
How To: Use the word "being" correctly in English
Being is a word that can be hard to master for English as a Second Language speakers. It can be used as a gerund, or in present or past continuous tenses.


Being is a word that can be hard to master for English as a Second Language speakers. It can be used as a gerund, or in present or past continuous tenses.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

One of the best features of Apple's Final Cut Studio is the graphics interface feature Motion. With its ability to create and edit motion graphics, you can easily create title sequences for your indie film, or maybe even a professional movie, with 2D or 3D visual effects compositing.
Learn the important steps necessary for the best printing experience when printing to the Epson 3800. This tutorial is specifically designed to address some of the issues with the Epson 3800 and the MAC OS X Leopard operating system. Here is a detailed explanation of the changes that were made to the 10.0.1 update to Adobe Photoshop CS3. Remember, having all the current versions of Adobe Photoshop, and the Epson drivers is critical to success when printing.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.
In the following lessons you will learn some essential tools and techniques for working with muscles in Houdini. In the first lesson, you will learn how to rig up a simple muscle arm using Houdini's Muscle tool. The Muscle tool uses meta-balls to capture your character's skin with realistic muscle/skin interaction.

Topiaries are no longer just speciality plants. They have become very popular and are showing up in garden centers and nurseries across the country. Topiaries have been used for thousands of years, in places like Babylon and England. Today we take the mystery out of topiaries and discuss pruning trees and shrubs to look like geometric forms. As well we talk about designing topiaries, selecting the trees and shrubs and maintaining them to look their best and show you how to create small topiar...

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

Boomerangs are perhaps the quintessential story tool on Instagram. Surprisingly, there's never been much to them — point and shoot, and your subject plays forward and backward in a never-ending loop. Perhaps its prolonged simplicity inspired Instagram to give Boomerangs a bit more depth because the company just introduced three new effects to try out.
Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.
Your Pixel has a few hidden features you probably don't know about, like the ability to clean up your funky contacts list. Since I'm sure you haven't manually organized your contacts since the inception of Android, there are likely some incomplete and duplicate contacts. Thankfully, your phone can fix this automatically.
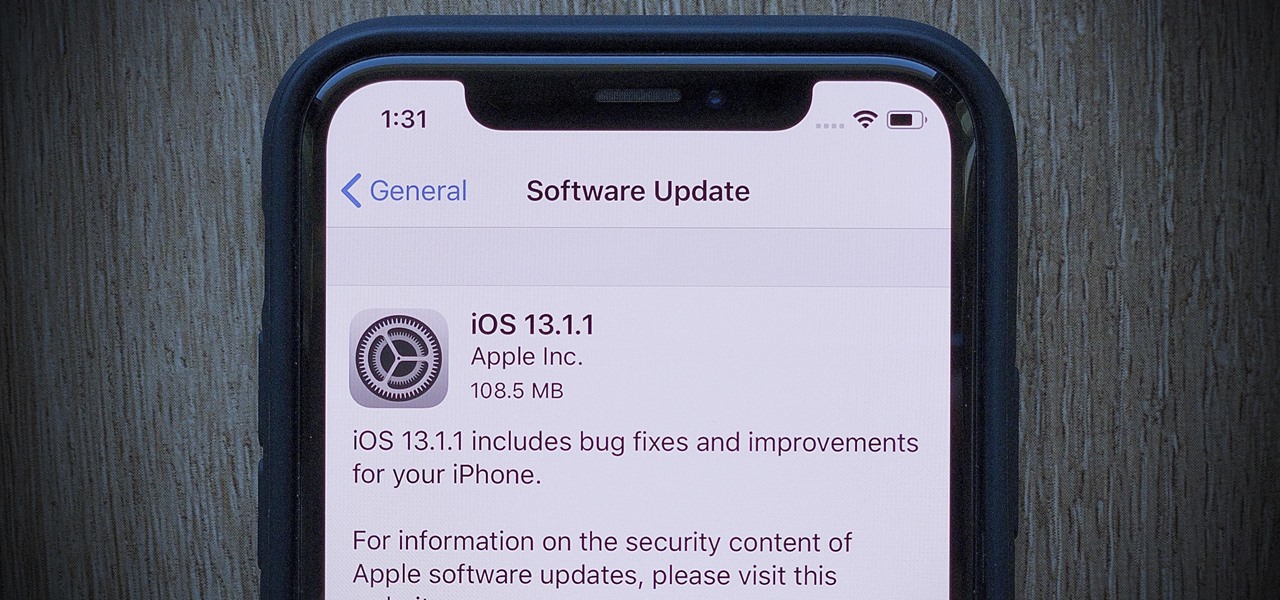
Is Apple trying to set a record for the highest number of updates within a two-week period? You wouldn't be blamed for thinking so. Just eight days ago, Apple publicly released iOS 13.0 for all compatible iPhones. Then, just five days later, Apple seeded iOS 13.1 with 22 new features to boot. Now, just three days into 13.1's tenure, Apple has released yet another update, iOS 13.1.1.
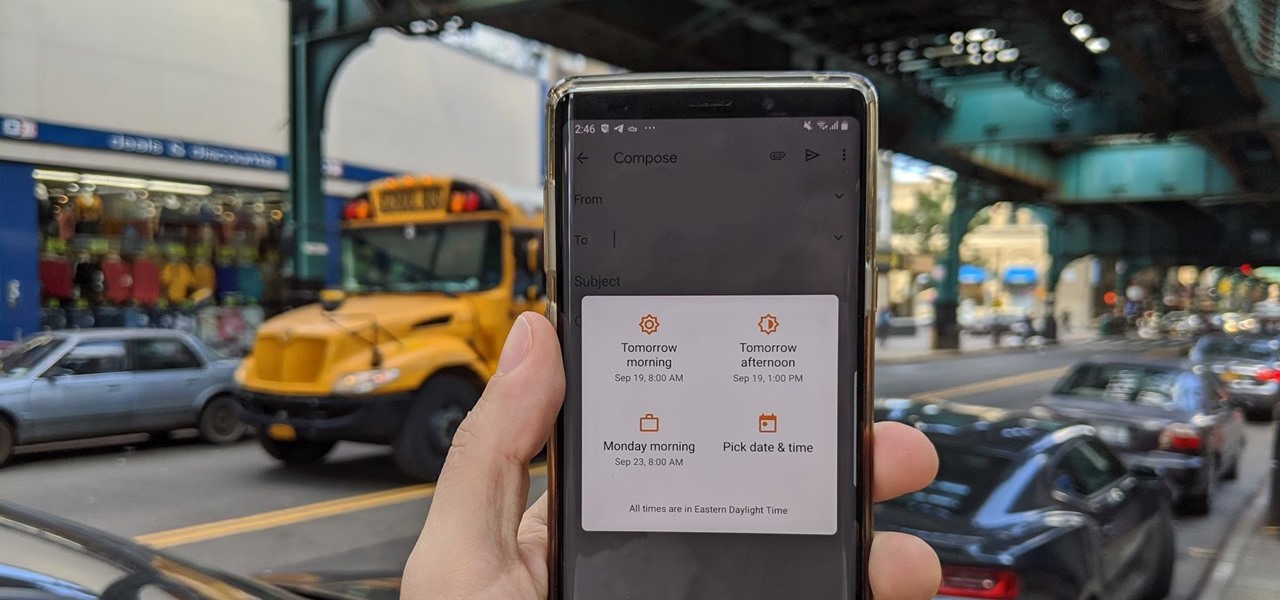
There is power in the detail. Sending an email at a specific time can give you an edge. Depending on what you are doing, it can help your email get read or it can put you at the top of someone's inbox. With the Gmail app for Android and iOS, you can now schedule your messages to maximize the efficiency of your email.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

Better known among consumers for its virtual reality apps, Jaunt is now pivoting toward solutions for augmented reality developers.

Kings of Soccer recently soft launched in the Netherlands and a few other countries, garnering positive reviews from the mobile gamers who've experienced it. With the 2018 FIFA World Cup now in full swing, we wanted to let you in on a little secret: You can play Kings of Soccer right now ahead of everyone else, regardless of where you live.

Futureplay has soft-launched Battle Bombers Arena, giving mobile gamers a refreshing twist on MOBA by infusing it with simple but addicting gameplay based on the console classic Bomberman. Though only available in select European countries, this game can be played on your iPhone right now, regardless of where you live.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

The Android version of Google Chrome only shows a home button on some devices. Unfortunately, this feature isn't available to all Android phones due to several factors. But thanks to a simple workaround, you can now enable this button and set a home page regardless of what device you have.
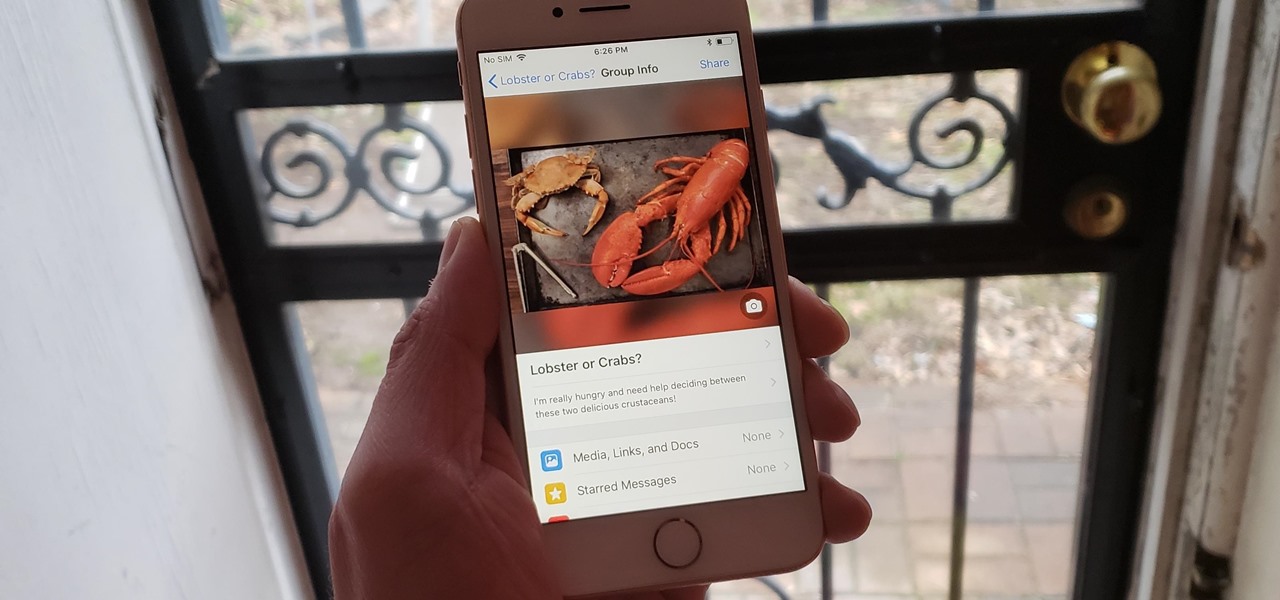
There's a fine line between order and chaos in group chats. With all the cross-talk, threads can easily devolve into a random mess that has nothing to do with the original discussion topic. WhatsApp group chats certainly aren't immune to this problem, but they've recently taken a step in the right direction.

Spring training has begun in earnest, and to mark MLB's soft debut, GLU has soft-launched a followup to the smash hit MLB Tap Sports Baseball 2017 in Canada. While MLB Tap Sports Baseball 2018 is still technically unavailable outside of Canada, you can actually play this game right now through a simple hack.
Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as possible with software updates.
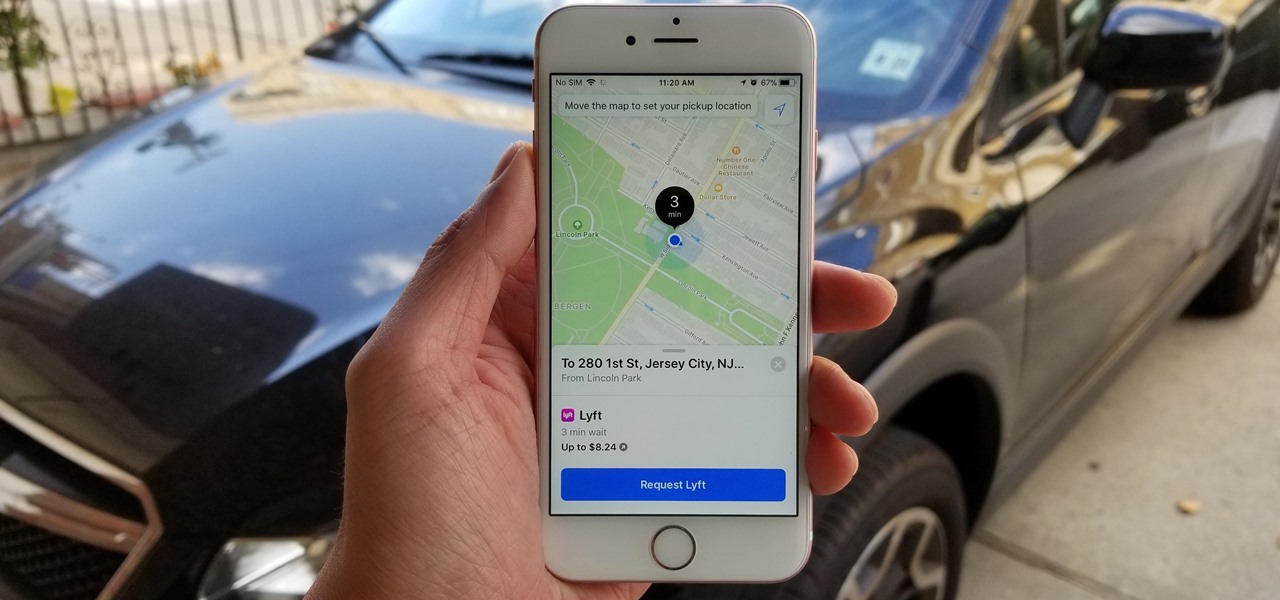
There's no denying the impact ride sharing apps like Uber and Lyft have made on our lives. With fares that undercut traditional yellow cabs, combined with the fact that your ride is just a tap away, these services have become the primary mode of transportation for many folks in urban areas. Thanks to iOS 11, booking an Uber or Lyft has just become a lot more convenient.

There are so many tips and tricks on how to improve your Instagram photos, but one really easy way is to use the HDR camera setting. HDR is high dynamic range imaging and takes three exposures of a photo — overexposed, underexposed, and one in the middle at the normal exposure. The end result is just one image of the three exposures combined.

4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.
Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

Apple's Live Photos is a cool feature that lets you turn ordinary pictures into a GIF-like animated photos. However, these images have some pretty big drawbacks: they live only in the iOS universe and can be shaky without a tripod.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

An app with overabundant features can make it more customizable, but too many options can also be overwhelming, even on a mobile web browser. If you're tired of Safari or Chrome on your iPhone, try out Frameless from developer Jay Stakelon, a simpler web experience using just the essentials.
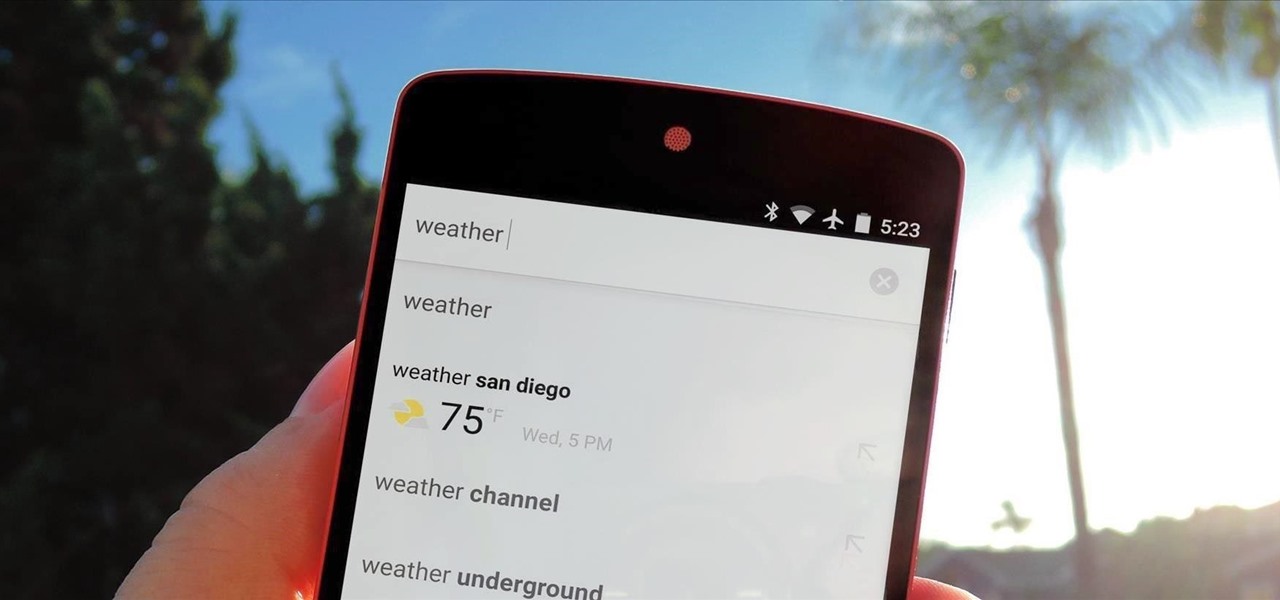
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Sharing files has always been one of Android's greatest strengths. A system of "share intents" allow apps to freely exchange data with each other, making it possible to take a picture with your favorite camera app, then send it over to your choice of photo-sharing apps, for instance.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.