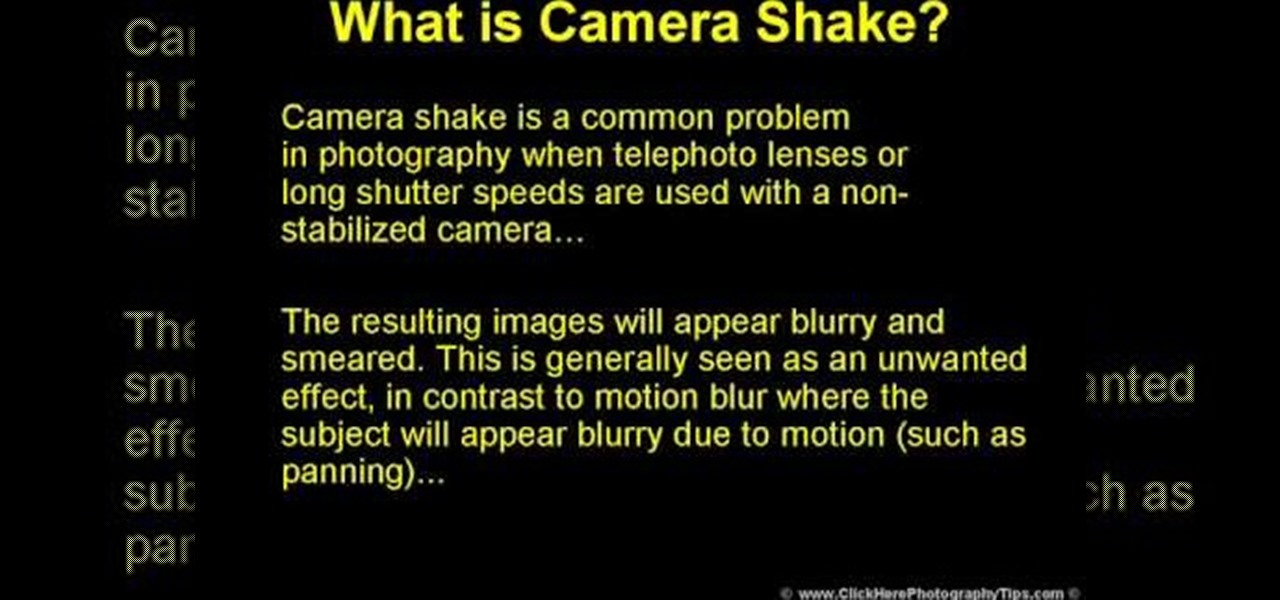
Camera shake is often an unwanted effect in photography, when a telephoto lens or long shutter speed has been used for a camera that hasn't been stabilized. The images subject to camera shake appear blurry and smeared, which is often considered an error - though some photographers find artistic value in camera shake and purposefully try to cause the effect in their art.

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.
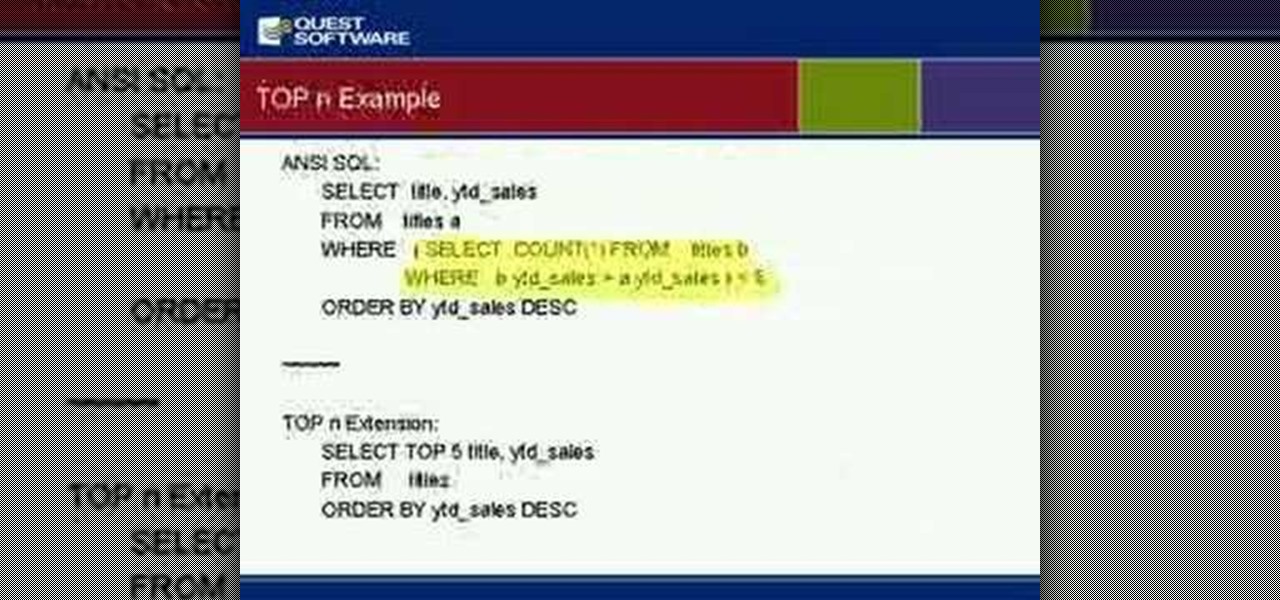
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

The hype around augmented reality has risen to a fever pitch over the past two years, and if this week's selection of business news stories are any indication, the din is about to get down right deafening.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

Just when you thought Google Glass was dead, it turns out there may be a second life for the often ridiculed device that won't relegate it to the staid confines of factories and repair jobs.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

As drug-resistant bacteria become more commonplace, researchers are looking for new antibacterial strategies to disrupt disease-causing microbes. Some scientists are working to create new drugs, while others are trying out drug combinations. Another group, however, are ditching pharmaceuticals altogether and experimenting with non-drug alternatives.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.

Looking past the obvious visual similarities between the iPhone 7 and Google's new Pixel phones, there are several indications that the search giant had Apple in its sights as they released their latest flagships. For once, this isn't an Android phone we're talking about, it's a Google phone—and it showcases Google's latest strategy.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

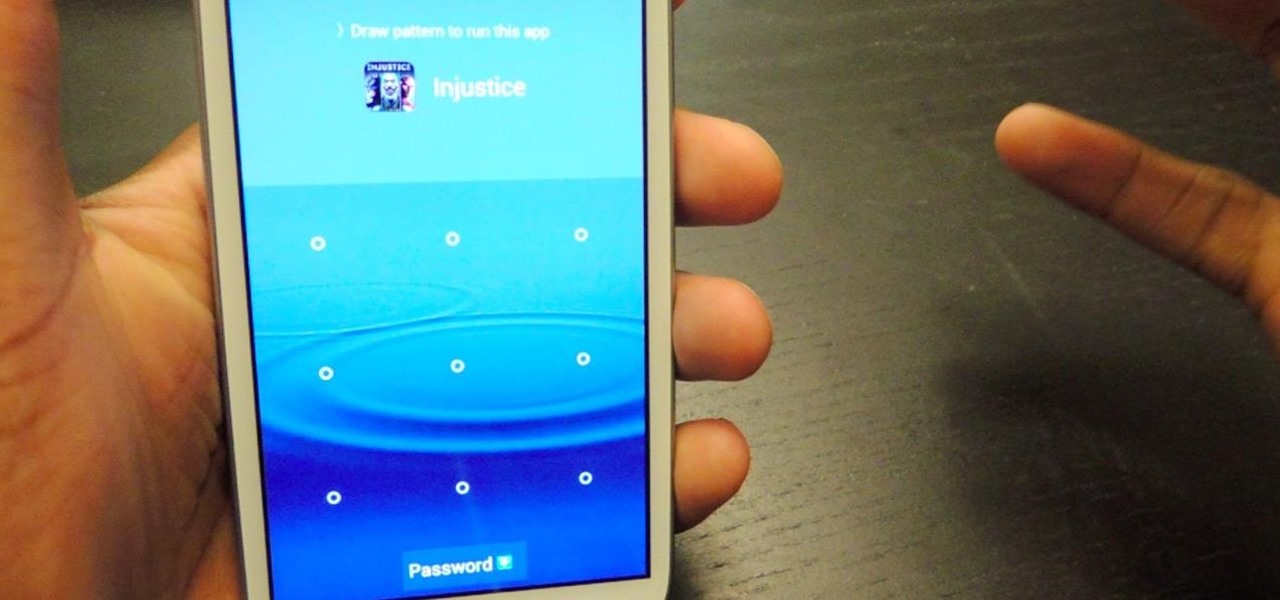
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.

2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at.

Apple's iTunes Match service is a great feature for people who have large libraries or want to sync their music across a lot of different devices. It lets you store any song in your library that exists in the iTunes Store on the cloud, even songs you imported from CDs, and even improves the quality of some of them. But, like any new service, it's not without its problems, and the fact that it costs $25 a year makes those problems seem even worse. Among the issues that users reported, unmatche...

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

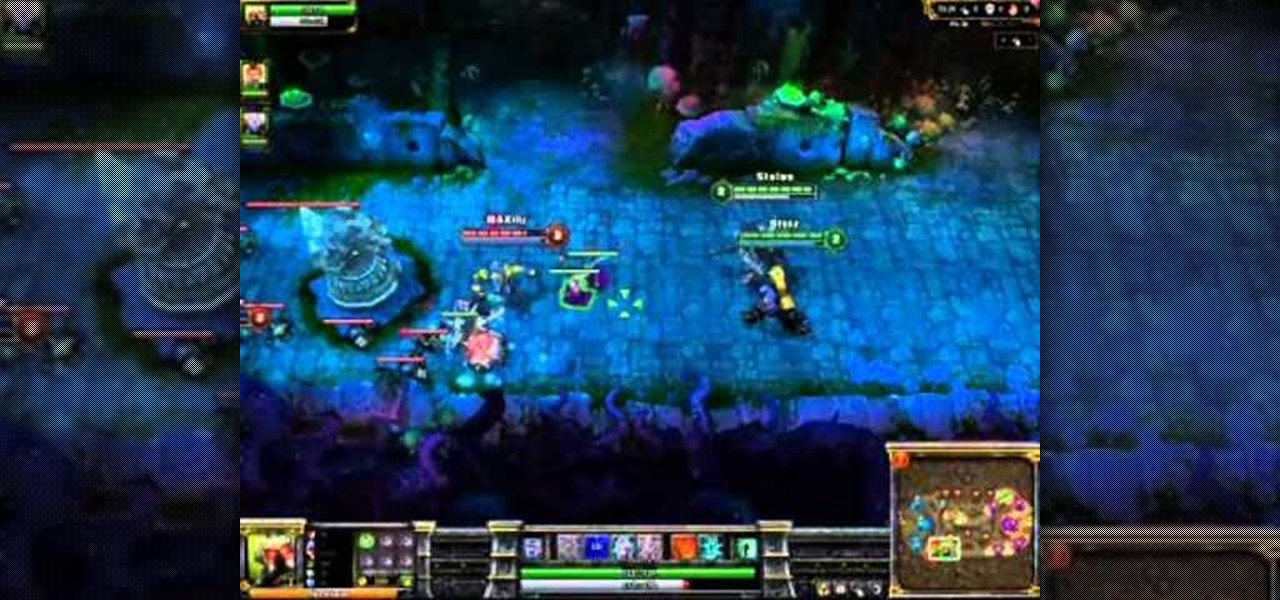
Katarina is one of the champions you can use in League of Legends, being able to both deal out damage and handle taking it herself. Here's a quick overview of what she can do, and the best way to incorporate this champion into a team game on the Fields of Justice.

Malzahar's strength is being able to damage over time. With his silence ability, he is also good at harassing the other team. Here's a video which explains what Malzahar can do as a champion, and then a demonstration of him in action on the Fields of Justice.

Laning is one of the more important phases during a battle on the Fields of Justice. This tutorial shows you the best way to use Nasus when you're trying to take or hold your lane. Make sure you choose the right abilities and items to make Nasus more than able to hold his own during your next game.

It can sometimes be difficult to win a solo queue game in League of Legends when paired with players you don't know. Here are a few tips and hints when you pick your champion in a way to compliment what your teammates are playing.

Becoming a chess master is very hard to do, and one of the most important things you need to learn is chess notation. Chess notation will help you study great chess games and learn classic moves and strategies. Check out this video and start studying, and who knows? You may be the next Bobby Fischer.

The three man weave is a staple basketball strategy that every player must master. Learn basketball skills and strategies in this video basketball lesson.

Learn how to play intermediate to advanced pinochle with expert tips and advice on shuffling, rules, game play, and strategy in this free video series about card games.

Learn how to play novice to intermediate double-deck pinochle with expert tips and advice on shuffling, rules, game play and strategy in this free video series on playing card games.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

While "Baby Yoda" from The Mandalorian threatens to overshadow it, Star Wars: The Rise of Skywalker arrives in theaters next week, which means it's time for Disney and Lucasfilm to ramp up its promotional strategy.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

As a frequent collaborator with Qualcomm, it would be kind of weird if Nreal didn't have something new to unveil at this week's Snapdragon Summit.