In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

The 12.9-inch iPad Pro was released in stores on November 11, 2015, and a couple days later I went to an Apple Store and to check it out in person. I had mixed feelings about the tablet, but was intrigued overall—so much so that over the next few weeks, as I found myself hearing more and more about the device, a thought began to take hold in the back of my mind—I really want one. At the same time, I was hesitant about dropping roughly 10 Benjamins for a tablet!

So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

Wear your heart on your sleeve - literally - by crafting this origami heart pin. Show some love for Cupid's holiday by creasing and folding your way to origami perfection.

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

Most girls dress up only one way during Halloween: With a suitably colored bra (green for a leprechaun, pink for a bunny, for instance) and teeny mini skirt in a matching shade, plus some sort of headpiece so people don't just think they're hookers.

In this video, Betty demonstrates how to make sweet and crunchy sesame seed brittle. This is hard candy, packed with sesame seeds. It's easy! So easy, in fact, that this free video cooking lesson can present a complete overview of the process in about nine minutes. The full recipe follows below.

Need to eliminate those pesky leg hairs but want to bypass the credit card bill? Then read below for a homemade sugar wax recipe and watch the video to learn how to rip off your hair!

Are you a radio control car enthusiast who's never moved beyond the store-bought toy models from Radio Shack? Then this nine-part series of videos is what you've been waiting for. It breaks down how RC engines work in exhaustive detail, including whole sections on carbs, pipe tuning, fuel mixing, and super chargers, among other topics. You may not be able to put your own RC car together entirely from scratch after this, but you will have a broad, deep understanding of how their engines work a...

1. First of all you need go to the 'view' button at the top bar menu. From the drop down click on 'view options'. Then click a 'check mark' against the 'kind' and then click 'ok'.

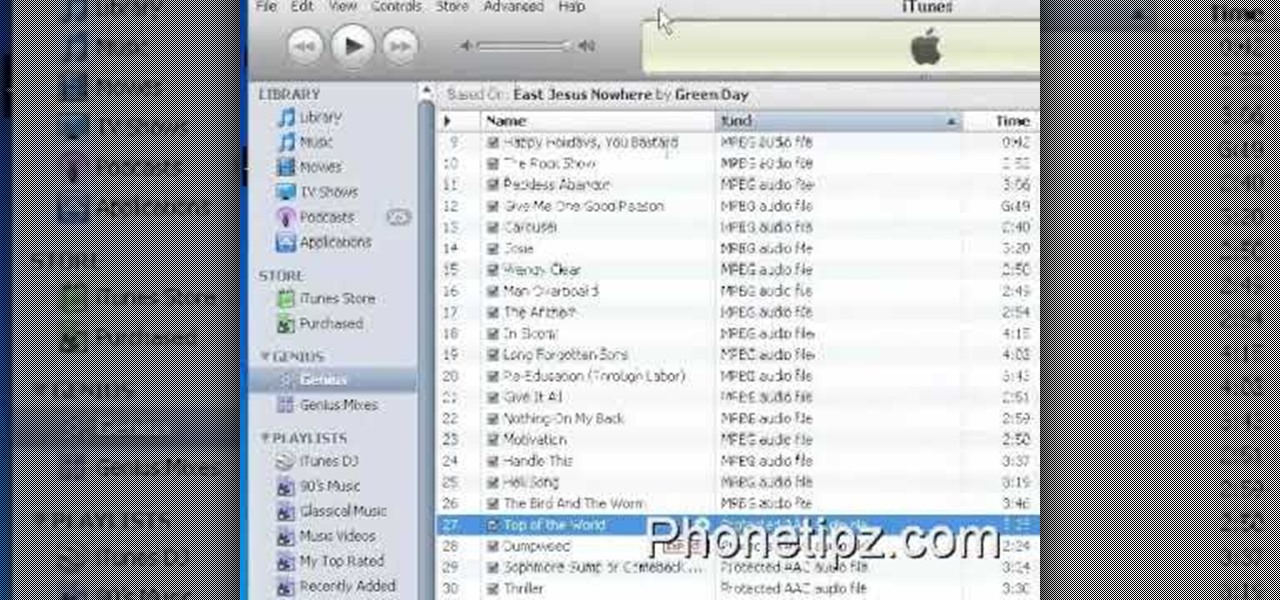
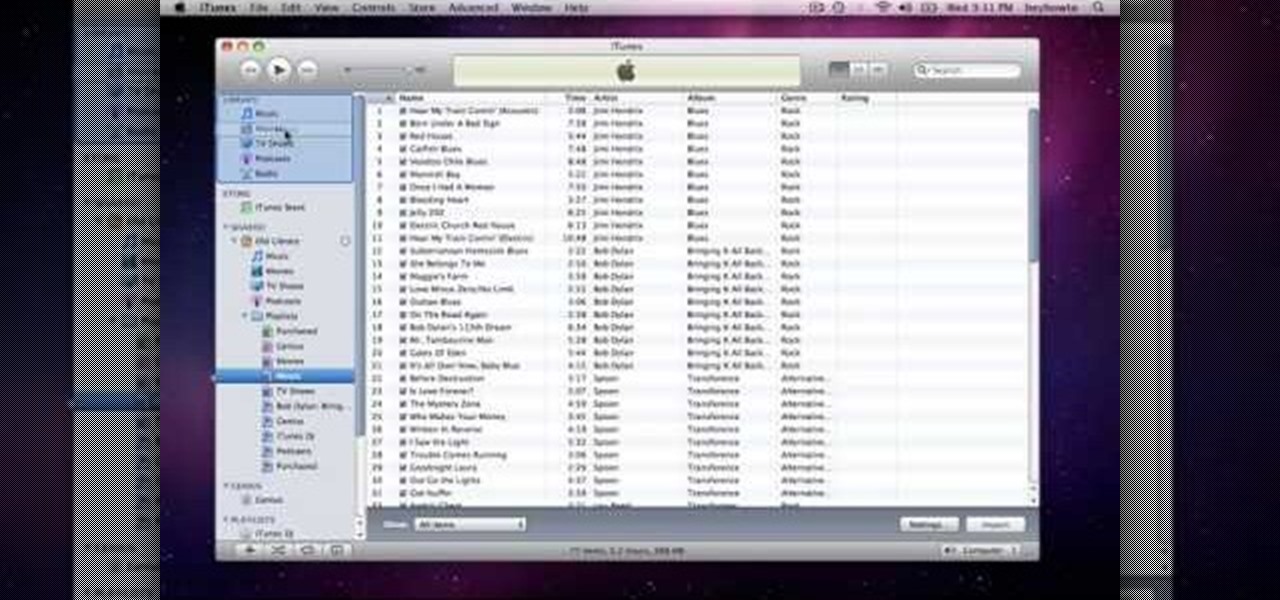
How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...

There is nothing like fresh vegetables from the garden. Dave Epstein shows us the secrets to planting peas.

In this how-to video, you will learn how to maintain your recorder instrument. First, label your recorder with a permanent marker in case you leave it somewhere. This will allow someone to identify who it belongs to. First, use the cleaning rod and put a piece of cotton cloth on it. Push it through the opening of the recorder to get any spit and dirty out of the recorder. To clean the mouth piece, use an old tooth brush and scrub it. Once in a while, it is a good idea to wash the recorder in ...

This video tutorial demonstrates tips for how to organize your home office when you are visually impaired. Here a rehabilitation specialist is helping a visually impaired person. The person who is visually impaired should know what is visually important to him/her. Mostly these people obviously need to know where every thing is because they don’t have their eyes to depend anymore. Here visually impaired person is 66 year old Deanne Jackson. She has wet macular degeneration. In order to set up...

When a girl gets her pointe shoes, it signifies a graduation - A step up in the ballet world. The only problem with picking up your first pair of pointe shoes from a store, is that they don't come with the ribbons sewn on! Learn how to sew your own ribbons on your pointe shoes. Besides your pointe shoes and ribbon, you'll need a needle, thread and scissors to complete this task. Learn how to sew ribbons onto your pointe shoes with help from this tutorial.

You may not realize it but when you buy music or movies from iTunes, you have to authorize it to be used on a computer and you can only authorize five computers. It's pretty easy to buy and replace computers and if you don't de-authorize the old ones, one day you will download a song and it will tell you that you have reached your five computer limit. At that point, what do you do if you don't have any of those computers anymore? Now Apple has put a fix in iTunes itself. Go to the iTunes stor...

This video describes what is known as the dashboard, which is located in the dock on the Mac desktop. The dashboard is a set of small programs known as widgets that let you see information at a glance. Some examples of useful widgets are a clock widget, a calendar, a calculator, a dictionary/thesaurus, and a Google search widget. You can bring them up at any time by simply clicking on the dashboard icon. If you want to add a new widget, click on the plus sign at the bottom of the window and y...

This video shows you how to fix a Windows "Blue Screen of Death". You should know what to look for when you get the BSOD. You should look for the error code first and then the stock code. You should hit the F8 button upon start up to go to the last known good configuration and it will boot your computer to the last time it booted correctly. You can also start in safe mode. You will need to do a system restore. If that doesn't work do a Google search for the file name that is causing the probl...

Grace Bonney from Design-Sponge shows how to create a corkboard and tray from sun print fabric (similar to the craft sun print paper, and available at bluesunprints.com). First iron the sun print fabric, far away from a light source. If printing leaves, first flatten them in a book. Arrange the leaves, then put the fabric in the sun for 10-30 minutes. The longer the time, the darker the print will be. Rinse the fabric in water until the water runs clear, then dry the fabric and re-iron. To ma...

Two ladies are discussing how to prepare to decoupage a wooden bangle bracelet. They are using a broad wooden bangle crafted from birch wood that can be purchased at a local craft store and printed tissue paper, for example, one in an animal print. This is part one of a three part series.

Homemade granola is a welcome addition to any recipe collection. This recipe is perfect for vegetarians and suitable for all ages. Serve granola for breakfast or with yogurt for a midday snack. Because this recipe contains wheat germ, sunflower seeds, and honey, you will find that it is a delicious alternative to commercial granola. There are no artificial ingredients or additives. Learn how to make it.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

Hanging closet hooks is one of the simplest ways to expand your storage space. You will need hooks, drill and bits, a steady hand, a stud finder (optional), a hammer (optional), & wall anchors (optional).

Installing shelves in a closet turns dead space into useful storage. You Will Need: