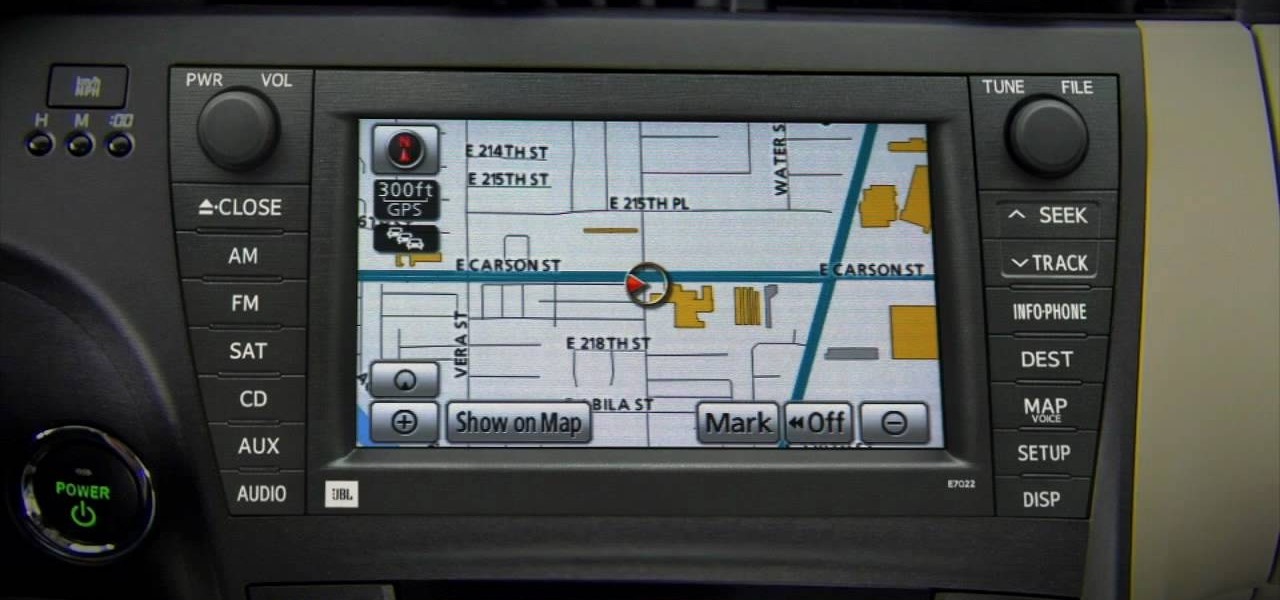
Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?
I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...
The days of Skype 2.8 for Mac are over! Mac users can now rejoice and make calls with ease using the new beta version: Skype 5.0 for Mac OS X (available here). It was well worth the wait, with a revamped look and feel that simplifies navigation and provides a more Mac-like experience.

Let your Canon EOS 7D do all the hard work. With the AF Point Selection option, the digital SLR camera will do all the focusing for you. It's easy to compose and shoot in just one step.

In a smaller interview setting, the lighting will be much different than a bigger scene. You will need to have a good focus on your subject's face and body as well as a clear background so your viewers don't get tired. In this tutorial, learn exactly how to set up your lighting for a smaller setting such as an interview while using a Canon EOS 7D camcorder. This clip will take you through a total step by step lesson so you can get started making great films at home.

This video shows how to properly set up a green screen, to set up the screen we are taking into account this four factors:

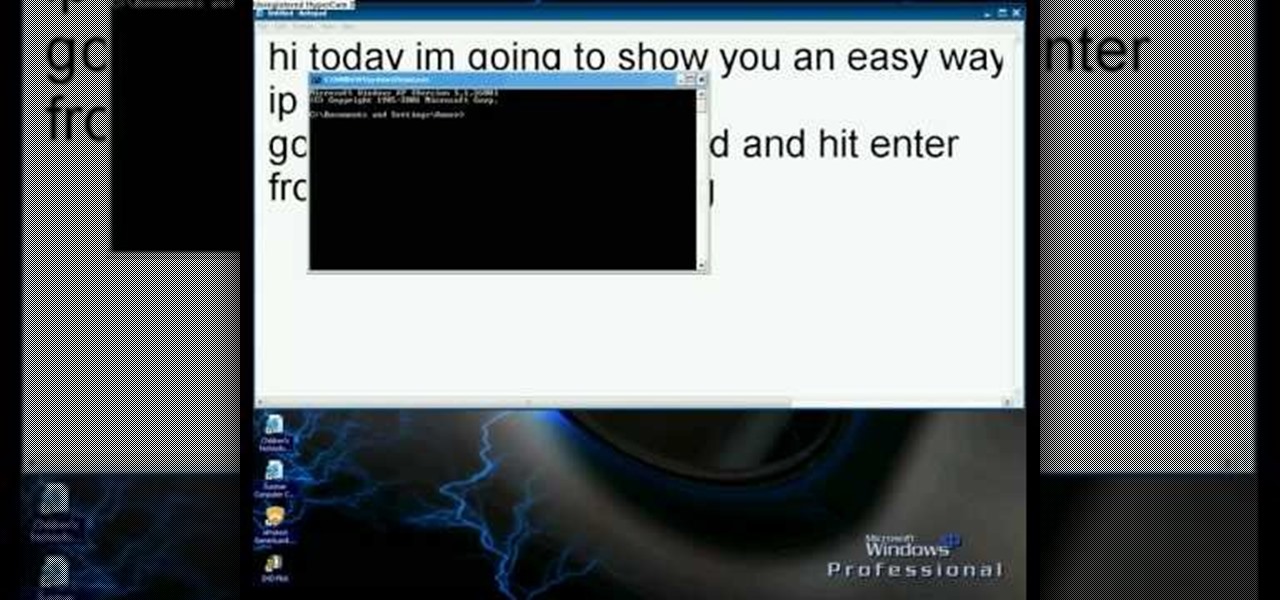
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer and put in the IP address and open the port you found. Now right click after you enter the computer's IP address and the open port. Select full control or view only and there you go. The computer has been successfully hack...

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

In this Fine Art video tutorial you will learn how to focus stack for great macro photos. This video is from EPhotoZine. The idea is to take several pictures of the same subject at different distances. For this you will need focus stacking. If you focus with a wide aperture, everything in front and behind the subject will be out of focus. The idea of focus stacking is to shoot several shots and put them together in a program that automatically brings them all into one. And that is focus stack...

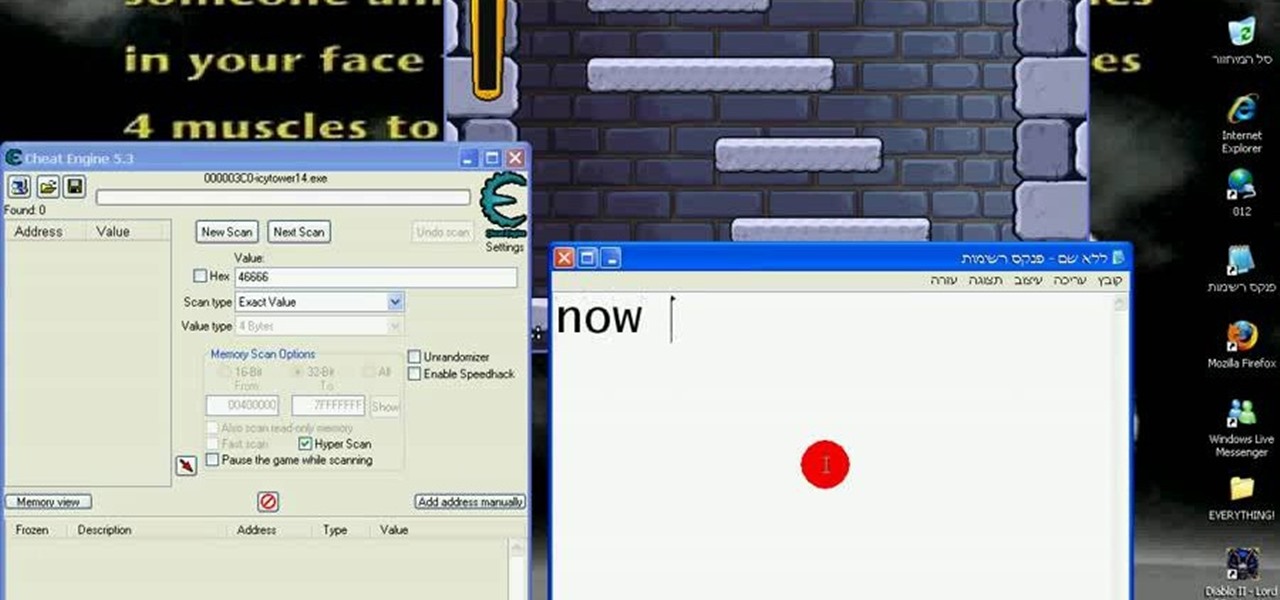
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

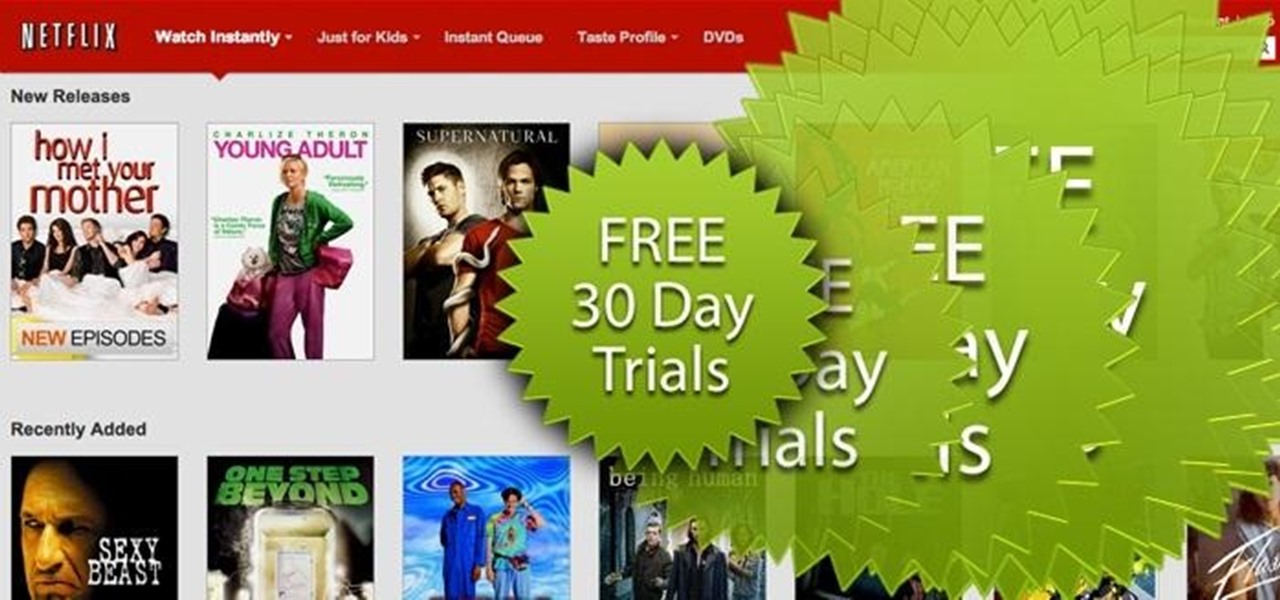
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

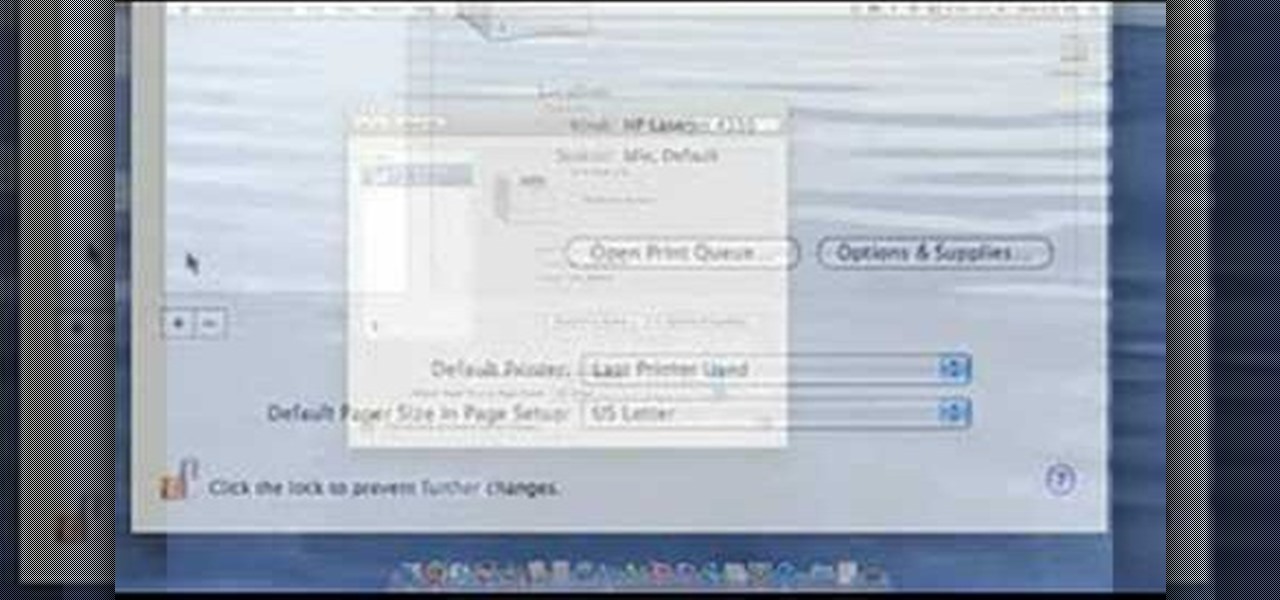
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

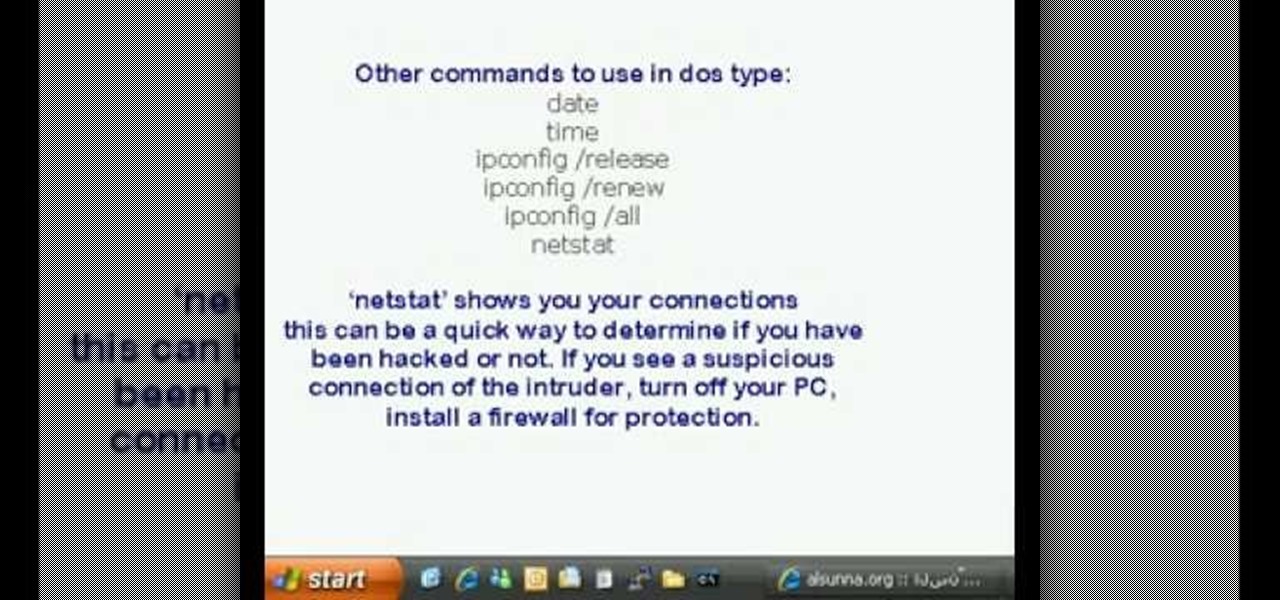
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

In this clip, you'll learn how to reset the IP (or Internet protocol) address on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

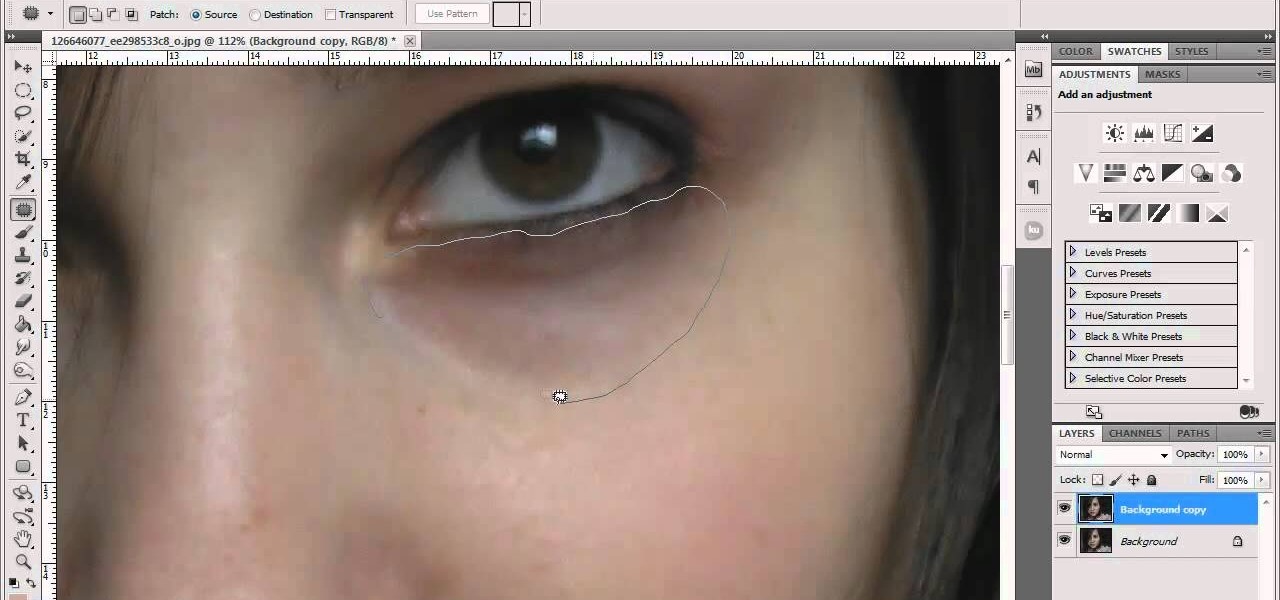
This technique is very similar to the one used for removing dark circles beneath the eyes of of people in your pictures. This shows you a simple technique where you can reduce the amount of gray in a particular area of your photo to get rid of the dark circle look.

Peter John shows palmistry students how to give the subject of your palm reading career advice. Know what to look for on the head, heart, fate and life lines to be able to tell what career your subject is ideally suited for, or if they should make a career change.

New students of palmistry might get thrown in a reading when they encounter a broken line, or one that changes. Peter John demonstrates how to give a good palm reading even when the head, heart or life lines change or break on the hand. He also shows how to detect a change in your subject's future

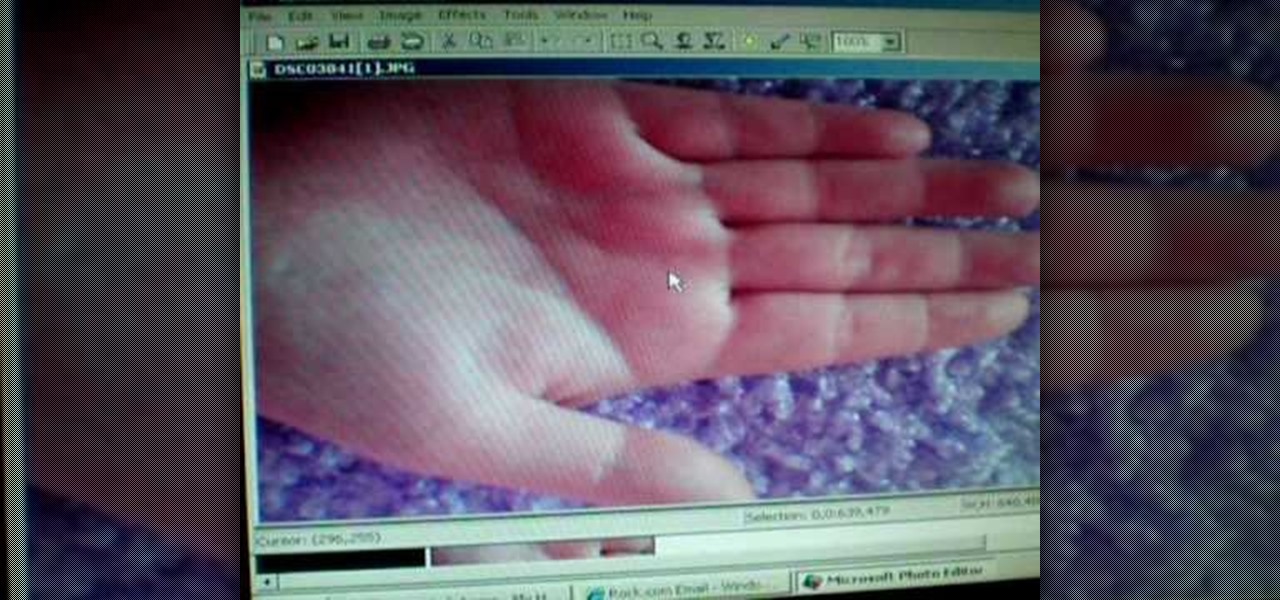
Peter John, an accomplished expert in palmistry, demonstrates how to properly understand what it means when your palm reading subject has a long hand and long lines on the palm. He indicates what to look for to indicate intelligence and good communication skills in your subject.

Is the querent for your tarot card reading destined to become someone famous? Are they looking for a way to gain recognition? Peter John explains which Tarot cards to look out for if your subject is seeking fame and fortune.

Learn how to use the navigation system in a new 2010 Toyota Prius in simple steps. It has DVD based navigation system with easy to use touch screen display. All the navigation routes of USA, Hawaii and parts of Canada are available in it supporting English, French and Spanish languages. When you start the car it opens the map and you can input the destination using voice command or entering text. You can also input your home address and five other special location address.

This video tutorial will show you how to apply four styles of lighting. This video teaches you how to apply four styles of lighting, namely Rembrandt, Beauty, Cameo and filling in from the Key Side. You will learn about high contrast lighting schemes, dealing with the amount of contrast used to highlight a person's face, as well as spotlight effects, and how these tend to draw the viewer into the scene. You will be shown how the Rembrandt Lighting setup contains three steps, namely taking a K...

Interviewing lighting basic training tutorial provides easy to follow instruction in this step by step video. Set up the interview area to allow the best camera angles. Place your lights in key, fill, and backlight positions. Use back lighting spillover to fill subject area without camera spillover. Check your setup with the subjects and make any necessary adjustments to your camera or lighting angles. Place your crew and your ready for your interview. This scenario using key, fill, and back-...

Tom Skowronski teaches us how to shoot a good video. Look before shooting so you have a more controlled movement. Hold camera steady at all times. Move the subject in front of the camera and turn the camera mans back to the sun to illuminate the subject. . Give nose room for a more professional look. Have a full frame and no dead space to have a natural looking video. Cut off at head to have a full frame. Following Tom Showronski's video-making advice can lead to a professional-looking video....

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...