Zune is a digital media players and services sold by Microsoft. It includes portable media players, client software, and the Zune Marketplace Internet music and video store. If you hate the Apple iPods, you probably have one of these MP3 players.
In this video tutorial, Chris Pels will show how to share data in between JavaScript and server-side code by using a hidden field in an ASP.NET page. Next, learn how to use the RegisterHiddenField method in server-side code to programmatically create a hidden field on the client. In addition, see how to programmatically create a HiddenField server control for sharing data on an ASP.NET page. Finally, use the RegisterArrayDeclaration method to create a container in server code for storing mult...

Digital video recorders, or DVRs are changing the way people watch TV. Check out this comparison of the top DVRs on the market.

Bring a little joy and festivity to this holiday season, check out this do-it-yourself video to see how to make a festive holiday wreath, perfect for creating that festive atmosphere around your house during Christmas. At home on your front door or in a hallway, this cheerful Christmas wreath decoration is a cinch to make and sure to liven the Christmas spirit.

Phil and Charlie explain how its done in space. Each Space Shuttle has a toilet that can be used by both men and women. Designed to be as much as possible like those on Earth, the units use flowing air instead of water to move waste through the system.

This match has me playing against the Alekhine's Defense. As my opponent was rated significantly higher than me, I tried something a little risky in the beginning with a bishop sack. My opponent probably should have been able to win, but I think the sack through him off guard and probably made him feel like this would be an easy win, which caused him to make some positional mistakes that I was able to capitalize on. Watch and store it in your own arsenal.

Watch to learn how to say the names of the types of things you find in an antique store or at a flea market in French.

When decorating for the holidays, try using as many natural materials as you can. The choices are virtually endless, from the grocery store to the garden. Some of the most effective Christmas decorations you can make are garlands. You can hang Christmas garlands over windows, over doors, over the mantle or even on Christmas trees.

If you love topping your salads with ranch dressing, then try making it at home! This make-ahead seasoning mixture allows you to stir some together in a snap. You will need saltine crackers, garlic salt, onion powder, dry minced parsley flakes, minced dry onion, dry dill weed, garlic powder, mayonnaise and buttermilk. Make a dry ranch by blending the crackers in a blender until it is powdered. Add parsley, minced onion and dill weed. Blend again. Pour mixture into a bowl. Stir in garlic salt,...

When a recipe calls for chopped chocolate, it can be hard to decide which tool to use for the job. Chocolate-breaking forks, sold in many specialty stores, may easily break chocolate into chunks, but they also punch holes in cutting boards and scratch countertops. Paring knives are too small for the task and, when working with a really big piece of chocolate, it's easy to ruin the blade of a chef's knife hacking into the dense, hard bar. The best tool for chopping chocolate is a 10-inch slici...

Love the taste of fresh ginger, but hate throwing out dry, moldy roots? Solve the problem by storing it in the freezer. Whenever you have a hankering for fresh ginger, just grate the still-frozen root into your favorite recipes. Ginger will lose some of its potency in the freezer, but not enough to make a significant difference. When previously frozen ginger thaws completely it develops a sodden texture, so once frozen it's best to keep it that way. Frozen ginger is also a little bit easier t...

You can edit videos in Windows Movie Maker. Movie Maker allows you to make videos. What you will want to do first is open pictures or a video that you will want to use. Select however many images or videos you want to use. Create a title and credits for this video. You can select whatever type of font and font color that you want to use. The next step you will want to do is add Audio. You can do this by looking under Tasks on the far left side of the page and add whatever audio from your hard...

Follow along as we are shown how to make a movie in Windows Movie Maker. -To begin, open up Windows Movie Maker, if you do not have this you can download it at http://www.microsoft.com

This dance tutorial teaches you how to do swing dance routines from great classic films. The moves in this tutorial are based on the 1929 film short "After Seben." Footage is of Shorty George Snowden and his partner, sometimes credited as Pauline Morse, at other times identified as Big Bea. The music is by Chick Webb and his orchestra.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

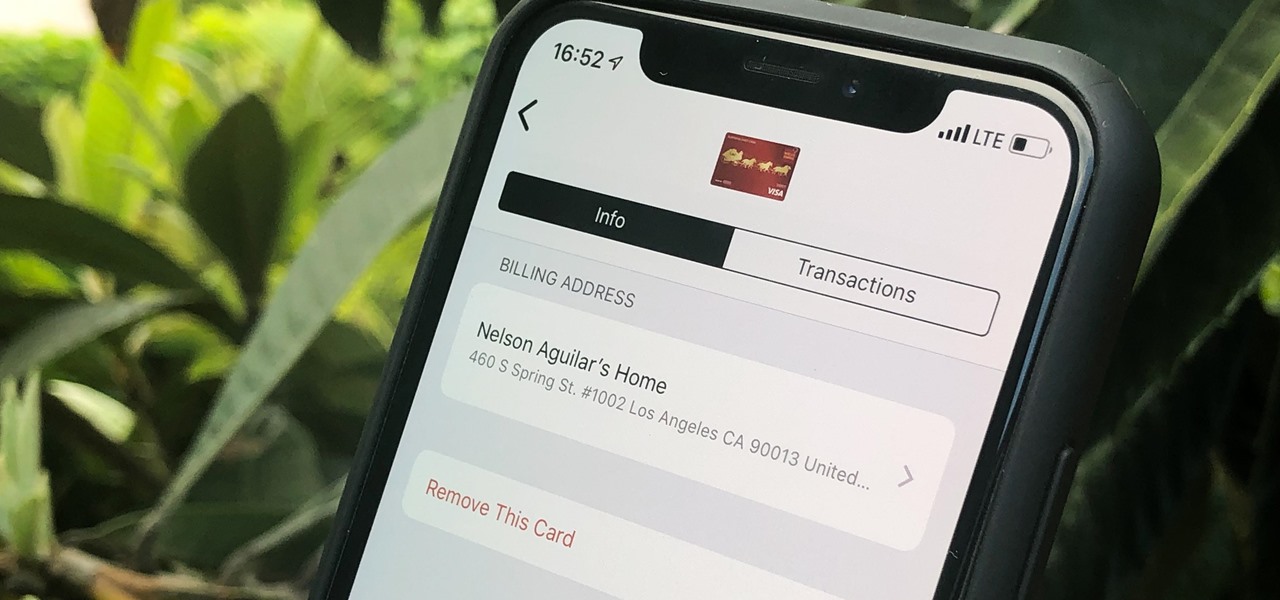
Apple Pay can be used at retail stores, restaurants, markets, and millions of other locations in the US and abroad. It's used to buy everything from clothing to groceries and vending machine snacks, so it's important to ensure that the cards in your Wallet are always up to date with the correct billing and shipping addresses.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

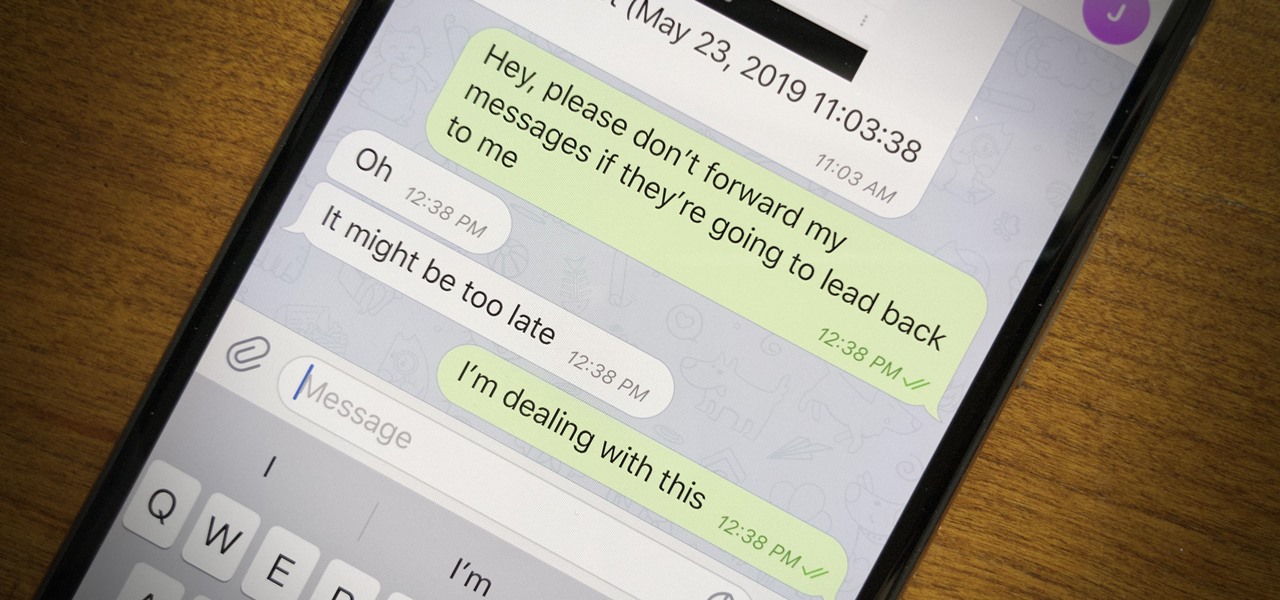
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Luckily, you can make your messages anonymous, so anyone receiving messages of yours that are forwarded won't be able to see you originally sent the message.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

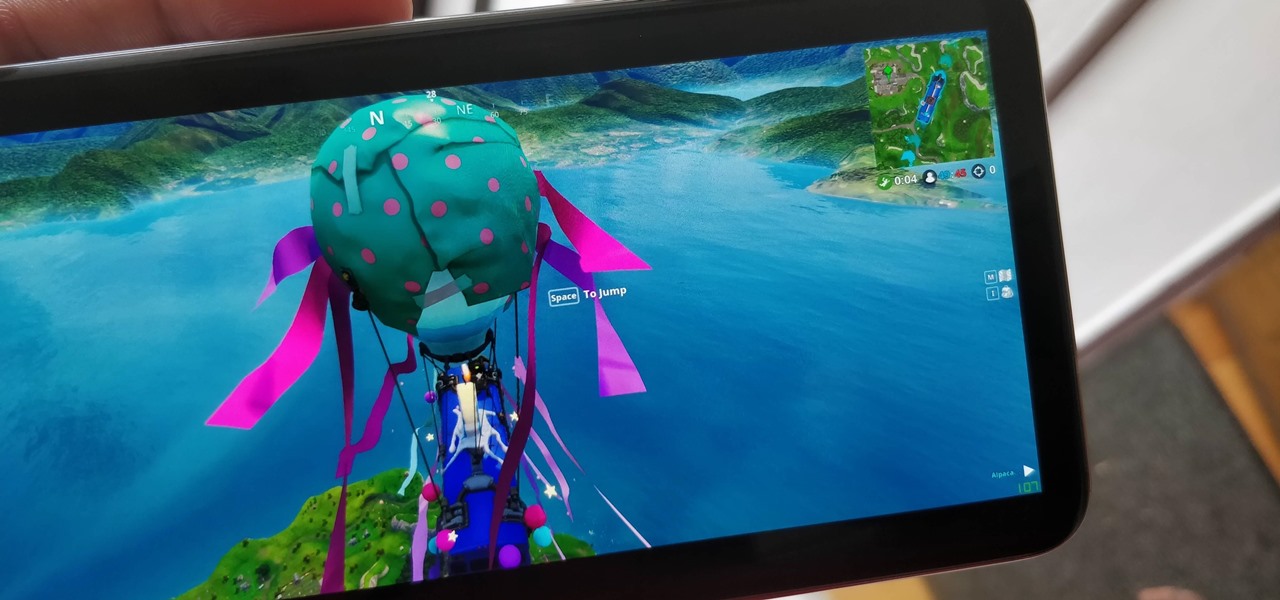
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

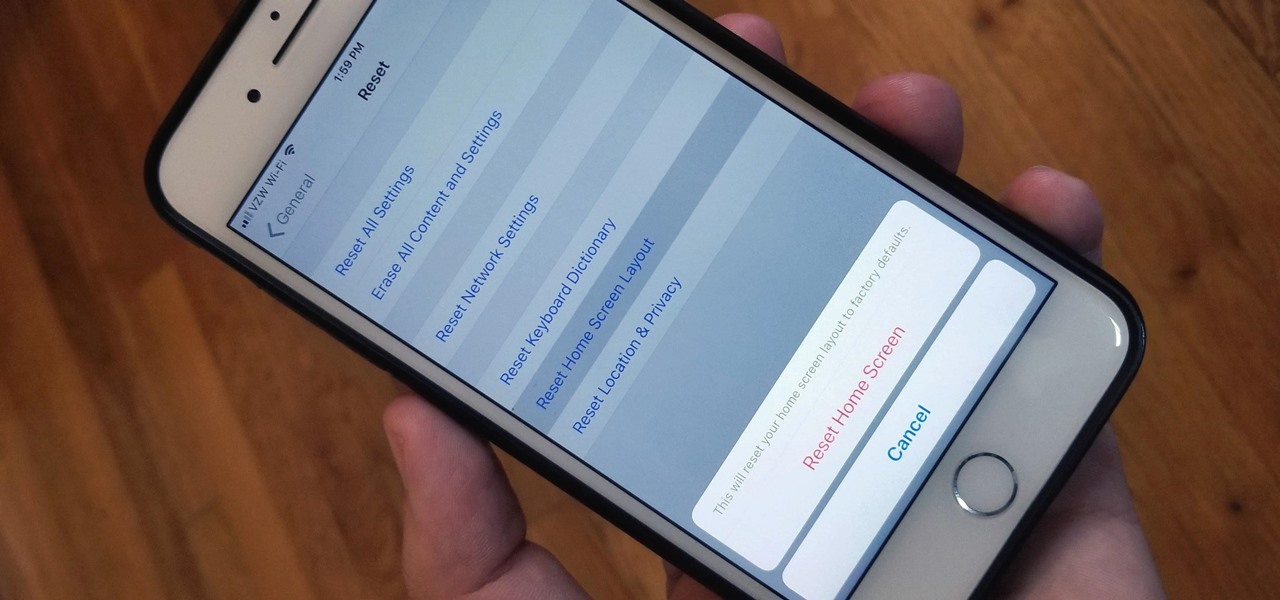
Unlike on Android, you can't easily hide your iPhone apps. Sure, you can nestle them away in folders labeled "junk," but they're supposed to be omni-present somewhere on your home screen. That is, until one day they're just ... gone. The fact that some of your apps disappeared only makes it more frustrating because there's no logical reason why they should have, right?

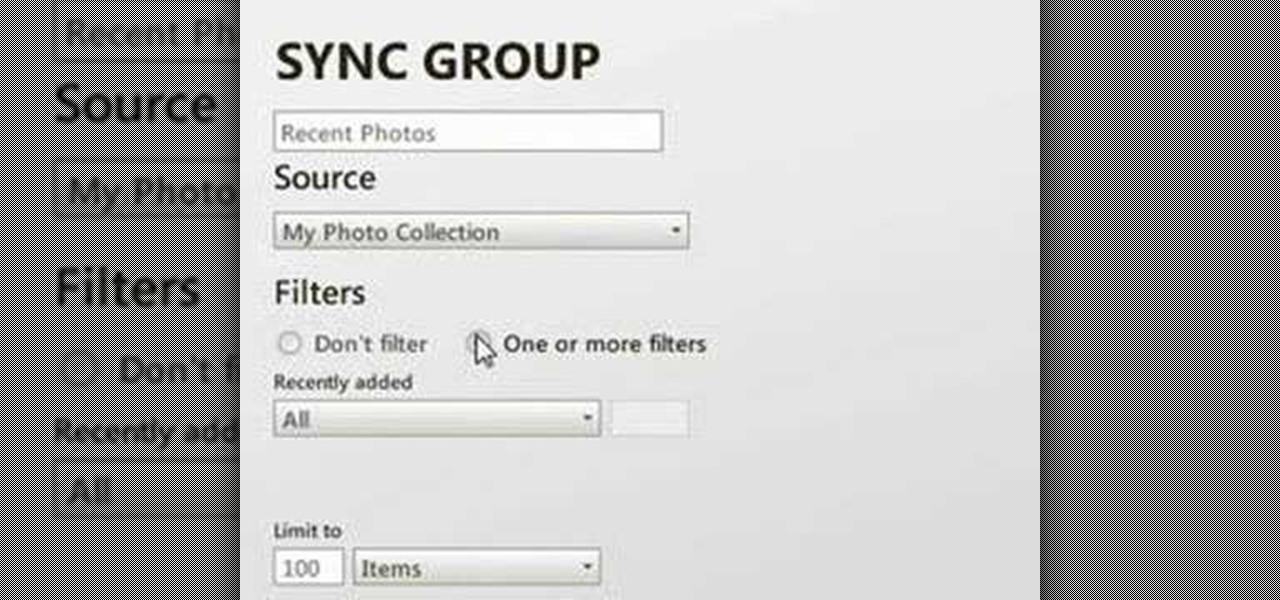
In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

Cheese is one of the most loved foods in the world, and there are hundreds of different types. Some prefer super expensive gourmet cheeses, others are fine with the cheaper processed stuff.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.