
How To: Connect a Sony PSP to the Internet via WiFi
This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.


This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

In this video you will see how to access network security cameras through google search engine easily!

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Battery life is precious to all mobile device users, and nothing is worse than running out of it. The only thing that can save a device from the dreaded low battery warning is the charger, but who carries those around?

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.
No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

Get an inside on how to build a home server that hosts all of your DVDs and movie content.
Adding clients to your network is a quick and easy process in Mac OS X Leopard Server. In this video tutorial, you'll find step-by-step walkthrough for the client adding process. For more, or to get started adding clients to your own Leopard Server, watch this video tutorial.
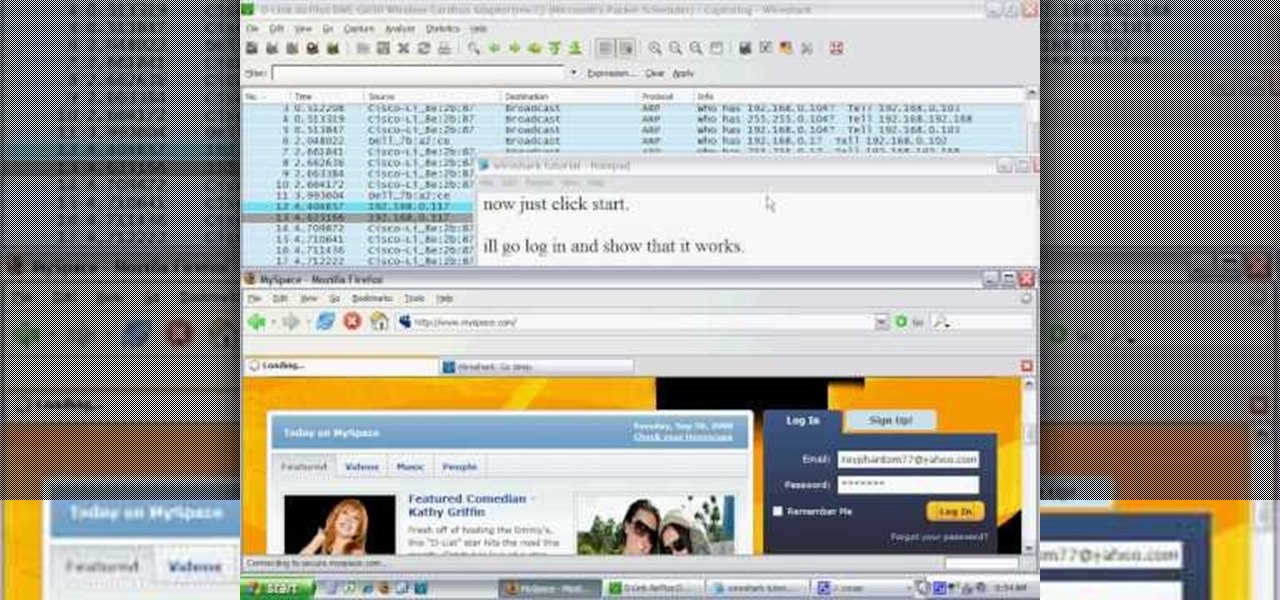
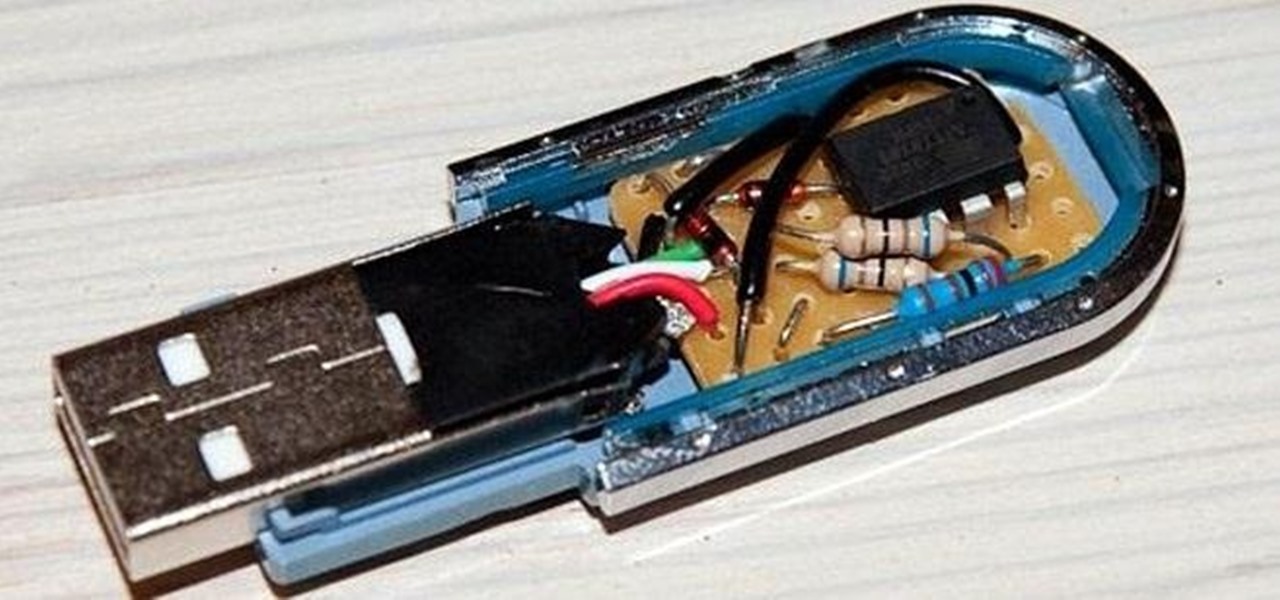
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

The Care Bears have stood the test of time, from their first appearance on greeting cards, to cutesy, plush teddy bears, to animated television series, to adventure-filled movies. The Care Bears may be long gone from television, but not from out hearts (especially Sara Griffith's of SharksBiteOfLife).
Urgot is a unique champion who can deal out high amounts of damage early in his game, and eventually evolves into a tank/assassin hybrid who can be sent after important enemy targets. Here's a guide for building and leveling Urgot to take advantage of his capabilities to help your whole team.

Galio's strength on the Fields of Justice comes from his ability to tank, though he can provide a bit of team support as well. This guide goes over his strengths, and gives good advice when it comes to making an optimum build for the Sentinel's Sorrow for your next League of Legends game.
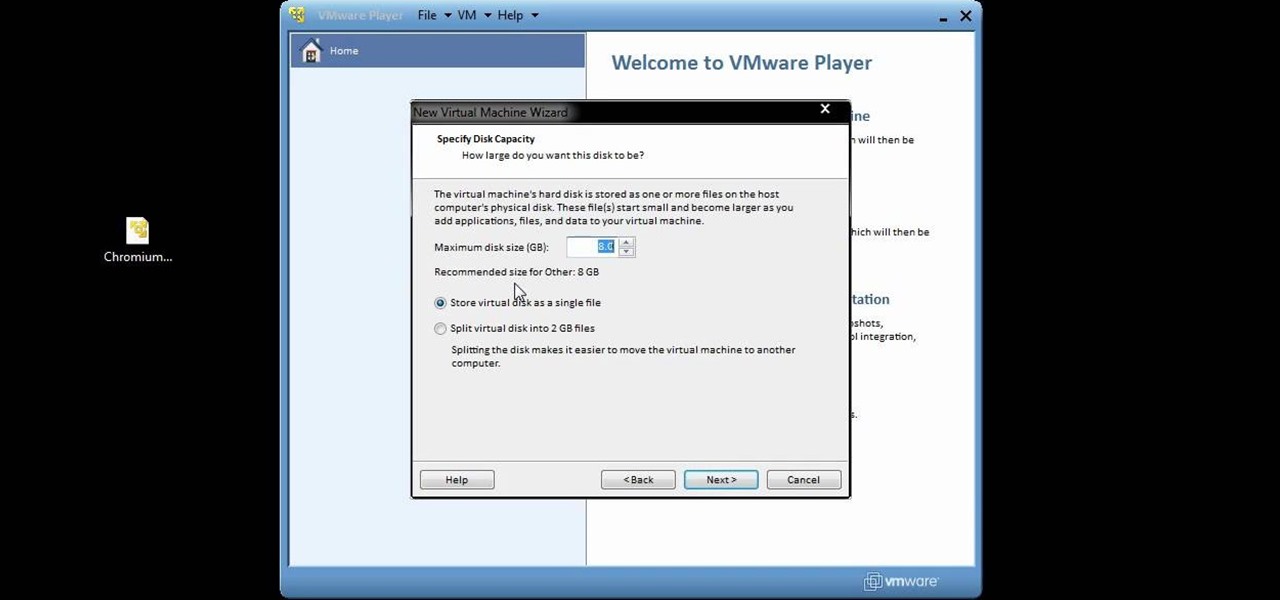
You can setup Chromium OS in a virtual machine. So first go to the download site for Chromium OS and VMWare download for the VMWare Player. Now run the VMWare Player and click on "create a new virtual machine" and select "i will install the operating system later" and click next and then next.

The iPhone has always has one very big problem: that it is tied to AT&T. AT&T is a terrible network, and many iPhone users out there are probably dying to switch network but keep their awesome phone. Well now they can! This video will show you how to unlock you jailbroken iPhone 4, 3GS, or 3G using a program called Ultrasn0w, leaving it ready for use on any cell carrier in the country. Except Sprint, they don't have SIM cards.
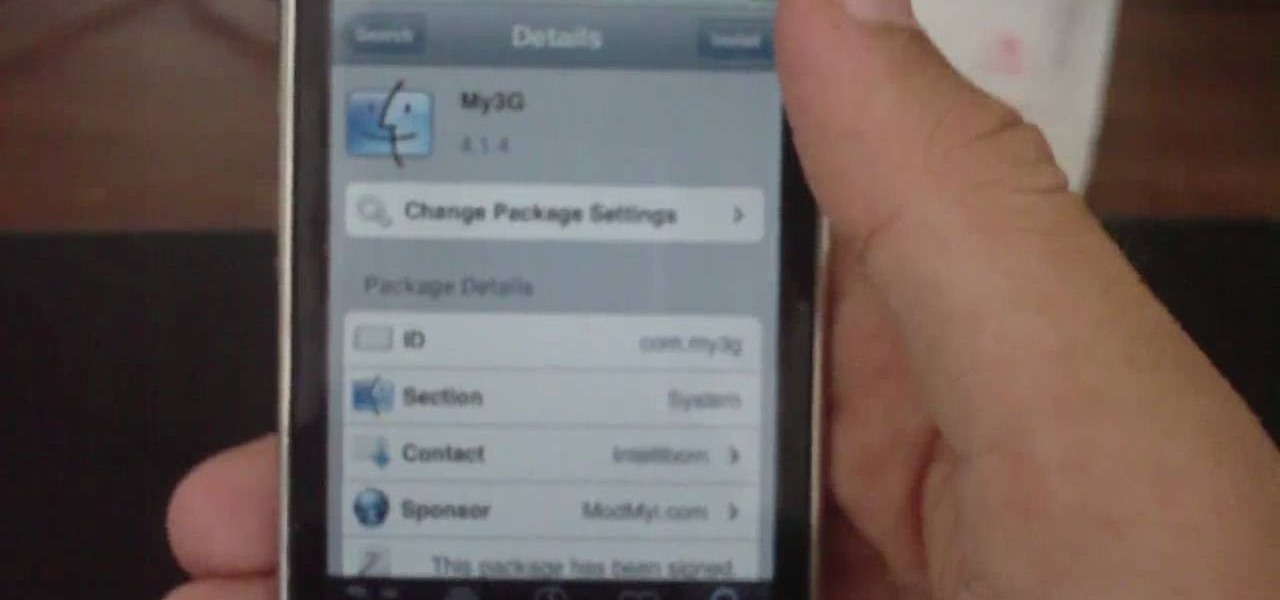
FaceTime is a very cool Apple App that makes video chat possible on the iPhone, but only if you're on a wifi network. Officially, at least! One of the many cool things that you can do after your jailbreak you iPhone 4 is use FaceTime on the 3G network! This quick video will show you how to enable Face Time 3G use using a jailbreak App called MY3G.

To make a french spiral bouquet you first start with straight stemmed flowers such as roses. It is very important that you rid the stems of foliage such as leaves as well as removing all the thorns. You can do this by using a gardening glove or washcloth and sliding it down the stem. Once that is completed it is time to begin the bouquet. The first step is to pick a base flower. It is important to use a flower that has a straight stem. From there you begin to add flowers by crossing them with...

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

Surprise your sweetheart this Valentines Day or any night, with a delicious Indian version of tiramisu. Tiramisu is traditionally an Italian dessert, and this is a similar recipe with an Indian twist. Why not give it a try? No one can resist the creamy deliciousness of fresh Tiramisu.
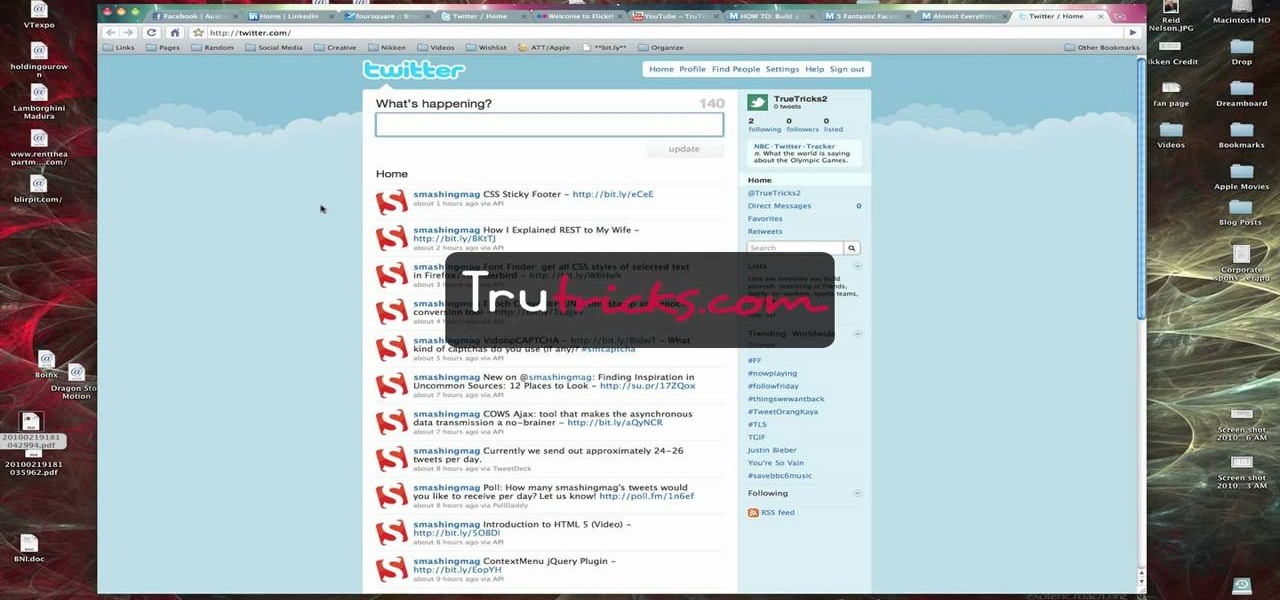
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...
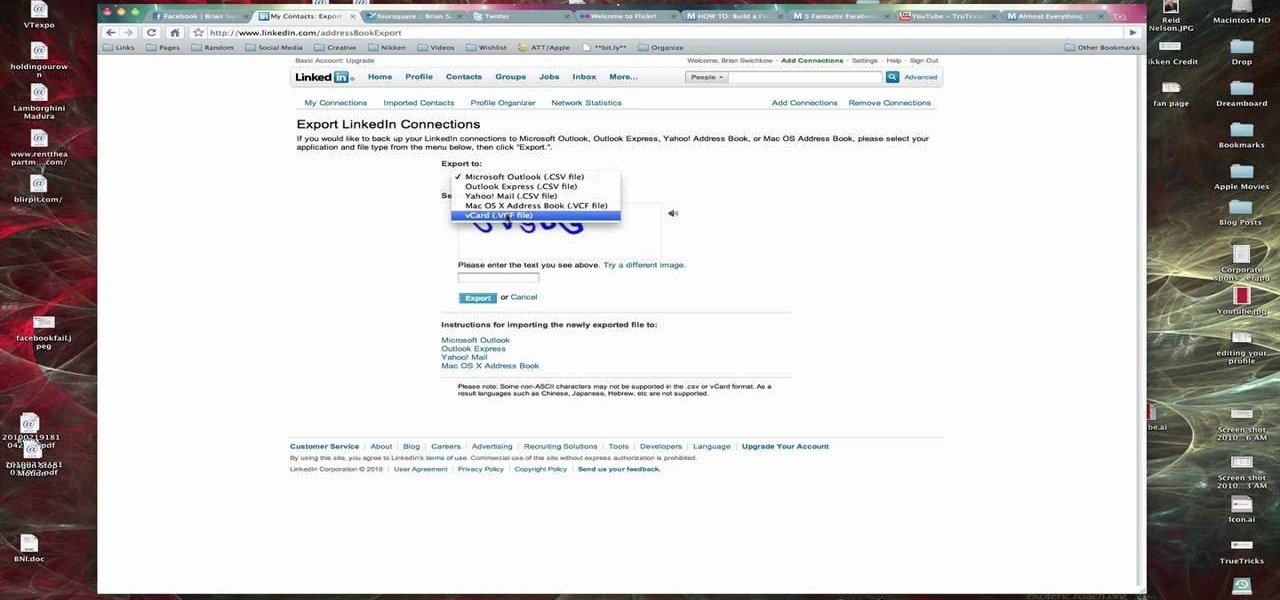
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...