Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.
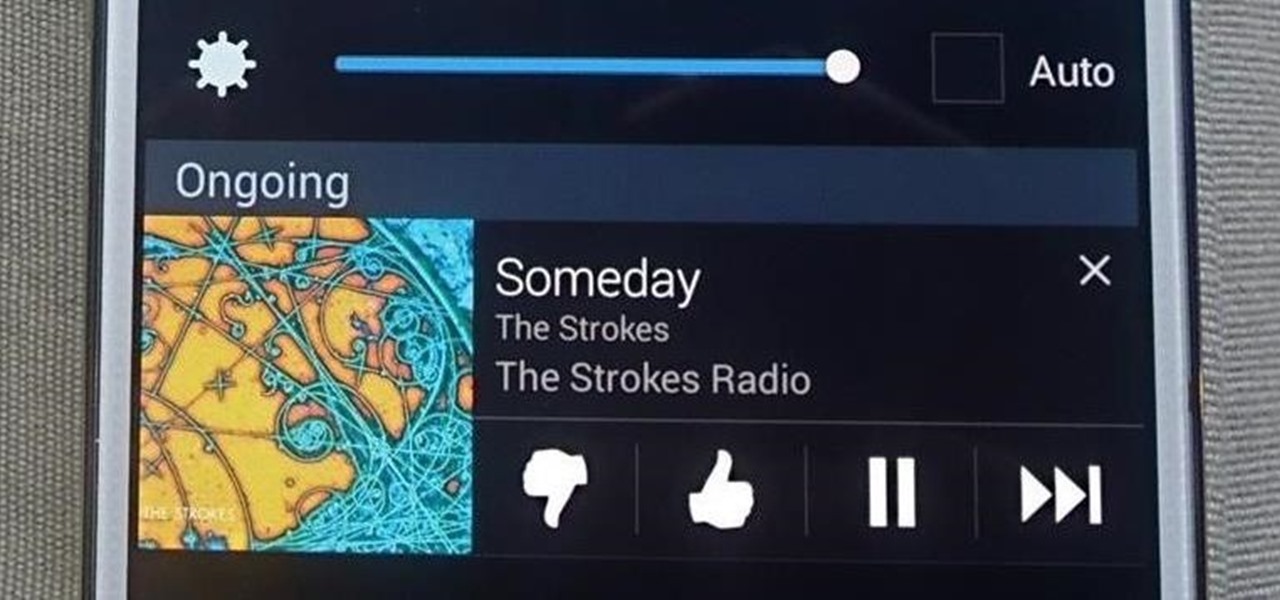
According to a recent survey conducted by Edison Research and Statista, Pandora still has a firm grasp as the most popular music streaming service in the United States. With iHeartRadio, iTunes Radio, and even Spotify trailing behind by a large margin, it doesn't look like Pandora will lose their footing in the near future.

One of the world's largest music festivals in kicking off this weekend in southern California, the Coachella Valley Music and Arts Festival. With a diverse lineup ranging from AFI to Empire of the Sun to HAIM to Muse, the music world is on display this weekend and the next.

Now that the Chromecast development kit has been out for over a month, more and more Android apps are being released or updated to work with the Chromecast.
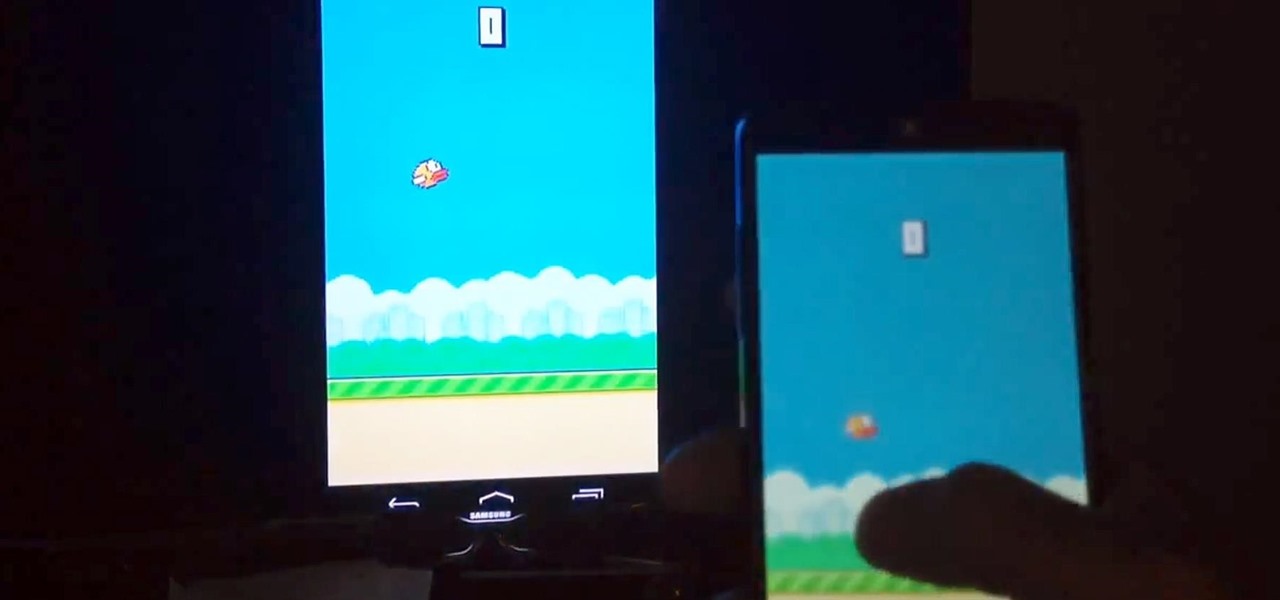
The flurry of Chromecast capable apps is slowly starting to gain steam; we've already shown you how to stream your local content from Android and iOS devices, but today we've got the teaser that many of us have been waiting for—full screen mirroring.

Android 4.4 KitKat has begun rolling out for the Galaxy Note 3 in India, Poland, Russia, Switzerland, and several other countries, and an unofficial build for AT&T customers has been leaked for all of us stateside.

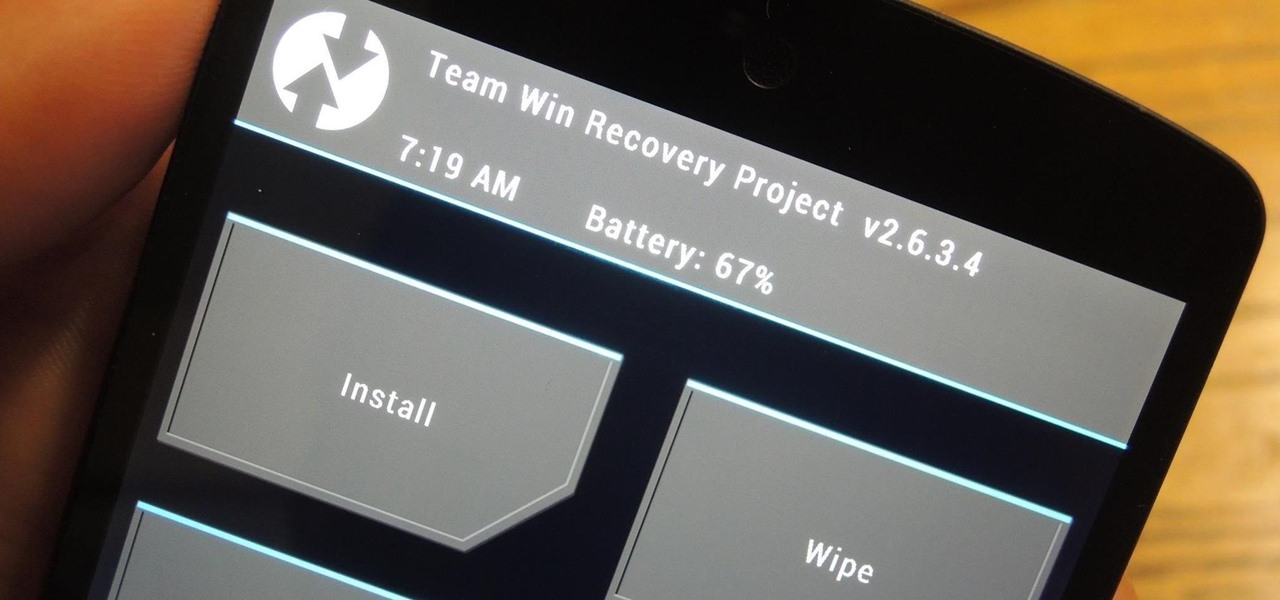
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

No matter your reason, if you want to hide what's on your computer screen from prying eyes, there are plenty of ways to do it. You can get a privacy filter, install a panic button for your browser, or just develop super fast reflexes. But all it takes is the right angle or a too-slow reaction to blow your cover.

Mac laptops, especially the older PowerBooks, often can become very hot when doing processor intensive tasks like movie rendering, YouTube videos streaming, database lookups, or just gaming. Often just lifting the machine from the surface is enough to cool it down without the need of expensive hardware or software tuning.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

A lot of my hacks use salvaged parts from an old microwave, with the microwave oven transformer (MOT) being the most useful component.

While Siri's integration with the iPhone is becoming increasingly substantial, restrictions with the intelligent personal assistant are apparent when it comes to third-party apps like Google Maps, Netflix, and Spotify (unless your iPhone is jailbroken, of course). As an avid Spotify user, it's distressing that I can't use Siri to navigate through the music streaming service's extensive library. In the car, I use Spotify about 90% of the time and it can become increasingly frustrating to chang...

There are some pretty incredible camera techniques out there, but the biggest problem that amateur photographers run into is that they don't have the equipment to try them. You can still get some great shots, but there are some things that are really hard to do if you don't have the money to drop on expensive lenses and accessories.

I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

I can imagine you sitting there thinking to yourself, "I've played a lot of games! I bet he won't have any that I don't know about!" Well, that's entirely possible. I'm only drawing from my own personal experience here, so you may, in fact, know of all these games.

You can create a lot of impressive effects by stacking or layering photos, whether you do it in a darkroom or with Photoshop. The Harris shutter effect makes your photos super colorful, and double exposing or stacking negatives makes for some crazy looking portraits.

Monitoring your storage space is always a nuisance, whether you have a desktop, tablet, or smartphone; having enough space for all of your files, music, and videos is a constant battle. One movie file can take upwards of 1GB of memory, and for people who travel a lot, it becomes extremely impractical to have those huge files on your portable device.

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

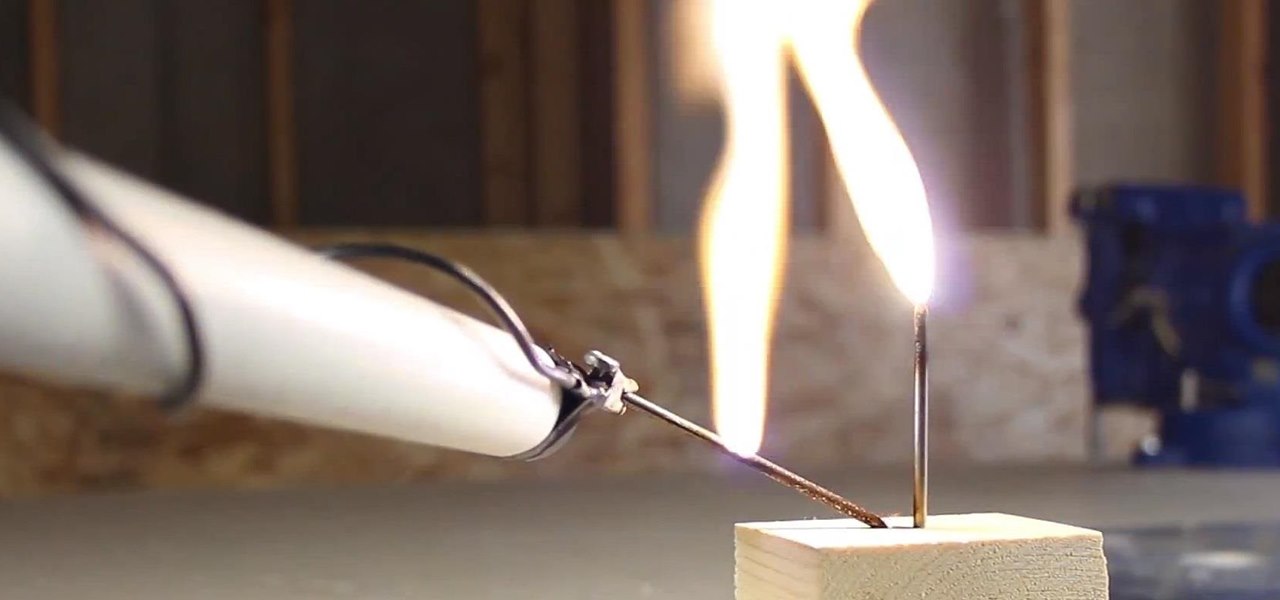
In a previous project, I showed how to build an electrical Jacob's ladder using an old microwave oven transformer (MOT). In this project, I modified the secondary coil on the MOT, which converts it from a high voltage/low current device into a low voltage/high current metal melter!

Want to know when you have a visitor, even if you're not home? You could always set up a security system and live-stream it with your iPhone. But if you don't have a spare iPhone, or just don't want to go to the trouble, this simple hack will add text message alerts to your doorbell so that it lets you know when someone's there.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Hate answering the door, but don't trust your friends with a set of keys? This RFID front door lock made by Steve Pomeroy will solve all your party-hosting problems. It reads the RFID tags in his friends' public transit cards and decides who's allowed in based on "groups" that Steve defines. And I have to say, it's also rather stylish. It's controlled by an Arduino serial console and a custom Android app to add and remove cards. The reader can store 50 or 100 tags at a time and allows 7 diffe...

I have owned quite the plethora of electronics in my life. A commonality between most of these devices' screens is frozen or dead pixels. This is probably the most annoying thing about buying new hardware—your LCD, or worse, LED display has one or more pixels that continues to stay lit. Most of the time, this will appear in the form of a brightly colored pixel that never changes, or a pixel that never displays the right color. Once you notice it's there, you just can't stop staring at it. It ...

Stuck on one side of a river or ditch? If you are stranded with no other way to get to your destination you will need to build a bridge! Without many supplies, your best bet is a beam bridge which can be made with just a single piece of wood. This video will show you how to get from one place to another.

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you Christian rock guitarists how to play a solo from a Matt Redman song. Not just any Matt Redman song, but one of his greatest: "Blessed Be Your Name." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Do not discount the "pretty" rocks found along with gold. The sapphires you see are worth many times more than gold. Sapphire (& Ruby, (corundum), is like garnet, a relatively high specific gravity that will catch in a sluice readily. These gems act as gold, they will drop behind a boulder, in bedrock cracks, and set up in the stratiform layers of a bar on the inside bend of a stream. In a perfect (laboratory world) a river bar sets up from front to back: Gold, Platinum, Lead, Iron Ore (black...

Get out your army pants and prepare to conquer your backyard. Learn how to play Capture the Flag with this video

Learn how to convince someone to go skinny-dipping. The trick to getting someone to skinny-dip with you is to make them think it's their idea.