
Hack Like a Pro: Networking Basics for the Aspiring Hacker, Part 2 (TCP/IP)
Welcome back, my greenhorn hackers!


Welcome back, my greenhorn hackers!

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

Hello NullByte! This will be my first How To series.

The stock Camera and Photos apps are great for taking basic pictures and doing some quick edits, but if you're serious about making your iPhone photos the best they can be, you can't stop there.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Bad news, guys. The shelf life for liquor leftovers does not apply to your two-buck chuck. While an opened bottle of your favorite whiskey will stay respectable for ages thanks to its high ABV (which makes it inhospitable to outside elements), an opened bottle of merlot will sour quickly. However, it turns out that red and white wines have different life spans once they're opened—for reasons which we'll cover below.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

We've all been there; waking up in the morning with a stiff, achy back. Maybe you overdid the yard work this weekend. Perhaps you were a bit too enthusiastic on the Nautilus circuit. Could be the long hours spent hunched over your computer are catching up with you. Perhaps your back pain is indicative of something more serious. Unfortunately, unless you've really injured your spine, your doctor isn't going to be much help; the best he can do is offer you pain medications and tell you to rest ...

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.
In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say.

This video demonstration series shows the process of creating an armature for stop motion animation, claymation specifically, out of aluminum foil and polymer clay. Armatures need to be flexible to withstand the positioning and repositioning required to make stop motion animation, but still secure enough so that the material won't break. For this reason, a tin foil skeleton provides a sound structure to the clay armature. Watch this video animation tutorial and learn how to sculpt an armature...

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.
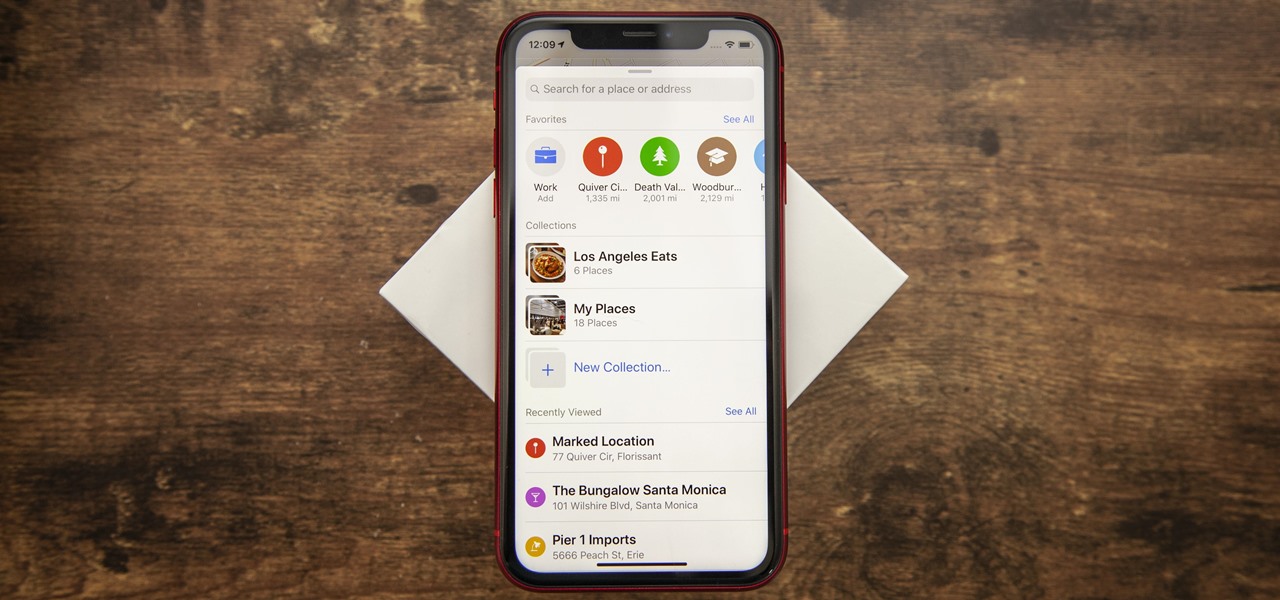
Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.