The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

Zently — the mobile app for renters — is taking on Venmo with its newest feature. Traditionally used to automate rent payments, deliver rent checks for free, and communicate with your landlord, it now allows you to connect to your bank account and split bills with housemates. Following the addition of Zelle to several major banks apps — to allow users to transfer money to their contacts — the battle of the mobile payment apps is getting increasingly fierce. With this new update, Zently is als...

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Do you know what your smartphone is made of? I've had smartphones for years, but if you asked me that question I'd probably respond with "Wi-Fi." For uninformed consumers like myself, it may shock you to know just how much goes into creating a smartphone.

The Augmented World Expo (AWE), the biggest event for augmented, virtual, and mixed reality companies, developers, customers, and connoisseurs, is happening right now. You know what that means for us here at Next Reality? Companies presenting and exhibiting at AWE are releasing news like crazy.

The driverless competition is heating up as Detroit automakers attempt to woo tech talent away from some of Silicon Valley's biggest players.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

There's a good chance that your iOS device has become unresponsive at least once. It's usually at this point that you start thinking your device can no longer pass muster. You could upgrade to a newer model, but that's not always feasible, and often times, unnecessary.

I'm no coupon-cutter (I just don't have the patience for it, sadly), but I do love buying things in bulk to save a buck or two. And one of the staples on my bulk-buy list is chicken; I cook with chicken so often that trying to save money on it is a no-brainer.

Lemons are often displayed as a bright and beautiful pop of color in many home kitchen displays. They lend a lovely scent to the air and an aesthetic sense of freshness to any setting. Therefore, it would be easy to assume that lemons are best left at room temperature.

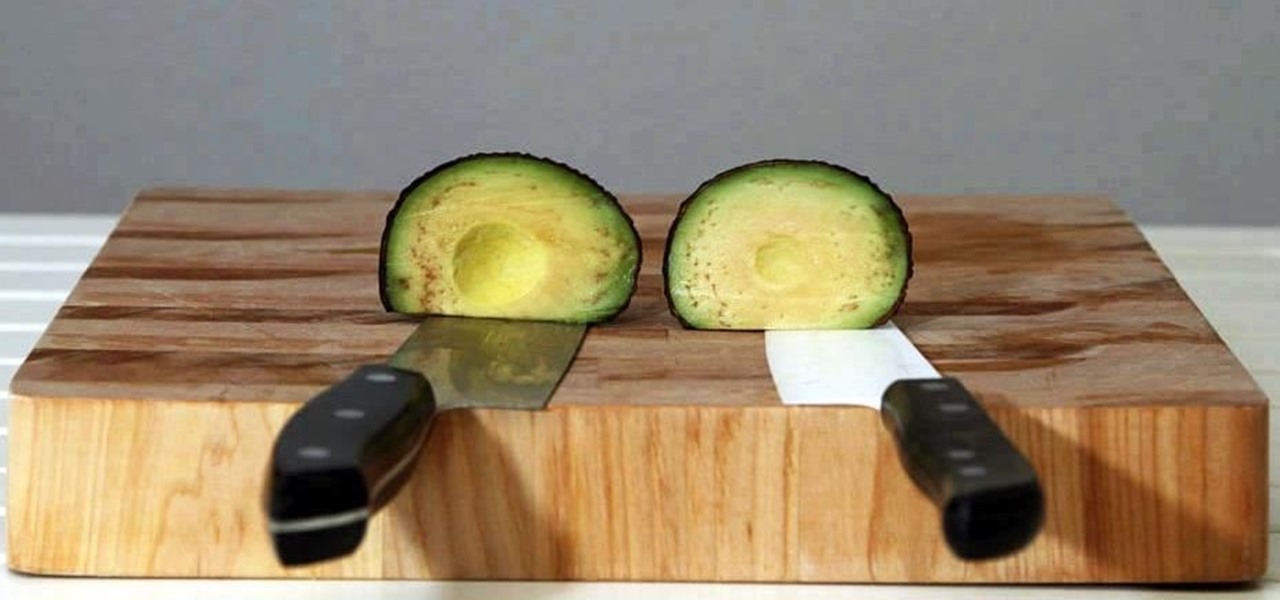
Keeping apples or avocados from browning after being cut is impossible; within minutes of being exposed to air, these fruits (yes, avocado is a fruit) begin to brown. No matter what you try—adding lemon juice, keeping the pits in place, immediately sealing the produce in an airtight bag—brown discoloration always occurs. However, air is not the only reason that foods like apples, avocados, and lettuce brown: it's also due to the knife you're using.

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

Welcome back, my hacker novitiates!

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the lavender lemonade.

I grew up eating Korean, Japanese, and Chinese food, but it wasn't until college that I experienced Thai and Vietnamese cooking. Once I started, I couldn't get enough of these cuisines. The dishes had an incredible richness and savor that I couldn't identify, but whatever it was, it made me want to keep eating.

I don't deep fry food that often, mostly because it uses a ton of oil, which is expensive, and the cleanup is a son of a mother. (That oil really splatters everywhere.) Plus, no matter how careful you are, you will get hit by hot oil at some point and it will not be pleasant.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.

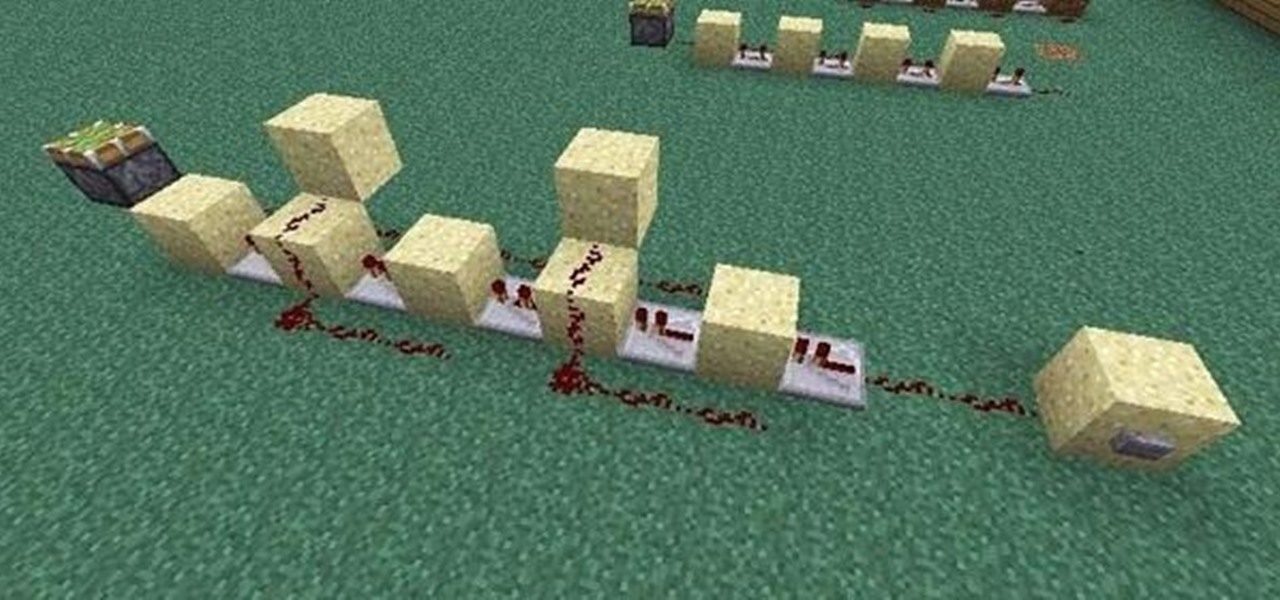
Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

In last Saturday's workshop, the tutorial was on the ABBA switch, so named because it fires redstone pulses in A-B-B-A order. While the turnout was low, it was a really productive workshop! We experimented with a lot of things and had a great time. Hopefully you'll consider joining us next time!

One of the hardest things a man can go through in life is a trip to the hospital, especially when he knows he's going to need a catheter. It's every man's worst fear. But for a nurse, it's necessary knowledge. Learning the male urinary catheterization procedure hands-on is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization technique of a male patient.

In many situations, learning proper medical procedures is difficult due to the urgency involved in patient care, so this video aims to prepare nurses so they can learn and stay fluent with the proper urinary catheterization of a female patient.

This is the ultimate guide to drawing correct human proportions. If you've always had trouble with it in high school art class or in art school, this video condenses all the information into a tight package that's fun and easy to understand. This will uncover all the tricks to human proportions for figure drawings.

Do you know what an idiom is? If you don't, this English lesson is sure to make you an expert on idiom usage.

Michelle Phan presents this tutorial on how to take a tomato and turn it into an invigorating scrub.

The key to getting good grades on your tests is being able to improve your study skills, including reading comprehension - the ability to understand what you've just read. Use these practices to improve your ability to read and comprehend your textbooks at a higher level.

When we're kids, learning a new language is easy, but that's not the case when we reach adulthood. For all the times you've struggled with rote practice from apps like Duolingo or wished you could take language courses without enrolling in an expensive university, now there is The Ultimate Language Learning at Home Bundle for Beginners.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

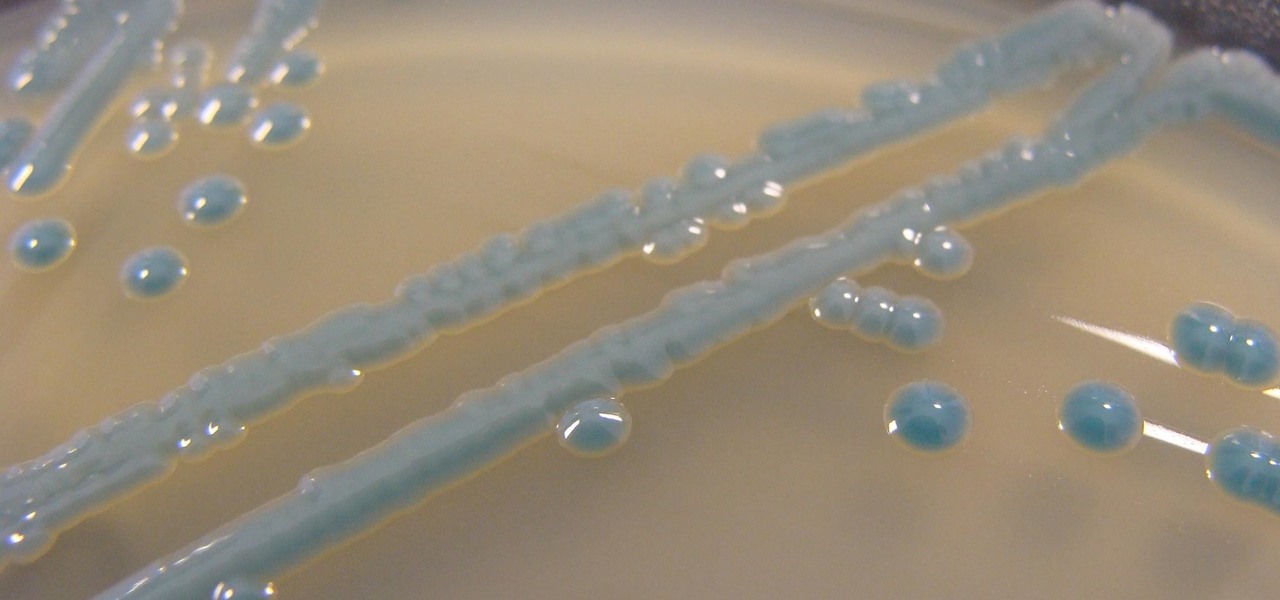
Not all bacteria in the eyes cause infection. A group of researchers from the National Eye Institue has shown that not only is there a population of bacteria on the eyes that reside there but they perform an important function. They help activate the immune system to get rid of bad, potentially infection-causing — pathogenic — bacteria there.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.