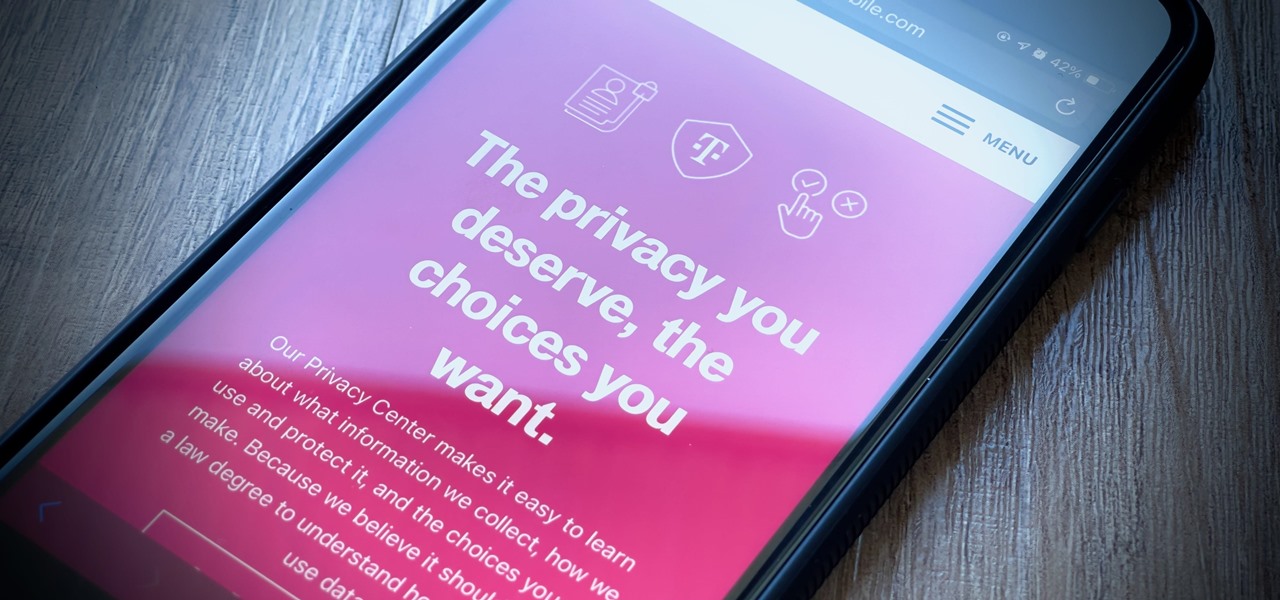
It's getting harder and harder to escape ad tracking by the day. For the latest example, look no further than T-Mobile. The No. 2 carrier updated its privacy policy on Feb. 23, 2021, indicating that it would start sharing customer data with advertisers under the guise of more relevant ads starting April 26. If that's not something you'd like to participate in, there's a way to opt-out.

The team over at Spatial isn't done innovating its way through augmented reality in 2020. Just days after adding a mobile option to its groundbreaking Spatial virtual collaboration product, the company is releasing Tele, a new app geared toward more casual, AR-powered video chats.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

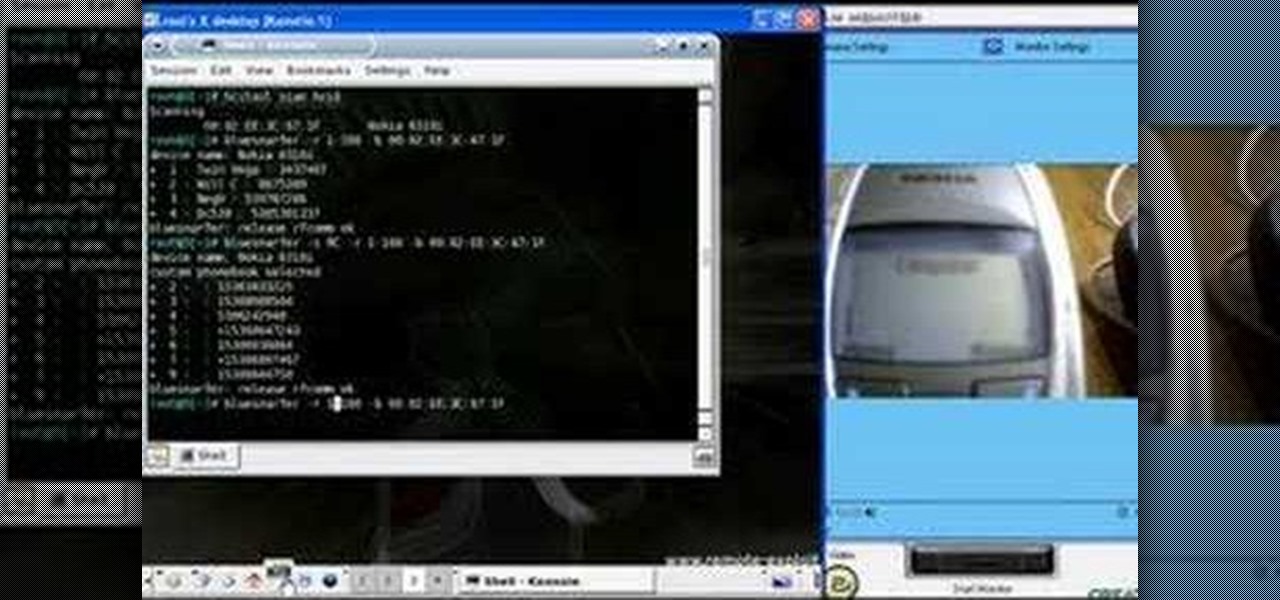
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

"I want to make video games" — Is there anyone who hasn't ever thought that? It's almost universal among gamers to want to get on the other side of the screen and design the games themselves, especially those of us who have played less than impressive games and thought that we could do a better job. But it's hard to know where to start — or how — when it comes to creating our own games.

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

The Lens Studio app has become a cornerstone of Snap and its augmented reality technology portfolio by giving developers, creatives, and novices the ability to create augmented reality camera effects for Snapchat.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

The next big phase of iOS 14 has started with the release of the iOS 14.4 beta. Right now, the developer-only beta features only one known item. Apple introduced the ability to scan App Clip Codes in iOS 14.3 with the Code Scanner control, and now in iOS 14.4, you can launch a local App Clip experience via Camera, NFC, Safari Smart App Banner, or iMessage.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

We're living in the age of Big Data. As the primary force behind everything from targeted marketing campaigns and online search algorithms to self-driving cars and even space exploration, massive sets of complex data stand at the heart of today's most exciting and important innovations.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

For Android 11, Google is doubling down on the handy App Suggestions feature that debuted in Android 10's app drawer by expanding it to the home screen dock.