This video tutorial teaches how to find homegroup password in Windows 7. For this you should be using the computer which is part of the homegroup. The way to check this is by going to the control panel and clicking on network and internet link. In the ensuing window the network and sharing center link is clicked. This will show if the computer is connected to the home group. On confirming that the computer is connected to the homegroup, now navigate back to the network and internet link, and ...

In this ExtremeBartending video, we learn how to make the perfect Mint Julep cocktail. Start with a Collins glass. Take four sprigs of mint (it's very important that it be four) and place them in the glass. Add a teaspoon of sugar, and about two tablespoons of water (it's a strong drink, so you might want to add more water). With a muddler, mix it up, and this will expand the taste of the mint. Now grab some crushed or shaved ice and put it in the glass. Add an ounce and a half of bourbon, ga...

If you had to answer the following statement, which answer would you choose? Water is:

Elie Krieger from Food Network bakes up a scrumptious chicken pot pie. Her version will give you a healthy boost because she added extra vegetables and cut down on the fat. This southern dish is sure to warm up tummies everywhere and you can customize the ingredients based on your family's tastes. For example, you may want to use turkey instead of chicken, or possibly beef. Maybe your family likes different vegetables. This particular recipe uses chicken, onions, carrots, celery and green bea...

Make spring rolls like a professional! Use pre-packaged purchased wrappers. Have some egg yolk ready. Apply some egg yolk on the edges of the wrapper, so that it can act like glue. Paint it on all 4 edges. You can use a brush for that. The filling is pre-prepared. It is a mixture of vegetables , cooked pork, and cooked shrimp. We will then add ginger and soy sauce to the filling. Take a small amount of filling, so that the spring rolls are thin, because that is how they are meant to be. Fold ...
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.

In this "super" video tutorial, you'll learn how to convert a Super Nintendo controller to PC controller. Now, dig deep into your garage and pull out those old SNES pads (or controllers) and get ready for some "super" modding!

Watch this science video tutorial from Nurd Rage on how to test if a fertilizer has nitrates rather than urea or ammonia as its nitrogen source.

The V-Cube 6 puzzle is a uniquely designed and constructed skill game. V-Cube 6 is a multi-colored, multiple-layered cube, rotating smoothly on based axes. The player is required to discover a strategy to achieve uniform color sides on her or his V-Cube, but in this process, the Rubik's Cube-like puzzle may break, especially if you're in the process of speedsolving.

Learn how to do single-leg flat bench standups and sculpt your body without weights! Presented by Real Jock Gay Fitness Health & Life.

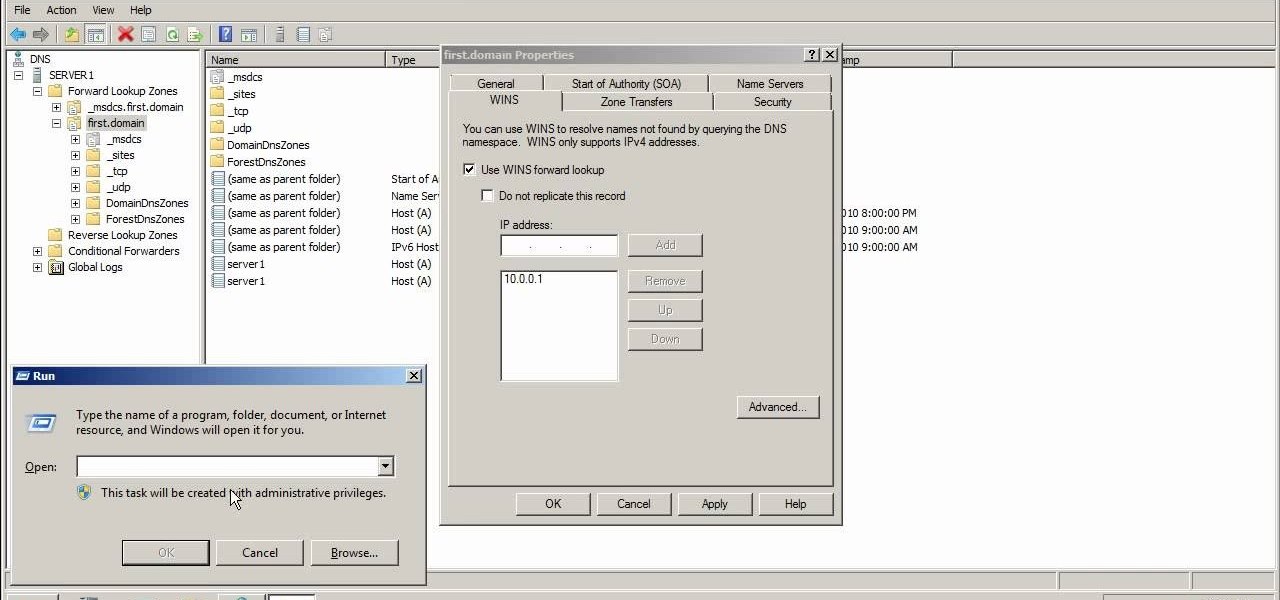
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.

A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

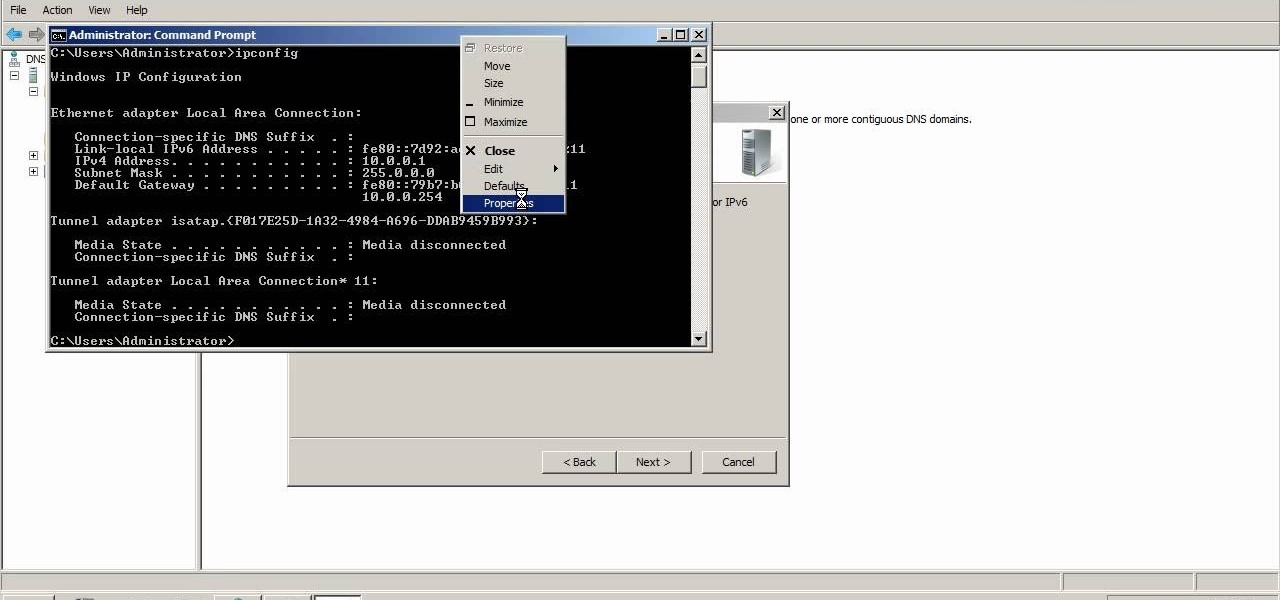
In this tutorial, you'll learn a few standard methods for resolving less common and more complicated wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

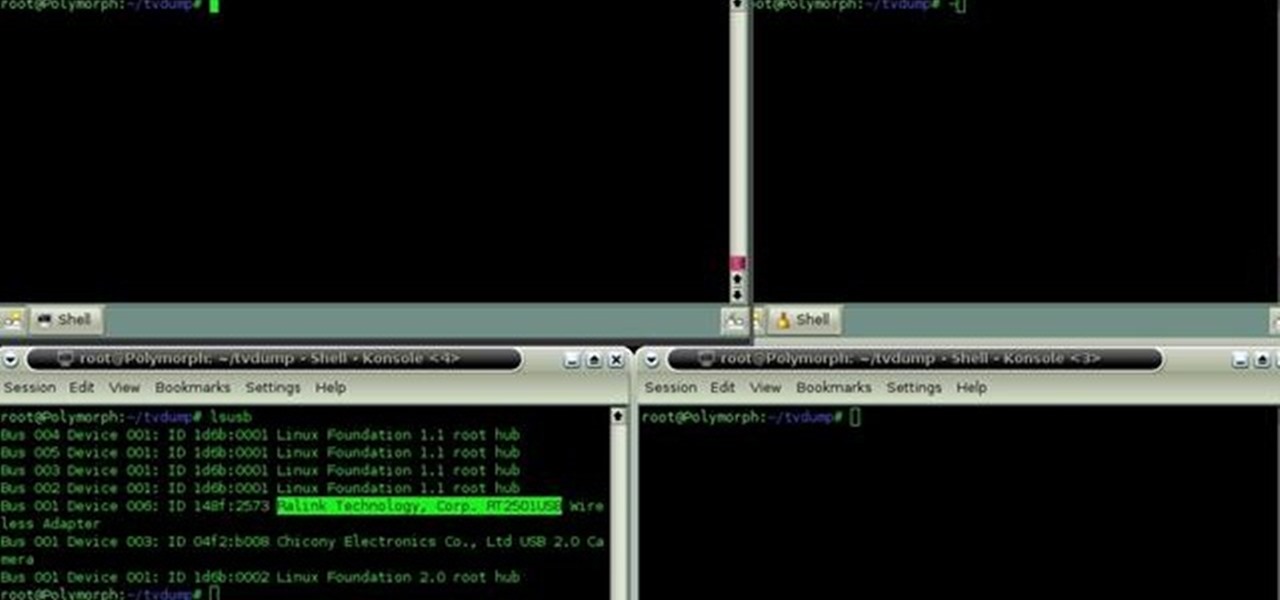
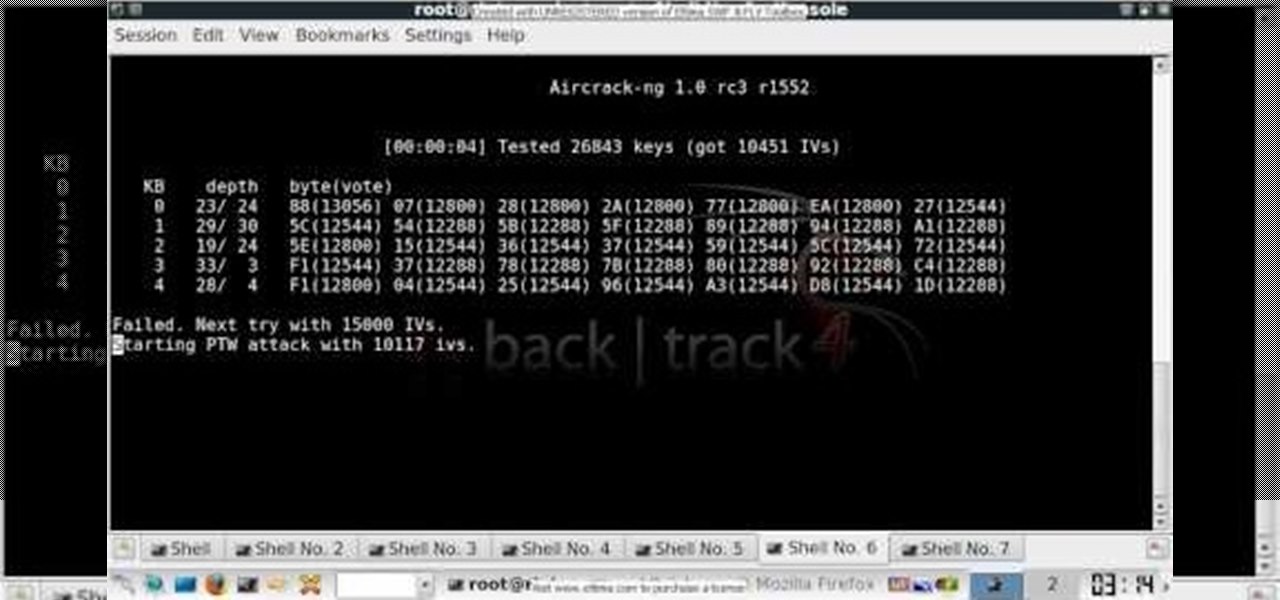
Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

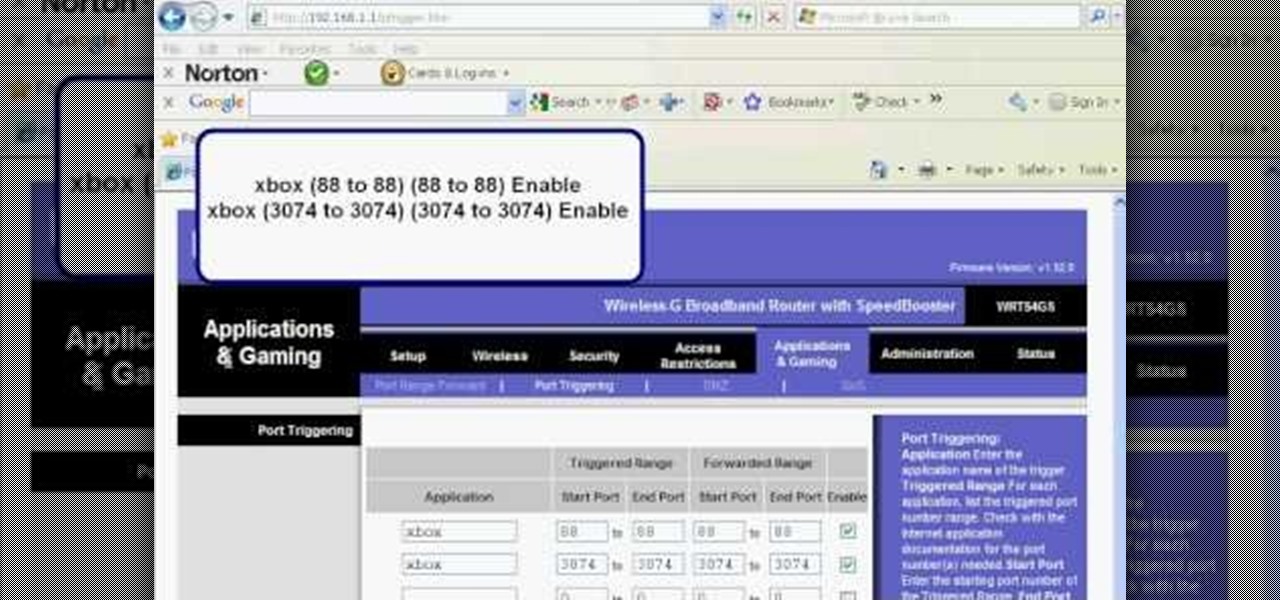
Before you can use Xbox Live 360, you'll have to allow your console to use certain ports that, by default, it may be blocked from using. One way to open up those ports is with port triggering. This helpful home networking how-to will walk you through the process of getting triggering set up in your own wireless router.

Overcome hardware differences in just a few simple steps- share files between your mac and PC and make your network truly seamless.

Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

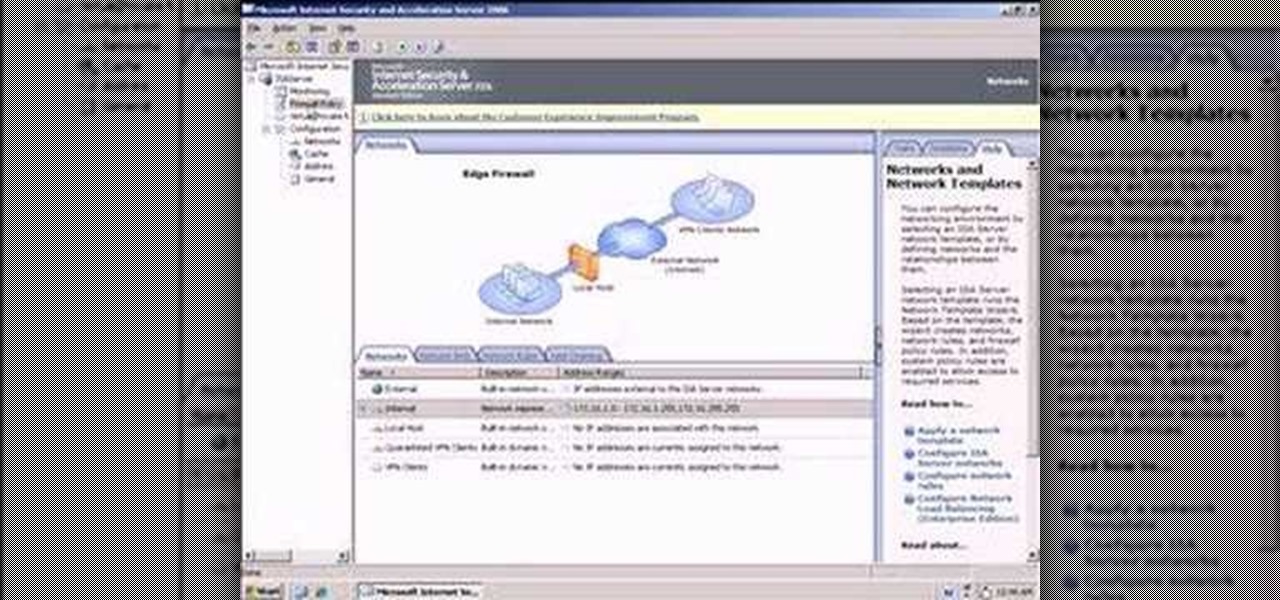
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

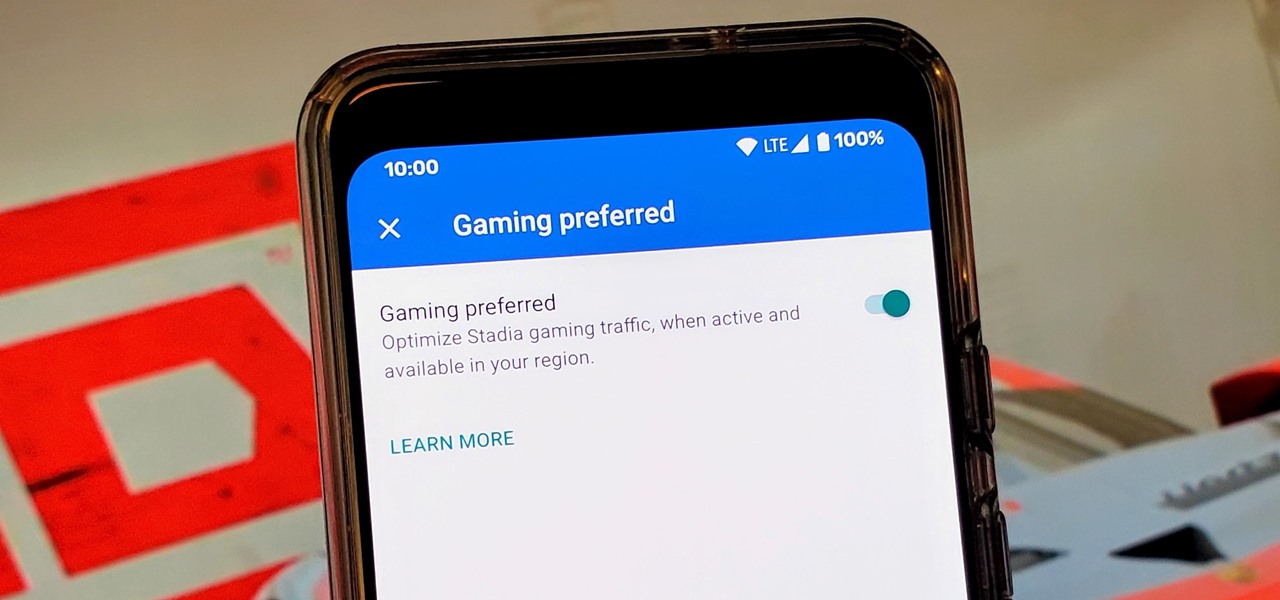
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

To punch up the launch of its new podcast, USA Today has created an augmented reality experience to introduce listeners to the story of corruption in Chicago.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

It turns out that the new Galaxy Samsung S8 Active (codenamed Cruiser) will be headed for AT&T in the US later this year, just like previous Active models. SamMobile revealed that the device would be exclusive to the network with a model number SM-G892A.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

You can find hundreds, if not thousands, of complaints about Wi-Fi performance issues with iOS 8 across all Apple devices. Even I had the issue on my iPhone 5S. The Wi-Fi connection on my router was strong, but I was getting extremely slow speeds. So slow, that I would resort to using LTE instead of Wi-Fi, which in turn led to going over my monthly data allotment.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."