
How To: Cook Without Measuring Tools
What would you say if I told you it was entirely possible—even desirable—to cook anything from a simple dinner to a great loaf of bread without using measuring cups, spoons, or a scale?


What would you say if I told you it was entirely possible—even desirable—to cook anything from a simple dinner to a great loaf of bread without using measuring cups, spoons, or a scale?
The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

Welcome back, my aspiring hackers!
Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great deal, the biggest issue most users have with the service is the limited amount of available content. Anything?

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

The biggest complaint I have with my Nexus 7 is the lack of support for different types of media files. I have a lot of movies and music that I've downloaded off the web, in many different formats, and I want them on my tablet.

There are two options when it comes to a dent in your car — live with it, cringing each time it enters your view, or get rid of it. While the latter is obviously the best option, most of us will probably just live with dents and dings since spare money is better spent on the actual functionality of the vehicle. However, there is a way to knock out automobile dents yourself with relatively little cash in the bank.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.
Everyone listens to music. I've got over 3,000 songs in my iTunes library, but am always looking for more, and I'm sure you are too. You can never have enough tunes to rock out to, right? If you're using Windows 8 like I currently am, these are some of the best apps in the Windows Store right now that will help you find new jams for your collection.

Computer Science Professor Francesco De Comité has a fantastic gallery of mathematical images on Flickr. As part of this collection, he has a few hundred images of real or rendered polyhedra made out of paper or playing cards which he calls "slide togethers." These are constructed by making cuts and then sliding one component into the other, creating a shape without using any glue. He constructed the entire set of the platonic solids—the cards form their edges—which can be seen in the image b...

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Dive (or more appropriately, soar) into another Tom Clancy video game on the Xbox 360— This walkthrough series for Tom Clancy's H.A.W.X. 2 covers the whole entire gameplay for the newly released sequel. Gun down countless MiGs, bomb enemy tanks and shoot down nuclear missiles before they destroy their targets! This video game is all about speed, battle and adrenaline. Try out this air combative flight simulator yourself, and see if you're not on the edge of your seat. Watch the full walkthrou...

Apple finally lets us fix sent iMessages, and I can honestly say it's a game-changer. Editing messages after sending them can prevent miscommunication and allow you to fix embarrassing mistakes before the other person notices them. It's one of the Messages app's coolest new features, but there are some important things for you to know about how it works.

One of Apple's most prominent iOS 16 features lets you unsend iMessages, but those aren't the only things you can take back. Your iPhone's Mail app also has the Undo Send feature, and unlike the Messages app, you can even customize the amount of time you have to stop an email before it's too late.

Apple released the third iOS 14.7 public beta for iPhone Tuesday, June 15. The update comes one day after Apple released the third 14.7 developer beta, and twelve days after the second iOS 14.7 beta, which was only released to registered developers.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).
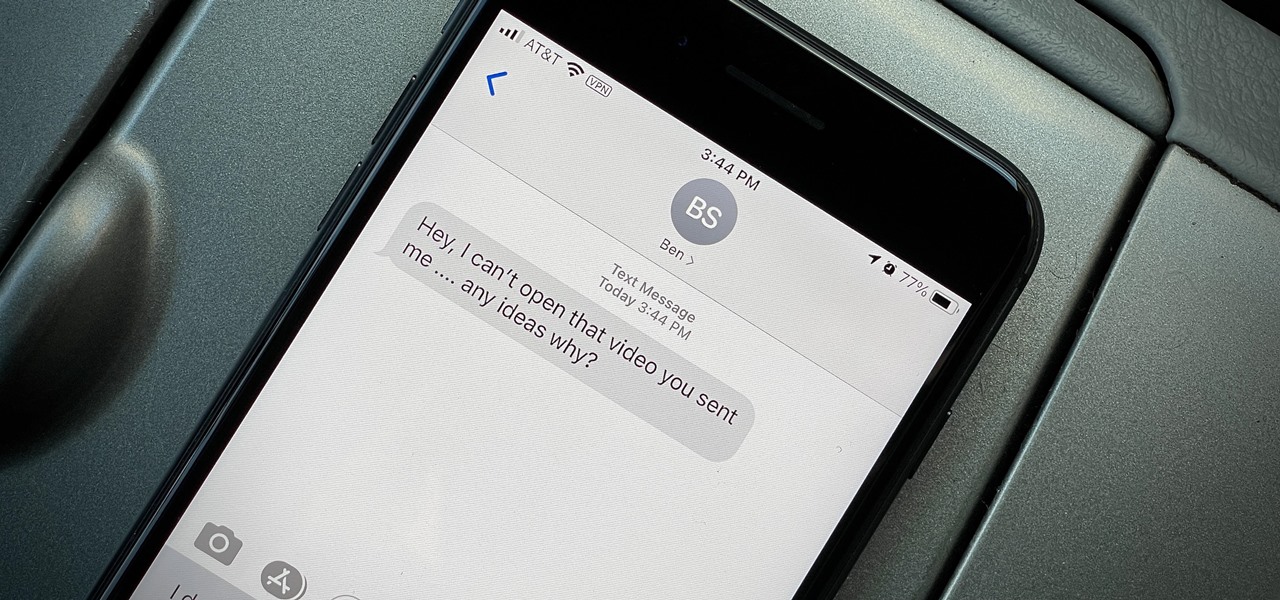
You take a photo or video, send it to a friend, and they say, "Hey, I can't open this." More often than not, your friend won't be using an iPhone, iPad, iPod touch, or Mac. Instead, they're likely trying to open the file with a non-Apple device. But this problem can be avoided if you know what setting to change.

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.
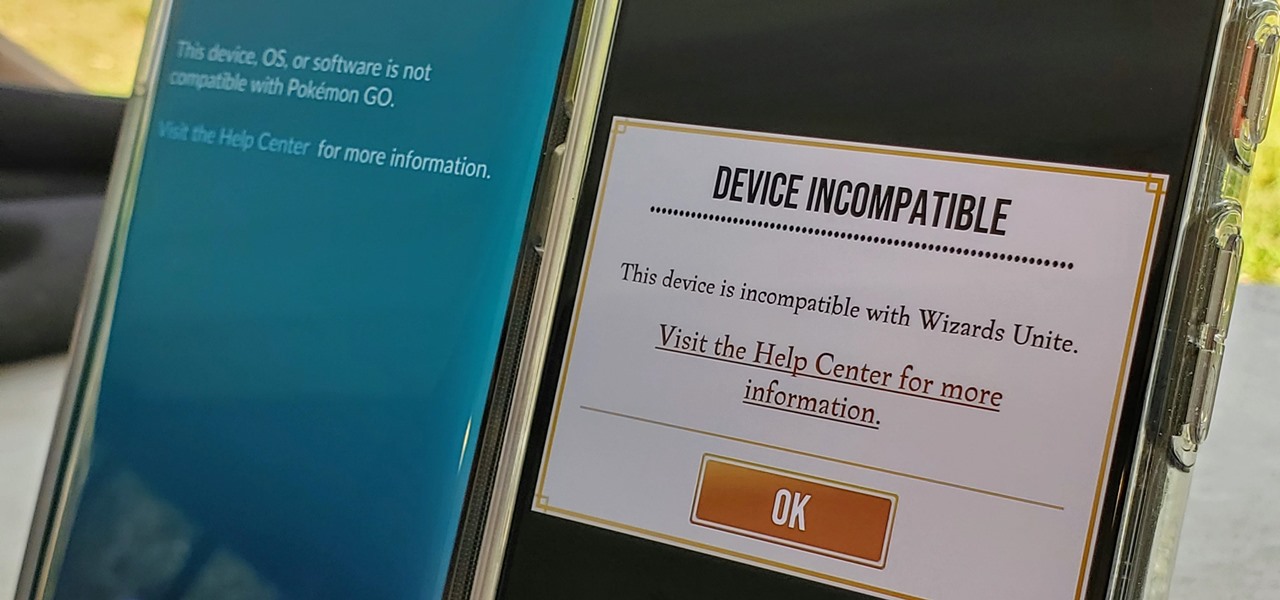
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.
There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.
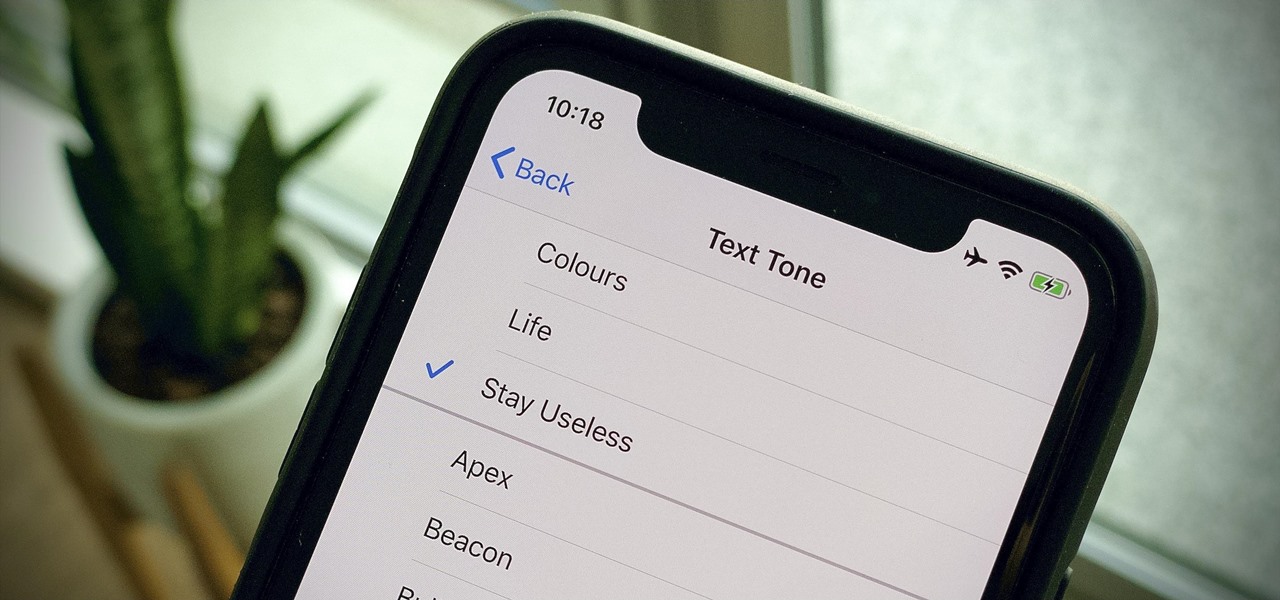
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.
Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.