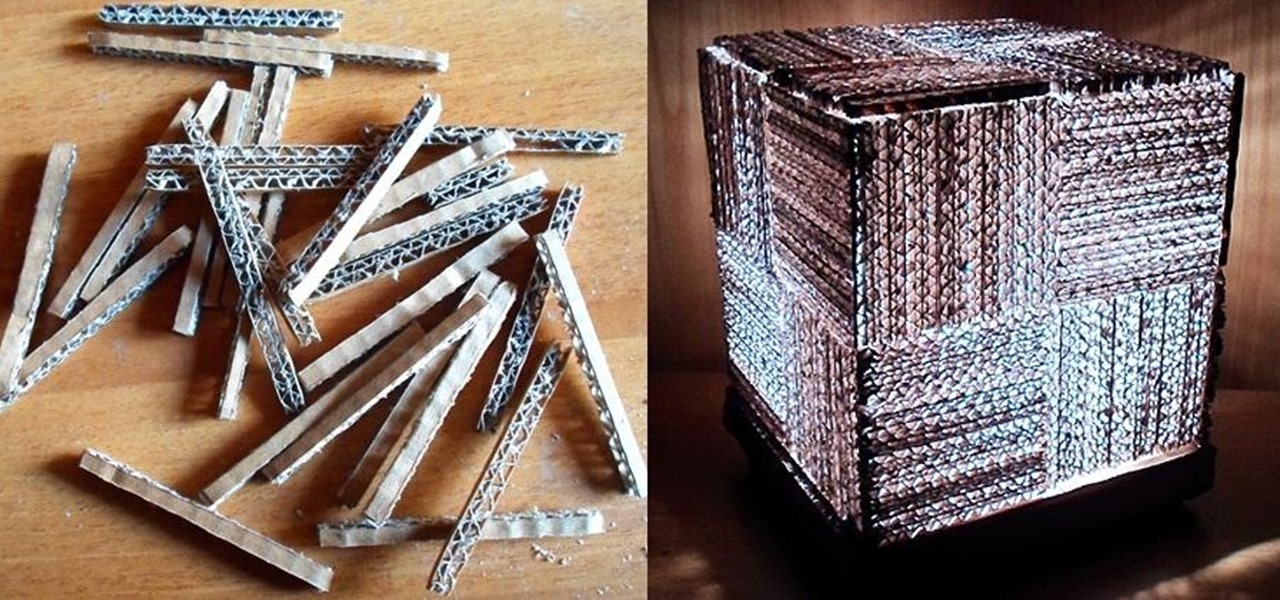
The problem with a lot of DIY projects is that they can require a lot of materials. You still end up with the satisfaction of something you built with your own hands, but the shopping trips can get pricey.

Contrary to popular belief, IKEA can get pretty expensive. You find something that comes pretty cheap, but then, you decide that your GORF will look good with the BLERGH, and you really need the SPLOOF to tie it all together. Pretty soon, your living room looks like an IKEA magazine ad, and your bank account has seen better days. Instead of spending so much money at IKEA, why not build your own pieces of furniture?

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...
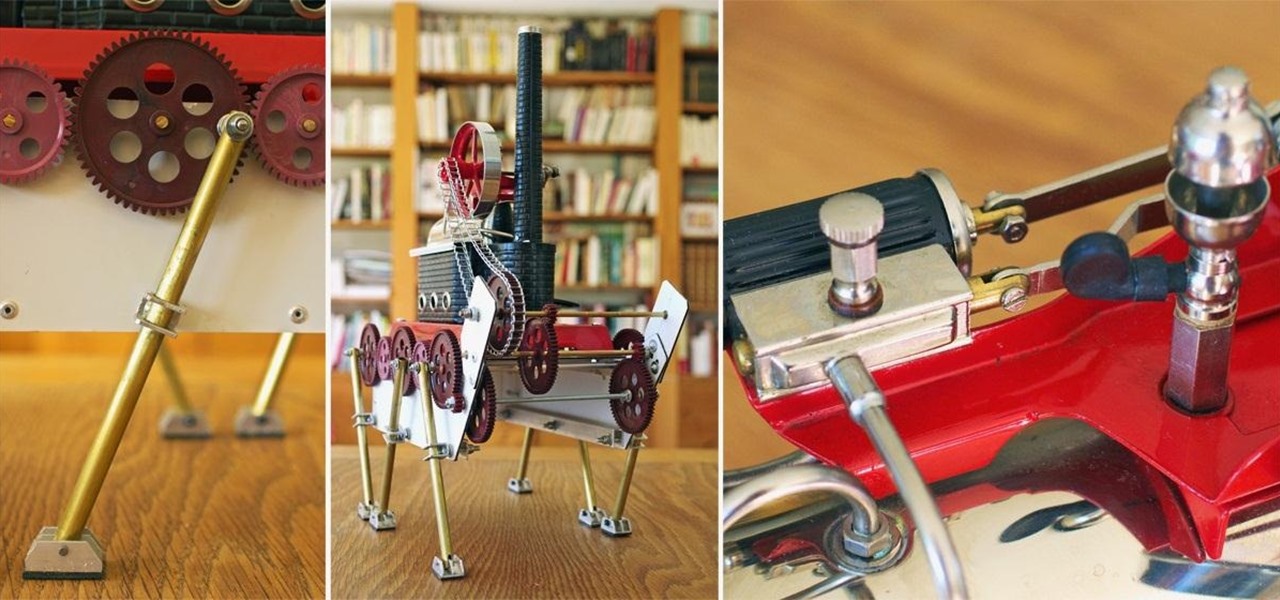
So you've made a somersaulting robot, one that delivers your beer, and even a robot you can ride, but you want to try out something really different. Why not add a steam engine?

Looking for a way to make your bike stand out? You could light it up with LED rim lights or turn signals. Or if you're looking for something a little less flashy, you could make your own set of custom wooden handlebars like these by furniture designer David Moore. To actually make these wooden handlebars, you will need some woodworking tools, not to mention some actual woodworking skill, or at least the tools and some knowledge on bending and forming wood. In his video below, David shows exac...

Hate answering the door, but don't trust your friends with a set of keys? This RFID front door lock made by Steve Pomeroy will solve all your party-hosting problems. It reads the RFID tags in his friends' public transit cards and decides who's allowed in based on "groups" that Steve defines. And I have to say, it's also rather stylish. It's controlled by an Arduino serial console and a custom Android app to add and remove cards. The reader can store 50 or 100 tags at a time and allows 7 diffe...

Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar?

If you're a steampunk enthusiast looking to give your bathroom an extra kick, this just might be the project for you. This stylish and functional "vintage" toothbrush timer knows when you've grabbed your toothbrush, and will visually count down two minutes before alerting you when you've brushed long enough. All you'll need to put one together yourself is a microcontroller (the designer used a ATmega328p), a weight sensor, light bulbs, brass cups and a tray, an alarm clock's chime, and some w...

Check out this video to learn how to make one layer of the felted flower from Itty-Bitty Hats for babies and accessorizing and customizing clothing.

Learn how you can do cool hat tricks to mix up your dance moves with this tutorial. This how to video teaches hat rolls, and hat flips to do when you are dancing. Watch this video and you'll be doing hat tricks on the dance floor in no time.

Who would have thought that dryer sheets can be a quick remedy for super-staticky flyaway hair? But it's true. It's all about the positive charges in the sheets and their ability to neutralize electron buildup. And that's not the only surprising quick fix for hair problems that you can easily find in your home.

Have you always wanted to be the captain of your own ship? Make that dream come true by following along with these simple steps; they'll make everything you need. Watch this video origami tutorial and learn how to origami not just a paper but, but the absolutely essential sailor captain's hat.

This video crocheting tutorial show how to crochet a reverse single crochet, handy for finishing off edges to hats, whether knit or crocheted. This will give you a handsome border to any of your hats or even scarves. It is a great stitch for a strong accented border. Learn how to crochet the reverse single crochet stitch by watching this instructional video.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Soda bread, corned beef and cabbage, and colcannon are all great dishes to serve up on St. Patrick's Day, but desserts really let your inner leprechaun come out to play. Not only can you have fun incorporating all kinds of tasty Irish liquors into baked goods, you get to dye things green.

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

This tutorial teaches viewers how to do a Cowboy Casanova hair style for short hair similar to Carrie Underwood's. You need to add volume to your hair by shortening it. Gather a small portion of the bottom part of your hair. This is where most of the long strands are. Separate it from the top half of your hair by placing it up and bounding it with a bobby pin. Divide the bottom half of your hair into 3 parts. Get one part and slightly twist it on the ends and bring it up. Secure it on place w...

In this video Anthony teaches you how to make a hat from newspaper. If you want to make a hat out of newspaper, do the following: Take the middle section of the newspaper, where you have two pages that are attached. Fold the two pages at the center crease. Make two triangles inward, towards the crease. Fold part of the bottom area of the triangle up. Flip the page and do the same thing on the other side. Open it up slightly and place it on your head.

Your job is to defeat Sapientia in this fight on the Xbox 360 game Bayonetta. In Chapter 13 - The Cardinal Virtue of Prudence, attack the red sphere over Sapientia's head. This fight starts with Bayonetta on the ocean, on a surfboard-like object. Sapientia will use two attacks. The first attack starts with his fin sticking out of the water, like a shark. He will then jump into the air and dive at you. Just keep moving in a straight line to avoid this attack. For the second attack the camera w...

Ten verses are in this level of the Xbox 360 game Bayonetta. In Chapter 9 - Paradiso - A Remembrance of Time, get ready to fight Golem. From the floating clock face you can jump to the yellow floating disk. Follow the path of floating objects to the floating courtyard garden.

Battle Temperantia is this episode of the Xbox 360 game Bayonetta. In Chapter 7 - The Cardinal Virtue of Temperance, prepare for a fight. This chapter consists of a boss fight. You'll start on a platform. Temperantia will punch the platform with his fists and they will stick in the platform. Attack the lighted area of his wrist. While you are attacking he will shoot at you with his other hand. He slowing sweeps his guns, so you can attack until his bullets get close to you, then jump as his l...

You'll need to complete 9 verses in this section of the Xbox 360 game Bayonetta. In Chapter 6 - The Gates of Paradise, there are plenty of battles to be had. As soon as you start this level, look behind you and you'll find a headstone with one-third of a Golden LP (Odette) inside. Also is this starting area is a book, "Entering Vigrid." Break down the gate here to start your first fight. After the fight you'll get the final thrird of a Golden LP (Odette) and a book, "The Angel's Banquet Hall ...

There's 14 verses in this chapter in the Xbox 360 game Bayonetta. In Chapter 5 - The Lost Holy Grounds, combat Grace and Glory, Durga, and Alfheim. Near where you start you'll find the book "Crescent and Sunrise Valleys." Walk along the path and it will crumble as you go.

Battle in verses 1-12, killing Fairness and Angels, in the Xbox 360 game Bayonetta. In Chapter 3 - Burning Ground, you have to make sure you know what you're doing. In verse 4, the creature is called Fairness. A soon as it appears it will shoot a fireball at you, be sure to dodge it. Fairness has several attacks it uses. It can shoot fireballs, which move faster than other fireballs you've encountered. It has a charge attack that you can dodge or you can jump over it. It also has a sonic atta...

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.

See the whole backstory behind the Xbox 360 game Bayonetta. In the Prologue - The Vestibule, you see how to start playing. The first part of the game is an extended cut scene where you will learn the back story of Bayonetta. During some scenes you can control Bayonetta and fight the enemies you, but you don't have to. You don't have a health meter at this point in the game and can't die.

Execute the 9th puzzle, called Hat Trick, in Assassin's Creed 2. Image 1: Move the cursor onto Houdini’s torso. Image 2: Move the cursor over Gandhi’s heart. Code wheel puzzle: Your hint here is pretty obvious; there’s a big, glaring “6=1” next to Oswald’s picture. So move the red wheel so that the 6 is over the gray 1, and plug in the corresponding numbers. For more info, watch the whole gameplay.

For women who need tips on proper hair care, Akiyia demonstrates how to take care of your weave. These tips will help you maintain your weave, get some ideas for keeping it looking good and natural, and above all, stylish! For more styling ideas, search for hairstyling on WonderHowTo.

Bluestone landings are athletically appropriate in just about any back yard. This how to video is a quick excerpt from a DIY show that demonstrates how to install a garden landing with bluestone. Learn tips for installing a stylish bluestone landing with various sizes of pavers.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Setting up Face ID is simple, but getting it to work correctly every time is a different story. While there are numerous tips for getting Face ID to work every time you need it on your iPhone X, XS, XS Max, or XR, Apple has added a better option in iOS 12 that lets you add an "alternative appearance."

Just over a week after debuting, Animal Crossing: Pocket Camp received its first-ever event geared toward the winter holiday season. With the ability to craft Christmas-themed goodies and own a full Santa suit, it's the perfect time to jump into Nintendo's latest hot mobile game.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Hello! I want to share a few hints about staying literally cool when the temperature of the air outside rises incredibly. So, if you're in a very hot area, please continue reading!








































