Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.
Well, this is my first article so if it sucks tell me...lol!! Story Time

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Resources for finding new music are at our disposal in all corners of the internet; the only problem is deciding which one is the best for you. Spotify, Pandora, and Rdio all have options to discover new music on your smartphone, but they tend to expose mostly established artists, making the process of finding lesser-known but good music a game of trial and error.

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

Step 1: Introduction: Hello! Hackers

Injustice: Gods Among Us is one of the most popular games to come out over the last couple of years. It was a hit on video game consoles, and it's got a solid 4.5 rating on both Google Play and the iOS App Store, with almost 2 million people rating the game combined.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Revised Version, Gallery pictures of the Ambassabank have been removed since XCL 2.0 has been released.

By eliminating the need for hard keys on phones, manufacturers are able to use that extra space for a larger display, which is clearly evident on the bezel-minimal LG G3. In order to replace the physical home, back, and app switcher keys, we now have stylish soft keys.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Real suffering is sitting through a thirty-second ad to watch a fifteen-second video, or watching your favorite music video in three-second fragments. Real suffering is this: “An error occurred, please try again later.” If you’re a modern human and multitask with multiple tabs while you're on YouTube, you don’t have to sacrifice your bandwidth and sanity. There's a simple way to watch YouTube ad-free and lag-free.

I still have a nexus one. This little phone 196 Mb of storage space (and most of that is taken by the system). But I have somehow managed to live off it for 2 years. This is for anyone with a small amount of memory. We will be using Link2SD. MUST HAVE CWR AND A ROOTED PHONE.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

Yes, boys. It’s true. It’s here. IT’S FOR REAL!! I am here to provide a list of things that boys should do (meaning they don’t do these things very often, probably why us girls think it’s adorable when they do) when they are pursuing one of us lovely ladies. There is a lot more to making her fall for you than you think, and yes, it’s the little things. The opened doors, the little touches, the tiny encouragements. Those are the things that matter. So here we go...

Considering how easy and convenient Photoshop has become, even for the average computer user, it's nearly impossible to tell whether a photo is authentic, or if it's had some "improvements."

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

A tip from The Virtual Frank on describing computer problems. Why not take a snapshot of the error to refer to later?

Need resources in Evony? Hack them… with a speed hack. You just need Cheat Engine and this video. Watch this video tutorial to learn how to hack speed in Evony with Cheat Engine (10/12/09). In order to perform this speed hack for Evony, you need to download Cheat Engine 5.5. Try it out for yourself.

Learn the basics of doubles tennis from our expert in these instructional videos. Watch as Tyler Thayer teaches how to score doubles, the different strategies to watch for while playing doubles tennis, how to serve, how to rush the net, how many sets are in a doubles tennis match, how to break a tie, and when and where is the best time to watch tennis.

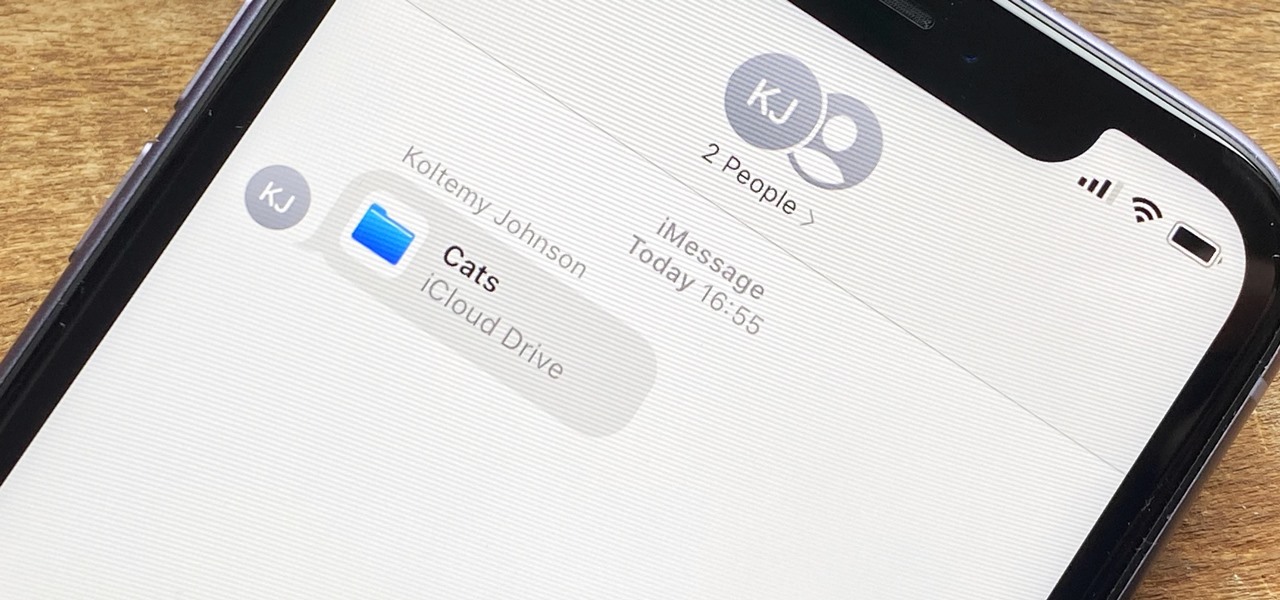
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

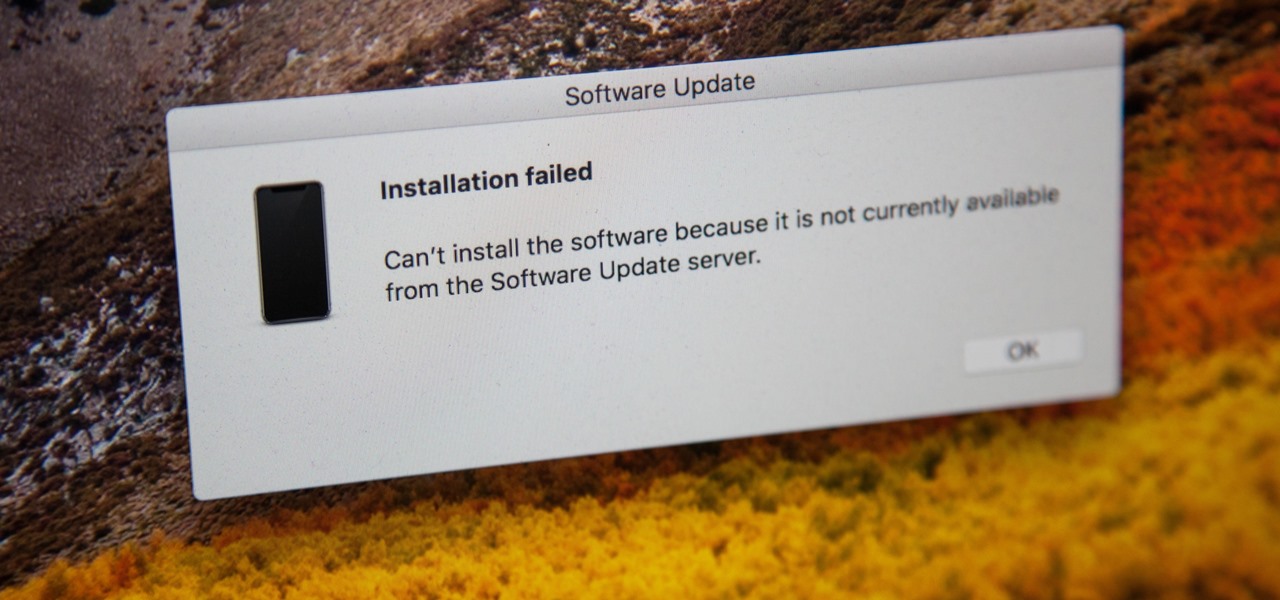
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.