
How To: Make a Simple UDP_Flooder in C pt2
Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.


Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

This Scooby's Workshop video shows how to add resistance to make pull-ups more difficult. This is the key exercise for building your lats if you are doing home workouts. You can also use a weight lifting belt and chain to hold the weight while doing these pull-ups. Wait till you can do at least 12 reps with strict form before you start adding weight.

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.
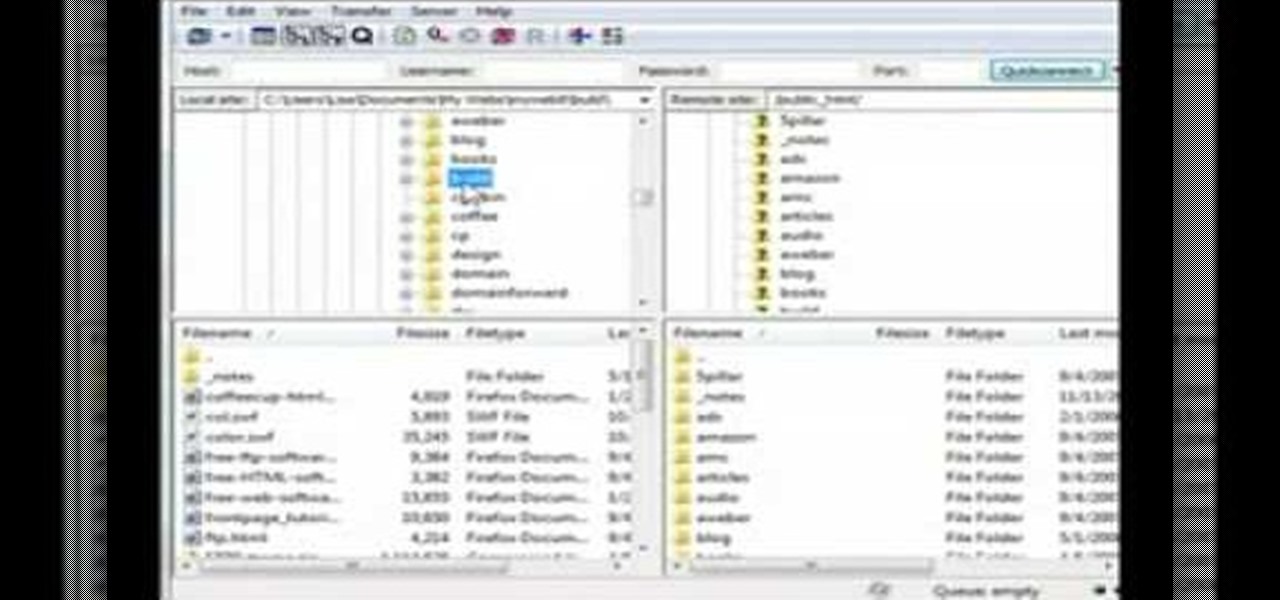
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

Steps to Configure Your Modem/Router are: 1. Open Network connection and click properties

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...
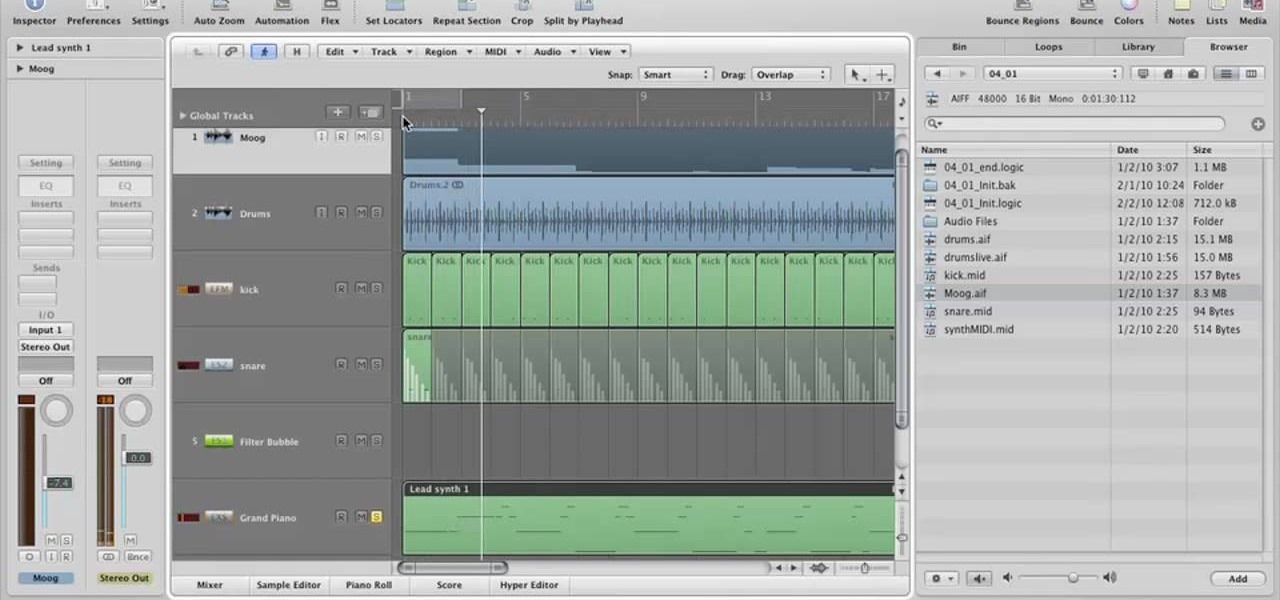
This Lynda tutorial teaches how to use the Logic pro, a songwriting application. Midi sequencing and quantizing is the main focus of this video. Midi is a short name for Musical instrumental digital interface. Midi is not sound. It is a low resolution computer protocol, developed in early 80’s to enable computer to communicate each other. Midi is fast, simple and reliable. It has a intensity stream. In this project, Scot Hirsch explained how a midi file is manipulated in Logic pro. Midi file ...

Going to be a nurse? Then one of the procedures you are sure to encounter in the hospital is the removal of an arterial line. Follow along in this nursing how-to video to learn how to remove the arterial line from a patient. Remove of you a line is also known as discontinuing the line. In shorter terms many nurses also say DC the line. Follow along and learn the standard protocol for removing arterial lines.
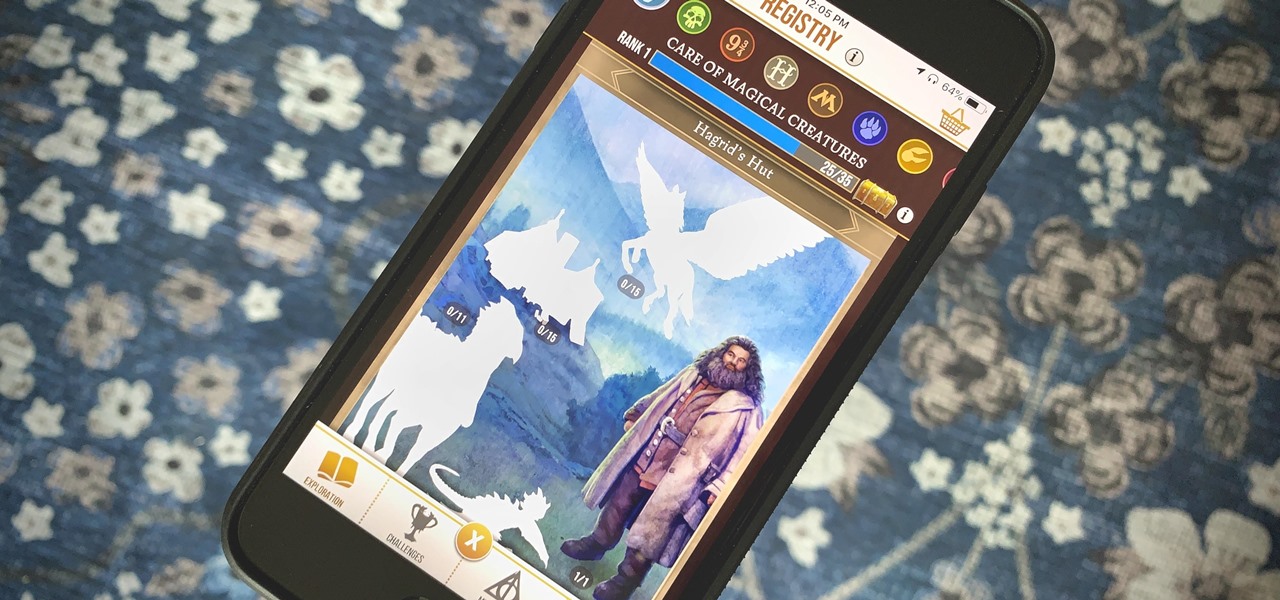
From the first moments of booting up Harry Potter: Wizards Unite to the hours of walking you're bound to experience, one thing is clear — encountering Foundables and defeating their Confoundables is a significant plot point of the AR game. While you receive rewards each time you retrieve a Foundable, the real treasure comes from completing parts of the Registry, called "Families."

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.
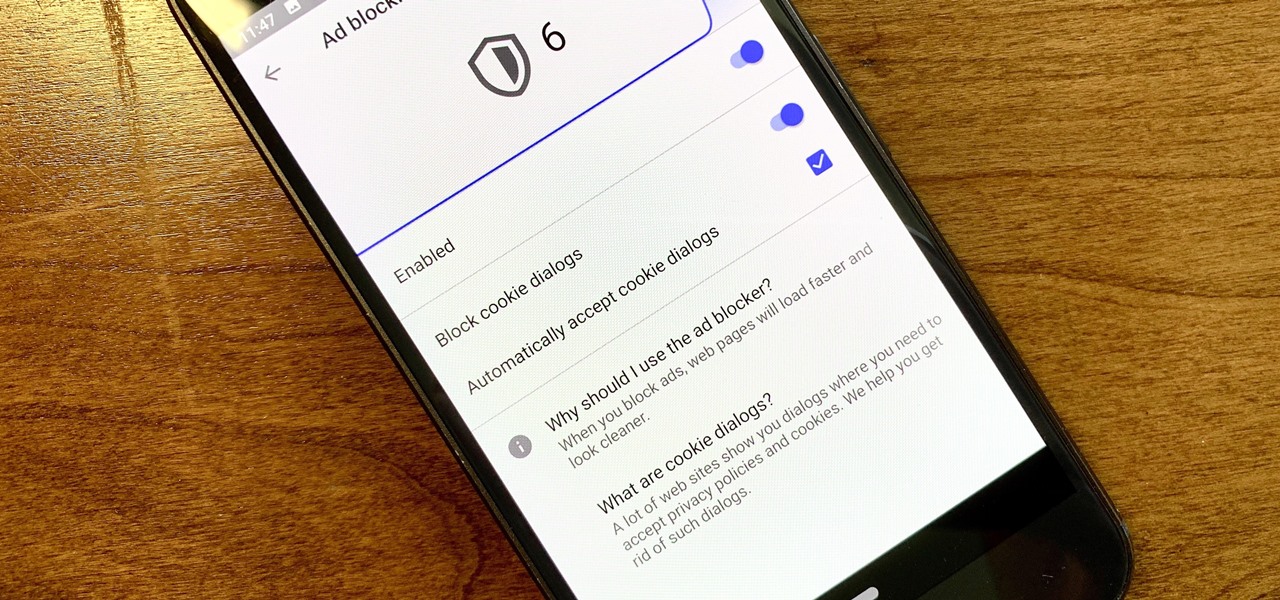
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Who doesn't experience food cravings? Whether you're trying to adhere to a strict diet, or simply hoping to avoid sugary, fatty foods, curbing cravings can feel like a monumental task.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Fish is a remarkably useful ingredient, whether you eat it as is or use fish sauce to give your recipes extra depth and flavor. However, if you enjoy a glass of Guinness on occasion, you might be surprised to know that there's most likely fish in that beverage, too.

With the release of the Nexus 5 back in 2013 came the Google Now Launcher, which has become the go-to choice for many Android users, especially those who prefer the Nexus line. With its integration of the Google Now page and the always-listening hotword detection, you'd be hard-pressed to find a more complete and useful launcher.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Ah, the art of the April Fool's prank. If you're a dedicated prankster, you probably already know who you're going to get on the big day. But if you're still searching for a prank to pull, never fear—we've got one that's pretty easy to execute and is guaranteed to get reactions. Those Oreo cookies look irresistible, right? Unless you're on a strict no-chocolate diet, you wouldn't be able to help yourself from shoving those in your mouth—and that's where the fun comes in.

I never really cared much for the clock widget on my Nexus 7, mainly because it only gave me two styles—analog and digital. There are many different styles of clock widgets available on Google Play, but the majority of them just don't look good enough for me.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:

Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.
It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

If you're looking into rooting your device yourself, you're going to need ADB and Fastboot on your computer.