A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.
Google's G Suite collection of premium cloud services and apps have become popular with business customers, with more than six million subscribers now.

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Sure, it's the giving season, but sometimes you've just got to treat yourself to some cosmetics. If you're shopping at Walmart, L'Oreal just made that a shade easier when shopping for Garnier hair color products with an assist from Google Lens and the Modiface AR platform.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

Snapchat parent company Snap credits its popular augmented reality experiences and its flourishing Lens Studio creator community to its user growth throughout the year.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

Halloween is barely in the rearview mirror, but Coca-Cola is ready to bypass Thanksgiving altogether to accelerate the arrival of Christmas, and the brand has enlisted augmented reality as an accomplice.

After talking up the Magicverse for the past year and adding new capabilities to Lumin OS to accommodate it, Magic Leap appears to be inching ever closer to actually launching its cross-platform flavor of the AR cloud while introducing a new tool for its development community.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

Although styluses and smartphones have existed together for years, the iPhone has always ignored the pairing. After all, "Who wants a stylus?" But ever since the Apple Pencil made its debut on iPad, the rumor mill has churned out the idea that an iPhone could one day see stylus support. That day will probably come with the release of iPhone 11, and there's a good indicator to make its case.

As Microsoft works toward fulfilling its $480 million contract to supply modified HoloLens 2 headsets to the US Army, Airbus is preparing to supply advanced augmented reality apps for the device.

With Snapchat making the leap into the smartglasses realm, Facebook had to find a way to try and steal its competitor's augmented reality thunder.

Already among the first game makers to add augmented reality content to an existing game upon the launch of ARKit, Zynga is breaking new ground with mobile AR once again.

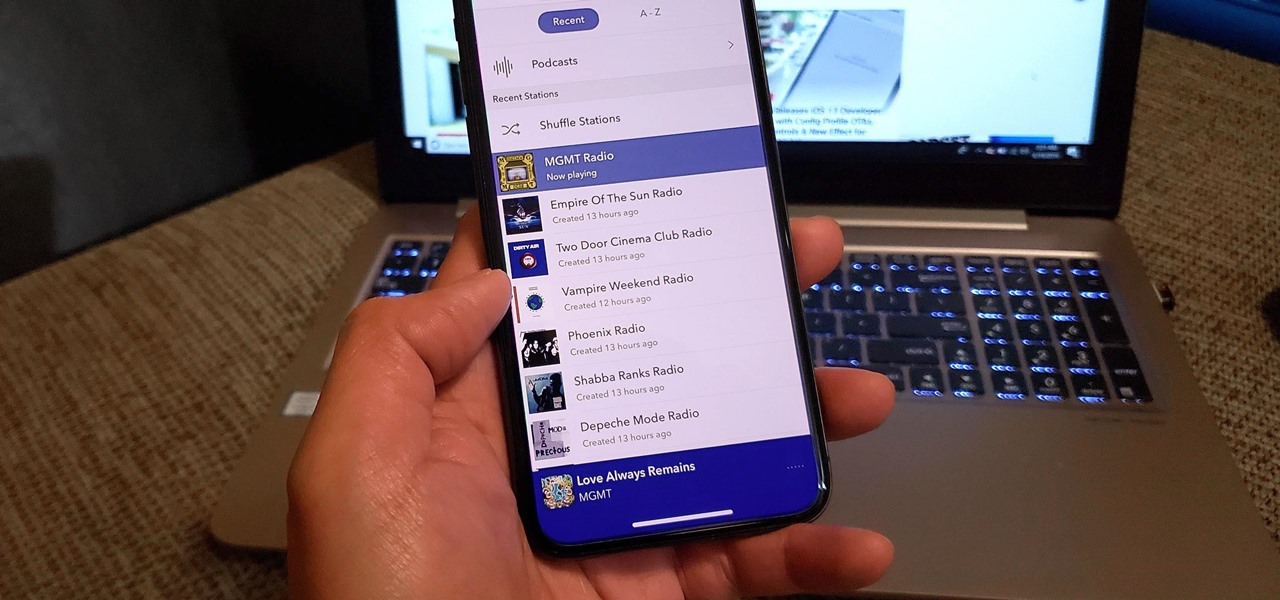
With such a vast selection of music genres available, it's easy to build up a massive list of stations in Pandora that can make your go-to playlists harder to find. Fortunately, the app lets you easily remove unwanted stations to streamline your experience and listen to your favorite tunes in the fewest taps possible.

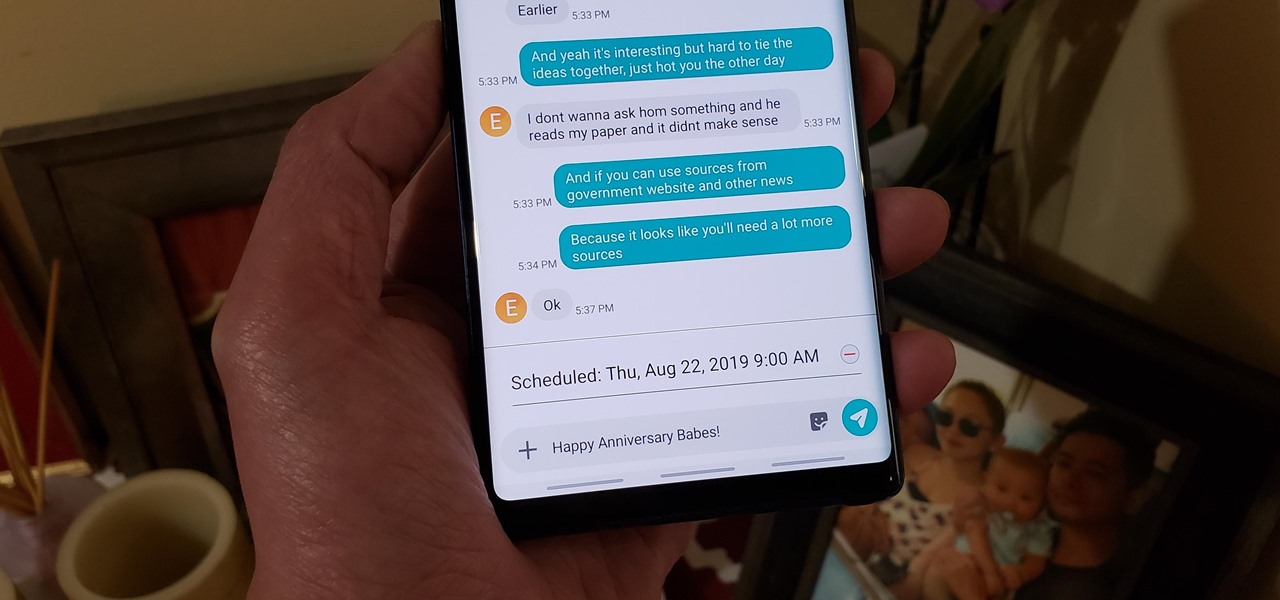
Ideas can hit you out nowhere, but texting loved ones in the wee hours of the morning or during work hours isn't always ideal, especially if they've muted their notifications. So you'll want to send a message at a better time to ensure it gets the attention it deserves. Samsung Messages lets you do just that by scheduling messages to send at a later date.

Lions and tigers and bears are just a few of the animals that Google users can now bring into their physical environments.

As one of the leading 3D engines for augmented reality development, a new release of Unity is a significant event that carries the potential to facilitate huge leaps forward in AR content creation.

While The New York Times' augmented reality section has largely been dormant in 2019 (so far), USA Today has continued to crank out AR news stories.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

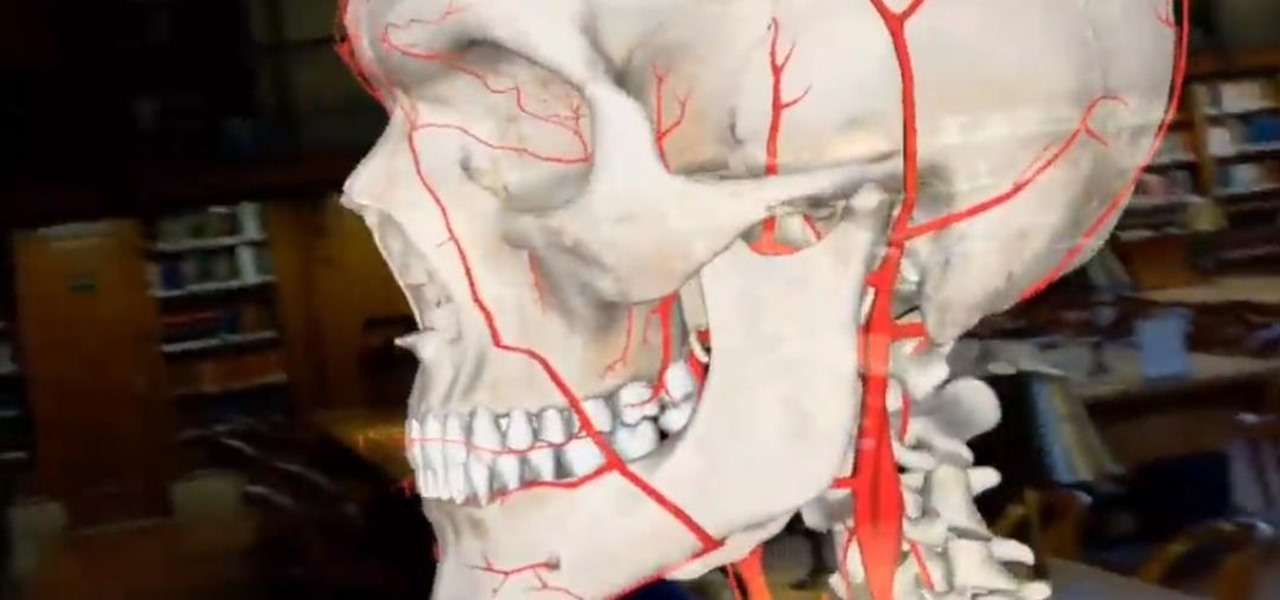
Not content to merely assist surgeons via the HoloLens, Medivis has expanded its augmented reality suite to Magic Leap One with an app for medical students.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

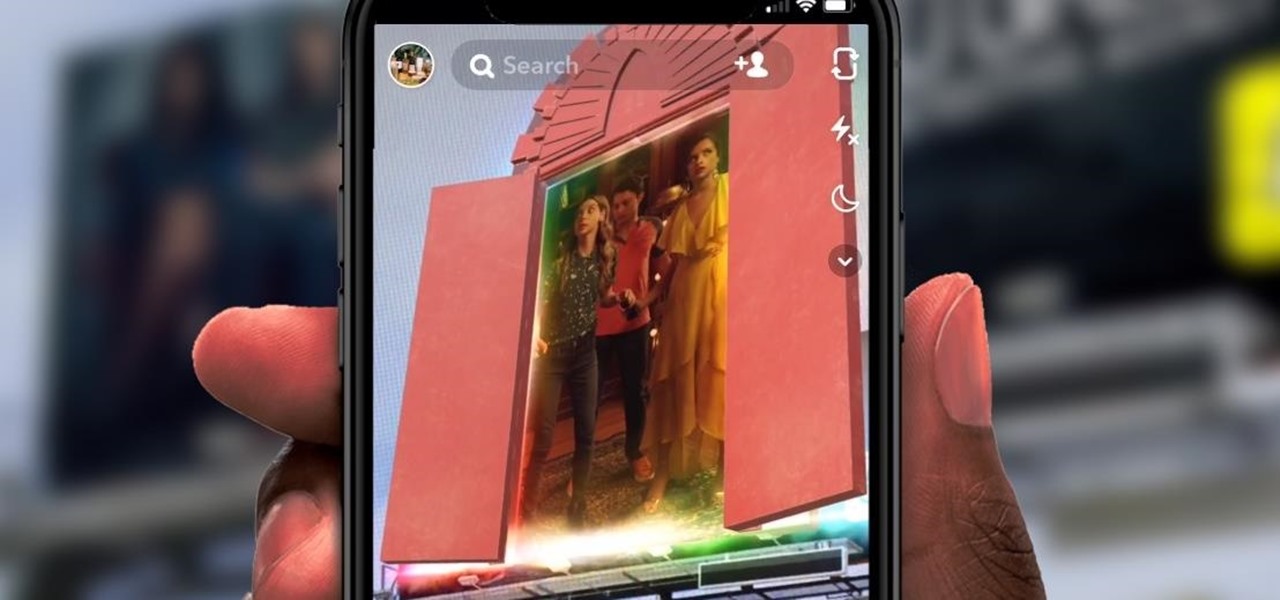
If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

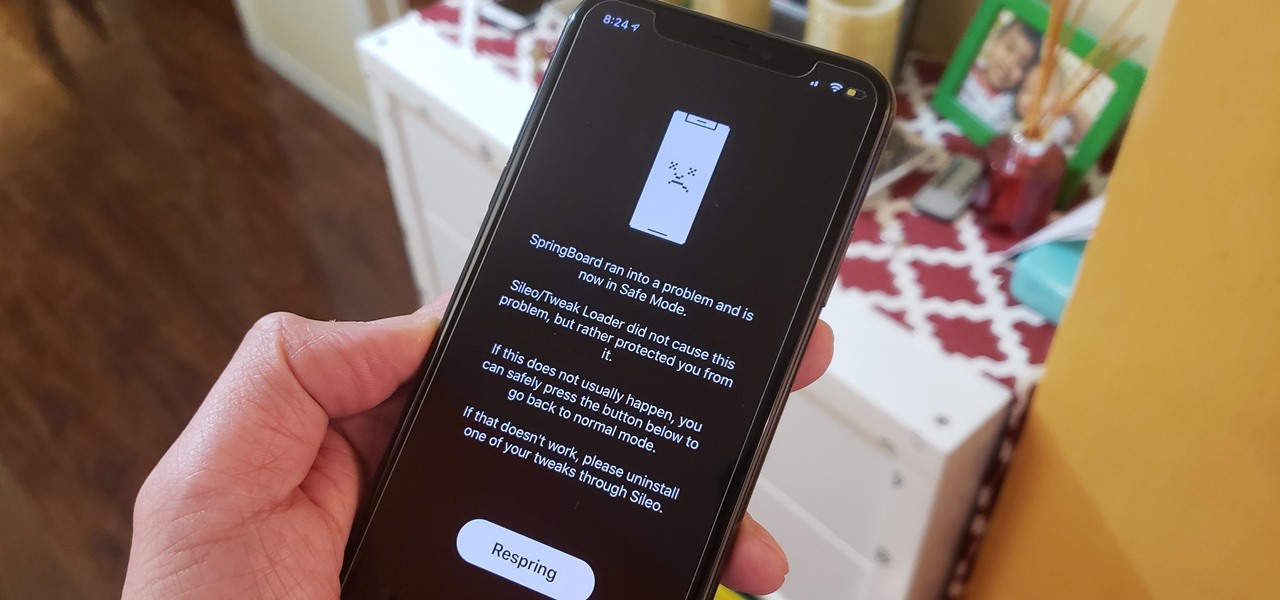
If you're familiar with jailbreaking, you're well aware of the fragmented nature of downloading tweaks. Unlike the iOS App Store, which contains about two million apps of varying categories, installing jailbroken packages often requires you to first install a separate repo into either Cydia or its replacement Sileo, as many of these tweaks aren't available outright.

Removing unwanted apps from your iPhone is a straightforward affair — long-press an app's icon, then hit the delete button once it appears. Unfortunately, the same can't be said when it comes to uninstalling tweaks from a jailbroken iPhone.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.

Any real Star Wars fan knows that fear is a path to the dark side, as it leads to anger, and then suffering. For players of Star Wars Jedi Challenges, though, access to the antagonistic side of the Force is now available through their mobile apps.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

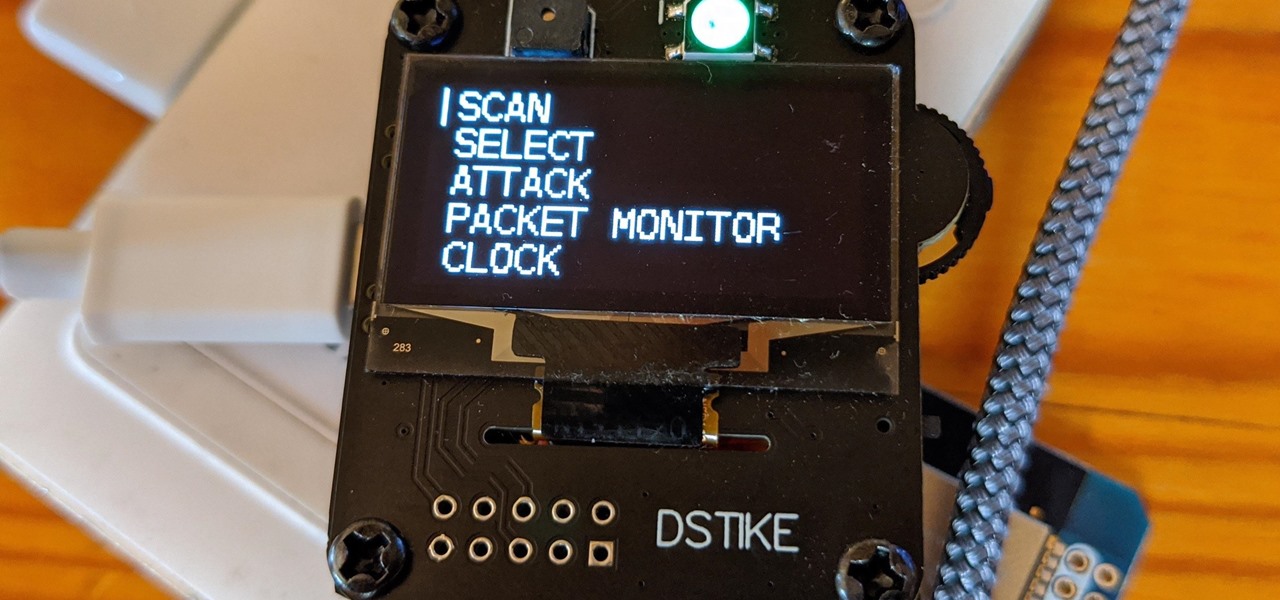
The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

On Thursday, Snap released three new templates for its Lens Studio that will give creators access to augmented reality capabilities previously only available to Snap's own design team.

Despite the relatively small size of Magic Leap's first annual L.E.A.P. conference, there was a lot to see and experience. Apparently missed by many was one of the best experiences I had at the event: Wingnut AR's unreleased Pest Control game.

The latest sponsored augmented reality experience on Snapchat from a movie studio might be its scariest — and perhaps most popular — yet.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

It's a sad day for one of the most beloved series of Android phones. For the first time since 2009, there's a new version of Android, but it's not being made available to Google's own Nexus devices.

The latest preview build for Microsoft HoloLens is packed with new sharing features, including support for the Miracast protocol.