
Coding with Typo: Structured Query Language (SQL) Part 1: What Is SQL?
Welcome to the first coding tutorial on SQL here on Null Byte. Typo:


Welcome to the first coding tutorial on SQL here on Null Byte. Typo:


Each paragraph should be roughly 4 sentences long. The first sentence is an introduction, and then you can follow up with detailed sentences. The last sentence is your conclusion. An essay follows this same makeup. The first paragraph is an introduction, and then you have detailed paragraphs, followed by a conclusion paragraph. Each sentence in your introductory paragraph can be the introductory sentence for each of your detailed paragraphs. Likewise, the conclusion sentence in your introduct...

Basically, I have been pondering this a bit. First Off:

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.
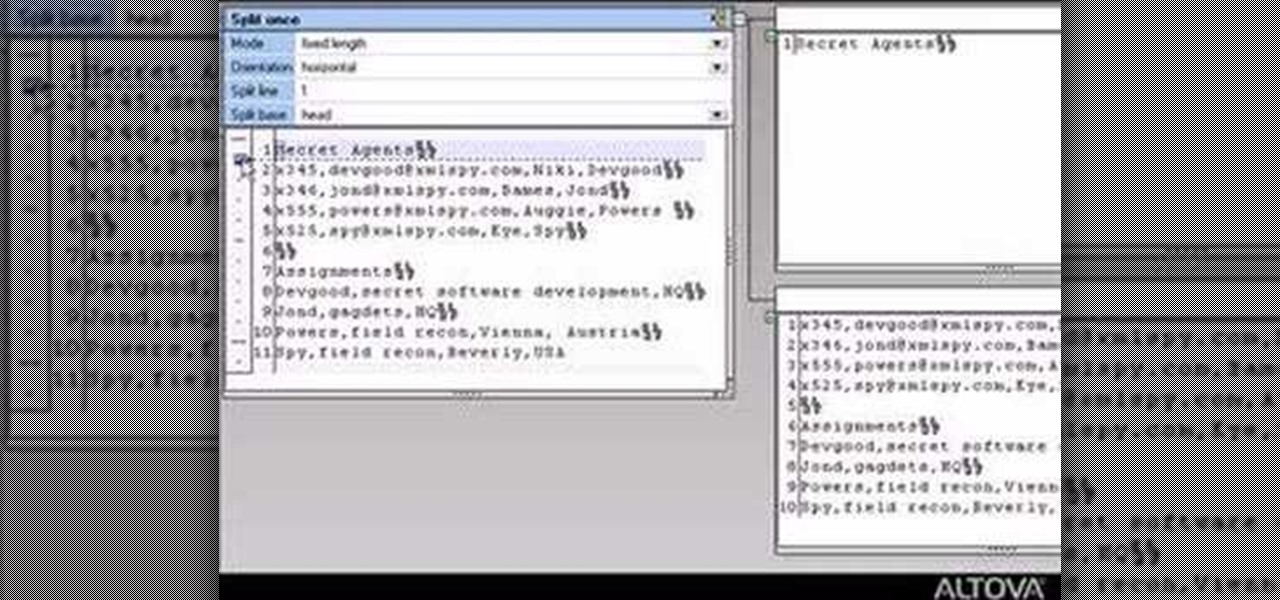
Learn how to use MapForce FlexText to analyze and parse arbitrary text files using an intuitive visual interface in this video. The resulting structured data can be used in any MapForce data mapping.

Now that you've got your tulip flower cookie pops baked and decorated, how are you going to package them? As individual gifts, they're convenient for slipping into small cellophane bags, tied up with a twisty tie, and sent to friends. But if you want to create an extra special treat for an upcoming birthday or celebration, check out this video.

This video is part of an instructional series on salsa dancing. In this particular video, instructors Anthony Persaud and Julie Merrill indicate the proper way to execute windmill dance moves in salsa. These moves involve structured turning, with or without a partner. The arm is raised up and outward, turning in a clockwise, then counterclockwise motion to facilitate turning from one way to the other. The name windmill refers to the way the arm turns to allow the move. Anthony provides instru...
This video is about how to dress to flatter your body type. Curvy body types look good with vertical stripes and clothing that accentuates the waist. High-waisted and belted bottoms and over-sized accessories work well for this body type. Pear body shapes look good in structured clothing. Form fitting tops work well with a smaller bust, making "pears" look slimmer. Cinching in the waist is also flattering for pear body shapes. For athletic body types look good in skinny jeans to show off thei...

In this video, we learn how to play "Lazy Eye" by Silversun Pickups on guitar. This is a riff based song, so you will need to learn how to use a lot of riffs to play it. First, play the open 11 and open 9 chords, which are going to be the most common in the entire song. The riffs are structured as two measures each with four beats. Each should be almost identical, so play it out to see if you have the sound correct while you are playing. Continue to play the song all the way through, keeping ...

Katy Perry doesn't leave the house without first filling in her eyebrows. Why? Well, other than curling your eyelashes, it's the one big - yet easy - thing you can do to instantly make yourself look more awake and youthful. Additionally, drawing in your brows makes your face look more structured as it adds face-framing and slimming lines.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.
MySQL is a structured query language (hence the 'sql'), and is an open source language published by Oracle. If you want to learn how to manipulate and use databases (such as customer lists or membership rosters), you will need to learn MySQL.

Learn to play one of Robert Johnson's best songs, "Kindhearted Woman Blues", on the guitar. This blues guitar songs from Johnson is a great song to start learning the blues, and is structured in a typical 12-bar blues in the key of A. "Kindhearted Woman Blues" was written in the late '20's, early '30's.
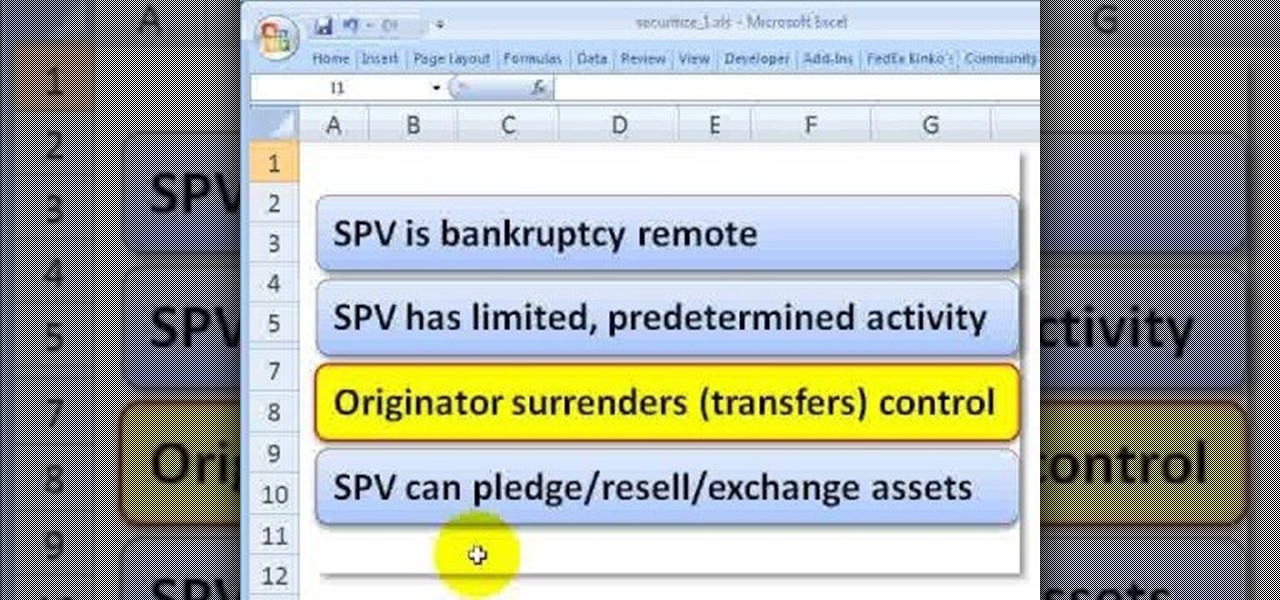
In this tutorial, we learn how to understand a securitization. This is a type of structured finance that has three key elements. the first is that there is a pooling of credit sensitive assets. In pooling the assets, you introduce diversification. The second element is to transfer credit risk to the third party and make rules around whether there has been a true transfer of credit risk. The third element in this is trenching of liabilities. This means when cash flows are transferred to a spec...

In this tutorial, we learn how to speak English with conditionals. Conditional statements need special attention and usually start with the word "if". An example of a conditional statement is "if you want, we'll go out to dinner". This has two parts, a condition, and a result. The condition is expressed by "if". To report them, don't change the verbs unless you're dealing with a real condition. Look and see if verb tenses can change depending on how the sentence is structured. Try to remember...
In this video tutorial, viewers learn how to prepare for the PSAT writing section. Avoid any long, wordy answer choices. Make sure that the answers are short and simple, and does not contain any redundancy. Read the sentences literally to check if the sentence is properly structured and makes sense. Review the grammar rules to ensure that you can understand sentence errors. Some grammar rules that should be reviewed include: pronoun reference, pronoun case, modifiers and parallelism. Not all ...

The Franklin Institute is rolling out the augmented reality carpet for the arrival of the Terracotta Warriors of the First Emperor exhibit, which will open on Sept. 30 in Philadelphia.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.

Two companies behind a number of augmented reality devices have joined forces to develop a 3D depth-sensing camera system that will facilitate computer vision capabilities for augmented/virtual reality experiences and more.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
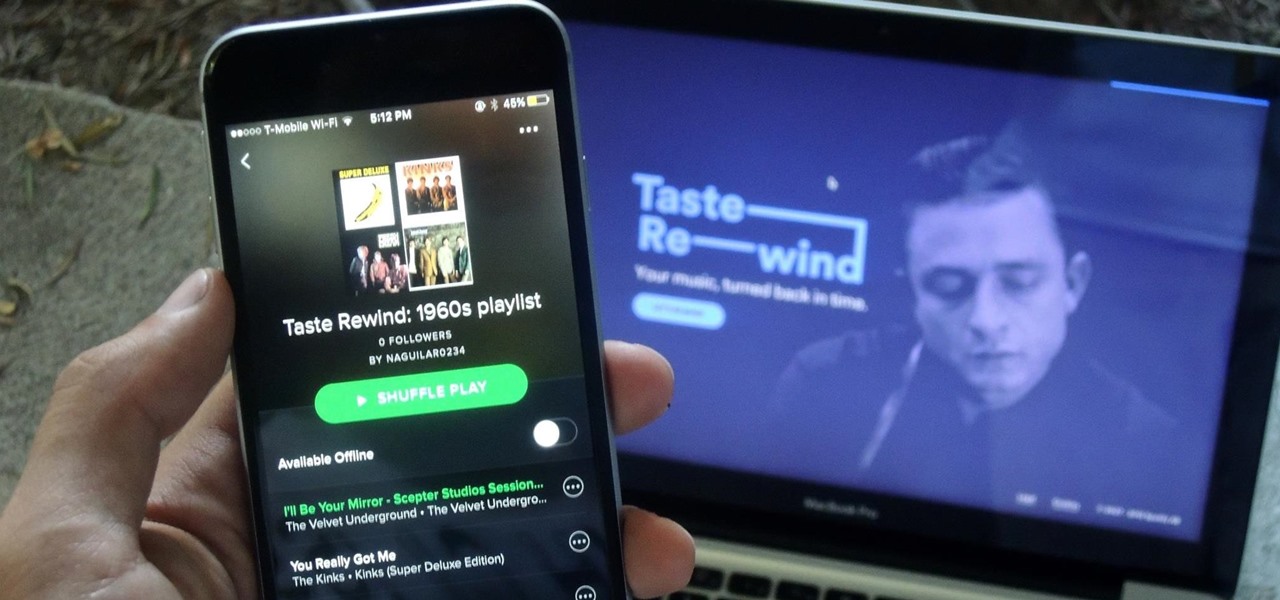
Spotify has a feature called Taste Rewind that claims to know what you would've listened to back in the '60s, '70s, '80s, '90s, and oughts ('00s), all based on your listening history and favorite artists. You can essentially time travel into the past and already have "favorites" songs to listen to! While I was skeptical at first, I tried the feature out for myself and was pleasantly surprised with the results. So if you want to create uniquely tailored playlists from the past five decades, st...

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.
Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

Ready to take the next step in your career and become an Amazon Web Services certified cloud practitioner in 2021? The complete AWS Certified Cloud Practitioner All In One Bundle is the easiest option to help you kill the exam — and right now, the entire bundle of courses is on sale with 91% off, for just $24.99 (regular price $300).

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

There's nothing worse than biting excitedly into your indulgent restaurant-style burger only to find a soggy mess of a bun on your plate. The conundrum of keeping a patty moist but bun dry has perplexed home cooks and chefs alike, and even top burger joints are guilty of soggy-bun syndrome.

Welcome back, my aspiring hackers!