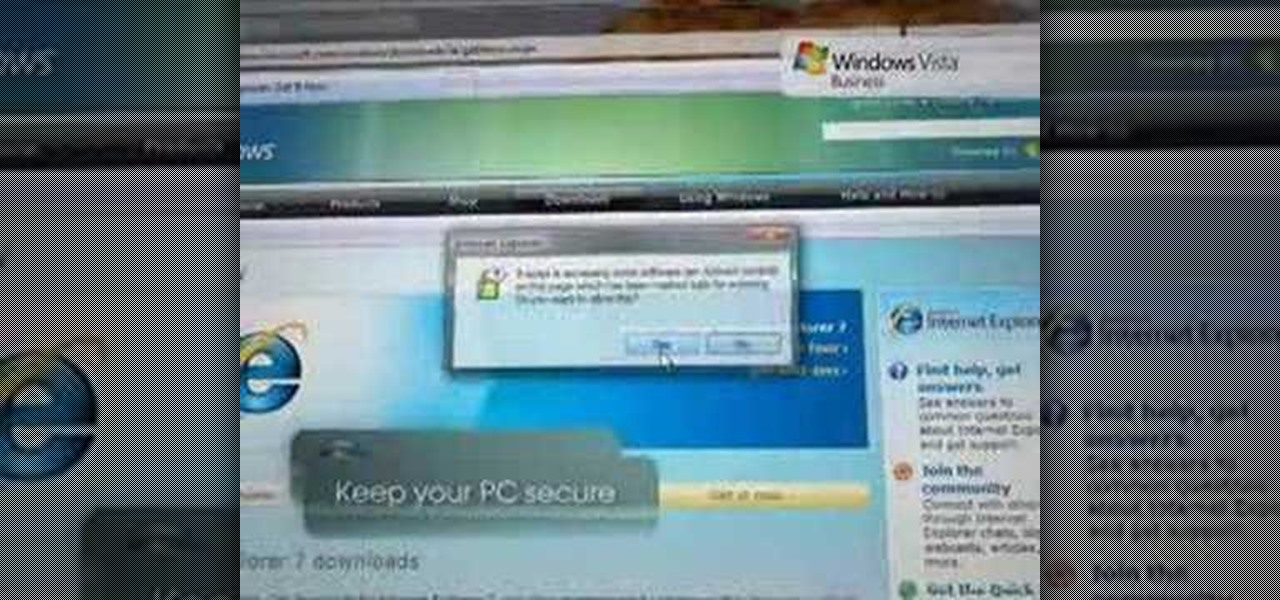
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...
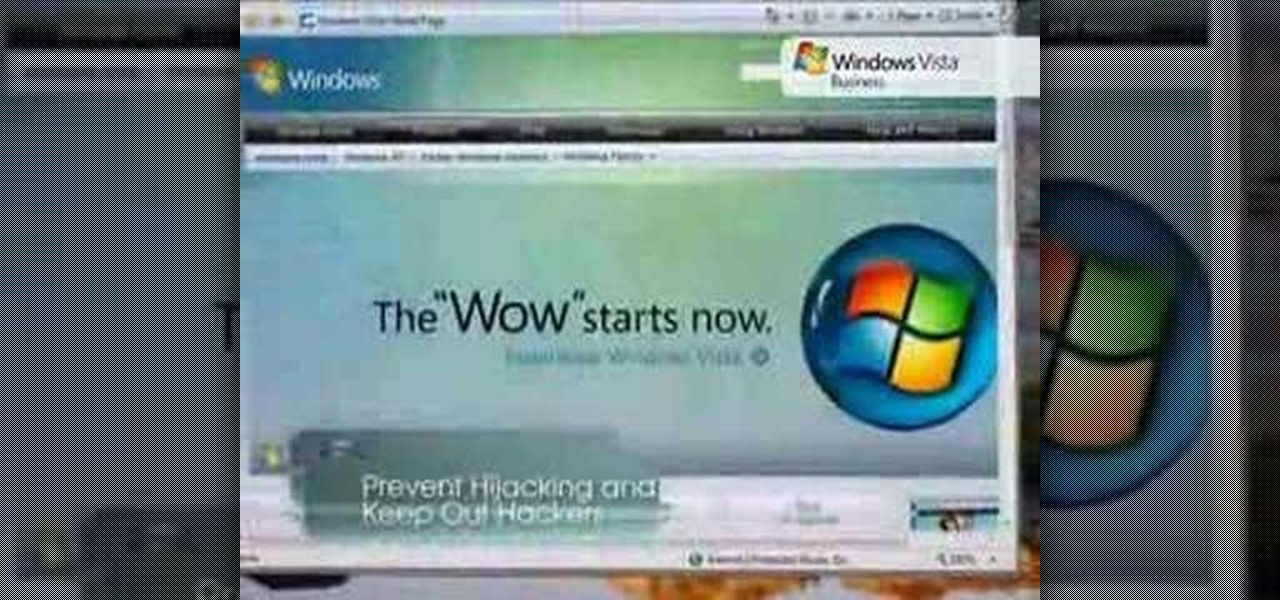
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...
In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

A hooking knee strike is legal in Thai boxing, not kickboxing. Learn the skills of Muay Thai in this tutorial on competitive kickboxing moves. When performing the

All day we use our calf muscles when we walk, run, and climb stairs. As a result calf muscles are popular massage targets. Learn the art of giving massage in this diet and health how-to video.

Pilates is great for strengthening and toning the body. This piltes how-to video illustrates the Single Leg Stretch exercise. It targets the transversus abdominus, rectus abdominus, obliques, scapular stabilizers and hip stabilizers.

This Pilates Side Bend exercise is used to enhance lateral mobility of the spine. It primarily targets the transversus abdominis, obliques and scapular stabilizers. Attention should be paid to the abdominal contraction to maintain rib connection and prevent the hips and shoulders from rotating. The cervical spine should stay aligned with the thoracic spine.

This pilates how-to video illustrates the Pilates Spine Twist exercise. This exercise is great for spinal rotation.

This pilates how-to video illustrates the Obliques exercise. This exercise is great for rotation, flexion and strengthening pelvic stability.

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Firebug is an essential Firefox extension for web designers and developers. You are able to quickly target any element on a page to see the markup, the CSS, the layout, and the DOM in an instant. Not only can you see all of this juicy information, you can edit and see the results directly in the browser window. This makes Firebug the go-to tool for debugging CSS trouble. Also indispensable for Javascript programmers. So all you Internet website designers out there, pay close attention to this...

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

It looks like Jaunt's pivot from VR to volumetric captures services for augmented reality experiences has paid off.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

There's no shortage of augmented reality platforms for remote video assistance, but startup Streem is looking to give its offering a leg up with an infusion of new technology.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Smartglasses are the future of augmented reality, and Samsung is betting on waveguide maker DigiLens to emerge as a leader in the growing AR wearable industry.

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

News junkies who own the Magic Leap One received some good news on Thursday, as CNN has published an app for the headset to display the network's news coverage in augmented reality.

In the aftermath of the launch of the Magic Leap One, Magic Leap has ejected two more executives from their leadership roles.

In recent years, Apple has assembled its augmented reality team and supply chain through a series of acquisitions, high-profile hires, and strategic investments, but at least one potentially major deal was recently ditched.

While these days it is better known for the cross-platform gaming sensation Fortnite, Epic Games also makes Unreal Engine, one of the top development environments for 3D content and, in turn, augmented reality and virtual reality experiences.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

Smartglasses maker ThirdEye has announced that its X1 model wearable will be updated by the slimmer, as yet unreleased X2 model. Both devices will be promoted and sold through its partner, brick and mortar technology retailer b8ta.

To punch up the launch of its new podcast, USA Today has created an augmented reality experience to introduce listeners to the story of corruption in Chicago.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

If touring the scenic vistas behind the Lord of the Rings film franchise doesn't persuade tourists to visit New Zealand, perhaps immersive content viewed through Magic Leap One will do the trick.

If $200 was too much for you to get in on some Star Wars augmented reality action, Best Buy is now selling refurbished Star Wars Jedi Challenges sets for $79.99 and new ones for $99.99.

This week, two companies preparing the most anticipated augmented reality devices for consumers were the subject of reports regarding strategic moves to put them in better positions to move those products forward.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

In the wake of reports of slow iPhone X sales and a possible early end to its shelf life, Apple CEO Tim Cook is on a public goodwill tour of sorts, espousing the virtues of Apple AR.

The Force was awakened in many a household on Christmas morning this year, as evidenced by numerous recipients of newly unwrapped Star Wars: Jedi Challenges systems sharing their first lightsaber battles in augmented reality on social media.