It doesn't matter what type of cuisine you're cooking - more likely than not, you're tossing the ingredients in a pan and smearing oil all over it for extra succulence (as well as to coat the pan). While a healthy dose of oil every day is vital for absorbing vitamins and nutrients, getting too much oil will land you in heart attack town.

Chef Chris Smith makes two different types of smoothies including a chocolate peanut butter and a berry smoothie usng berries, soy milk, tofu, banana extract and fiber fruit smoothie. Both demonstrations are low carb smoothies.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).

Let's say you're using your iPhone's Calculator app, and you're knee-deep into a complicated calculation with many steps. You type in a large number, for example, "123,466,789," but mess up. You meant to type "5" midway through but accidentally typed "6" instead. The only thing to do now is start over, no matter how far along you are, right? Wrong.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

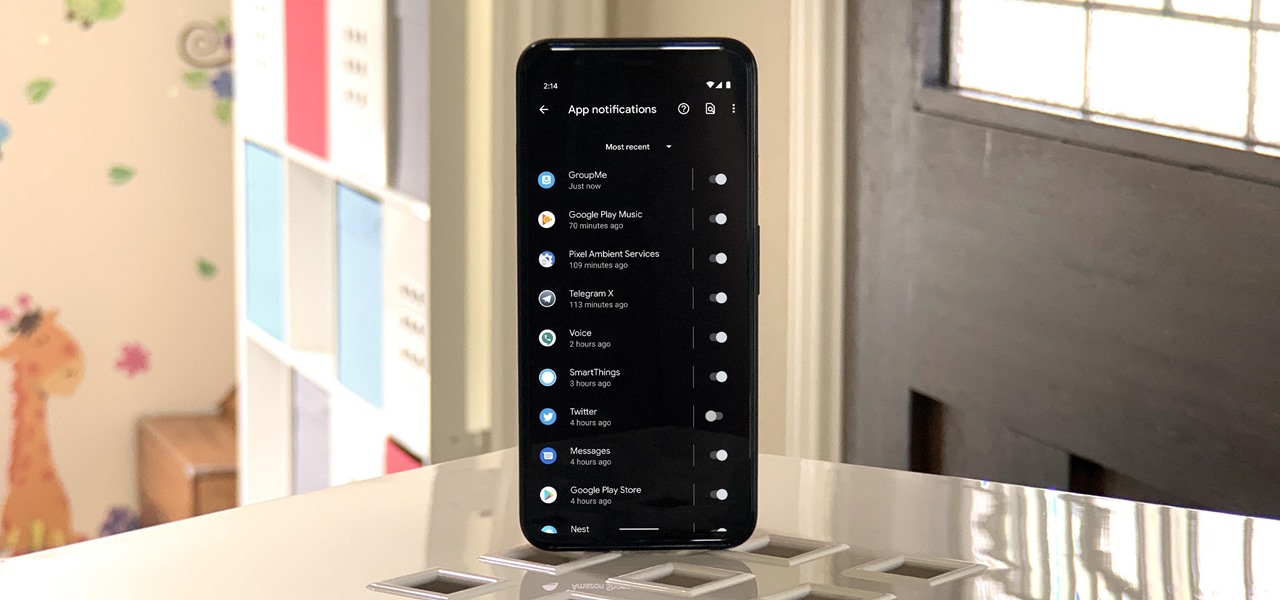
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.

From the iPhone X onward, the Side button has taken on many of the functions associated with the Home button, such as summoning Siri, pulling up the AssistiveTouch shortcut, and more. So if you've finally ditched your Home button iPhone for the latest iPhone 11, the process of shutting down and restarting is something you'll need to learn all over.

Wearables startup North has made a smart move to get its Focals smartglasses into the hands of more consumers.

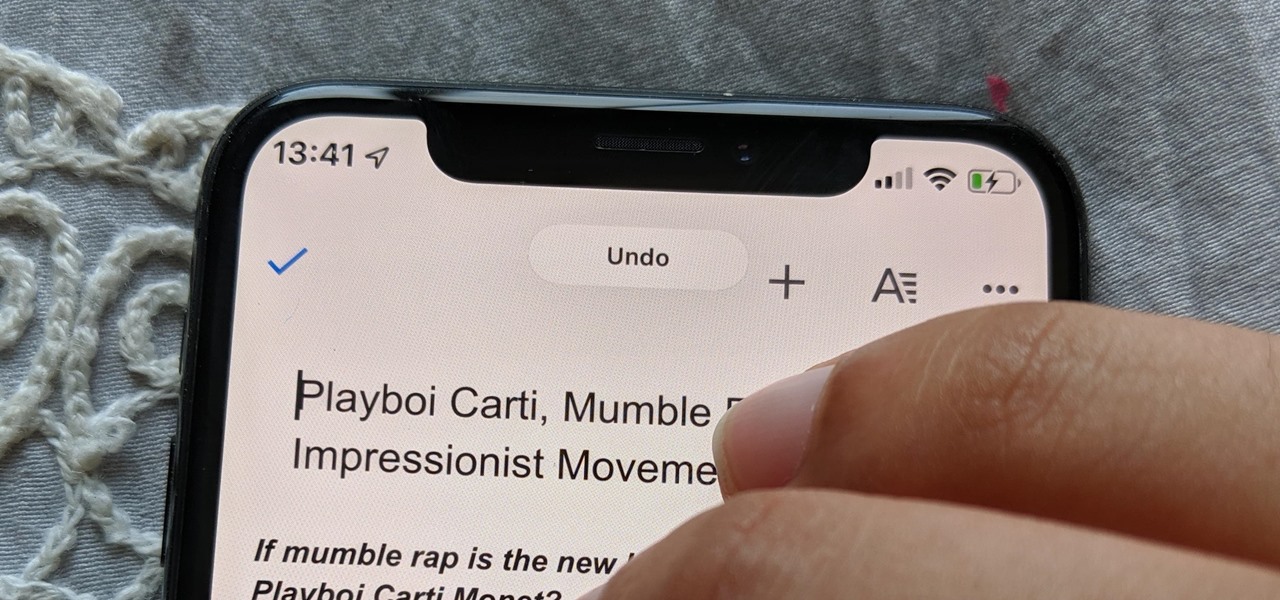
Shake to undo is now the worst way to take back what you just typed on your iPhone. Among the many changes in iOS 13, Apple has updated text gestures, including how you select a word, sentence, and paragraph, copy and paste text, and undo and redo what you type.

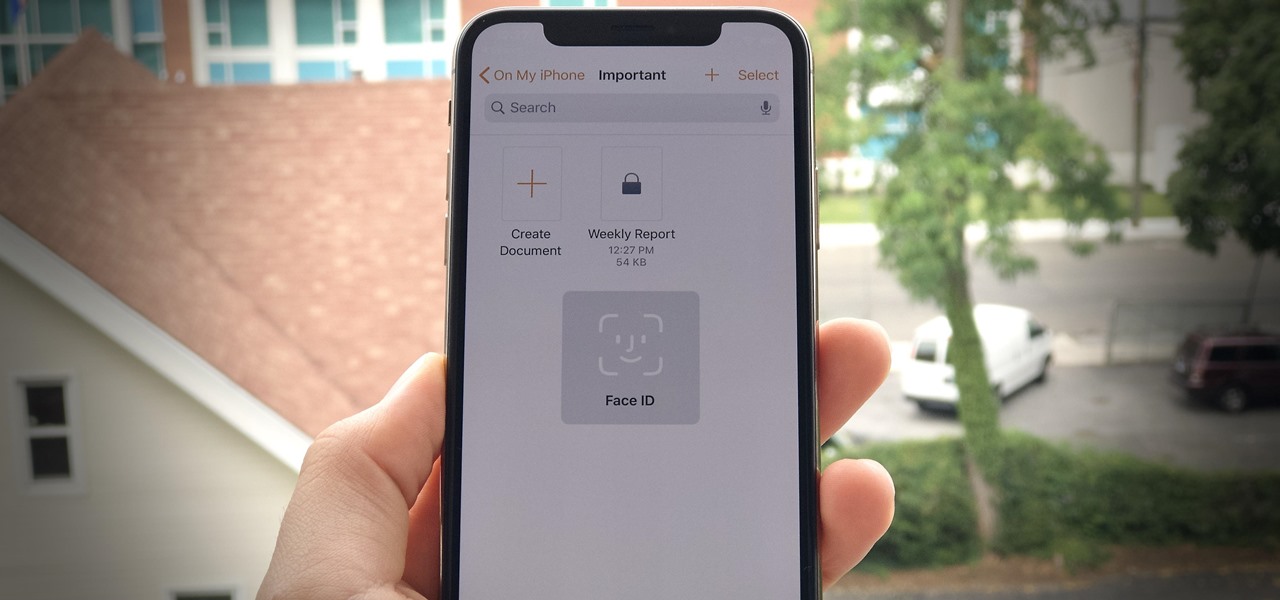
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

Over the years, TV has become more of a solo activity than ever before. It is exponentially more difficult to discuss the latest shows with friends since platforms like Netflix just release all episodes at once. Luckily, Snapchat makes it easy to keep your pals in the loop on what you're watching, so they can pick up the remote and do the same.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Android has gotten significantly better at handling intrusive ads over the years. Things have gotten to the point to where these nuisances are largely a non-issue for most of us. However, there are still a few ad-laden apps that fall through the cracks — particularly the kind that bombard your lock screen with ads.

Android lets you sync your contacts across devices. The OS will use not only contacts saved on your phone, but also your Gmail. This choice can lead to a contacts list populated with entries that don't have a phone number, which can quickly add up. To mitigate this problem, there are a few methods.

Despite numerous reports announcing its stateside arrival, "Final Fantasy Awakening" has yet to show up in the iOS App Store, much to the chagrin of millions of fans in the U.S. Unfortunately, the game seems to be stuck in soft-launch limbo, with no word as to when it'll land stateside. With a little hack, however, you can give this immersive game a try right now.

Whether due to spotty cellular reception or just data that you want to save, popular navigation apps like Google Maps and Waze offer an offline feature that lets you navigate from one location to another in the absence of internet service. Apple Maps also lets you use its service offline on your iPhone, though the feature is not as straightforward as it is on its competitors.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

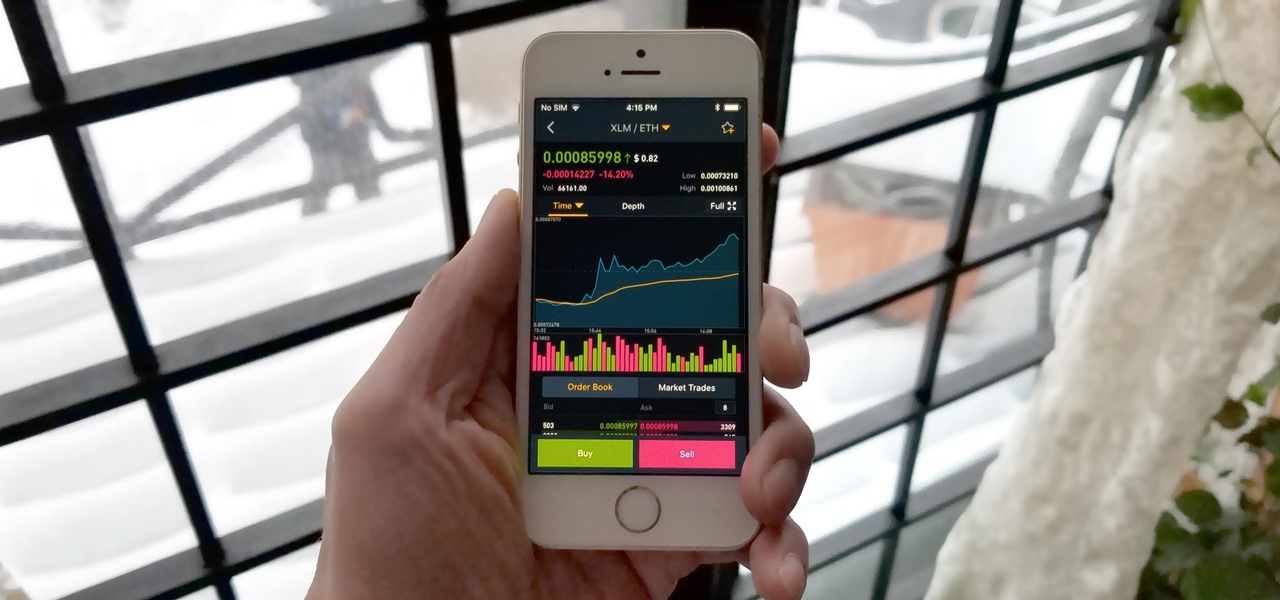
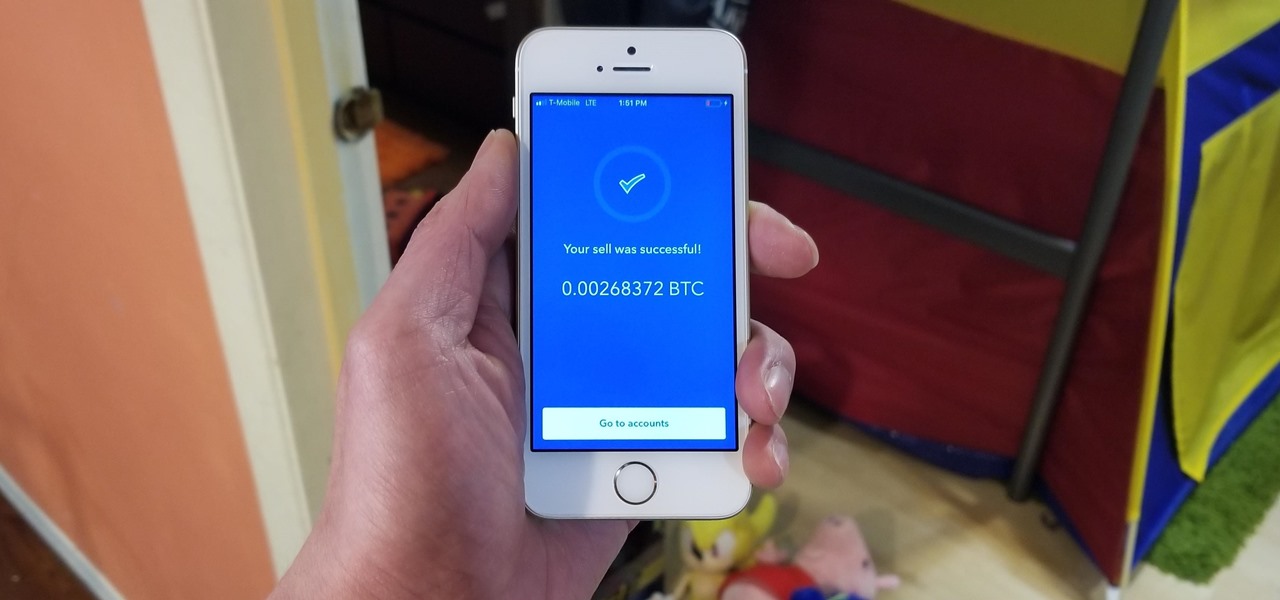
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.

Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

If you're trying to get somewhere fast, taking a toll road or two can definitely help you do that, but at a cost. When you're not in any rush, that would-be toll money will work much better in your gas tank, especially if it's only minutes that are being shaved from your trip. With this in mind, Apple Maps has a simple way of avoiding tolls to save you money while navigating on your iPhone.

Just over a week after debuting, Animal Crossing: Pocket Camp received its first-ever event geared toward the winter holiday season. With the ability to craft Christmas-themed goodies and own a full Santa suit, it's the perfect time to jump into Nintendo's latest hot mobile game.

Now that it's been officially released for Android, Monument Valley 2 shot to the top of our best paid puzzle games list, and rightly so. This was no easy feat, as the games we covered ran the gamut of puzzles and all had stellar reviews. But there's just something about Monument Valley 2 that made it stand out from the rest.

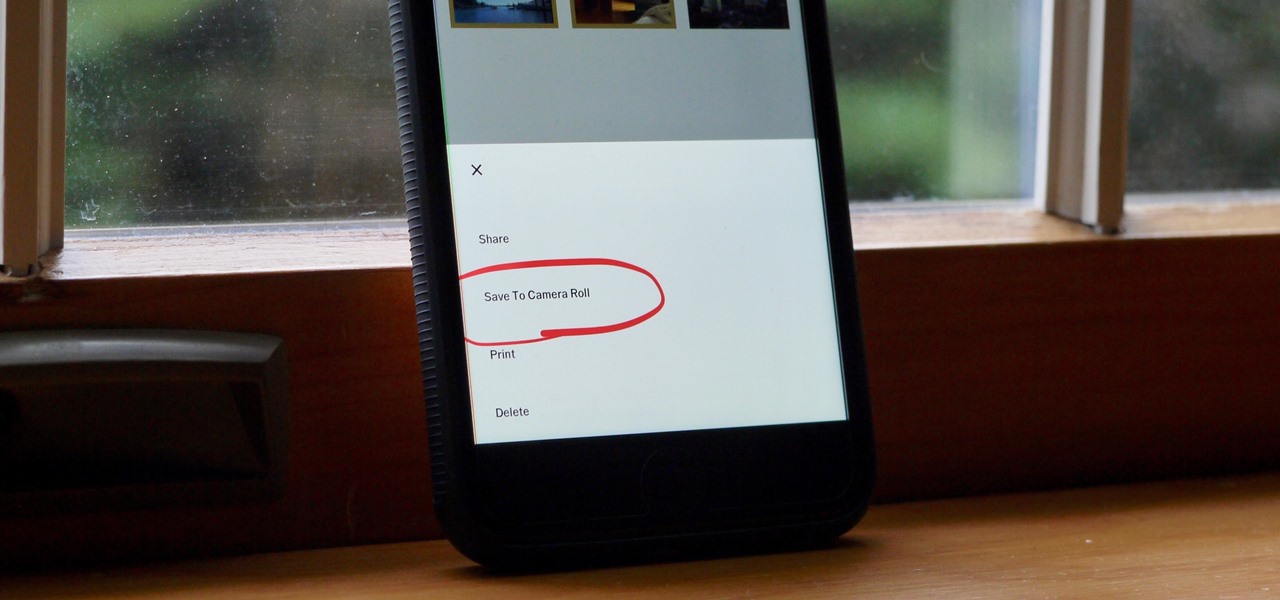
Whether you use VSCO to take all of your photos or you use it primarily to edit photos you take with others apps on your iOS or Android phone, you're at some point going to want your VSCO pics to end up in your Camera Roll or Gallery. VSCO doesn't add them there by default, but there's a couple of ways to get them there.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.