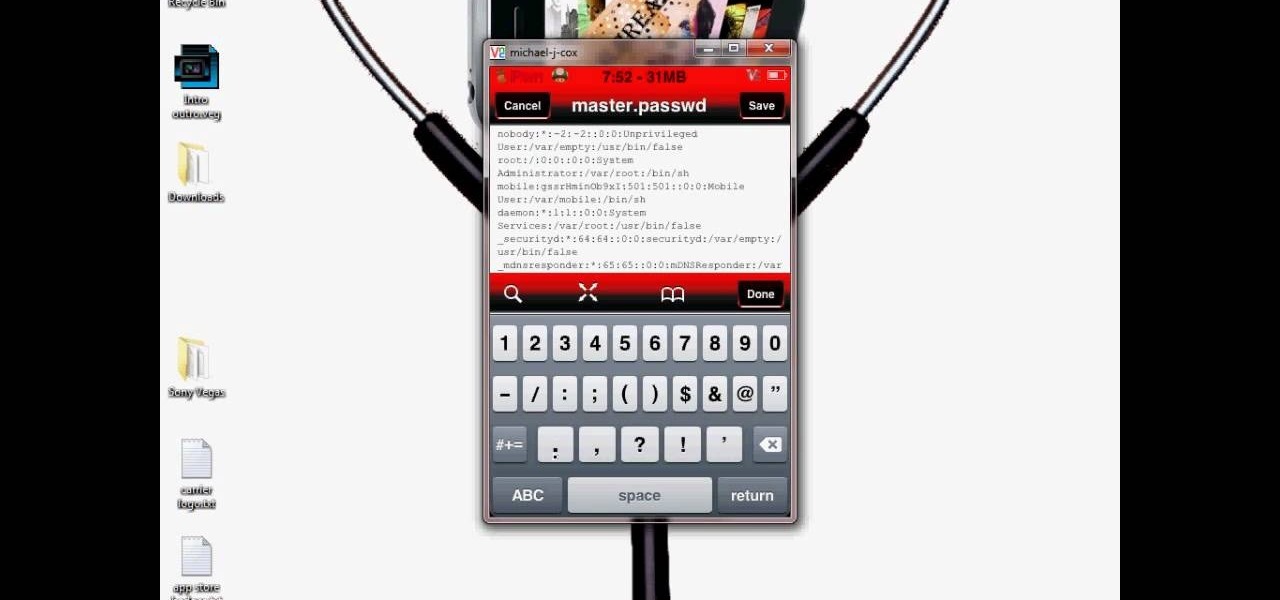
This video tutorial from DrJailbreak shows how to reset your SSH password on iPhone or iPod.If you changed your password through Rock with your Mobile Terminal and forgot it, this is what you are going to do to set your root and mobile password back to alpine.First you will need iFile application. Open Cydia and browse to http://repo.beyouriPhone.com. Navigate to Be Your iPhone Repo and scroll down to iFile. Download and install.Open iFile and navigate to /Private/etc.Scroll down and open mas...
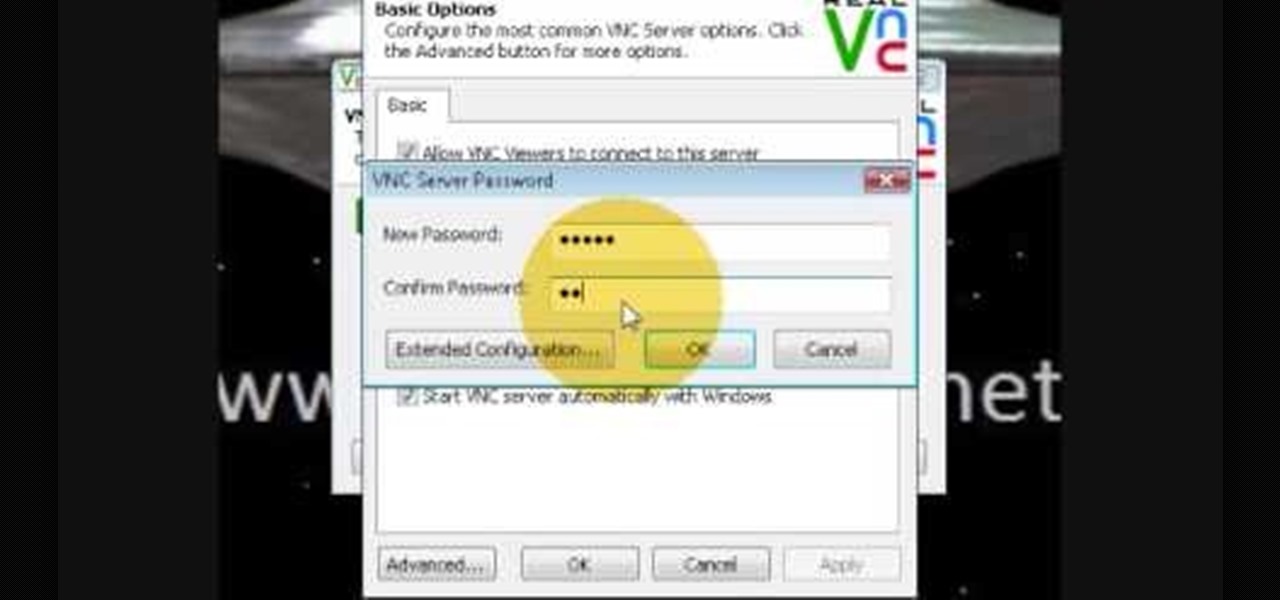
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

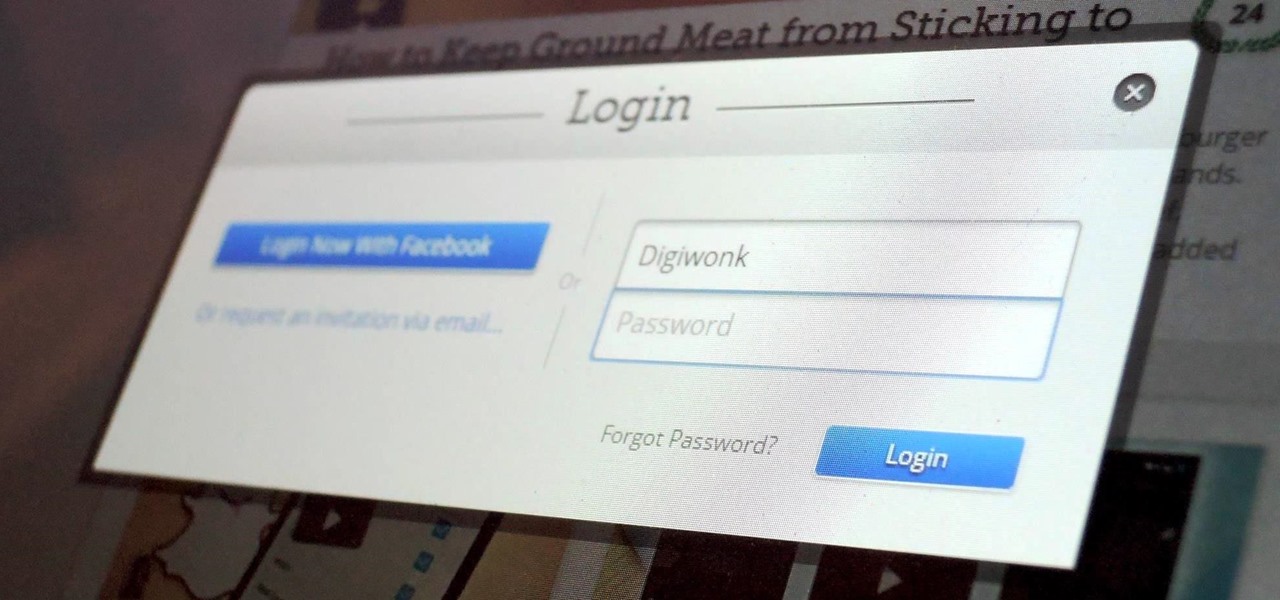
The Google mail service can be quite confusing in the beginning. If it is your first time using it, you may be having a hard time trying to find where to change your password. This video tutorial will show you exactly what to do in this situation. Just follow the steps and you'll be able to change your password without any hassle.

This video will allow you to view your saved usernames and passwords in Firefox. This may be useful for users in case you forget what your user names or passwords are for different sites and would like an easy way to find them. Under the Firefox toolbar, go to "Tools" and then "Options" in order to get a popup which will allow you to view different aspects you can change in Firefox. Go to the security tab and then click on the button which says "Saved Passwords" in order to view all your save...
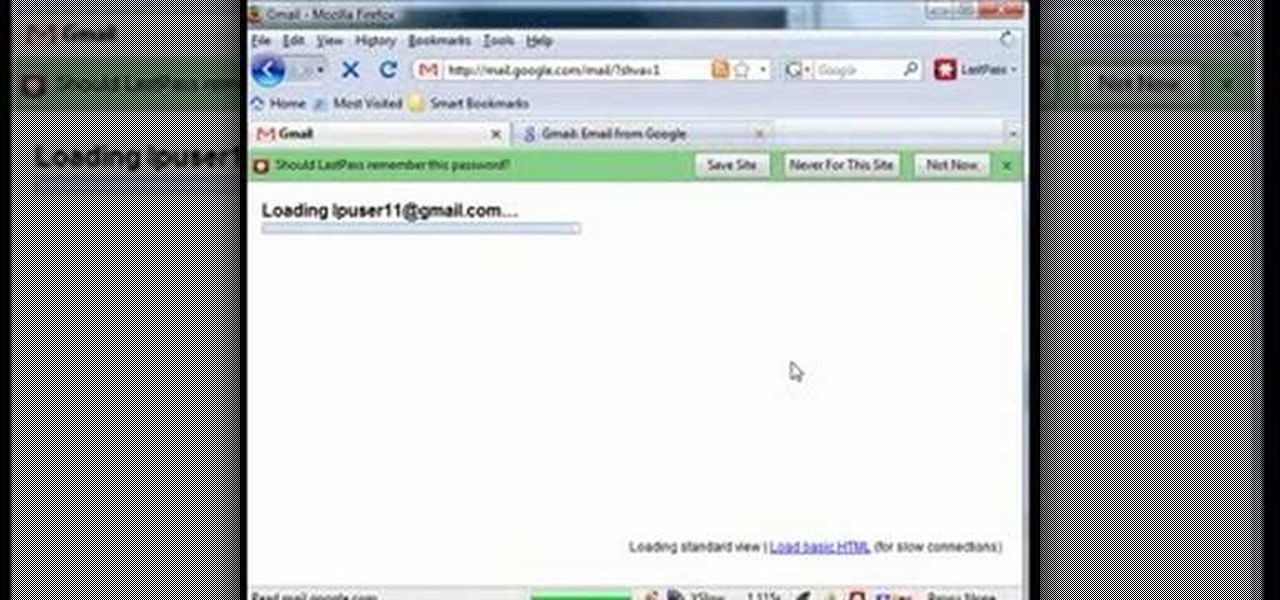
LastPass is a free password manager and form filler that makes your web browsing easier and more secure. This video tutorial presents a basic introduction, demonstrating the basics of using the LastPass Password Manager. Learn how to use LastPass with this how-to.
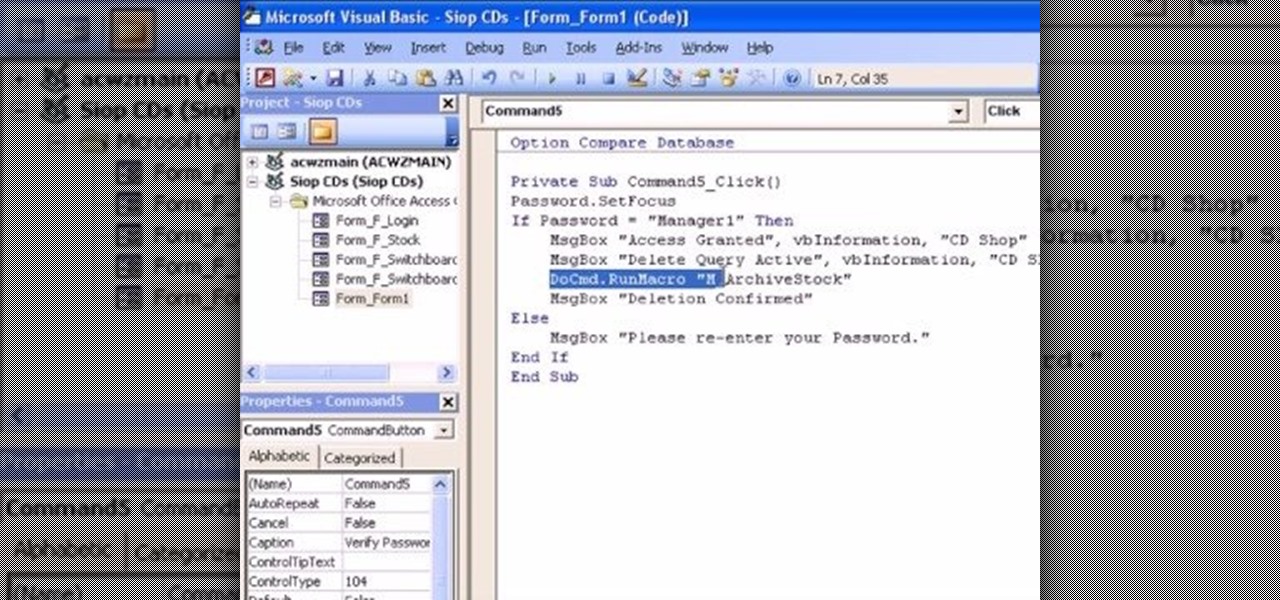
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

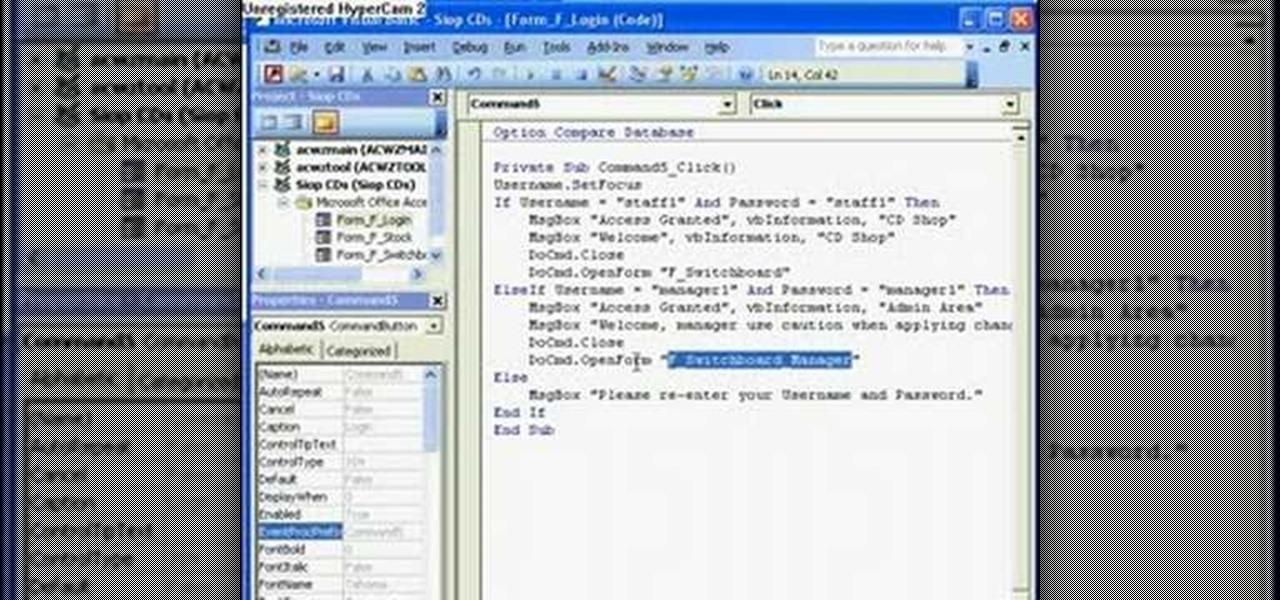
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a multi-user login form to password protect different areas of your database.

From email to online banking, you never want someone poking around in your personal information. Learn what to avoid when creating passwords, and try these tips to keep your passwords safe and secure.

This is hardcore, serious hacking at its best. So it goes without saying that you probably shouldn't be attempting this computer hack unless you've successfully shut down your friend's computer at school using Command Prompt and sent out a fake virus to loved ones.

Locked yourself out of your Windows Professional system? No problem—this video tutorial will show you the steps required to change the administrator's password in Windows XP. You can actually change this password without knowledge of the original one. To get started, go to Start > Run… and type in mmc to open up the console window. Watch the video to figure out where to go from there.

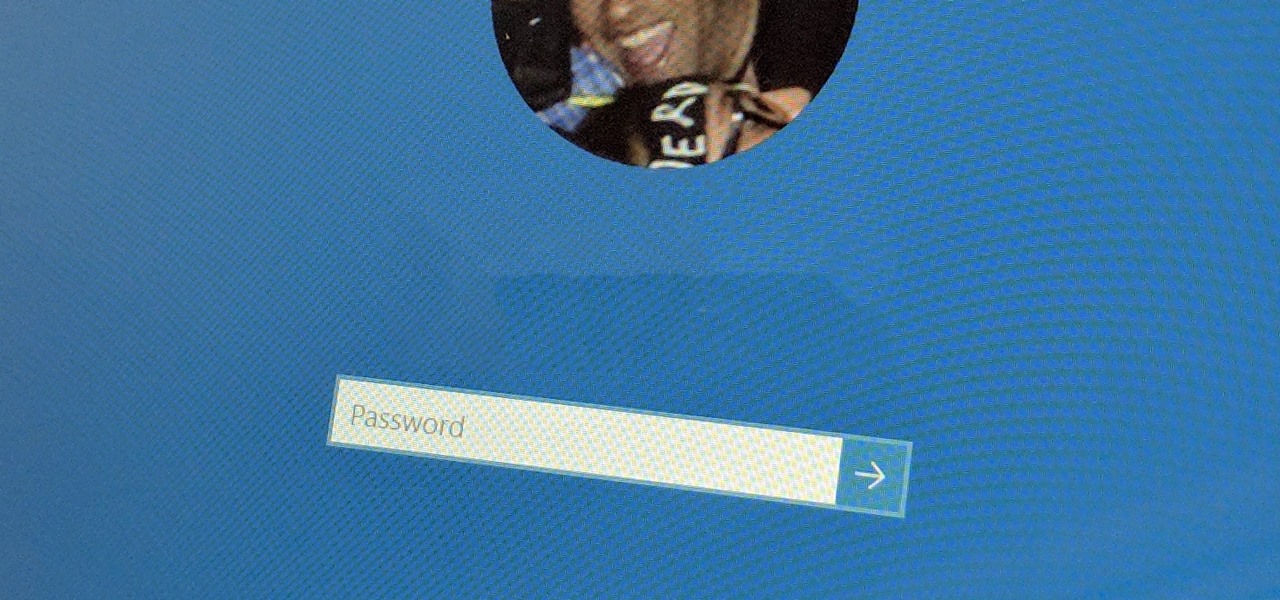
Have you lost the password to your Windows PC? Learn how to retrieve your Windows password with several different approaches.

In this video, we learn how to get into a password-protected Windows machine. First, you need to have this software onto your computer from http://www.piotrbania.com/all/kon-boot/. Once you have this, you will burn it onto a disk. When you forget your password, pop this disk into the drive on your computer. After this, boot it up and then reset your computer. After this, you will see a pop up appear on your computer and it will start to go through your computer to get the password. When it fi...

American Bartenders School shows you to make the Mai Tai cocktail drink recipe. Perfect if you love strong rum drinks.

Yoga is a lot more intense and difficult than those who have not done it before believe. Don't believe us? Whip out a sticky mat and try this five minute yoga flow for yourself to discover how much muscular intensity goes into flowing and holding each position.

Emma Watson, who plays Hermione Granger in the "Harry Potter" series, is actually a lot like the character she embodies. Both are quite intelligent (Watson just finished her freshman year at Brown), strong, and independent, and both rely on minimal makeup to enhance their features.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

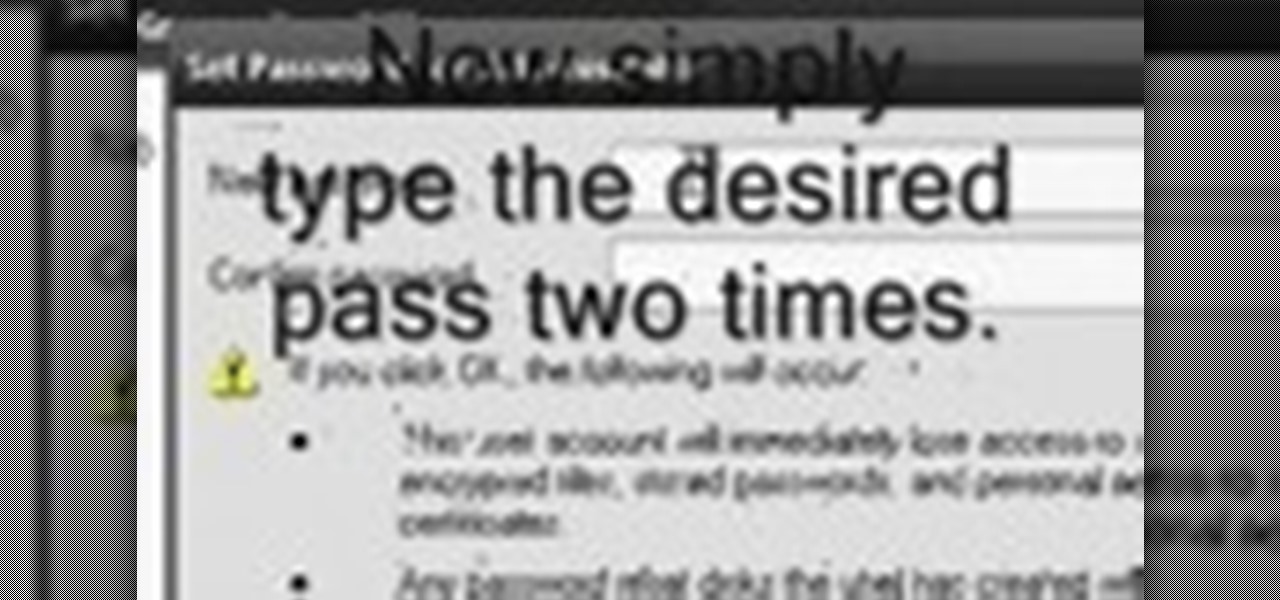
If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

After you have registered to this site,sign in then to start missions. Basic Missions

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.
I wrote this about two years ago to help people make realistic passwords. The best part was while writing it I realized I encrypted the list in a manner only the maker would know.... on to the show

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

Kipkay demonstrates how to extract the laser from a DVD burner and mount it in a small flashlight to create a handheld laser burner that can light matches and burst balloons, all in this how-to video. All you need is a 16x DVD burner, a laser housing, and a flashlight. Watch this video tutorial and learn how to modify a flashlight into a relatively strong laser.

Zombies are all the rage right now, inspiring TV shows, movies, video games, books, everything. Even Yu-Gi-Oh! decks. Watch this video for a guide to building a powerful zombie deck for Yu-Gi-Oh!, then go play some Plants vs. Zombies or watch The Walking Dead.

This bloke has very strong opinions about the different types of Elemental Hero (e-hero) decks in Yu-Gi-Oh! the card game. In this video he breaks down why his e-hero deck and e-hero philosophy in general are superior to others and why Elemental Recharge is a crappy card.

The winder is the ziptie-like cord that you pull through your Beyblade launcher to start your Beyblade spinning around the board. They often come bent into a near-circle when purchased, and this can cause your shots to lose power and even break your launcher. Watch this video for a quick guide to straightening your winder and keeping your Beyblade spinning strong.

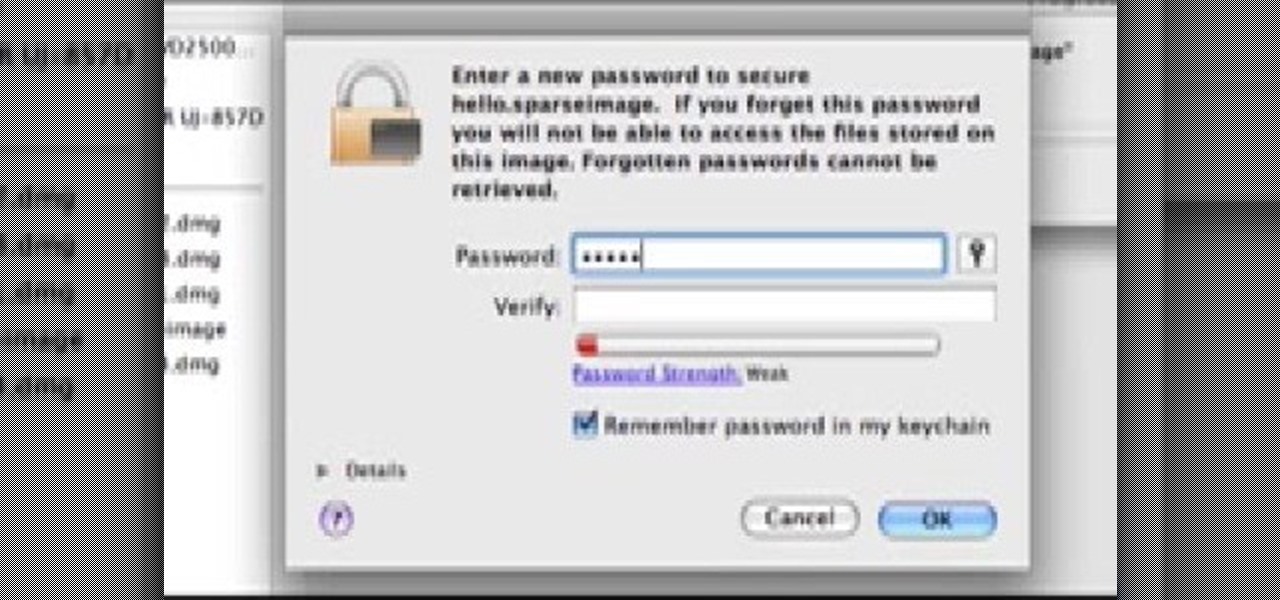
In this tutorial, we learn how to password protect your folders on a Mac computer. First, use the spotlight tool to type in "disk" and then click on disk utility on the drop down menu. From here, go to the save as menu and enter in the name for the volume. After this, change the size of the desktop and change the encryption choice. Use the one that is recommended and then click on 'ok'. Form here you will be asked for a password, then you will need to verify that password. From here, click on...