Video: . Extraterrestrial life is life that does not originate from Earth. It is also called alien life, or, if it is a sentient and/or relatively complex individual, an "extraterrestrial" or "alien" (or, to avoid confusion with the legal sense of "alien," a "space alien"). These as yet hypothetical forms of life range from simple bacteria-like organisms to beings far more complex than humans. The possibility that viruses might exist extraterrestrially has also been proposed.

If you watched a YouTube video on your Android device today, you may may noticed something just a little different. If you haven't, go check out the app in your drawer or homepage. Google today pushed out an update to their YouTube app, but by all accounts, it was never meant to hit the public. This is labeled a dogfood build, which is a term used to describe products going through in-house testing, in effect "eating their own dogfood".

Closing apps in iOS 6 was different that what is now in iOS 7. Shown in the video below is the old clumsy way of closing apps on the old iPads.

Via Twitter, HTC, the Taiwanese device manufacturer, announced today that their barely 18 month old flagship phones will not see official updates for anything past Jellybean. HTC went on to elaborate, saying:
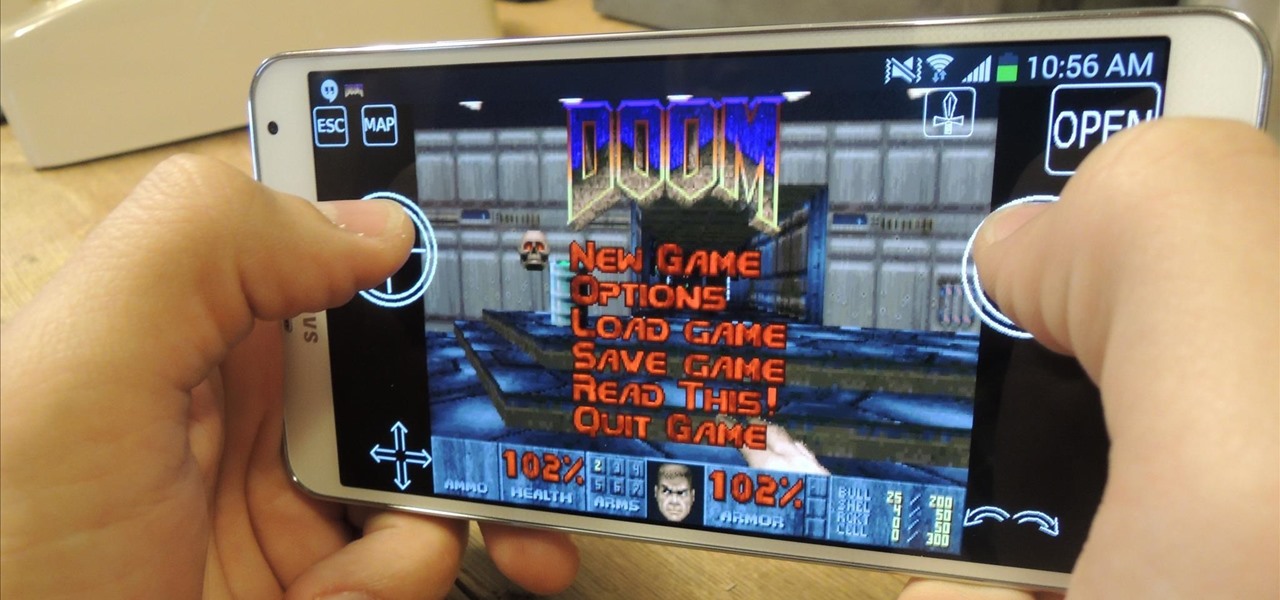
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

This is how to build a wine rack out of pallet wood. I was tossing around some wine rack ideas and decided that pallet wood, or reclaimed wood, is the perfect choice for a rustic wine rack. All you need for this project is an old pallet (for me a hardwood one is my choice). A pallet that has seen some wear is preferable so as to achieve that rustic look.

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

If you need a sturdy, super strong knot, but you want be able to reuse the rope, then the bowline knot is what you want. The bowline knot is one of the strongest knots available. It's a nonbinding knot which makes a nonslipping and nonjamming loop at the end of the rope. This is perfect for heavy equipment, and great for boats and other watercraft vehicles. The bowline can take as much weight as the rope can handle, and it can be untied!

In this video, 305 Nicky shows the viewers how to clean up a penny by using Tabasco sauce. You will need a piece of sturdy paper towel, Tabasco sauce, and an old penny. Next, fold the paper towel into fourths and put the penny on top of the paper towel. Open the Tabasco sauce and put 4 or 5 drops onto the dirty penny. Make sure the penny is evenly coated by spreading it with your index finger. Wait for about 10 to 20 minutes after applying the sauce and using the paper towel, beginning to rub...

Master your tennis serve: the kick serve. Be sure to click on all the video chapters to view the entire tutorial.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

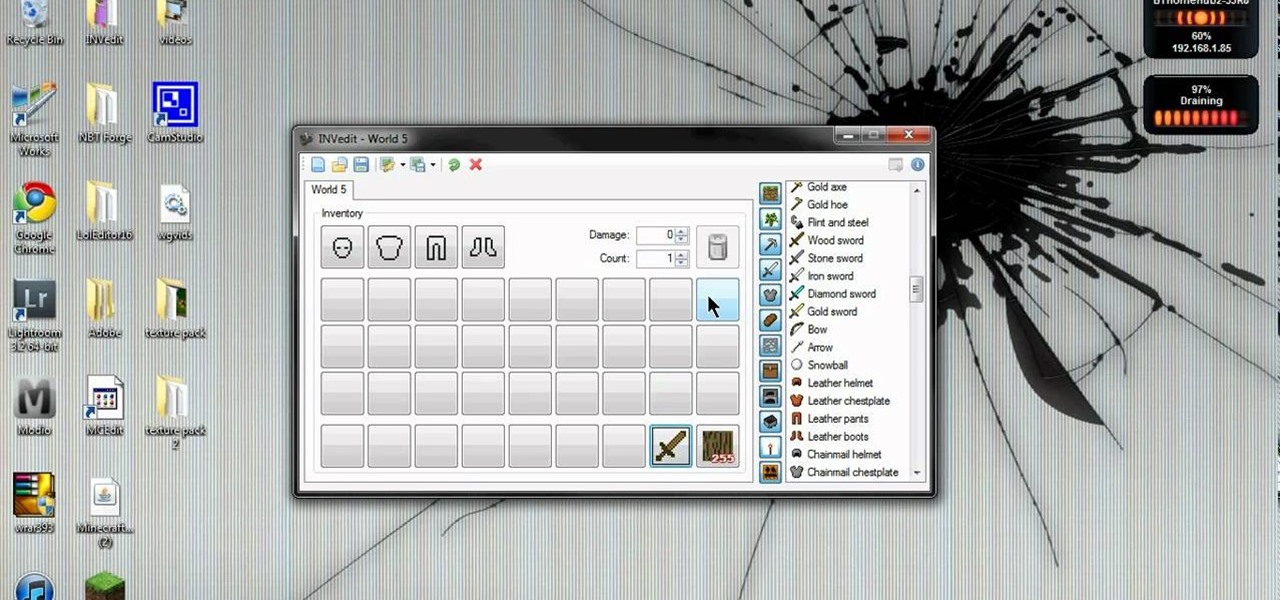
INVedit is an inventory modification program that you can use to hack into your character's inventory when playing Minecraft. Give yourself more items of one time, unlimited resources or whatever else you feel like. Fill a whole island with diamonds or TNT!

Start with just a little bit of money and the multiply it into a vast fortune! All you need is the most current version of the free game hacking software, Cheat Engine! Then open your game in Firefox and follow the tutorial!

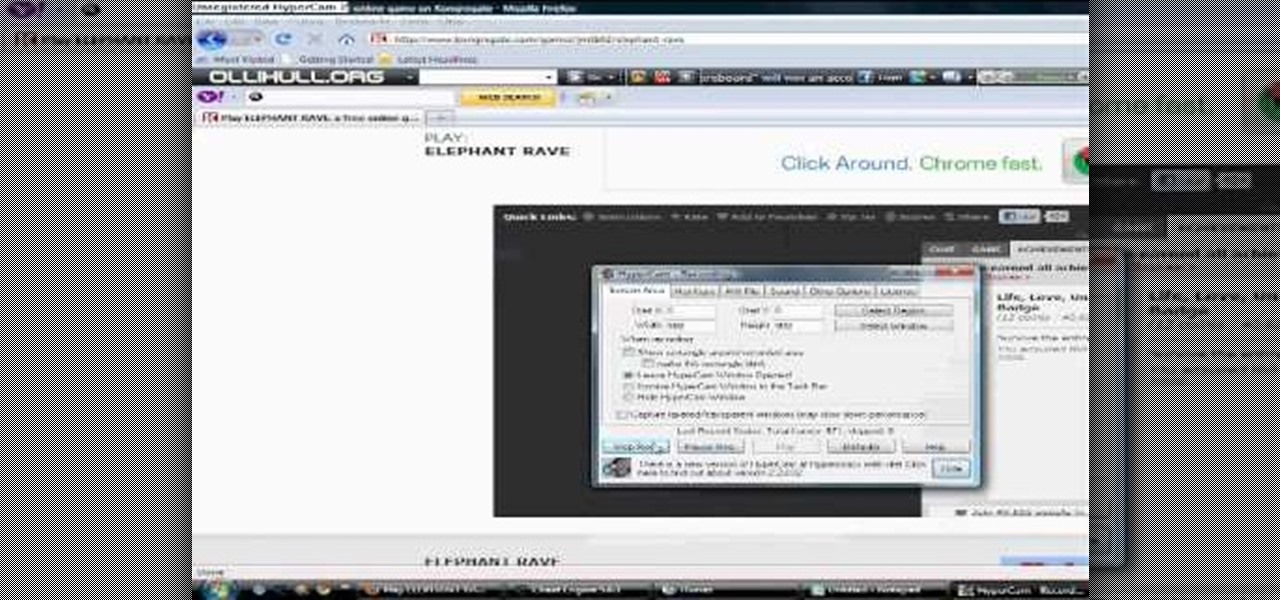
You'll need to make sure that your version of Cheat Engine is at least 5.6.1 or higher. If it is, then you can follow this tutorial, which shows you how to hack the game Elephant Rave and get resources for free!

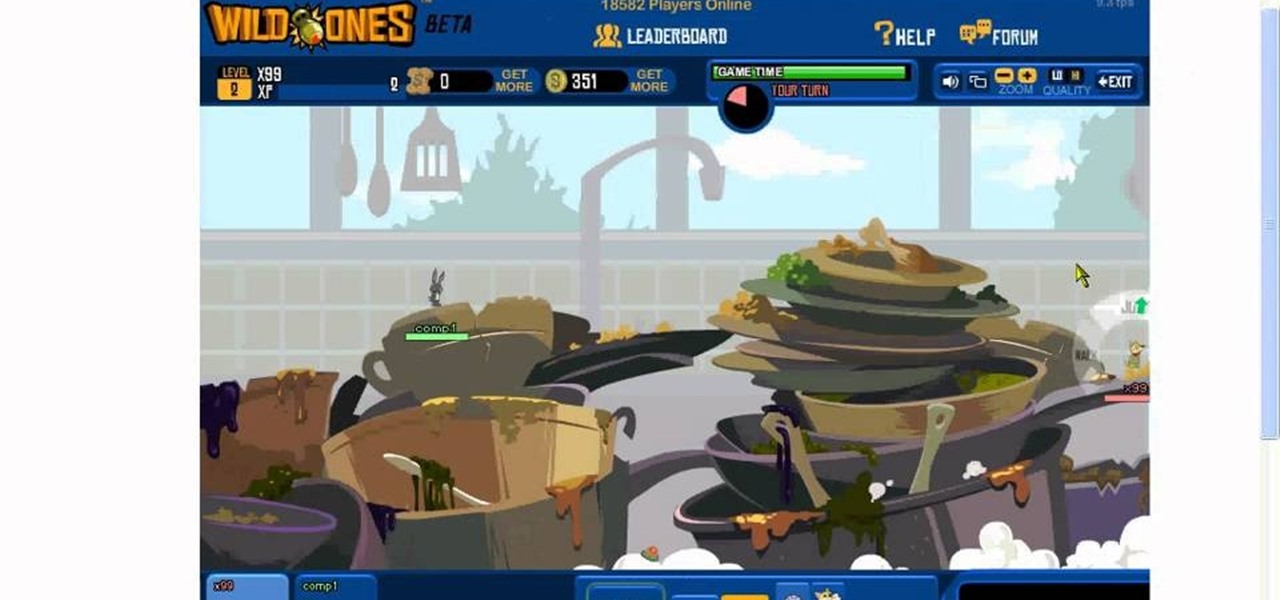
Want to give yourself extra points or resources in the online game Wild Ones? All your friends will be asking you how you passed them up so quickly! Make sure you have the most recent version of Cheat Engine downloaded, first!

Messy drawers getting you down? You no longer have to spend another day rummaging through unruly junk drawers. With some cardboard and character expressing contact paper you can turn any drawer into a neat and well organized one.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

Learn how you can get free online education: see this must-have, massive list of resources.

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

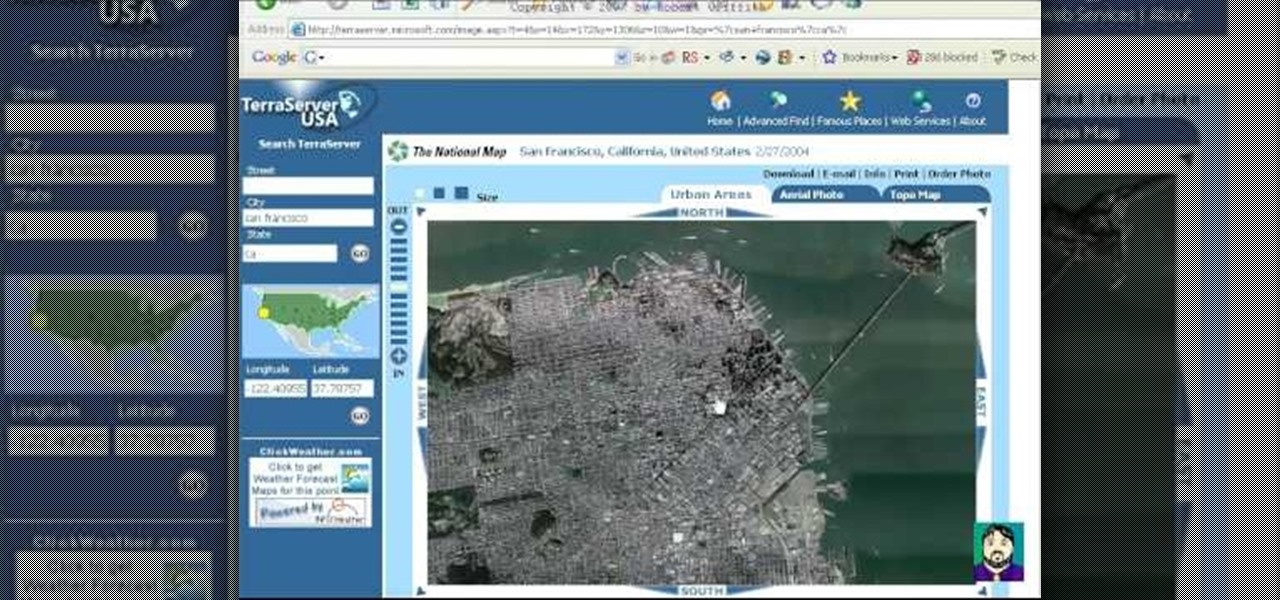
Have you ever wanted to see an aerial photo of your house? Your school? Your office? The White House? Terraserver is a free resource that allows you to do just that.

A look at how to manually create forms with Delphi. Creating forms as they are needed can make your application start faster and take up less resources.

In this dance instruction video series, build on that sturdy tradition by learning some advanced steps and moves.

If you're looking to get started with your training in web development, a natural starting point is learning to code with Python and then saving and sharing your work on Git and GitHub. These are standard tools of the industry, and mastering them will put you one big step closer to succeeding in the professional sphere.

It's a common and unfortunate myth that you need to work in web or app development if you have a knack for coding and design. In fact, more and more development pros are entering the exciting and increasingly lucrative world of game design, thanks to a growing demand for strategy games that can be played on multiple platforms.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

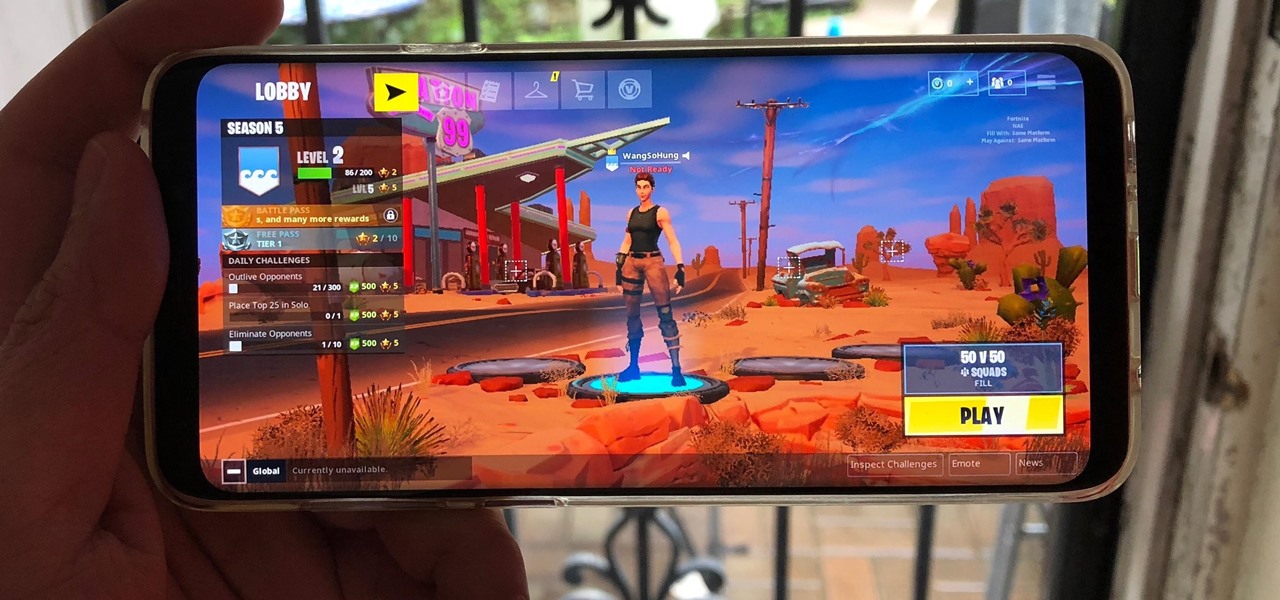
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

Water makes up about 60% of your body weight. Whether you like it plain, flavored, bubbly, or in beverages or food, we all need water daily to avoid dehydration and stay healthy. For communities in need of clean drinking water, new research using bacteria may offer a simplified, lower-cost method for boosting potable water supplies.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.