Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

If you bought the new iPhone 5, you've probably been less than thrilled with the lack of cases and accessories that you can use it with. Docks are no exception—users were disappointed to learn that Apple has no plans to even make one for the newest addition to the Apple family.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

There are two parts to the StormShield product: The server components (including the relational database and server) and the various agents that run on each endpoint. Among other things, the agent contains a host-based firewall and policy engine that can be customized to control applications and particular endpoint device features such as USB peripherals and registry entries. So watch this tutorial and learn how to protect your PC computer with SkyRecon's StormShield.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Recently, iPhone users have been bragging that they can set Live Photos as their lock screen wallpaper. While this is a great way to spice up a boring lock screen, Android users shouldn't feel left out in the cold. The highly customizable and feature-rich OS has a few tricks up its sleeve too, and it's really easy to set any GIF as your Android's home screen and/or lock screen background.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

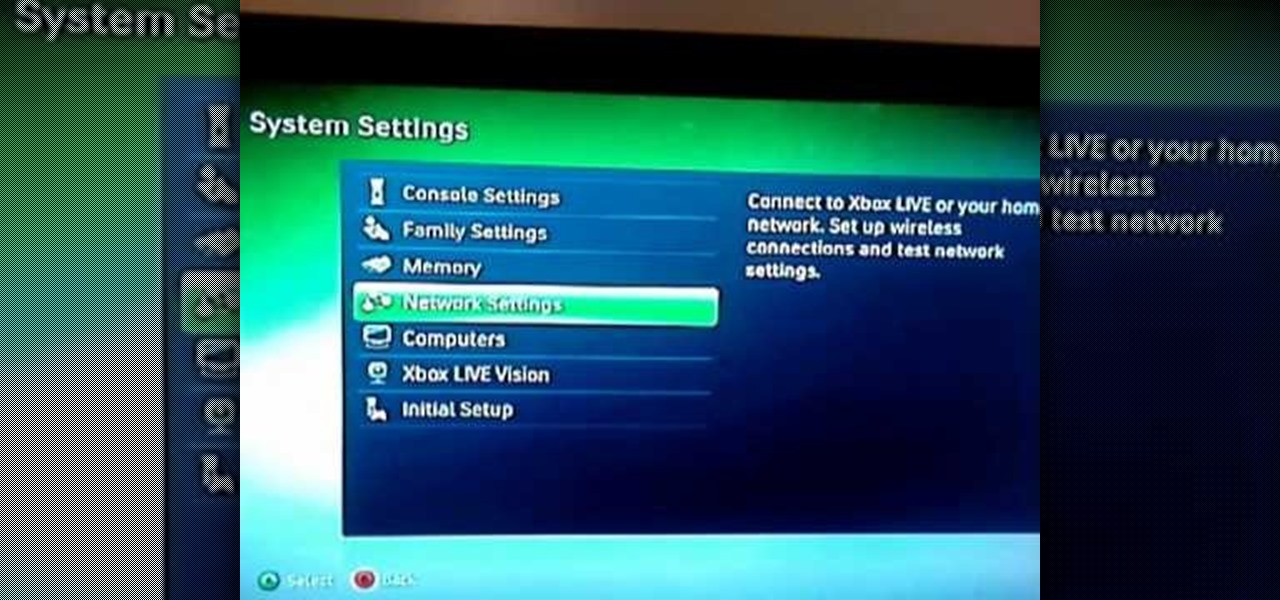
Your router is automatically equipped with firewalls meant to protect your PC from intruders. However, these firewalls often misread information needed to run online video games, and block necessary files from reaching your XBox. In this tutorial, learn how to change the NAT settings of your modem to "Open" and allow these files to get through. By doing so, you will be able to take full advantage of your XBox Live account.

Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row.

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need

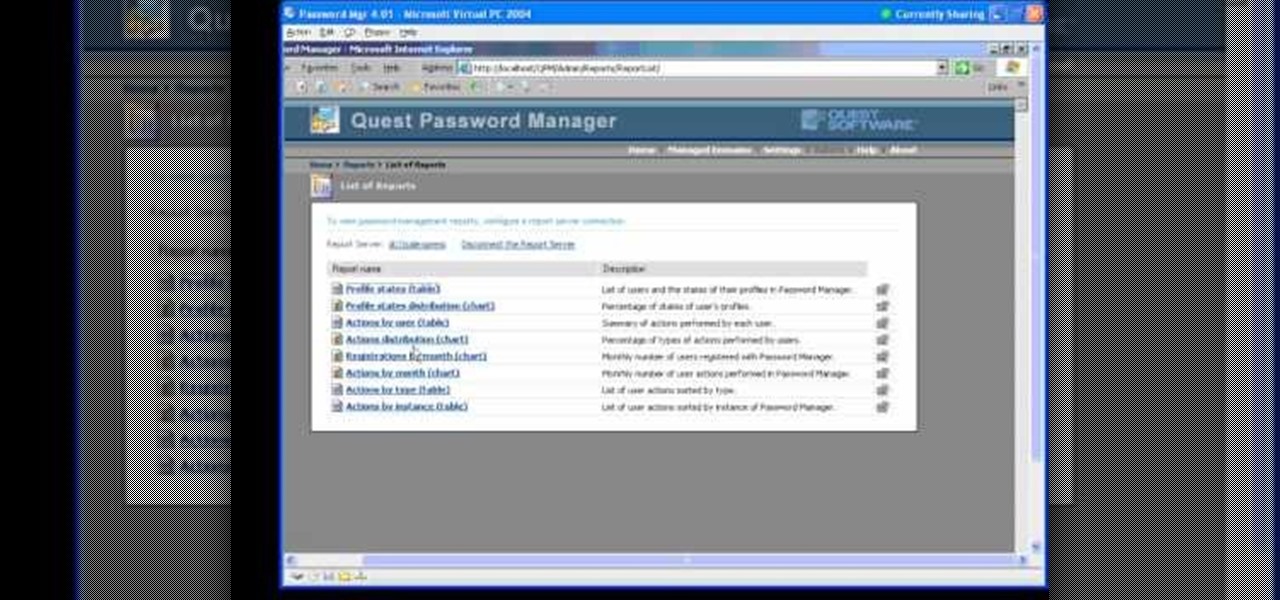
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

Crusty, itchy, red eyes? There is a decent chance you could have conjunctivitis, or pink eye, an infection of the thin lining around the eye and the eyelid, caused by bacteria, an allergen, virus, or even your contact lenses. Whatever the cause — you call up your doctor to get a prescription to clear it up, right? Not really.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Apple wastes no time with betas. Right on the heels of the official release of iOS 12.1, Apple released the first beta for iOS 12.1.1 to developers on Wednesday, Oct. 31. The update comes just one day after iOS 12.1, which itself was in beta development for 43 days this year. The denotation for 12.1.1 indicates it's a minor update over 12.1, and there are only a few things in its release notes.

In an SEC filing published on Monday, Snap, the company behind Snapchat, disclosed that Imran Khan, its chief strategy officer and a member of the NR30, is leaving the company to "pursue other opportunities."

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

While some in the augmented reality space are tweeting about future amazing immersive experiences and others are showing off cool experiments, Microsoft continues to move forward with tangible business solutions right now that show how the HoloLens can improve business.

Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expect to see one of those in the list of top apps. Unfortunately, that's exactly what happened — Google is promoting obvious adware in their list of best apps.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

While many have their own strong opinions on Apple and their products, few have complaints about the way they embrace accessibility. Apple typically finds ways to make products functional to all customers, regardless of their situation. This philosophy can be seen in Apple's partnership with Cochlear, as the two develop a new cochlear implant sound processor for iPhone.

Beware: After a new caucus — the Congressional Caucus on Virtual, Augmented, and Mixed Reality Technologies for the 115th Congress — formed in the US House of Representatives, the government has decided to go after all mixed reality head-mounted displays. The HoloLens, Magic Leap — nothing is safe anymore.

Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

Google dropped its opposition to T-Mobile's Binge On service due to some favorable policy changes at the magenta carrier. From now on, YouTube and Google Play Movies will happily work with the feature. Binge On rolled out late last year, allowing many customers to receive unlimited video streaming at 480p. That's not a great offer if you care about video quality, but it's nice if you want to save money.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names: