There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.

Apple Maps has had a rocky history since its introduction, which included limited features and questionable data, earning it a reputation as a lesser alternative to Google Maps. Since then, Apple has worked to close the gap, and in iOS 13, they're introducing Collections, which allow you to create groups of locations on your iPhone that you can then quickly access and share with others.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Now that the the iPhone 8 and iPhone 8 Plus have been revealed, we've been eager to see how the new devices will stack up against top-of-the-line Android phones like the Galaxy S8 and S8+. We can't compare real-world usage right now since the new iPhone models haven't been released yet, but we can see how they stack up on paper to get an idea of which one is the better buy.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

I've never met a person who doesn't love French fries. And, to be frank, I have no desire to meet such a person.

Ah, bello risotto. There are few comfort foods in the world that provide the same savory creaminess. Yet for all its simplicity, risotto has gotten a bad rap as a difficult dish to cook. In actuality, nothing is further from the truth.

It's an unspoken rule that diseases are not things that you want to purposely consume. So if anyone ever offers to cook you something made out of a disease, just kindly say no... unless it's huitlacoche.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

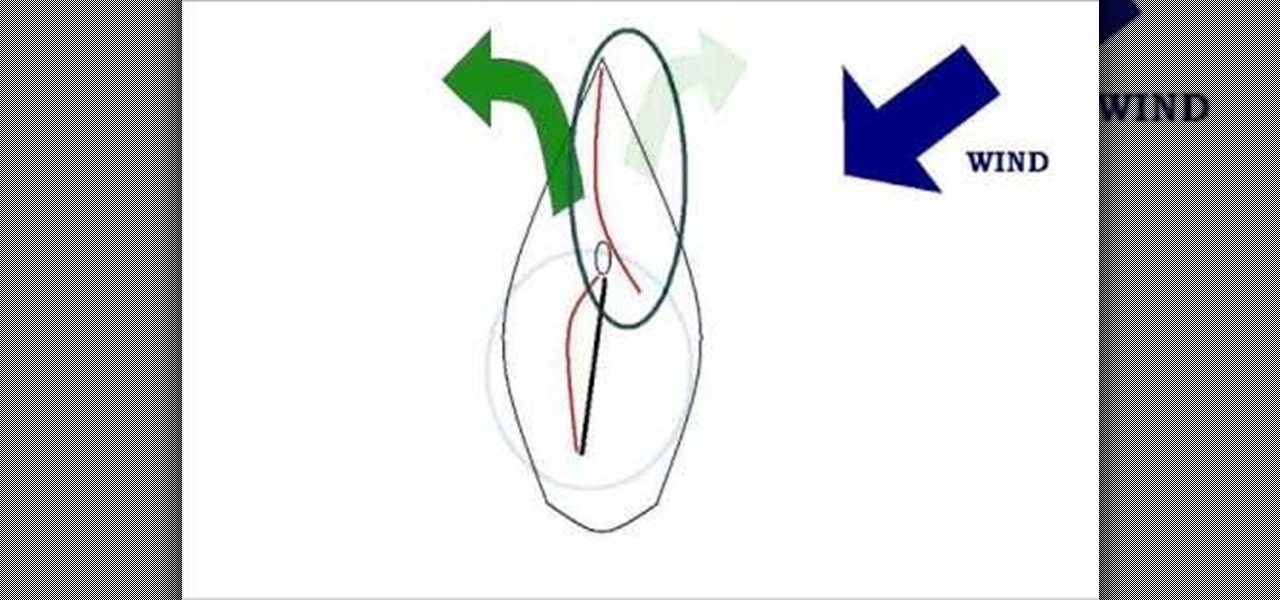
This video talks about the principles of heaving to, which is nothing more than stopping your boat in the water with the sails fully up, without making the boat create much forward motion. There are multiple reasons why you would want to heave to, and one is when the seas are getting rougher and the winds are becoming too strong to safely continue sailing. Watch to learn more about these situations and to see diagrams of everything.

This video tests the idea that an igloo, once left to freeze in the extreme cold, will be strong enough to stand on without collapsing. The experiment takes place in Minnesota where the temperature was fifteen degrees below zero at the start. Begin by shoveling snow into a dome-shaped pile. In the video, the dome is approximately six feet across at the base and three-and-a-half to four feet tall. Let the pile freeze for about two hours. The temperature had warmed up to about eleven degrees be...

How does one fertilize plants? Well, a fertilizer is a material that supplies the essential elements for plant growth. Most fertilizers are concerned with nitrogen, phosphorous and potassium. It isn't always easy to know which type of fertilizer to use. In this video tutorial, you'll find a guide to selecting the right fertilizer type for your application. Grow strong, healthy plants for a green garden with this how-to.

Sculpting hands in polymer clay can be difficult. Clays like Prosculpt and Sculpey can be brittle when used to make hands without armatures. A mix of Puppen Fimo, Cernit and Fimo Mix Quick has proved to be strong thus far. Watch this video sculpting tutorial and learn how to make hands out of polymer clay.

Tackling in field hockey is essential to having a strong defense, and there are subtleties that a defender must know when attempting to tackle without being penalized. Learn how to tackle in field hockey in this video tutorial.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

The field hockey forward is the chief scorer on the team, and must be fast, strong and accurate. Learn how to play forward in field hockey in this video tutorial.

Learn how to make focaccia bread. Ingredients are as followed: 1 x 7g sachet instant yeast (or 1 sachet dry yeast; 1 tsp sugar; 200ml tepid water); 350g (2 1/2 cups) strong white bread flour; 1/2 tsp salt; 2 tbsp olive oil.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Personification of the Infinite Consciousness. Lord of Hosts. Master of the Universe. These are just three of the hundred-odd titles of the Hindu god Ganesha. Luckily, drawing the Hindu deity Ganesha isn't so complicated.

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

In these rock and mountain climbing instructional videos, learn how to set anchors for lead and top rope climbing. Having strong anchor points is crucial to a safe and successful climb. Get professional tips and techniques on using strong rope knots to secure your climb. Learn how to rock climb with natural anchors like trees and boulders. Discover how to join anchors together for a more stable climb in unstable conditions. Watch this series and use these tricks on your next rock climbing trip.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

The Braun immersion blender is cheap yet powerful. It is strong enough to crush ice, frozen fruit, nuts, vegetables, etc. and is typically used to make smoothies. Watch this how to video to learn how to make an ice cream and banana smoothie with a hand held blender.

In Yoga Psychology, consciousness consists of body, mind, ego, intellect and self (the koshas). Rasas (emotional essences) are primarily a game of mind, but only become strong if the Ego identifies with them. Part of a Yoga class on Rasa Sadhana, the Tantric practice of emotional fasting.