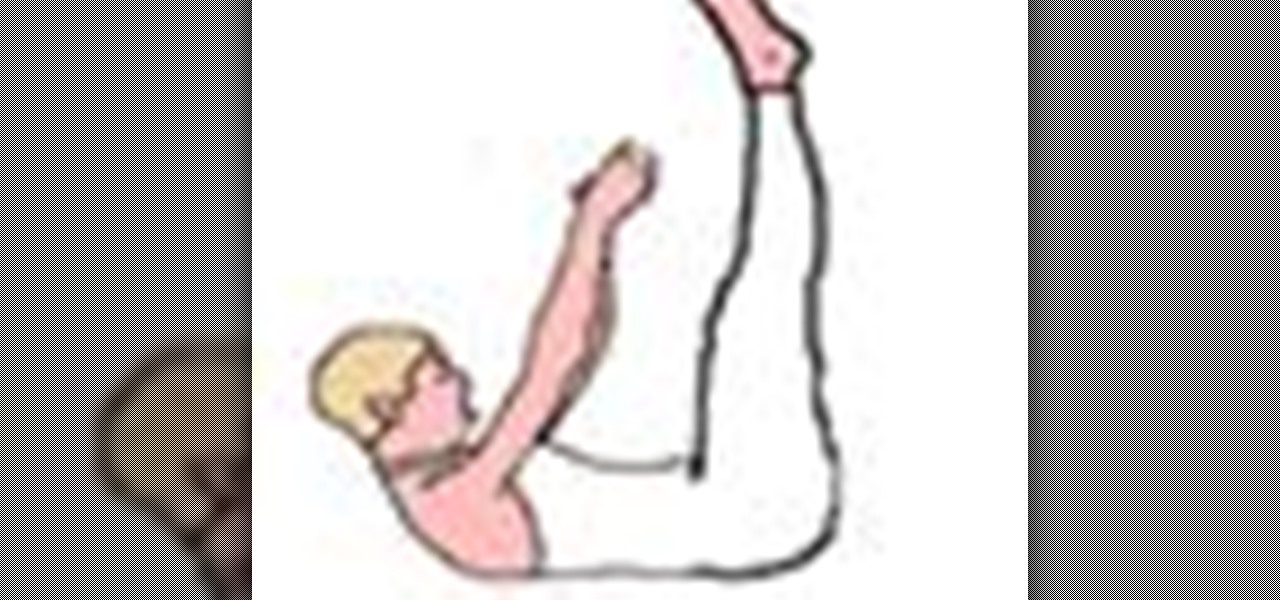
Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:
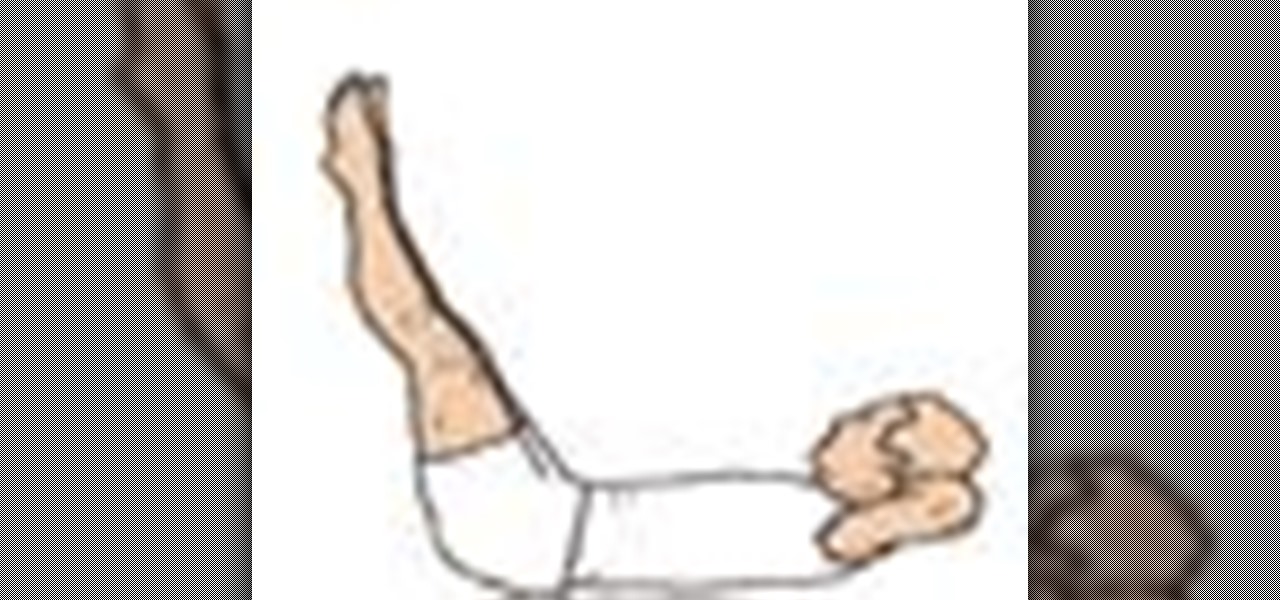
Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:
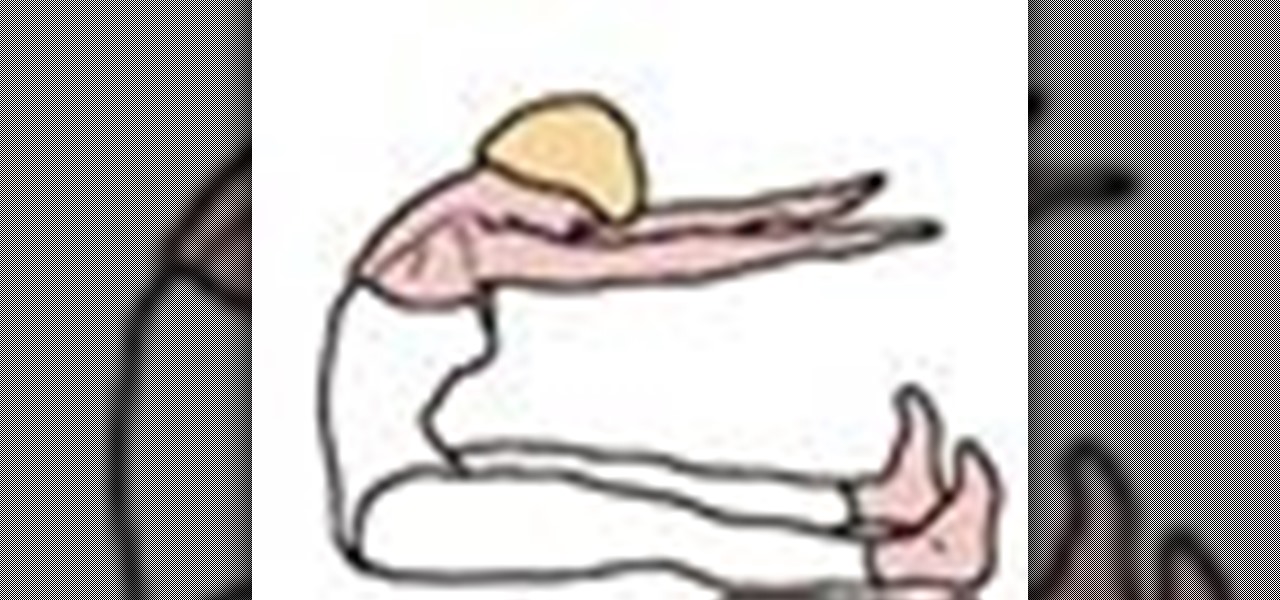
Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:
Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Did you ever think a question mark could turn into a cartoon? Well, grab your pen because Bruce Blitz is going to show you how you can create cartoons from symbols. This is an easy way to learn to draw cartoons. All you need is paper, pencil, markers, colored chalks or colored pencils, and an eraser. First, draw a question mark. Next, draw 2 C’s (one backwards) for eyes at the top point. The curve in the question mark will become a nose. Add 2 pupils and eyebrows facing up. Draw hair and an e...

Connecting a fragile tippet to the leader can be frustrating and time consuming. Dr. Mark Lamos has a quick method that delivers a connection as strong as a blood knot. With practice, you'll be able to make this connection in less than a minute. Tie a hemostat blood knot when fly fishing.

Chef David Ogonowski demonstrates how to make this delicious parfait made with the strong, rich flavor of espresso. Beat egg yolks and boil a sugar syrup; combine. They speed the cooling of the sugar syrup with an ice water bath. Make espresso parfait.

There’s a lot going on in your head when creating a comic book and it doesn’t stop after it’s done. There are other things that you have to do once your comic book goes online. You have to market it, introduce it to the right market, and find a way how to get it published.

Are you ready to learn a magic trick that is sure to amaze your friends and family? Ryan Oakes is going to show you how to pass ropes right through your body. You will need two pieces of rope, about four feet long each, a pair of scissors, and white thread.

The way you place your hands on the golf club will have a direct relationship to the flight of your ball, as demonstrated in this how-to video. If your grip is too weak, the clubface angle at impact will be off line, which will cause the ball to curve. The bottom edge of the clubface needs to be straight to the target line in order for the ball to fly straight toward the target. A good golf grip would be considered neutral, that is, neither weak nor strong. A neutral grip will allow your hand...
It’s hard to know where to start talking about a book like 2666. That’s partly because, in some ways, it’s actually five books. Published posthumously, the book begins with “A Note from the Author’s Heirs” explaining that, before his death, Bolano stipulated the book be published as five separate works. Instead, his friends and family opted to publish Bolano’s novel as he originally would have – as one single volume divided into five parts. Ultimately the five parts belong together. They shar...

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

In my opinion, Isaac Newton is definitely the number two astronomer, right below Galileo Galilei. His discoveries were very important to uncovering the secrets of space, and he deserves to be remembered.

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

Words that will help you with your writing Alliteration - The repetition of aconsonant sound. This si important because it makes words stand out, and because it can help set the mood for something.

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

After a stressful day, there's nothing more relaxing than a smooth glass of straight, room temperature whiskey to help unwind. On hot days, popping a few rocks in does the trick. And on cold days, hot toddies are truly amazing.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Visit the charming historical town of Quimper in Northwestern France. Enjoy ancient architecture, cobblestone streets, a stunning cathedral, and world-famous crepes..

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Kentucky Fried Chicken is one of those things that nearly everybody loves. But if your craving is strong and you want to make it yourself, think again – the Colonel’s not keen on parting with his top secret recipe. According to KFC’s official site, “one company blends a formulation that represents part of the recipe while another spice company blends the remainder. As a final safeguard, a computer processing system is used to standardize the blending of the products to ensure neither company ...

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...

What's the Difference Between Ales and Lagers People often ask me, "Nick, what is the difference between Ales and Lagers?" Well, as you may or may not know, there are two types of beers -Ales & Lagers. All beers are made from the basic combination of water, hops, malts, and yeast. However, Ales have been around for thousands of years longer than lagers. So, what makes lagers and ales unique? Here are a few steps to figure out the process:

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

When you look up the word free in the dictionary, you'll find a lot of definitions, but in the days of digital dependency and a falling economy, free only means one thing—expensive stuff for nothing. And if you own a Windows computer, one of the best sites to get free software from is Giveaway of the Day.

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

Any time a feature is introduced in an MTG set and not replicated in subsequent sets, balancing issues are surely forthcoming. You wind up with one set that can do things the others can't, forcing players to counter that set with other cards from it, and generally limiting the creativity with which one can effectively play the game. Playing these types of cards is like playing trap defense in hockey or boxing like Floyd Mayweather: you might win, but neither you, your opponents, nor the peopl...

GreenYou can tell a lot about a person's thought process by MTG color they favor: Red: aggressive, unsubtle, will surpass an obstacle by blowing it to bits with the largest explosives available (or Fireballs, as the case may be

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

Hello wizards! Welcome to The Wizard's Spiral! This new blog is about Wizard101. Feel free to post about anything in the Forums, ranging from equipment to Helephants, from castles to Mooshu. If you have any questions or technical problems, go to the forums and open a new thread. Me or any other wizard will be there right away to help you. For those of you who are wondering what Wizard101 is, you have come to the right place. Wizard101 is an MMORPG game that is all about wizards and magic. Whe...
Prop 25 prevents a suspension in CA’s budget. It means that legislators will not get paid if the budget is not passed on time. A budget will be passed with the vote of a small majority rather than two-thirds like it was before. However, a two-thirds vote is required to increase taxes.

I love broccoli. I love cake. I know zucchini bread is sweet and delicious, but savoury broccoli cake? I'll have to take Kitchenist's word for it and give this unusual recipe a try:

Yes, they are May numbers, NPD is late by a month due to "IT" problems. They might have well blamed it only oil spill crisis.

Thanks to Steam's Summer sale, we got to play Killing Floor over the weekend. It's a multi player survival game where up to six players roam around a map killing wave after wave of zombies.