
You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

The rock drum beat is an intricate drum pattern that incorporates the hi-hat, snare and bass drum. Learn some tips for playing various patterns of the rock drum beat from an experienced drumming instructor in this free music lesson video series.
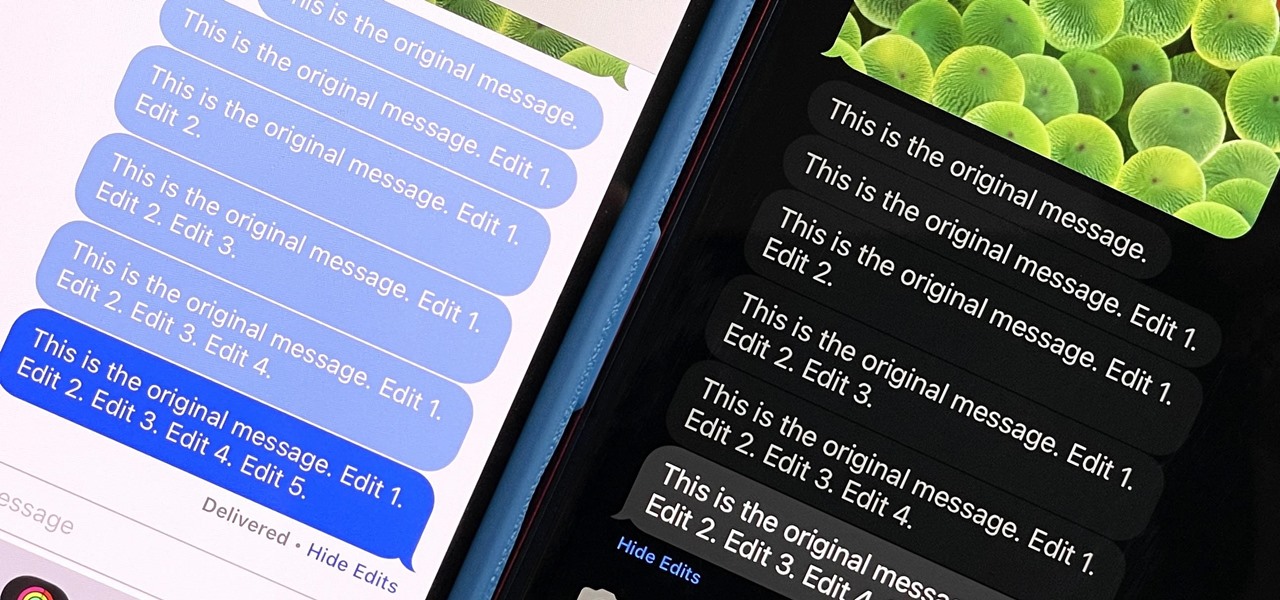
Apple's controversial iMessage-editing feature in iOS 16, iPadOS 16, and macOS 13 Ventura is now less likely to be abused by malicious users.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.
If you have information technology or computer science aspirations — even white hat hacking — then Python is a programming language you absolutely have to be familiar with. According to a recent survey of industry experts, Python is the fastest-growing language in the developer field. It's also one of the most sought-after skill sets among employers and is responsible for some of the best hacking tools.

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

While there is a lot to be excited about when it comes to iOS 12 in general, iPhone X users will not just get the same new features and tweaks that all other iPhones will get — they'll get a few unique ones that will make the device even more desirable to those who don't have one yet. Also, iPhone XS, XS Max, and XR users will also see these benefits out of the box.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Over the years, mobile gaming has become a phenomenon, rivaling in magnitude with its console and PC-based counterparts. We even have mobile versions of Fortnite and PUBG now, games that require lots of processing power to run. But when you just want a quick game to play in the grocery line or even on the toilet, try these simple, quick games that you can play right on your lock screen.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

One of the best new features in Android Oreo is the new Adaptive Icons system. Starting now, developers can create a single icon for their apps, then your launcher can stylize those icons in a broad range of shapes to match your system theme. Most home screen apps haven't added support for this feature yet, but Nova Launcher just threw its hat into the ring.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certain cells of the body, resisting treatments that kill it.

Whether you made the switch from iOS, or you came from a different Android device, there's a lot to learn about your new Galaxy device. Samsung does things a bit differently, and thanks to their TouchWiz interface, there are tons of added features to take advantage of—though some folks might find these extras to be a bit too much.

I know I'm in the majority when I say that grilled cheese sandwiches are one of life's simplest and best pleasures: gooey, rich, melted cheese, sandwiched between two perfectly-buttered pieces of toast... perfection.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

In the era of smartphones and cloud-based computing, it almost seems irresponsible to keep a stash of paper documents. Not only is a physical paper printout environmentally impractical, it's also a lot harder to organize and keep track of than a digital file stored on a hard drive.

Halloween is a night to dress up as any character you'd like—but for women, that typically means wearing something skimpy or downright absurd. From "sexy" policewomen to nearly undressed fairy tale princesses, we're surrounded by costumes that leave little to the imagination. And, let's be honest: who wants to spend a chilly October night in barely-there clothing?

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

The Dark Knight Rises. The Amazing Spider-Man. The Avengers. Halloween is a few weeks away and all we're going to see are these same ol' superhero costumes. It's like that every year, due to the immense popularity of comic book films by DC and Marvel.

For those who don't know, LEGO recently came out with a new line called Monster Fighters. This set is about fighting monsters, sure, but it's about fighting classic monsters in a Steampunk universe. Just look at this promotional picture from the LEGO site: That LEGO dude (properly called a minifig) is wearing a vest, pocket watch, bowler hat, and a mean smirk. Not to mention that he has a robotic leg. You won't find the word "steampunk" anywhere in this marketing campaign, but I call Steampun...

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Your closet is an area that holds important things such as keys, glasses, clothes and shoes. However, for some reason, it's always messy. Why is this? I know my closet is messy because I don’t have a lot of time to sit down and organize every little thing in there. I have never really even given much thought into organizing it.








































