Find out how you can kick butt in Obsidian Entertainment and SEGA's video game Alpha Protocol. The RPG and action hybrid came out on June 1st, 2010, and is available on the PlayStation 3 (PS3), Microsoft Windows (PC), and the Xbox 360. This video game walkthrough series from Mahalo focuses on Alpha Protocol for the Xbox 360.
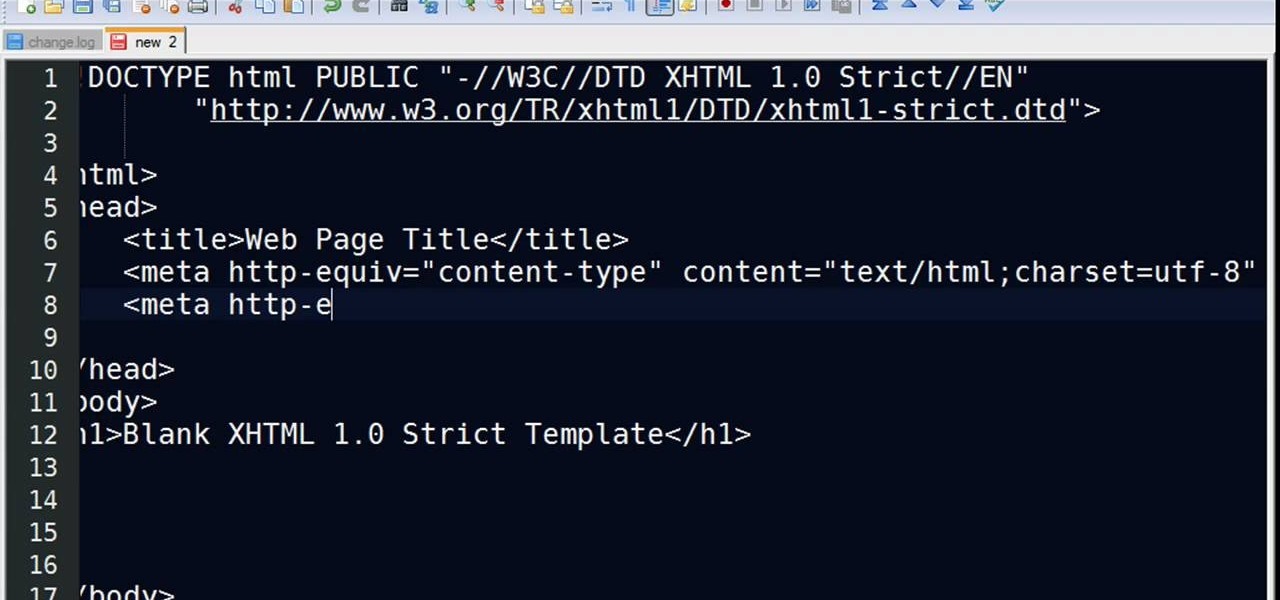
In this clip, you'll learn how to use the Notepad++ text editor to create XHTML 1.0-strict templates. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started creating your own XHTML templates, take a look.
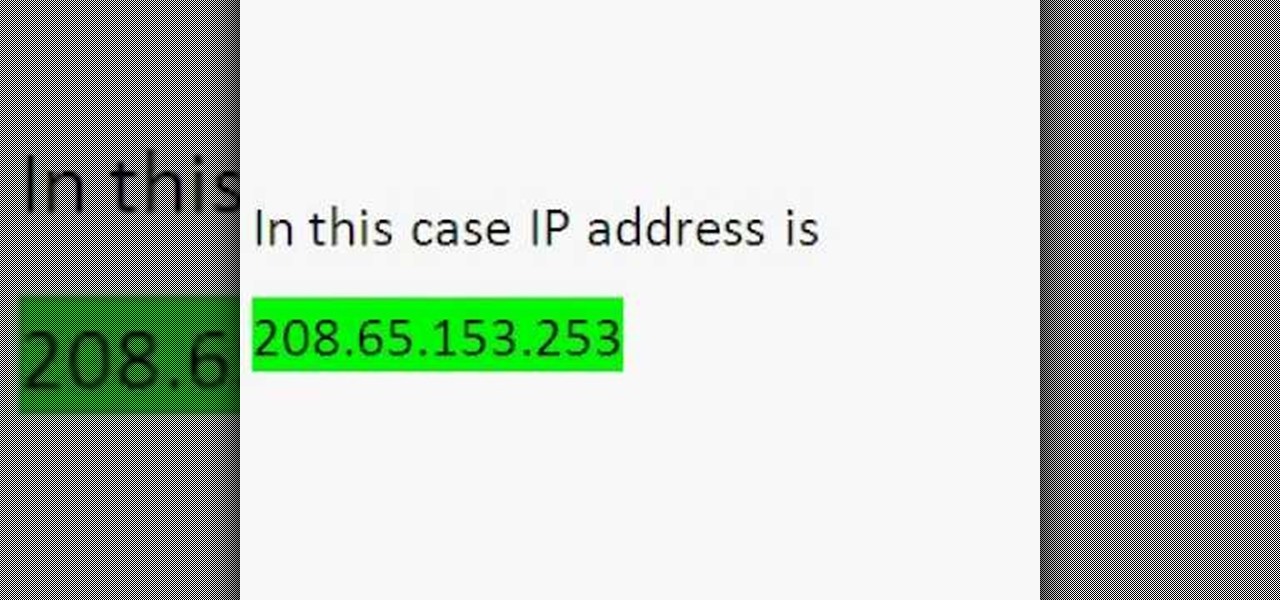
Wondering how to find the Internet Protocol address of a website?
***WARNING*** Do not record ANYTHING without strict permission from the person or persons or artist that you're recording.

Are your white walls closing in on you? Are you moving into a dorm room or have a strict landlord or parental unit? No worries, we have no-nail and no-paint wall solutions for you in this episode. This week, we will make DIY wall decals that are easy, movable and stylish. With a full wall decal guide and peeks into how other nesters DIY their wall decor.
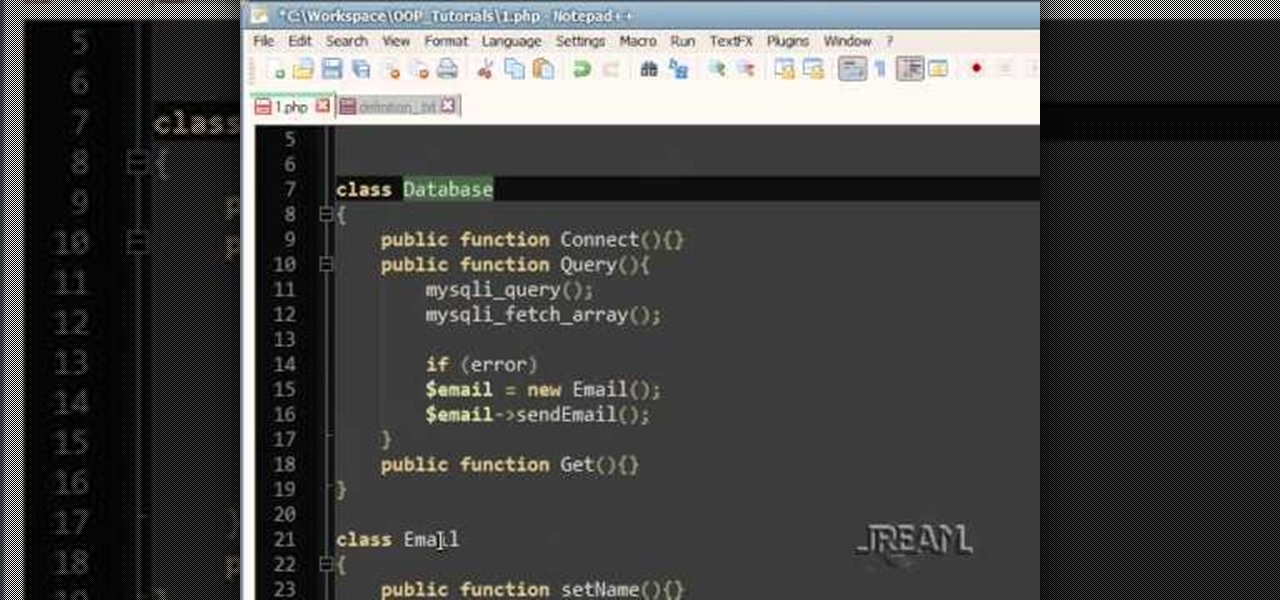
One of the things you'll need for a successful future in programming is a great re-usable library of code. In order to achieve that you'll need to practice strict organization and consistency with your coding. This tutorial shows you how to do both, and help up your PHP proramming potential.

It's time to practice your pick-up lines for this achievements. The game is Alpha Protocol and the objective of this achievement is to become more than friends with a character in the game known as Madison Saint James.

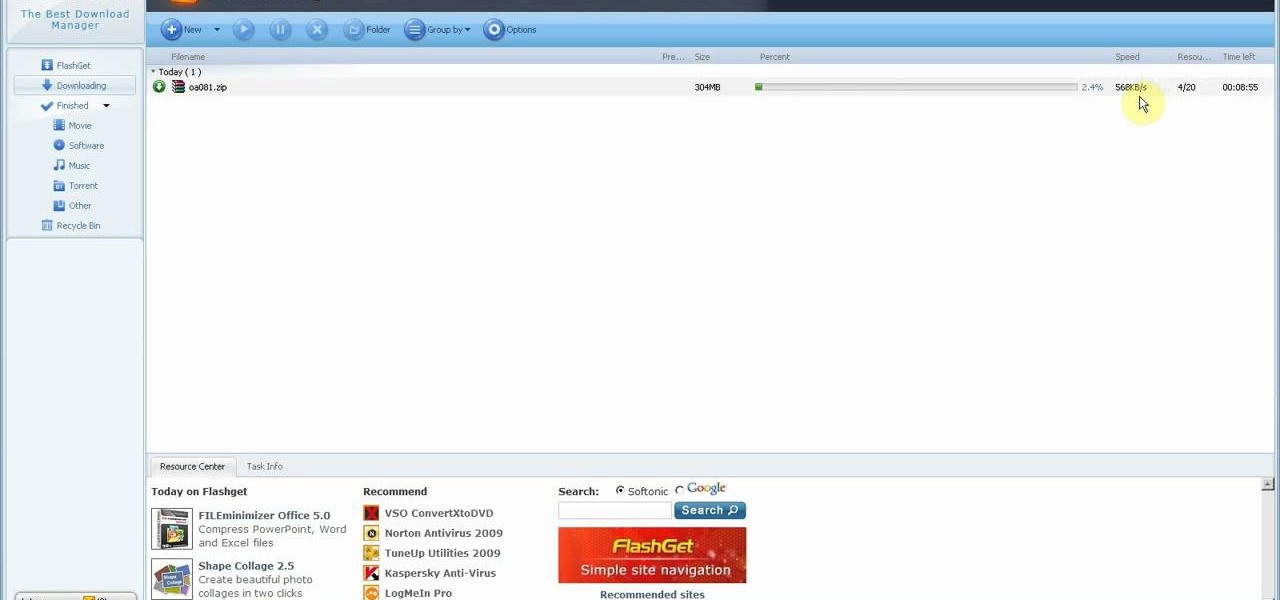
FlashGet 3 is a free high speed download manager that helps you keep track on how much far your downloads have left to complete. FlashGet supports HTTP,FTP,BT,MMS,RTSP and other protocols. It is seamless between protocols and there is no need to operate manually for download switch.

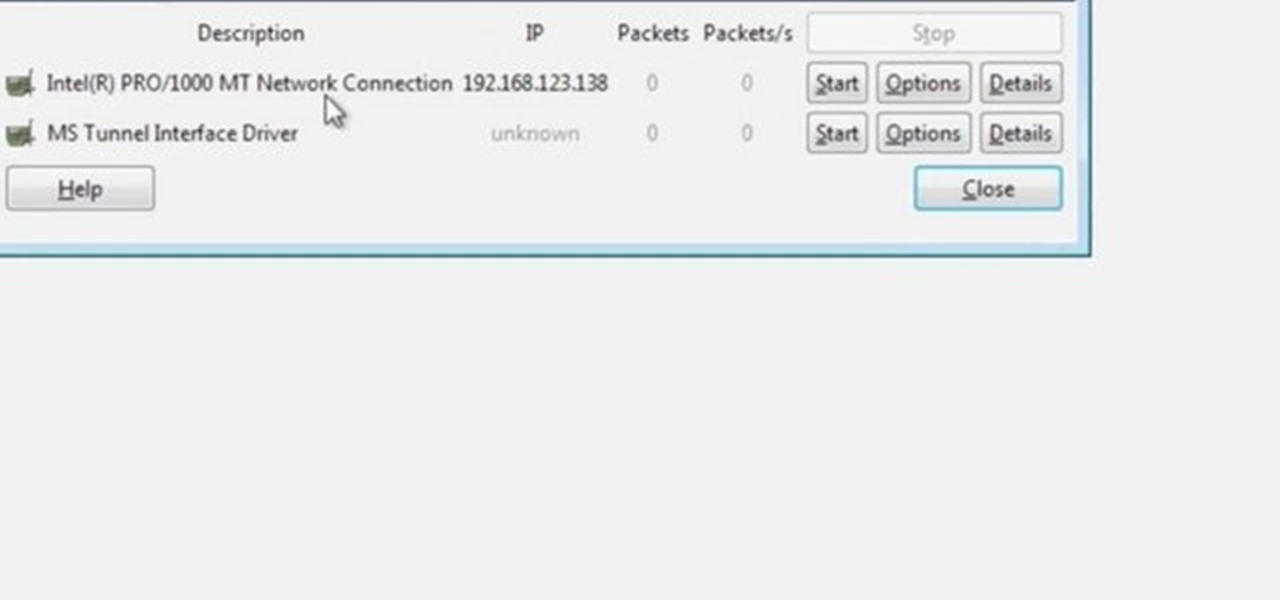
In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Adobe apparently did not plan for it's AIR protocol to lead to people turning their websites into programs, but it turns out that it is fairly easy to do. This video tutorial explains in great detail how to create an AIR application using Flash CS4. Topics include how to create a digital signature and .swf files that you will need to create the program.

It's time for another achievement video and another chance for you to show your stuff. In the game Alpha Protocol, you'll be going up against enemies with guns, who are trying to kill you and end the game. But something a bit more challenging that you might face are the women.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

No pain, no gain honeys! Though there exist a few genetically gifted women in this world (we're looking at you, Megan Fox), the rest of us have to commit to eating right and exercising in order to maintain fabulous bodies. It isn't fun, but sticking to a strict diet and workout routine does produce a pretty sexy body.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

How do you know if you are making progress when you put yourself on a strict diet and exercise regimen? Many people wonder whether the numbers going down on the scale means they're losing fat, and if the numbers are going up, whether they're gaining muscle. This is a question that many body builders and those trying to lose weight (while gaining muscle) try to understand on the way to their goal weight.

In this video tutorial viewers learn how to wear the National Working Uniform. This uniform has a strict policy and all must follow the uniform rules. The basic components of the uniform are: an eight point cap, blue cotton undershirt, shirt, trousers, belt with closed-faced buckle, black boot socks, blousing straps, black 9" steel-toed leather boots, embroider rank insignia and service & name tapes. This video is very detailed and clearly explains all the uniform expectations. This video wil...

Your home router is automatically programmed to run firewalls to protect your computer from viruses. Unfortunately, these firewalls often mistake programs needed for online gaming as intruders and block them.

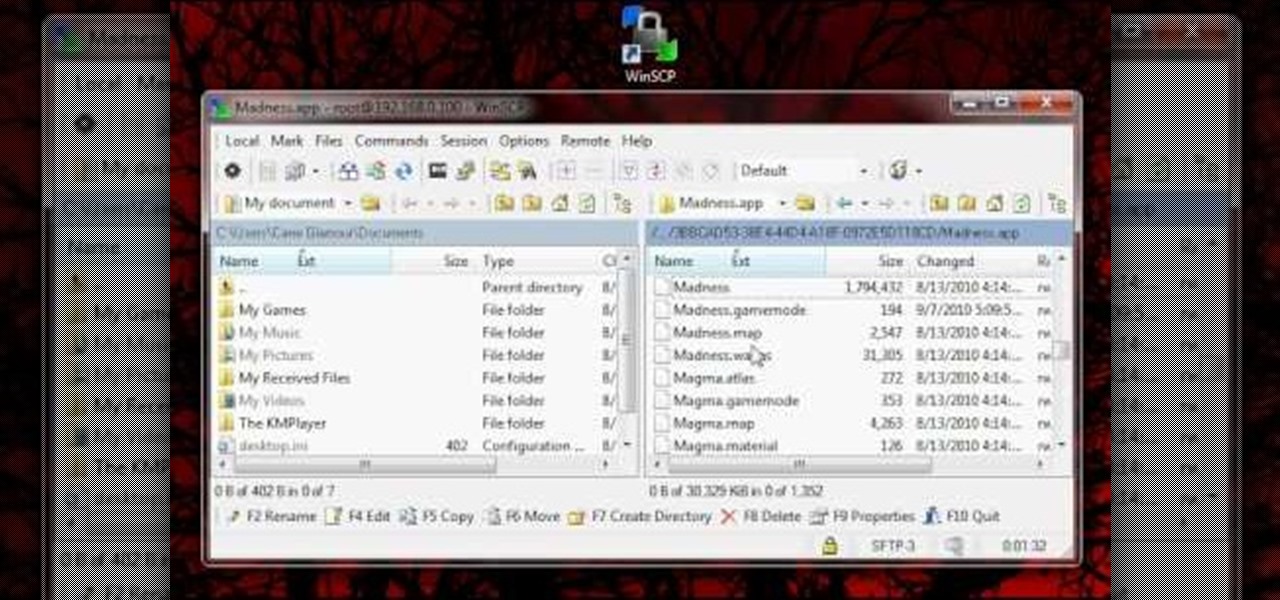
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory until you find the TowerMadness app. Once you have opened the TowerMadness app, all you need to do now is find the right file and change it around to increase the amount of money you have!

Streets of willow springs instructional video goes over protocol and instructions to racing on Willow Street. He goes over all the turns and when to accelerate and turn. This discusses the surfaces and sections of the track. This is a great overview on how to start racing on tracks around California. If you like Nascar, you will love racing your own car at Willow Springs.

Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

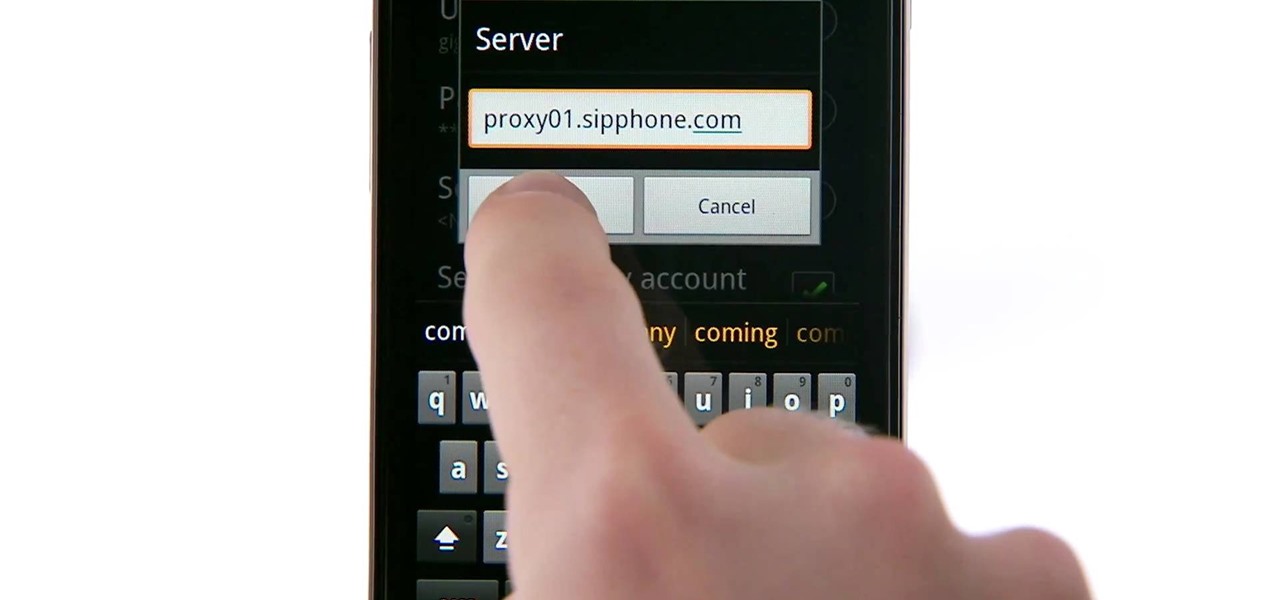
If you've got Android 2.3 Gingerbread running on your Google Nexus S smartphone, try out this cool feature. Set up a SIP (Session Initiation Protocol) account, and you'll be able to make Internet calls over Wi-Fi. You'll be able to talk to anyone with VoIP.

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

This clip presents an overview of the general technique required for pairing a mobile phone with a headset via the Bluetooth wireless protocol. For detailed instructions, and to get started pairing your own cell phone with Bluetooth-enabled devices, take a look.

Adding resistence in the form of weights to your workout is the best way to increase the difficulty of the exercise. This forces your muslces to work harder and makes you burn more fat (which is always a good thing).

This medical how-to video demonstrates how to do an equipment setup for hemodynamic monitoring. Follow the instructions and protocol for the equipment needed to setup hemodynamic monitoring before the physician arrives. This procedure is typically used for pulmonary artery catheter insertion.

Going to school to become a nurse? Then one of the many things you will do as a nurse is trying to keep your patients comfortable while they are in the hospital. Follow along in this nursing how-to video and watch as the nurse places an abductor pillow under a total hip replacement patient. Sue, a physical therapist, shows you the correct protocol for administering abductor pillows.

Studying to be a nurse? Then follow along with this nursing how-to video to learn how to administer an intradermal injection. This injection technique is very common in nursing. Watch and observe the nursing student as she shows you the proper protocol for an intradermal injection. Before starting always make sure to check the doctor's orders and have all your equipment handy.

Studying to be a nurse? Then a very common procedure in nursing involves removing a saline lock or an IV line. This procedure is also called DC IV, or discontinue an IV. Follow along in this nursing how-to video to learn the proper protocol for discontinuing an IV line. Before DCing the IV always double check the doctor's orders and have your materials handy.

Studying to be a nurse? Then a very common procedure in nursing involves removing a saline lock or an IV line. This procedure is also called DC IV, or discontinue an IV. Follow along in this nursing how-to video to learn the proper protocol for discontinuing a saline lock. Before DCing the IV always double check the doctor's orders.

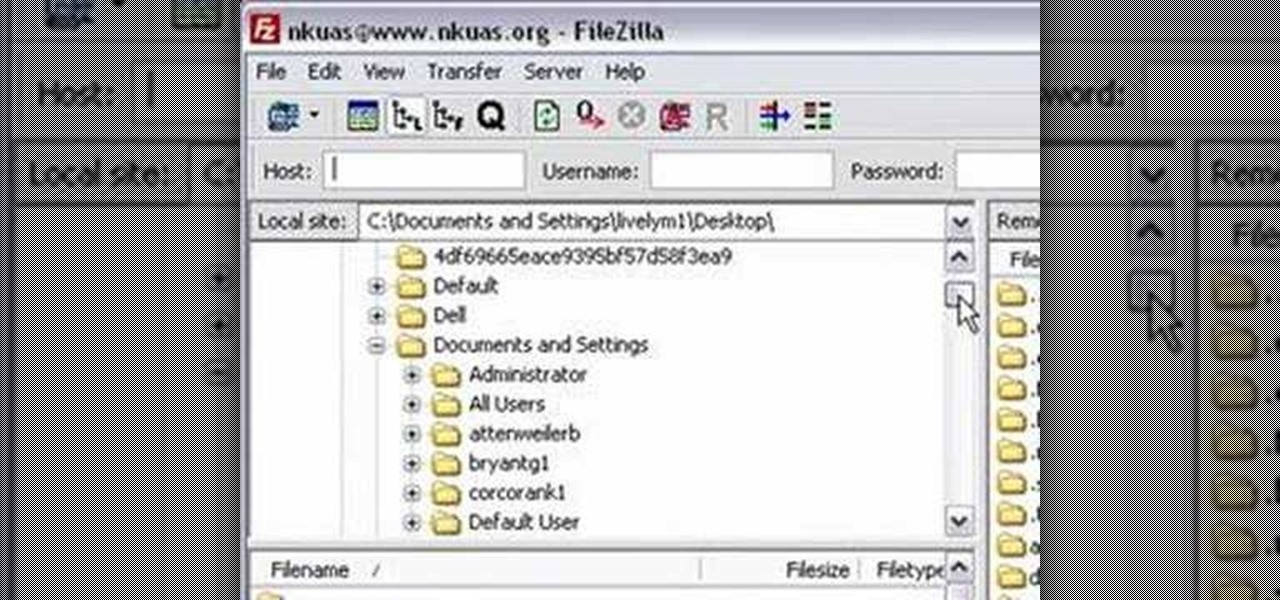
In this video tutorial from Matt Overwine of the Instructional Design Group at Northern Kentucky University, you'll find instructions on how to use the FileZilla FTP, or file transfer protocol, client to upload to the web. FileZilla is available for both Mac OS X and Windows XP and Vista. For more information, and to get started using FileZilla for yourself, watch this handy how-to.

This is a Computers & Programming video tutorial where you will learn how to change your NAT to OPEN with a Linksys router. Go to your browser and type in 192. 168. 1. 1 and that will take you to the basic set up. The authentication dialog box comes up. Type in ‘admin’ for the username as well as the password. These are default settings. In the Linksys page, go to ‘applications and gaming’ and on the Port Range page fed in these information. Your application you can name anything. Start 80, E...

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Watch this science video tutorial from Nurd Rage on how to make a test tube thunderstorm. They show you how to make the thunderstorm in a test tube using alcohol, sulfuric acid and potassium permanganate.

In this clip, you'll learn how to reset the IP (or Internet protocol) address on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Watch this video to learn an easy way to FTP (file transfer protocol) files using the Safari browser.

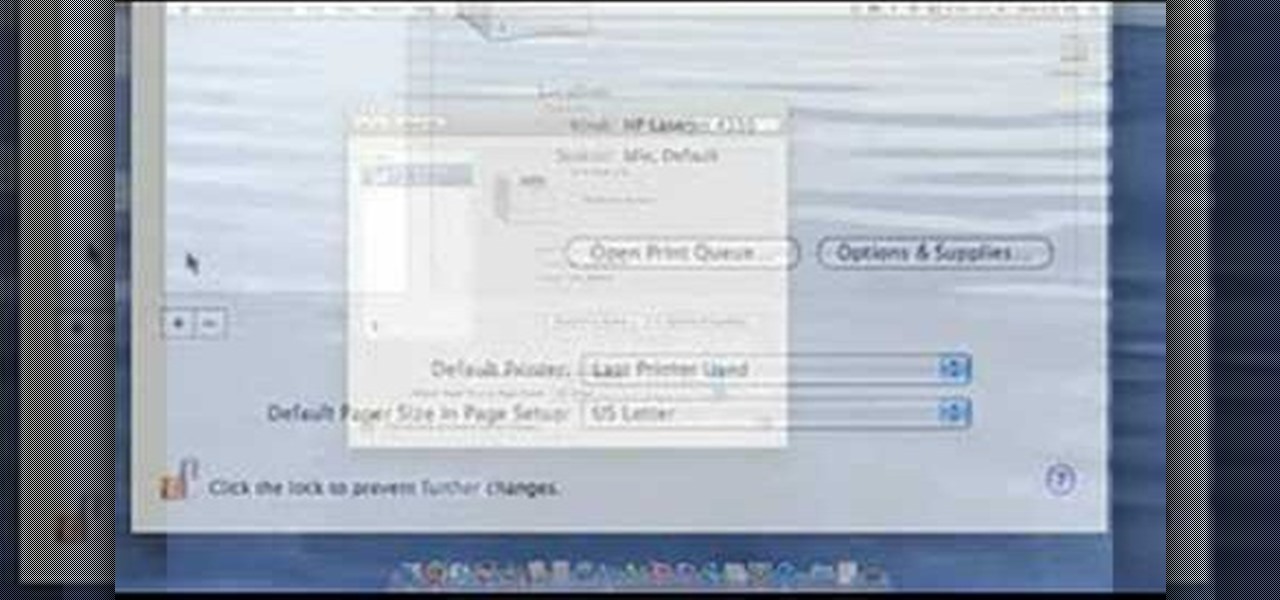
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...