Healthy, shiny hair is just an avocado away. In this tutorial, Roni Proter, host of Simply Beautiful, shows you how to make a conditioning hair mask using ingredients at home. All you need is some honey and a ripe avocado. Watch this how to video and you will have stronger, silkier hair in no time.

This yummy Japanese pound cake has a light consistency and a subtle green tea flavor. If you'd like a stronger tea taste, double the amount of powder required in this recipe.

An English teacher explains how to use "had better." This is an idiomatic modal which closely resembles "should," but it's a little stronger than "should."

Learn how to improve follow-through on your free throws with the help of this chair follow-through drill, aimed at making you stronger and improving your shot.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

In this tutorial, we learn how to make hydrochloric acid from salt. First, you will pour some salt into a distil flask. After this, you will add in some concentrated sulfuric acid to the salt. Next, you will let these react with each other. You will start to see gasses bubble up and the excess hydrogen chloride gas come out through the top of the tube. To create a stronger reaction, you can add heat underneath the reaction. Then, test this by exposing it to ammonium chloride. If it's the righ...

This video workout is aimed at skinny guys who want to get ripped. Some tips for weight training are to train less than 45 minutes at a time, focus on compound movements, try to get 5% stronger every two weeks, don't do more than one or two forced reps, and split your workout into 3 days for various body parts. To gain muscle mass, eat about 15 times your current body weight in calories, including 1-1.5 grams of protein per pound. Eat twice as many carbs as protein, high quality fats, and nut...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

The third trimester is here! Pregnancy weeks 29 to 32 may bring heartburn, Braxton-Hicks contractions, and the return of morning sickness. Your baby now has all 5 senses, and each baby kick is stronger than the last one. Watch to learn about month 8!

This tutorial teaches you how to warm up your cello playing for an audition. By working the "pulling" muscles of your left hand you will create stronger more precise fingers, like "core training" for your hand. When you add these variations you will wake up and warm up your brain, open up new connections by challenging the coordination between your left and right hands. Watch this how to video and you will improve your cello playing with these warm up exercises.

It seems impossible. Ripping one piece of paper is effortless. Ripping a small stack of papers takes a little force. But ripping a book? No way! Actually, it can be done, but only with a telephone book. This tutorial will show you how to rip a phonebook in half, quickly and easily. This is a great trick to perform at parties to impress your friends.

Tacking is an important part of windsurfing and, of course, it's best to start learning when there are light winds. Usually, at this level, most time is devoted to the gybe move, and the carve tack is a variation of this, a transition that you need and will give you the confidence to get on smaller boards and go out in stronger winds. When done well, the tack can also look impressive. Watch Sam Ross teach you how.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

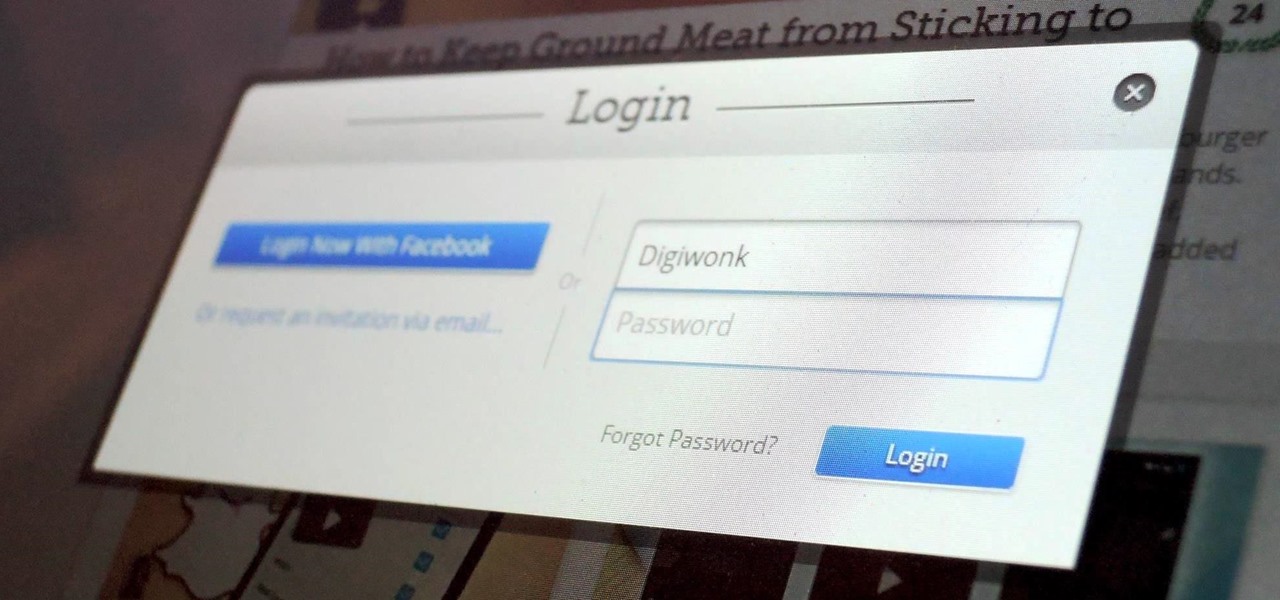
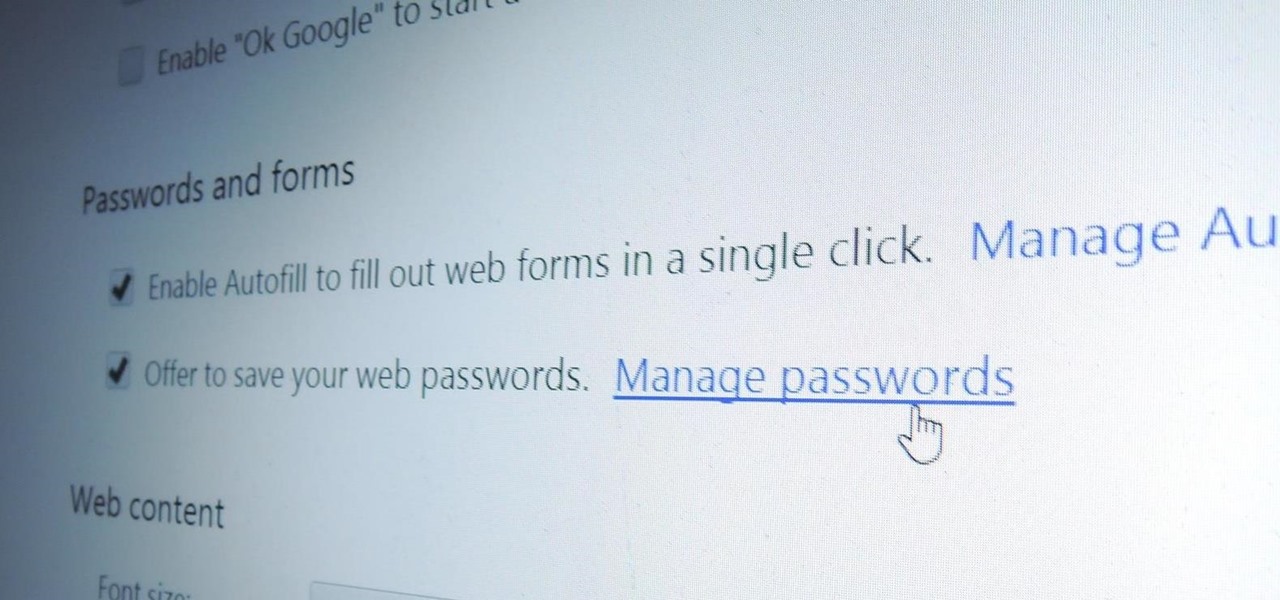
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

Back in 2007, YouTube user HouseholdHacker posted a parody video on how to make a high-def speaker for under a buck. MythBusters took on the challenge and busted it.

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

Learn how to draw Alucard (Adrian Farenheights Tepes link text the easy way. Adrian had special powers, preordained to be stronger than any human but not potentially as strong as his father especially in the dark arts. For the full tutorial with step by step & speed control visit: how to draw.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

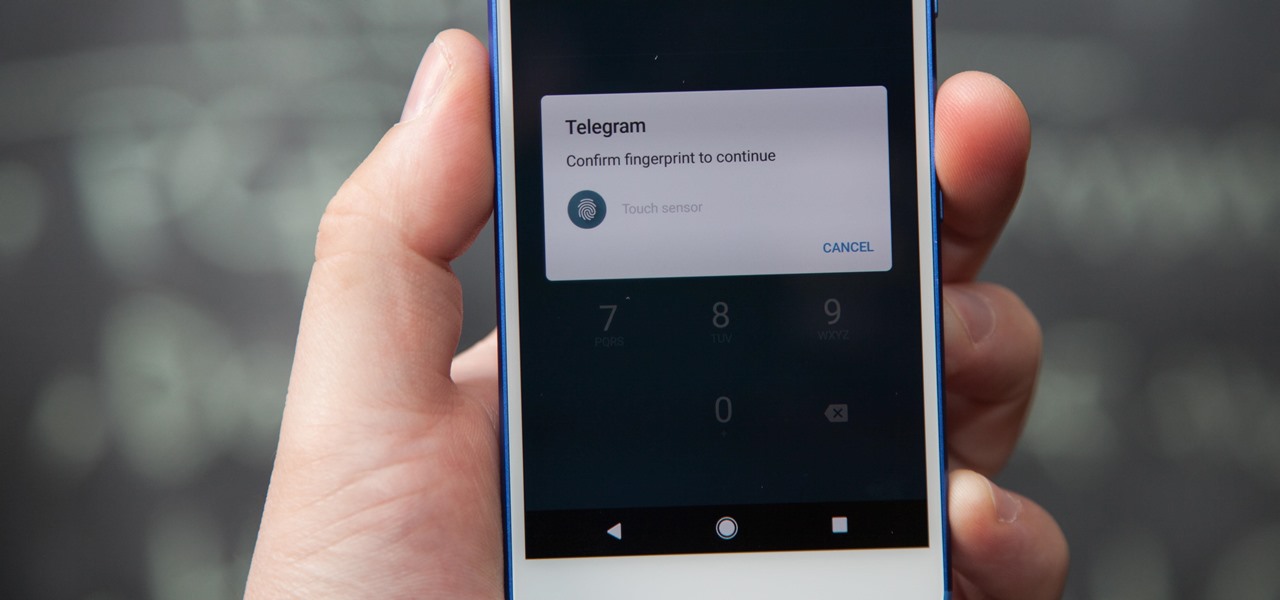
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Ramen has always been a go-to meal for frugal foodies, college students, and anyone else who loves a soothing, cheap, and easy meal. And while instant ramen is delicious (and can easily be improved), making a simple homemade ramen is even better, and nearly as easy.

Everyone benefits from positive coping strategies when dealing with divorce – learn how. Step 1: Stay in touch with both parents

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Today I decided to try out a cool new DIY craft! But seriously, Superwowstyle and DIY crafts! Did you expect? Nah! Neither did I! But these bling shoes were a DIY fashion that I simply could not resist when I realized what potential these old shoes have. the shoes decoration just had to happen once the idea hit my head!

When you're trapped at your desk before a jumble of data just waiting to be categorized, or zoning out during an important meeting, your mind wanders and, chances are, you feel a little guilty because of it. Yet you shouldn't try to reign in that distracted thinking. Instead, let your brain get distracted, and you'll unconsciously strengthen your memory.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

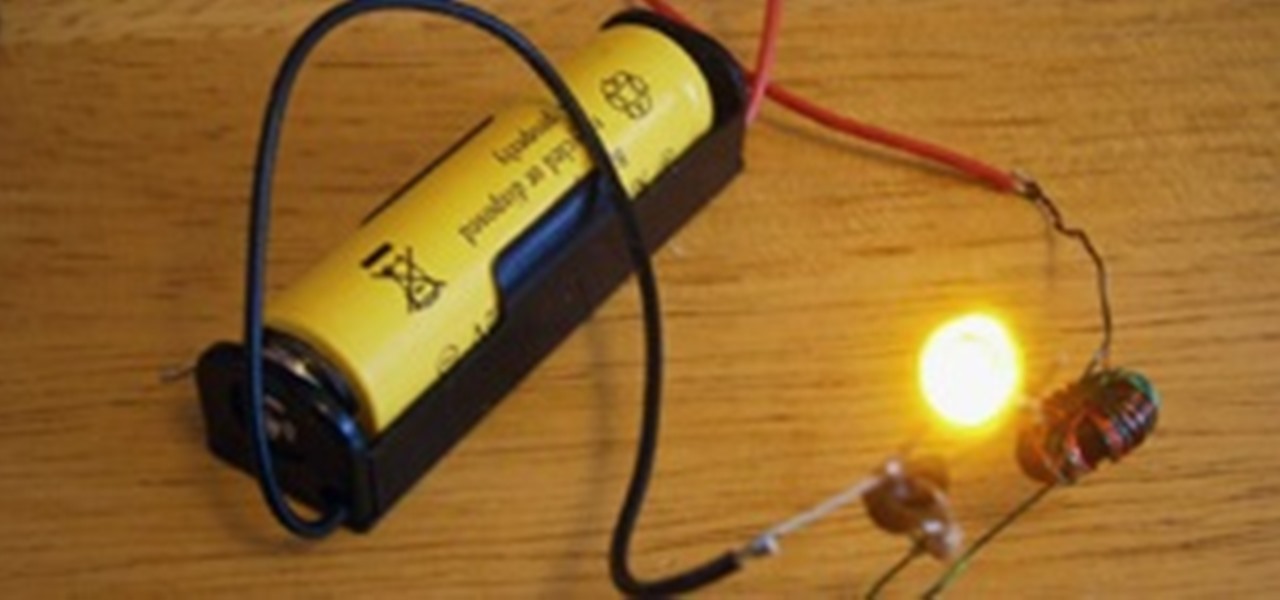
Just about every household gadget we own runs on 1.5 volt batteries of one size or another. Wouldn't it be great if you could reuse all of those dead AA, AAA, and D batteries after they've passed on? It turns out you can make a simple circuit called a "Joule Thief" to reanimate the undead flesh of your deceased batteries and create a zombie battery.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

Welcome to Minecraft World! Check out our full tutorials and make sure to post to the community forum if you have any questions or cool builds you want to share.

Postural problems can lead to all sorts of problems, from back, hip, and neck pain to heartburn and digestive issues. Over time, balance problems, insomnia, fatigue, and even jaw misalignment can emerge. How you carry yourself matters.