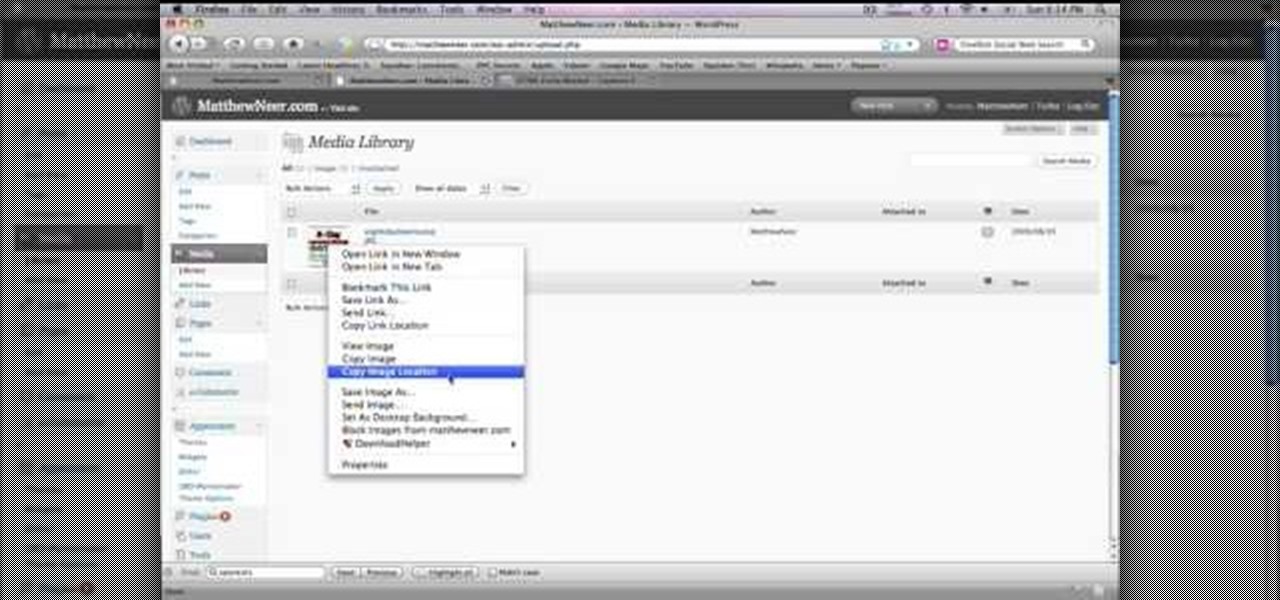
In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

This is a javascript trick that will work on any website. Just go to the webpage you would like to view go bananas, erase the url from the address bar, insert this code into the empty address bar, hit enter, and enjoy:

It seems like its hard to get as much sleep as we need, doesn't it? Sleep is important and effects how you function throughout the entire day. Follow these tips and you will be on your way to a good night's rest.

Setting up a chroma key backdrop contains various steps/ the support system and muslin consists of various parts like the support stands, shrink lamps and the muslin. Place the two stands 12 feet apart and attach 4 clamps to vertical section of each stand. Snap the crossbars together in a proper way and insert the muslin into the respective end of the crossbar and put the crossbar on the stands with the green end of the muslin facing out. The muslin should be attached using the clamp. And ens...
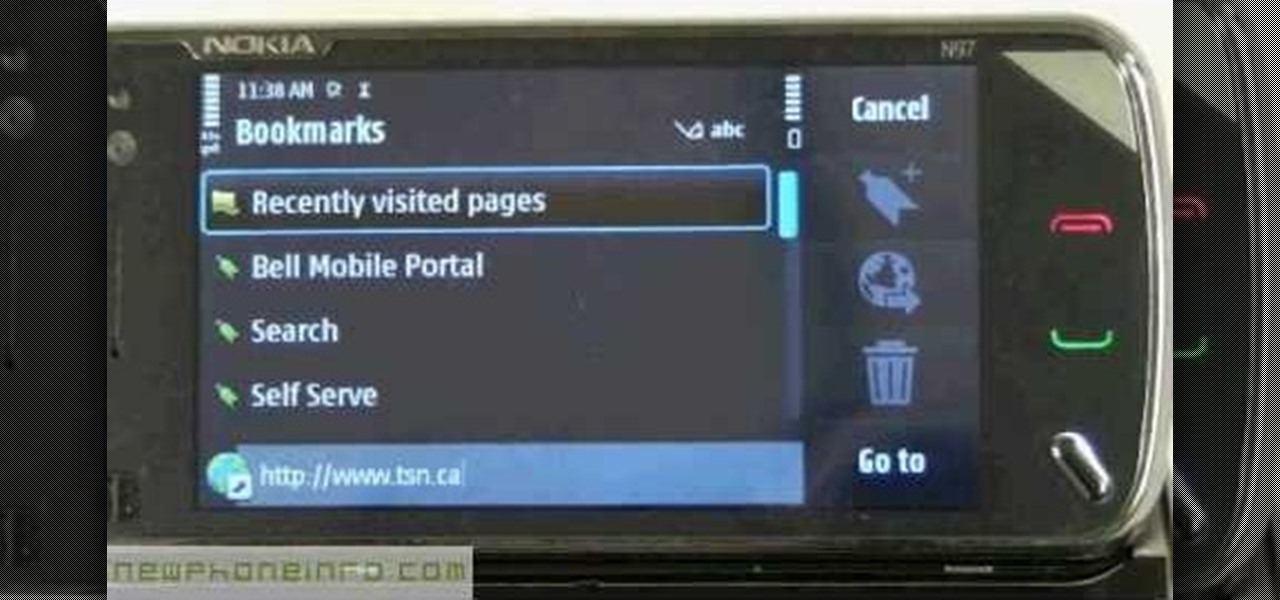
If you want to know how to use the web browser on your Nokia N97, you should watch this video. On the home screen, tap the Web icon. Bookmarks screen appears. On the right side of the screen there are icons present namely: Exit, Add Bookmark, Go to Web Address, Delete, and Options. Type in your desired URL and tap Go To after tapping the Go to Web Address icon and a URL textbox appears at the bottom. Wait for the webpage to load. If you want to display some options, tap the Expand Sidebar ico...

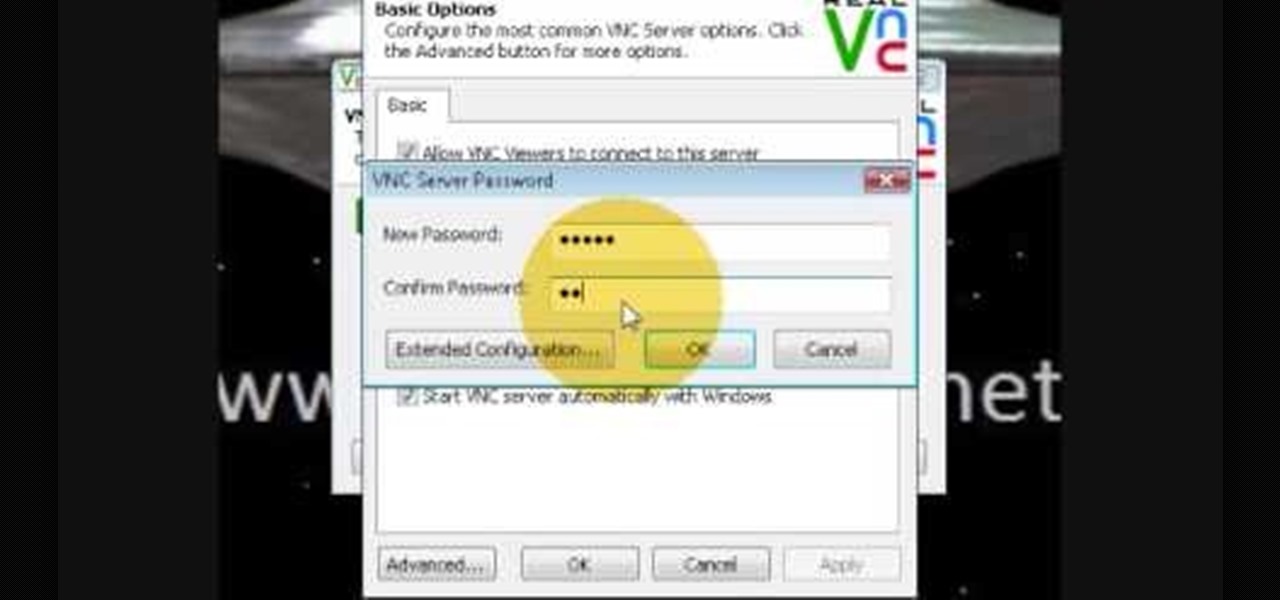
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

Award winning author Susan L. Reid teaches us how to write a great mission statement for your business. 1. First, write your "purpose statement". This answers what your business wants to accomplish and what problem or need your business is trying to address. Simply state the answer to this question. 2. Write your "business statement'. This describes the activities or programs your business must do to support it's purpose. Ask yourself what you are doing to address the need identified in your ...

This how-to video explains how to copy and paste text in the browser in a Motorola Droid phone.

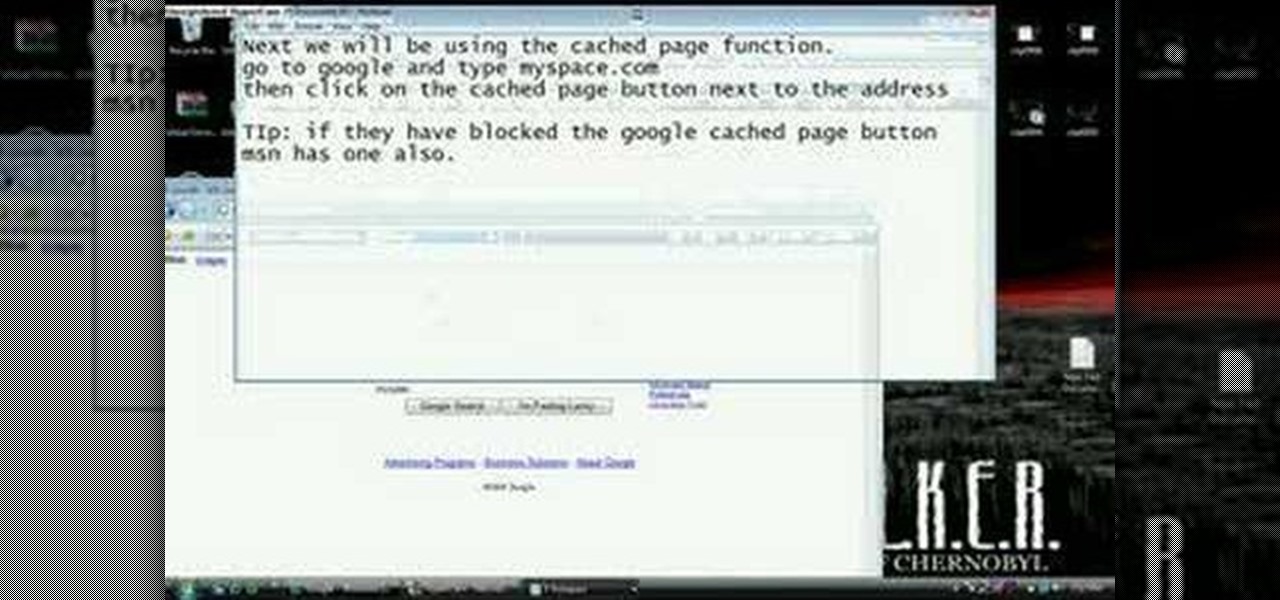
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

Dropping out of high school doesn’t have to mean the end of your educational career. You can earn a General Education Development diploma, also known as a GED. In this video, learn about the process needed, step-by-step, to get your GED.

Looking to get your family together somehow? Why not a family portrait? It's both a great keepsake and as an excuse to get everyone together. In this video, learn how to snap a great family portrait.

Having trouble coping with the fact your son picked a less than stellar choice to marry? Not too fond of your son’s taste in women? That’s his problem; don’t make it yours.

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Don’t laugh—butter sculpture is a true art form that originated in Tibet in the 7th century. It is now one of the highlights of many American harvest fairs. Learn how to make your own butter sculpture.

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from Apple Maps, so they know precisely when you'll arrive, and they'll even get updates if traffic is holding you back.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Facebook added a new feature that lets you post 3D versions of your portrait mode photos for all your family and friends to see on their smartphones, computers, and virtual reality goggles. These new 3D photos add a whole new dimension to your images with movement and more depth.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Greetings my fellow hackers.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

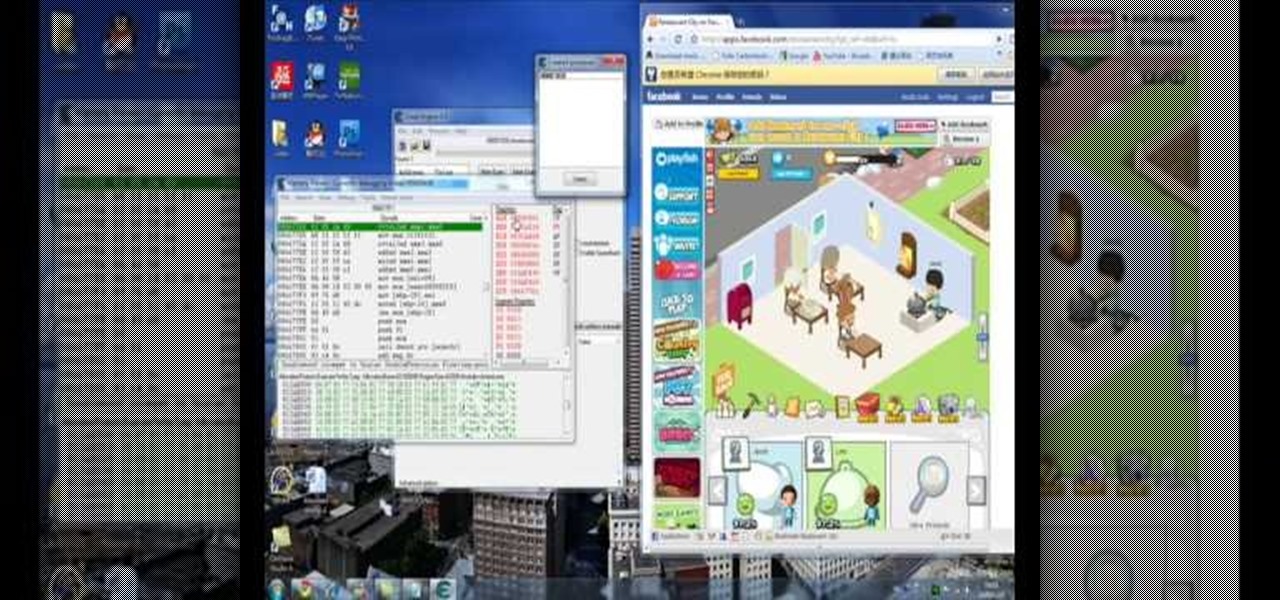
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

Hera, wife of Zeus, was the queen of the gods. As such, she sat on her throne on Mt. Olympus with great majesty and elegance. And as the goddess of marriage and women, she exhibited great poise and care for her subjects.