Augmented reality (AR) generally exists through the lens of our smartphones as information layered on top of what the camera sees, but it doesn't have to. Developer Jon Cheng worked with an indoor climbing facility in Somerville, Massachussetts, called Brooklyn Boulders, to turn rock climbing into a real-world video game where participants compete in a time trial to hit virtual markers on the wall.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

If you think phablets are too big to be smartphones, and not big enough to be tablets, then you're going to love what's coming next.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

While I consider myself to be a pretty organized guy, there are often times where I just can't find a file I put on my phone. Most of the time, when I download a file it goes automatically into my Download folder, but when I use a third-party to download other files, like torrents, they could end up in a number of places. Filtering abilities on file explorers often fall short, so it was time to find an app that would automatically sort files in real time.

Don't throw away your dead light bulbs, they may come in handy one day. This video will show you how to start a fire using a dead lightbulb. And no electricity. The tricky part is emptying out the insides, but this can be done with sticks and stones, assuming you're in a survival situation and just happen to have a light bulb with you for whatever reason.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

The runaway chainsaw family of glitches for Gears of War 2 enable the player to chainsaw a target to death instantly, without having to wait through the tedious process of watching their victim being sawed in half vertically. This video will teach you how to use the glitch in multiplayer, whether hosting or not. Like most of the game's glitches, this isn't all that useful in the game, but if you've finished all the other content, it's time to turn to the glitches!

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Aerobics are targeted by total physical fitness: strength, flexibility and cardiovascular fitness. Aerobics can be taken in classes and are usually done with music. To practice aerobics you should follow an instructor, stay in motion, use arms to lower or raise intensity, and strengthen heart rate. With this how to video soon you will be able to practice aerobics.

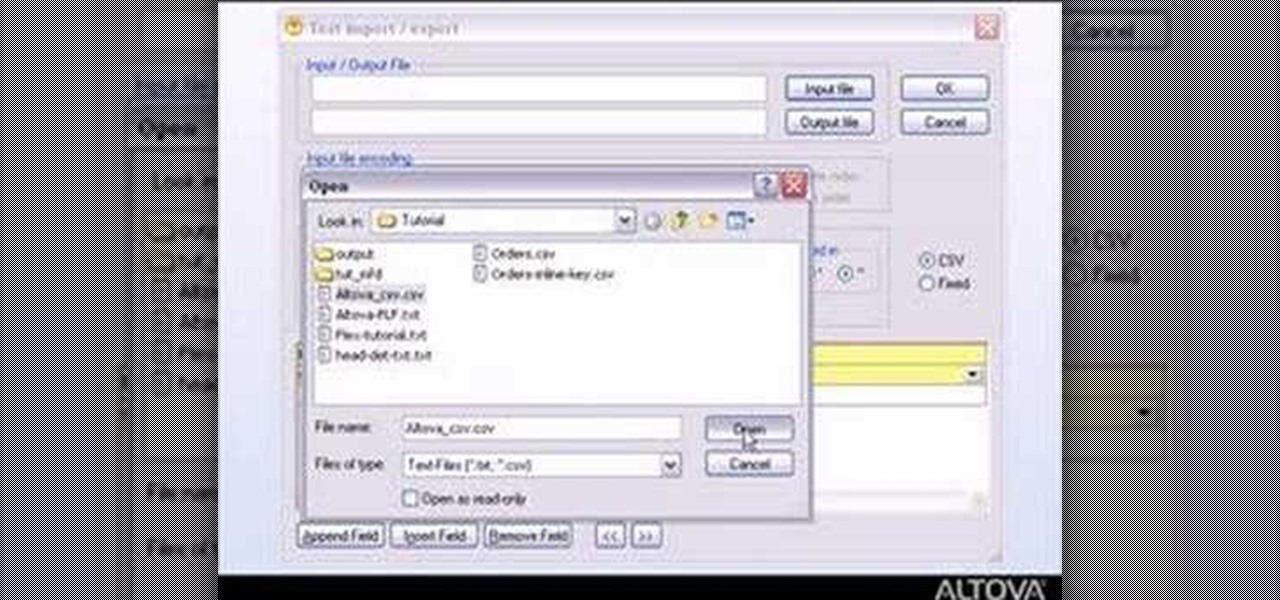
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

This three part how to video shows you a butt workout that will help you tone and tighten your glutes with three of the best butt sculpting exercises to target your butt, hips and thighs. Do these exercises and you will be able to get in great shape.

This tutorial demonstrates a weight training workout for your triceps. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your triceps and the rest of your arms.

This tutorial demonstrates a weight training workout that develops your deltoids. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your shoulders.

This tutorial demonstrates a weight training workout for the chest. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your pecs.

This tutorial demonstrates a weight training workout for your biceps. The how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your biceps.

Learn to play the board game "Plunder" with tips from this how-to video. To play Plunder, you need six players at the most. It is targeted mostly toward adults but even kids as young as eight like to plunder.

This is my updated video of eyeshadows brushes that I use when I do my eye makeup. I tried to be as detailed as possible.

The oblique muscles targeted by this bend-and-twist exercise will help you pick up everything from envious stares to spare change on the sidewalk.

In this tutorial, Bert will show you quickly how to use a bunch of different layers to create a ray gun shooting and exploding it's target. It will help if you already have some Photoshop knowledge for this one.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Most ab workouts target your upper abdominals only. Sit ups and crunches, for instance, only work on that upper part of your abs without even touching the lower portion, where most of us have muffin tops and really need the work.

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Have you ever wondered what it would taste and feel like to take a bit fat bite out of a supersized Twix bar? No, we're not talking about the King Size Twix bars you can get at Target. We're talking a goddamn cake-sized Twix bar.

The arms are the part of the body most used by Westerners in fighting. As a result, targeting and disabling an opponents arms is a great way to end a fight quickly without the risk involved in hitting an opponent's head. This three-part video details pressure points all over the arms and various ways of striking them in order to hurt and disable your opponent, ending your engagement with limited damage to both yourself and them.

A poker face is sharp, beautiful, and intimidating, giving your target a peak at the cow without giving away the milk. Bring out your inner card-dealing bovine by watching this professional makeup tutorial by makeup artist Reiva Cruze.